this week in security — april 18 edition
THIS WEEK, TL;DR
U.S. sanctions Russia for SolarWinds hacks
Washington Post ($): Get excited, folks. It's international sanctions week! *pfffrrhhpt!* The Biden administration has formally blamed Russia's foreign intelligence service, SVR, for the SolarWinds attacks, and imposed fresh economic sanctions to hold the Kremlin — and its enablers — accountable. @nakashimae laid out the sanctions and their impact, and has a good tweet thread on the basics of what went down. Several Russian intelligence were expelled from the U.S. in the process, and Cyber Command uploaded the malware samples used by the Russians to VirusTotal. It was long suspected that the SVR was involved in the SolarWinds supply chain attack, which resulted in at least 9 federal agencies getting hacked, along with hundreds of private businesses. (It was also reported this week that six EU institutions were also hacked as part of the SolarWinds attack.) But Biden dropped the sanctions with an olive branch to the Russians, since the two superpowers will have to work on some things together — whether they like it or not.
More: NSA | Treasury | U.S. Cyber Command | The Record | @gordoncorera
The untold story of the SolarWinds hack
NPR: @NPRDina is back with a deep dive on how the SolarWinds attack happened, with fresh new details. It's well worth the read. This week also saw sanctions dropped against Russian tech companies for their alleged involvement with the Russian government's activities. By far the highest profile is Positive Technologies, which denied the U.S. allegations made against the company. Positive had early-access to vulnerability information from Microsoft, according to an AP report, which Microsoft has now revoked access. MIT Technology Review ($) did a great explainer on Positive. The U.S. also charges that Russia's FSB was working with Evil Corp, a cyber-criminal group known for phishing attacks and using ransomware, as well as disinformation groups like InfoRos and NewsFront, which Facebook took down from its platform in April 2020.
More: Forbes | Associated Press | MIT Technology Review
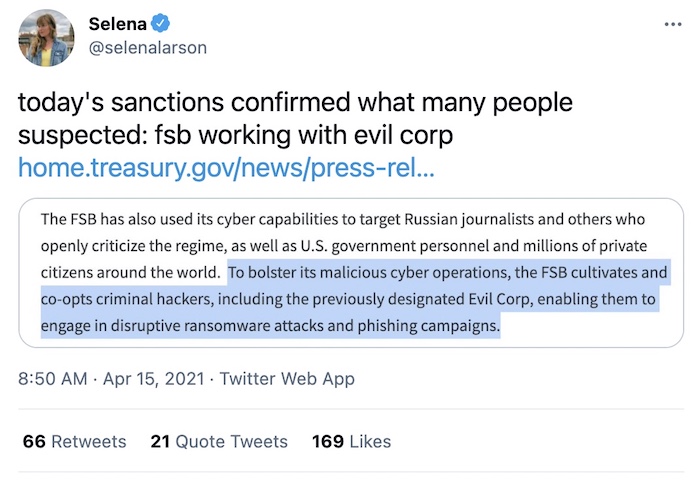
FBI accesses computers around the U.S. to delete Microsoft Exchange hacks
Motherboard: The old Reagan saying, "I'm from the government, and I'm here to help," became reality this week when the Justice Department obtained a court order to remotely break into hundreds of private Exchange servers around the U.S. to remove the backdoors left behind by China-backed hacking group Hafnium. The number of servers backdoored by Hafnium had reduced from thousands to hundreds but still posed a threat to U.S. networks, the DOJ said. It's not the first time the government's taken offensive action to clean up an active threat — the U.S. has taken action against a few botnets over the years (like Coreflood). @pwnallthethings has a really good thread on how this court order came to be (fun for Rule 41 nerds).
More: Justice Dept. | TechCrunch
NSA helps out Microsoft with critical Exchange Server vulnerability disclosures
The Register: Oh we're not done with Exchange yet. Microsoft's Patch Tuesday this week saw over a hundred fixes, including four vulnerabilities reported by the NSA to fix flaws in Exchange servers. These are pre-authentication remote code execution bugs — so no passwords needed.
More: MSRC | @ryanaraine tweets | @olivia_gazis tweets
Iranian nuclear plant sabotage likely meant to permanently damage centrifuges
The Intercept: Fascinating report by @kimzetter this week on the attack at the Natanz uranium enrichment facility in Iran. Israel is suspected of carrying out the explosion, which caused a blackout, likely aimed at disrupting the centrifuges used to enrich uranium for use in nuclear weapons. The debate is still out on whether cyber had anything to do with the incident. But Zetter's read on how the attack happened, and why, is fascinating — especially when revisiting the Stuxnet cyberattack in 2009 and 2010. You might not know anything about uranium enrichment before but you'll certainly understand the events better — and why it matters — after reading this.
More: Zero Day (Substack) | BBC News
A little-known Australian firm broke into the San Bernardino shooter's iPhone for the FBI
Washington Post ($): It's a two-scoop week for @nakashimae, who with her colleague @reedalbergotti finally revealed who broke into the San Bernardino shooter's iPhone for the FBI, Australian firm Azimuth Security. We knew long ago that it wasn't Cellebrite, as many had claimed, and we also knew the price, thanks to Sen. Dianne Feinstein just reading it out on the Senate floor. I won't spoil the story, but it's a fantastic read — and the ending may make you feel slightly better about the situation. @josephfcox also confirmed the reporting.
More: @nakashimae tweets | @ReedAlbergotti tweets
Parents were at the end of their chain — then ransomware hit their kids' schools
NBC News: Parents are already struggling with school during the pandemic, and ransomware attacks against schools are only making matters worse. The latest victims are Buffalo's schools in upstate New York, held ransom for $40 million. @kevincollier walks through this latest attack, and how the attackers operate — including rarely seen correspondence between the ransomware group and the victim — but also the effects these attacks have on ordinary families and the kids who attend school.
More: @asankin
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.S. investigators probing breach at code testing company Codecov
Reuters: Federal investigators are probing an intrusion at San Francisco-based Codecov after attackers broke in and tampered with its software, which is used by some 29,000 customers across the tech industry to help test code for security flaws. The immediate ramifications aren't clear but fears are that it could lead to a similar knock-on effect as the SolarWinds breach. The attack was only detected this week, months after the intrusion in January. This is probably going to be a story to watch...
Zerodium is offering $300,000 for WordPress exploits
SecurityWeek: Zero-day exploit broker firm Zerodium said in a tweet that it's offering $300,000 for remote code execution (RCE) bugs for a clean install of WordPress with no plugins, up threefold from its usual asking price. Prices usually vary depending based on supply, suggesting WordPress zero-days are in high demand. Just goes to show how far WordPress security has come in recent years.
You can't hide whether you're online on WhatsApp
Motherboard: You can't hide your online status on WhatsApp and that's a problem because this leaves the door open for stalkers. Cybersecurity company Traced published research showing how easy it is to see if someone is online on WhatsApp or not. Several apps and websites exist that allow people to enter a WhatsApp number and check. WhatsApp investigated and blocked the accounts associated with one website, and the person sent a cease and desist notice — but only after Motherboard's story went out. (Makes you wonder if Facebook only cares about optics and not actually protecting users?)
EU poised to set AU rules that would ban surveillance scoring
Bloomberg ($): The EU is readying a ban on AI systems for using mass surveillance or ranking social behavior, and will impose fines up to 4% of a company's global revenue if they don't comply. The proposal will ban remote biometric identification systems used in public places — like facial recognition — and would require special authorization from the authorities. But the ban won't apply to AI systems used for the military, so killer drones aren't going anywhere any time soon.
FIN7 'technical guru' sentenced to 10 years in prison
Cyberscoop: Fedir Hladyr has been sentenced to ten years for his role as the admin for a multi-billion dollar crime group, FIN7. Hundreds of firms were breached by the financially motivated group, which prosecutors now say caused losses between $3 billion and $5.7 billion. Ouch.
~ ~
OTHER NEWSY NUGGETS
Estate agent's hi-tech house tour exposes personal data
Well this is awkward. A realtor in the U.K. apologized after a 3D tour of a Devon house was put online with a "substantial amount" of personal information visible, including financial paperwork. The 3D tour was pulled offline and the U.K. data protection authority alerted. "Other identifiable data about the home-owners in the property included the names of their pets on a photograph (pet names are commonly used as passwords), clues about their political views based on their choices of reading material, and their health — an asthma inhaler was visible in one of the bedrooms." Yikes.
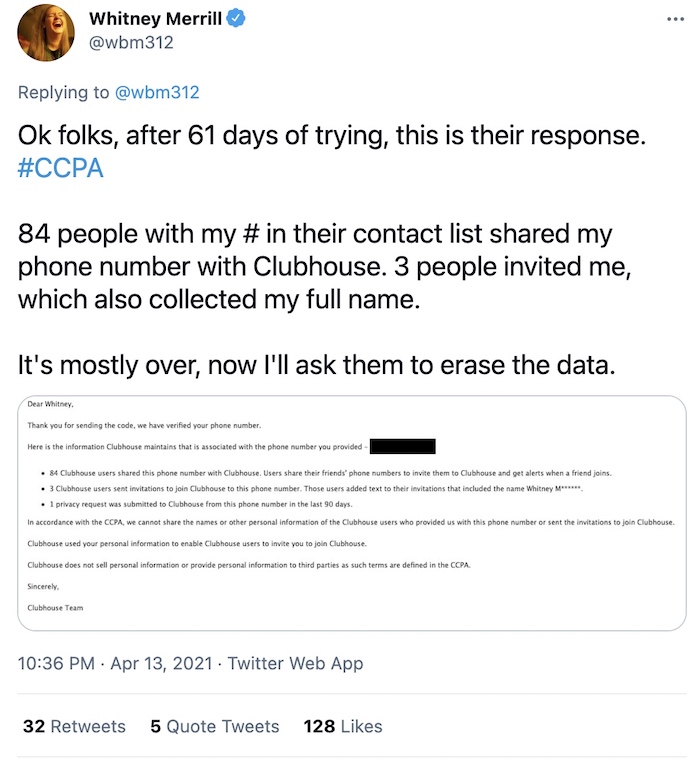
Clubhouse finally responds to a months-long CCPA request
Good news. Clubhouse finally responded to @wbm312's request under California's CCPA. It only took two months (and persistence). Merrill has a full thread on how she got Clubhouse to disclose the data it has on her, even though she isn't a user.
Risk startup LogicGate confirms data breach
LogicGate, which helps companies to identify and manage their risk and compliance with data protection and security standards, had a data breach. But unless you're a customer, you likely didn't hear about it. An attacker took the company's AWS keys and decrypted customer backup files. CEO Matt Kunkel confirmed the breach, but wouldn't say when (or even if) it had informed U.S. or EU authorities about the breach as required by law. "We believe it’s best to communicate developments directly to our customers," he told me. GDPR seems to think differently... (Disclosure: I wrote this story.)
ParkMobile breached, license plates and mobile numbers of 21 million users taken
ParkMobile, a mobile parking app, had a data breach, exposing the personal data of 21 million users, including cell numbers and license plate numbers — and, in some cases, mailing addresses. Gemini Advisory reports that the data is for sale on a Russian-language crime forum.
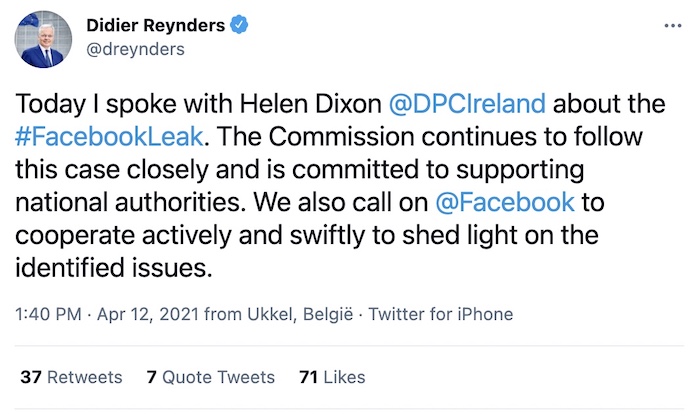
Ireland opens GDPR investigation into Facebook leak
Facebook is back under investigation by the Irish data protection commissioner for potentially breaching EU's GDPR reporting rules by not disclosing that 533 million Facebook users' data had been scraped. It comes after multiple reports of Facebook phone numbers, scraped from the site, circulating around the web in recent weeks. Companies that flout GDPR can be fined up to 4% of their global annual revenue.
~ ~
THE HAPPY CORNER
Welcome to this week's ~this week in security~ for the people who read this newsletter from the bottom-up. Who doesn't want to read the good news first?
First up, @swiftonsecurity wins Twitter this week with this incredible thread on the biggest IT fails. My favorite (though there were several):
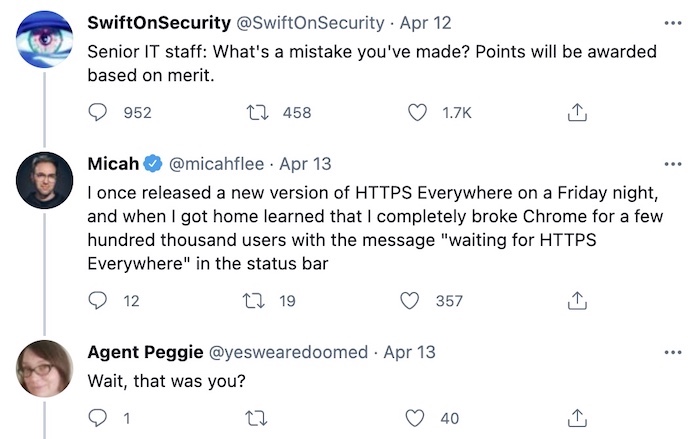
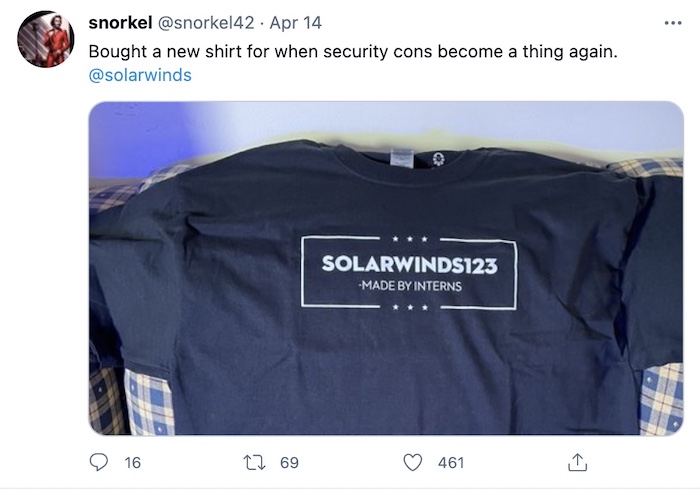
And, SolarWinds' CEO is never going to live this down. (Which, by the way, you should really read this week's big NPR story since it pours cold water on the password claim.)
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
Meet Belle, this week's cybercat. Who can resist this advanced purr-sistent threat? Many thanks to Belle's human, Nicolas, for the submission!

Please keep sending in your cyber cats (and their friends)!. You can drop them here, and feel free to send updates on previously-submitted friends!
~ ~
SUGGESTION BOX
That's it for this week. You can always drop any feedback you have in the suggestion box. Take care, and see you next week.