this week in security — april 16 edition
THIS WEEK, TL;DR
Researchers out spyware maker QuaDream's iPhone exploits
Citizen Labs: Israeli spyware maker QuaDream has flown largely under the radar since its inception in 2016 when two former NSO employees founded the startup. Until this week, that is. Citizen Lab and Microsoft dropped detailed reports on how the spyware maker targets iPhones running (at the time) the latest iOS 14.4 software using malicious calendar invites. The victims weren't identified by name, but are said to be journalists, politicians and at least one NGO worker. QuaDream's spyware is used by governments, and sold via Cypriot firm InReach as to avoid Israeli export restrictions. A source told my TechCrunch colleague @lorenzofb that QuaDream is used by Saudi Arabia and Mexico, among others — the typical places with terrible records on human rights. Another reminder that NSO isn't the only spyware player out there. It's not a spyware story without @jsrailton tweets.
More: Microsoft | Washington Post ($) | Reuters ($) | TechCrunch | @lorenzofb | @tek
Discord member details how documents leaked from closed chat group
Washington Post ($): Hands up who hasn't posted classified information to the internet to show off to your internet friends? Jack Teixeira, put your hand down. Feds this week arrested the 21-year-old TS/SCI-holding air guardsman, who the U.S. government trusted to handle some of its most valuable and sensitive intelligence (let's not forget!). Teixeira is accused of posting top secret documents to a Discord server. Some of the docs he allegedly posted are detailed and, well, unsurprisingly quite revealing, given that they also include some rather embarrassing intelligence gathering on our allies. (Even allies spy on each other; the problem is getting caught doing it). The fallout from this leak will probably take some time to realize. But hey, what a fantastic time to have a big ol' congressional chat about the government's mass surveillance authorities! Bellingcat, the investigative journalist group, has covered the leak from the beginning.
More: NPR | BBC News | @postroz | @jennamc_laugh tweets | @drewharwell toots
CISA and partners issue secure-by-design principles for software makers
Fedscoop: Moving on from very leaky government to... government with a plan to stop a different kind of security problem. U.S. cybersecurity agency CISA has rolled out guidance urging software manufacturers to bake in secure-by-design and default principles into their products. The idea is to reduce the overall attack surface exploited by bad actors by making software more secure from the start (rather than tacked on at the end — which, by the way, doesn't work). MFA all the things! Log all the things! Let's just hope that America's tech companies actually listen this time. @jackhcable has more in the tweets.
More: CISA | SecurityWeek
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
New details suggest Oldsmar water treatment wasn't hacked
Cyberscoop: In 2021, officials in Oldsmar, Florida stood in front of the world's press to announce that hackers broke into the city's water supply system and changed the levels of lye, which could've poisoned local residents. Except, just one thing — that didn't happen, according to a rehash of the story two years on. It caught a fair number of reporters out (myself included). But the hack was, as it turns out, was a "non event" caused by human error that was resolved in about two minutes. First reported by GCN, it turns out that the sheriff who gave the initial press conference was just plain wrong.
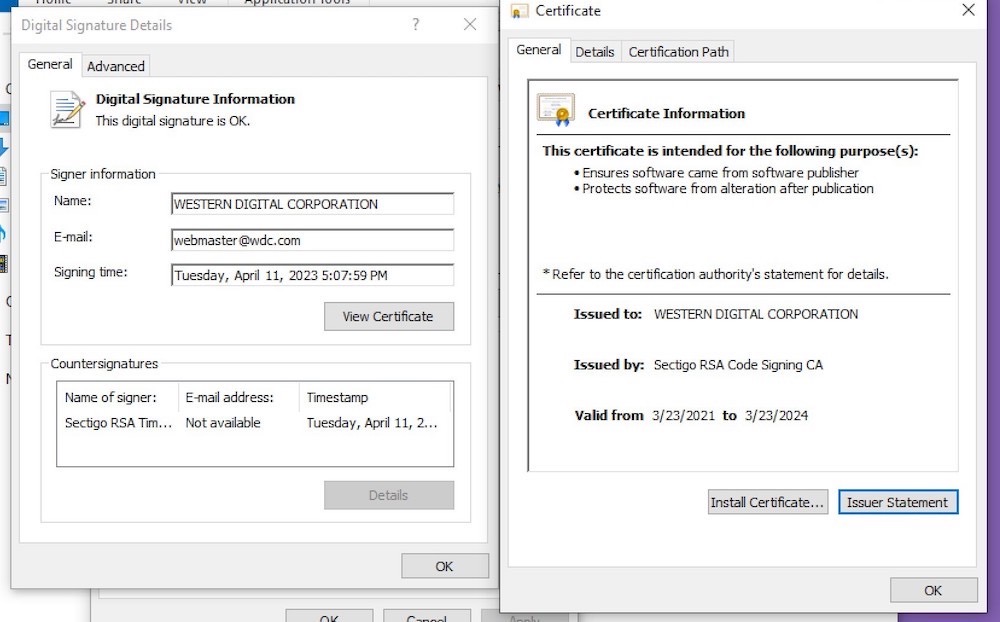
Hackers claim vast access to Western Digital systems
TechCrunch: Western Digital was hacked, spectacularly. Its customers' cloud storage is back up after a week of breach-related downtime. Western Digital described the outage as a "network security incident." But it seems like the hackers are still rooting around with vast access to the company's systems — including their ability to sign files and malicious code with a Western Digital code-signing certificate. At the time of reporting, the certificate had not been revoked. Bloomberg ($) reports that the stock dropped ~4% on the news.
Predator's control center has its roots in North Macedonian capital
Inside Story: Incredible reporting from Greek media, which found that authorities in North Macedonia, where spyware maker Cytrox is based, knew that the company was developing spyware but never delivered a license to authorize its production and sale. Cytrox (owned by Intellexa) develops the Predator spyware, used to target journalists and opposition lawmakers in neighboring Greece, likely at the behest of the Greek government, which denies its use.
Juice-jacking back in the headlines, but why?
Krebs on Security: It's the old cyber-fable that never ceases to go away. The FBI and FCC warned this week about "juice jacking," which claims your phone can be hacked by a malicious charging cable at airports. But as @dangoodin notes, there are no known cases of juice jacking. At all. (I know, I've asked before!) So what gives, exactly? It's not a completely unrealistic threat. OMG cables are a great example of keylogging cables that can be used for pen-testing and red-teaming. But surely nobody in their right mind would burn a zero-day on hacking a random person at an airport charging station. Still, even though modern smartphones block unwanted cable data connections, it's still good advice not to randomly plug your phone into untrusted cables, just like you wouldn't plug in a random USB stick from the floor into your production laptop.
~ ~
OTHER NEWSY NUGGETS
North Koreans hacked 3CX phone software: Mandiant linked a supply chain attack targeting enterprise phone maker 3CX to North Korean hackers, specifically a subgroup of the DPRK-backed Lazarus Group. 3CX disclosed the findings in a blog post this week. The group, known as UNC4736 or Labyrinth Chollima, is known for targeting cryptocurrency exchanges, since the North Korean regime uses stolen crypto to fund its nuclear weapons program. Kaspersky also linked the attack to North Korea, which reaffirmed the effort targeted crypto companies running 3CX's phone software. (via SecurityWeek, TechCrunch, 3CX)
Google patches Chrome with first zero-day of 2023: Update your Chrome browser (if you haven't already). A quick close and reopen should do it. There's a new zero-day under active exploitation targeting Chrome's V8 JavaScript engine. Google's Threat Analysis Group, which investigates nation-state hacks, discovered the bug. (via Bleeping Computer)
Montana's looming TikTok ban is dangerous a.f.: Montana is poised to become the first U.S. state to ban consumer downloads of the viral video sharing app TikTok. As @lhn deftly notes, the First Amendment exists precisely to protect against laws that do this kind of thing. "It's clearly unconstitutional," says @riana. Disagree with TikTok as much as you want, but banning an app at home sets a really dangerous precedent. Do you really want any government telling you which apps you can and can't download? The bill is now on the desk of Montana governor Greg Gianforte, whom you might remember from past incidents such as bodyslamming a journalist — in case you needed another example of what Montana's leadership thinks of the First Amendment. (via Wired ($), @lhn)
BBC reports from Ukraine's cyber front line: As Russia's unjustified war in Ukraine continues on, BBC's @joetidy traveled to Ukraine to interview hackers working to defend the country and how the conflict is rewriting the rules of cyber war. You can also watch Tidy's report on YouTube via his tweet thread. (via BBC News)
CISA has 'no confidence' in first responders' cell network: Cybersecurity agency CISA has "no confidence" that the cellular network used by first responders and the military, known as FirstNet, is secure against digital intrusions. That's in large part because epic bureaucracy prevents CISA and the NSA from seeing FirstNet's cybersecurity audits. AT&T, which operates FirstNet, isn't obligated to share the results of its cybersecurity audits with the federal government, even though it's as vulnerable to flaws — like SS7 exploits — as other cell networks. "Concealing vital cybersecurity reporting is simply unacceptable," wrote Ron Wyden, whose office dug this up. (via Reuters ($), @razhael)
Fake voices, real SWAT teams: Motherboard has traced a spate of swatting attacks to an account on Telegram, dubbed Torswats, which uses synthesized voices to trick police SWAT teams to storm specific locations with false claims. Brilliant reporting here. Dozens of schools have been targeted in recent weeks. (via Motherboard)
~ ~
THE HAPPY CORNER
Welcome to those who read from the bottom up. The happy corner is in bloom.
First, @k8em0's Luta Security is sponsoring four SWSIS scholarships of $5,000 for women pursuing undergrad or graduate degrees in cybersecurity or related fields.
Shout out to the BBC for this easter egg. (If you haven't heard of security.txt before, check it out — it's a really great project.)
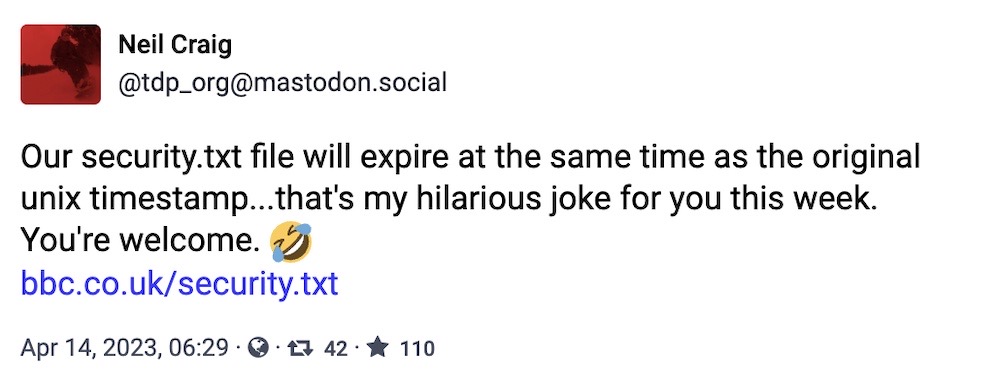
And finally this week, of all weeks.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this weeks two-for-one cyber cat special, Sumac and Yukai, who can be seen snuggling after a long day of threat hunting. Thanks so much to Max B. for sending in!

Keep sending in your cyber cats (or their friends). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for now. Hope you enjoyed this week's newsletter! As always, feel free to drop me an email with any feedback. I hope you have a great week, and see you next.
Toot, toot. Find me on the fediverse,
—@zackwhittaker