this week in security — april 14 edition
THIS WEEK, TL;DR
CISA warns of Sisense data breach
KrebsOnSecurity: CISA took the unusual step of going public with news of a breach at Sisense, a data analytics firm whose products allow companies to monitor the status of multiple third-party services. That, unsurprisingly, relies on unique customer credentials for each service to keep the connections alive. CISA also warned all customers to reset and rotate any creds or secrets stored with Sisense. Sources tell @briankrebs that the attackers may have accessed the company's S3 storage data to "exfiltrate several terabytes worth of Sisent customer data," including access tokens, passwords, and SSL certificates. Sisense is used by airlines, telcos, and more — hence why CISA is sounding the alarm (and because Sisense has yet to go public). Definitely one to watch, as customers begin taking notice.
More: CISA | TechCrunch | Bleeping Computer | Censys | @gossithedog
Apple alerts users in 92 nations to mercenary spyware attacks
TechCrunch: Apple sent threat notifications to an unknown number of individuals in 92 countries this week warning that they have been targeted by "mercenary spyware attacks," my TechCrunch colleague @refsrc confirmed. Little else was said about the notices, but it comes as a number of nations prepare for elections — the U.S. and U.K. included. The language of the notifications changed from "state-sponsored" attacks — reportedly because Apple faced pressure from India after linking spyware attacks to the Modi government. Israeli media reported this week that spyware makers are working on delivering spyware through the banner ads. All the more reason to use an ad blocker!
More: Apple | Reuters | Haaretz | @runasand
New Palo Alto firewall bug under active exploitation
Volexity: Palo Alto Networks went public this week with a new zero-day under active exploitation — likely by a "single threat actor" so far (that may change) — in its firewall tool, used by corporations around the world. Volexity had the meat of the findings: The maximum 10.0 severity bug, tracked as CVE-2024-3400, which can be exploited without authentication, which means no passwords are needed to break into a victim's network. Exploitation goes back to at least March 26, per the Volexity researchers, who point the finger at UTA0218, a "state-backed threat actor," but which state is not yet known. Since so many organizations rely on these corporate network edge devices (think Cisco, Ivanti, etc.) you'd expect these technologies to be more resilient. Patches are expected out April 14 — so, today!
More: Palo Alto Networks | CISA | HelpNetSecurity | @ryanaraine tweets
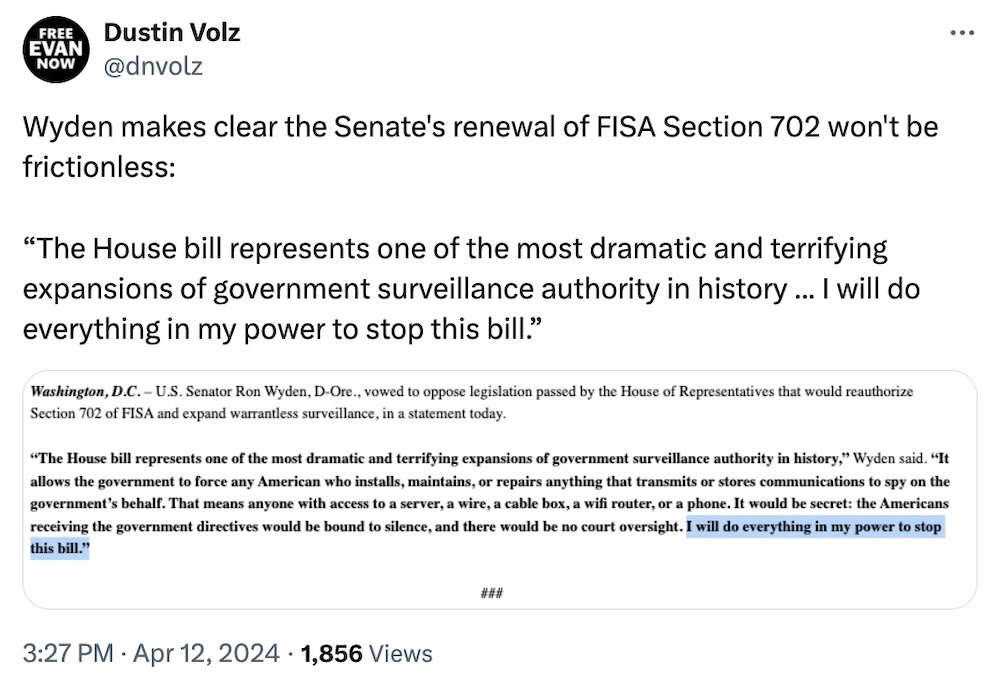
House (finally) passes FISA bill, setting up Senate showdown
Politico: We don't talk about politics here (because they're pretty much all insane) but here's one we can't avoid. U.S. House lawmakers finally passed — on the third attempt — its spy law renewal bill, which by all accounts everyone already hates. That's because the House basically reauthorized FISA, the spy law that allows U.S. agencies to snoop on overseas communications (and those of Americans who get caught up in that), without any meaningful changes or privacy protections. Next stop, the U.S. Senate, where the bill will almost certainly go to die, where at least one senator says he'll do "everything in my power" to block the FISA bill in the Senate. FISA expires on April 19, but don't let that fool you; the annual FISA certification just happened, so U.S. agencies won't lose their FISA powers until at least April 2025. More from @LisaDNews in a video for PBS.
More: New York Times ($) | CNN | @seanvitka | @ronwyden
~ ~
THE STUFF YOU MIGHT'VE MISSED
How to stop your data from being used to train AI
Wired ($): In case you didn't know already, AI systems are largely trained on our data. Here's a helpful PSA on how to block a range of companies — from Adobe to AWS, Google, and Slack — from using your data to train its models. There's also advice for those who own and host their own websites.
Thousands of LG televisions vulnerable to takeover
Bitdefender: Security researchers at Bitdefender found a set of vulnerabilities that allow attackers to take control of a range of LG WebOS-powered televisions. Per their findings, "these vulnerabilities let us gain root access on the TV after bypassing the authorization mechanism." Although these TVs are running software intended for use on the local network, some 91,000 devices are connected directly to the internet. Patches were released in March. Another reminder that you don't always have to connect a device to the internet. Ars Technica also has a good write-up.
New privacy bill in Congress 'isn't there yet'
Tech Policy Press: A bipartisan privacy bill in Congress dubbed the American Privacy Rights Act is the first time lawmakers have introduced a broad consumer rights and privacy law for the entire United States. Finally! Phhhrrrpht! 🥳 ...right? Well, not quite. An analysis of the bill by @JustinBrookman says APRA "isn't there yet" — because a federal blanket law risks "undoing the substantial progress that has been made at the state level," such as California, which actually has a pretty solid data protection and privacy law in the CCPA and subsequent CPRA. If a federal law contains a weaker set of privacy standards, it wipes out any stronger law at the state level. The Washington Post ($) also has a profile of Sen. Cantwell, one of the co-authors of APRA. The reporting cites aides close to Cantwell who say the senator has upended online privacy legislative efforts for years in large part due to "personality clashes and political squabbling," rather than the gobs of money taken in from Big Tech over the years.
Chipmaker Nexperia experiencing ransomware attack
RTL: Dutch media outlet RTL reports that the Netherlands-based chipmaker Nexperia was hit by a ransomware attack, with the malicious hackers making off with alleged trade secrets and customer data, including SpaceX, Apple, Huawei and others. RTL said it validated the data by checking leaked emails and the passports of company executives. The crims are said to be part of the Dunghill extortion gang.
~ ~
OTHER NEWSY NUGGETS
U.S. may ban Kaspersky software: Russia-based antivirus maker Kaspersky may be effectively banned in the United States over national security fears. The U.S. banned the use of Kaspersky software in government in 2017 after hackers working for the Russian government stole U.S. classified data from a NSA contractor's computer, which had Kaspersky installed. A full consumer ban of Kaspersky software could arrive as soon as sometime in April, if at all. (via CNN, Wall Street Journal ($))
Police sifting LockBit files for clues: After a U.K. and U.S. law enforcement operation seized LockBit's infrastructure and servers in February, the plods and feds have been combing through the gang's files to track down its other affiliates and members. So far, Bloomberg reports, some 200 suspected criminals have been linked to the ransomware gang, and investigators now have a clear idea of "who they plan to pursue." Also, Bloomberg has a good weekly cyber newsletter if you haven't signed up already. (via Bloomberg ($))
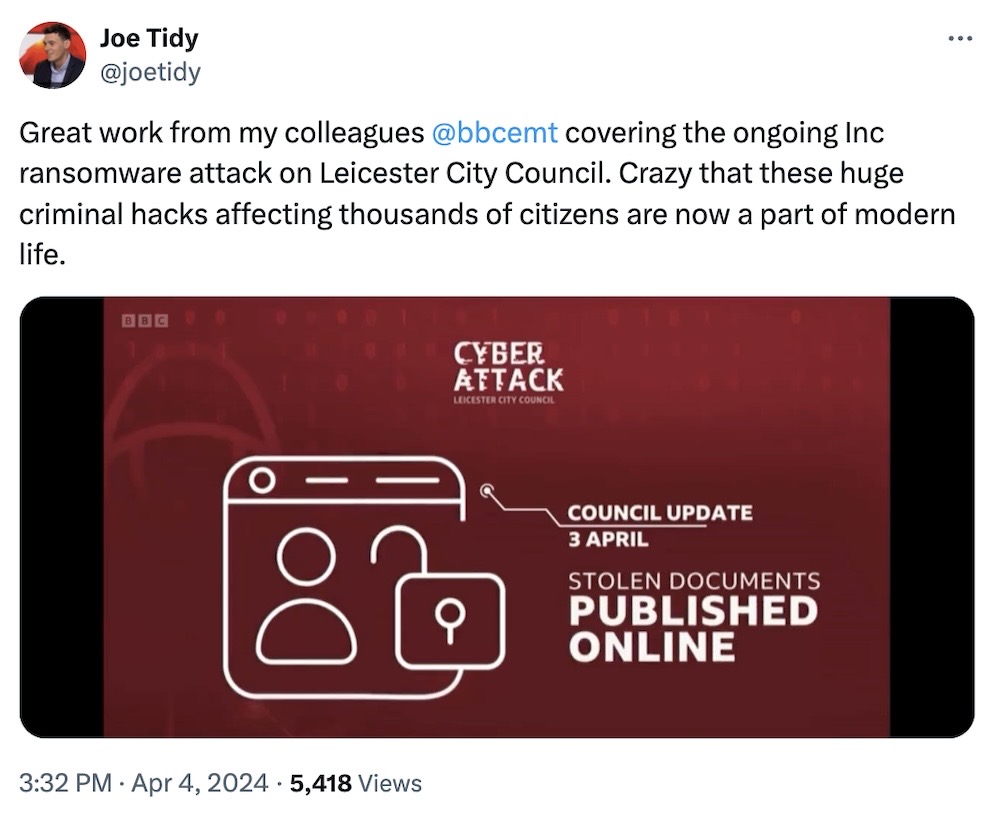
U.K. city council files published after ransomware attack: The council for the U.K. city of Leicester said a "much larger batch" of stolen data was published online following a ransomware attack in March, which knocked much of the city's systems offline for more than a week. The city didn't pay the hackers' ransom. BBC's @joetidy has a good tweet thread on the story plus BBC East Midlands' telly report, and another reminder of why local journalism is really, really important for stories like these (and not just in the U.K.!). (via BBC News,)
Change Healthcare's second ransom looks credible: Change Healthcare, the U.S. health tech behemoth that handles around half of all U.S. patient records, was hacked in January, which led to widespread disruption and outages across the U.S. healthcare system. The company allegedly paid a ransom of $22 million to stop the leak of millions of patient records. Now, a second extortion crew is claiming to have the company's stolen data. After Wired asked the gang all week for evidence, the new extortion crew finally sent some over — including some patient data and an internal company contract — which Wired said looks "credible." Suffice to say, this is not good. (via Wired ($))
CISA says fed agency emails hacked in Microsoft breach: Another CISA fire alarm, this time for federal agencies under its cyber-watch. Last week CISA privately notified federal agencies to secure their email systems following an(other) email breach at Microsoft, which hosts government emails. CISA subsequently publicly released that emergency directive, which confirmed that federal emails were exfiltrated by a Russian government hacking group known as Midnight Blizzard (aka APT29). Researchers say APT29 is Russian foreign intelligence, known as the SVR. Microsoft said back in January that these hackers were rooting around its systems, and as recently as March said the cyberattack was "ongoing." Microsoft hasn't commented since, so assume the fire alarm is still ringing. (via Cyberscoop, CISA)
~ ~
~ ~
THE HAPPY CORNER
Well that was a lot. Time to breathe and decompress in the happy corner.
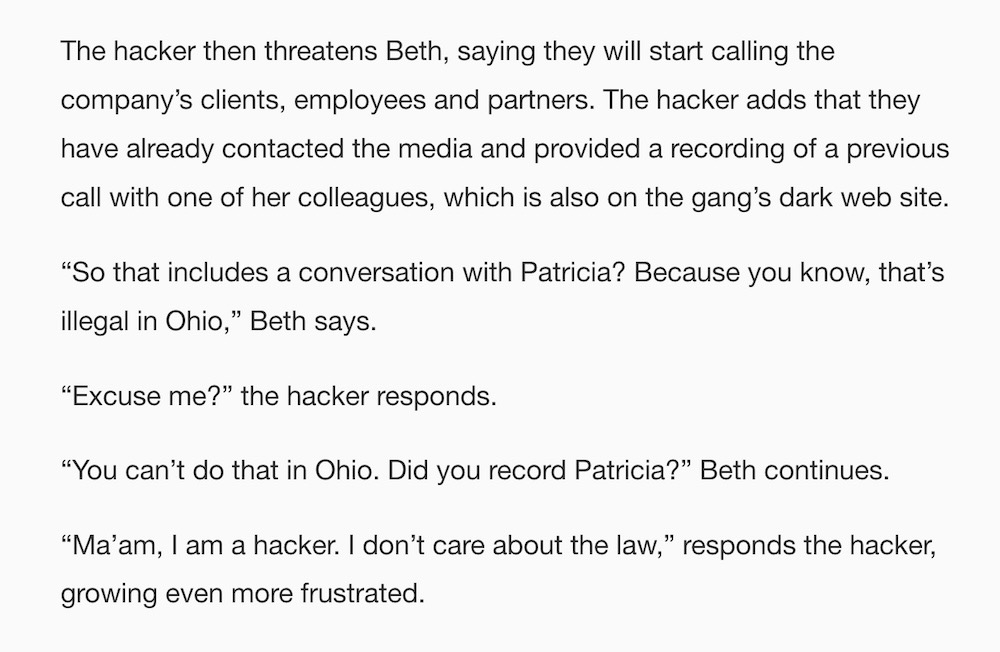
It's not often you get to be a fly on the wall in a ransom negotiation. But this week, a relatively new extortion gang called DragonForce published a phone recording of a negotiation in progress — in an attempt to pressure the company into paying. Instead, the effort failed — hilariously — thanks to Beth in HR, who was having absolutely none of it. If you need a pick-me-up, the full conversation is worth the read. Beth in HR is definitely the hero we needed this week.
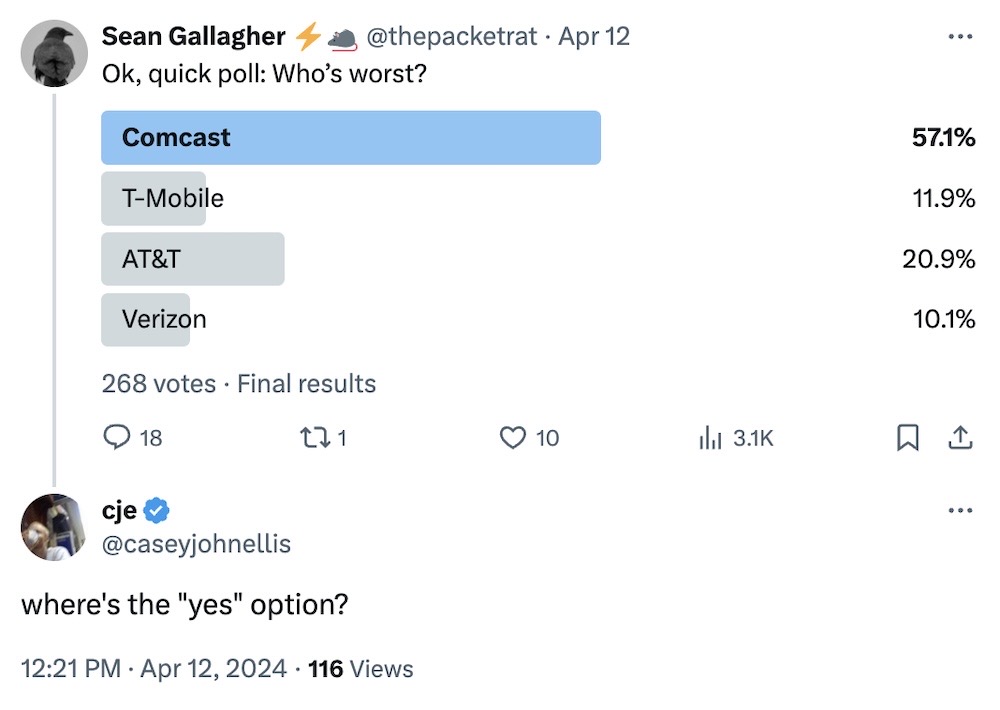
Anyone (read: everyone) with an internet provider can empathize with this.
Bonus cyber-bodega-cat, courtesy of @juliareinstein, and proceeds are going to a local good cause.
And finally. Did you see the eclipse? Turns out the eclipse saw you. The astronauts in the International Space Station were watching and took some incredible photos from the Earth's atmosphere. Almost looks like someone left a huge smudge on the camera lens... nope, that's just the shadow of a solar eclipse. (via @coreyspowell)

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Sir Tomas Puffington, who is carefully monitoring all attack surfaces. Doing vital work there, Sir Tomas! Many thanks to Anna L. for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
Aaaannnd that's it for this week's busy edition! Thanks for reading! As always, feel free to drop me an email with any suggestions, feedback, or anything else you want to send in.
For now, have a wonderful rest of your week — let's hope it's a quieter one!
Until next week
@zackwhittaker