this week in security — april 2 edition
THIS WEEK, TL;DR
U.S. restricts federal agencies from using commercial spyware
Associated Press: Rare to start with good news, but here we are. The Biden administration signed an executive order effectively blocking U.S. federal agencies from using commercial spyware, which is created by the private sector and exclusively sold to governments. The U.S. said it was sounding the alarm on spyware — the kind that breaks into a target's phone using undisclosed vulnerabilities to steal data — since it has been used to target Americans and U.S. personnel. That includes some 50 U.S. federal workers stationed overseas, more than what was previously known. It's not an outright ban — since the U.S. has tested spyware before and won't 100% rule out using it in limited circumstances. Though no public ban list will be published, the U.S. is taking aim at Pegasus, Predator and Candiru-style spyware that relies on zero-days that violate human rights. That does leave open the possibility of the U.S. using spyware that's not known to violate human rights. But it's a start. Citizen Lab's @jsrailton has more in a thread.
More: White House | Washington Post ($) | Wall Street Journal | CyberScoop | Reuters ($)
Spyware vendors use zero-days to target iPhones, Android users
Google Threat Analysis Group: Well, speaking of spyware... Google's security researchers said this week that they have found two spyware operations targeting iPhone and Android users in "limited and highly targeted" campaigns. The vendors aren't known (but can probably be guessed) — given that one of them is using links to a malicious landing page that look identical to Spanish spyware maker Variston's. That spyware was being used to snoop on people in the United Arab Emirates, and includes a full exploit chain for Samsung's native browser to hack victims. The other campaign that seems to use the same exploit as Predator maker Cytrox (but not yet confirmed).
More: TechCrunch | CyberScoop
Supply chain attack hits 3CX desktop apps, used by millions
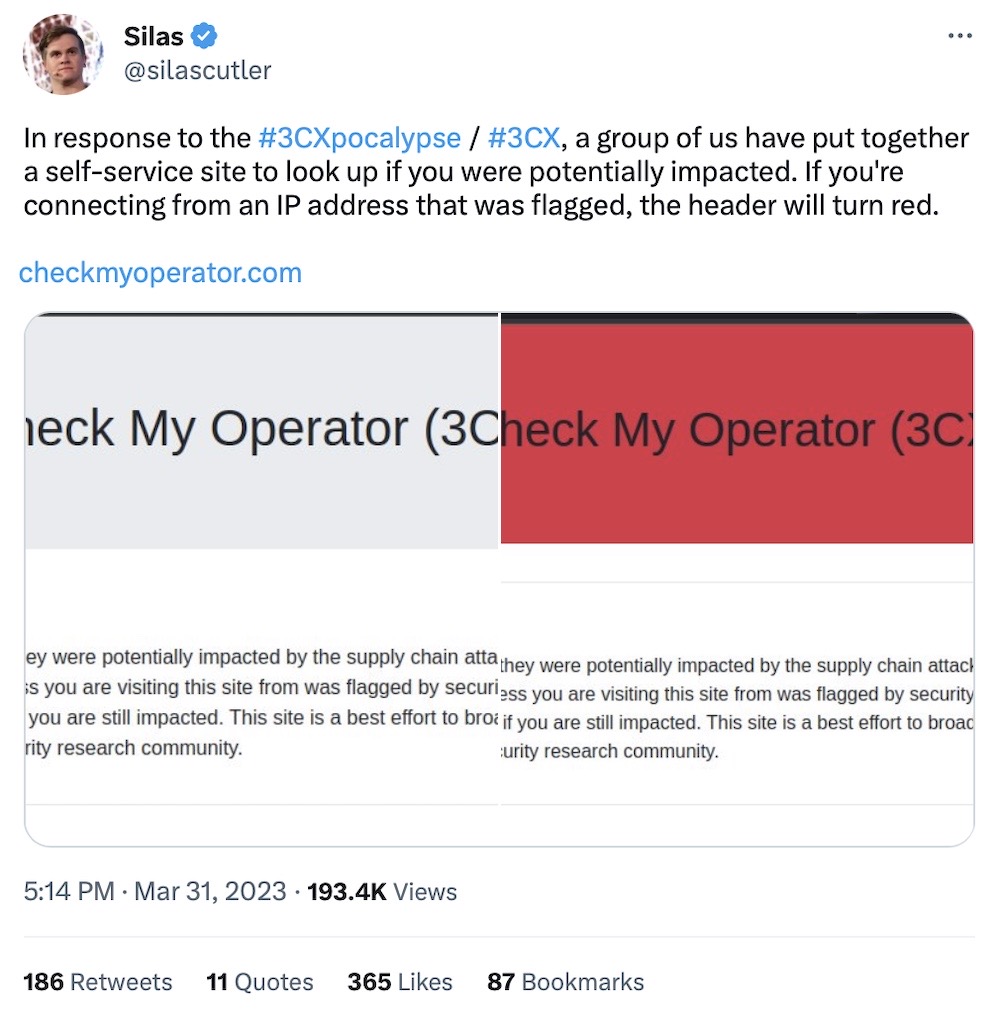
SecurityWeek: A broad supply chain attack is hitting 3CX customers around the world. Earlier this week, security companies flagged 3CX's trojanized software as malicious. The maker of VoIP software and hardware didn't acknowledge their apps had been compromised — in some cases outright dismissing the alerts — for almost a week. Both its Windows and macOS Electron-based desktop clients were compromised with malware and signed by the company — suggesting the hackers broke into 3CX's internal systems during the development process. A subdivision of North Korea's state-backed Lazarus Group hackers is blamed for the attack. 3CX has some 600,000 customers, including Mercedes Benz and PWC. Luckily, @silascutler and others have a new website set up to alert you if you're connecting from an IP address that was flagged as compromised.
More: 3CX | Volexity | CrowdStrike (Reddit) | Objective-See
'Insanely broad' RESTRICT Act could ban much more than just TikTok
Motherboard: There is some bipartisan support for a new bill in Congress dubbed the RESTRICT Act, which, as the name suggests, would restrict access to technologies with links to foreign governments — like TikTok. Yes, it's a TikTok* (*and everything else) ban, according to experts who read the thing, even though it doesn't explicitly name TikTok. The White House seems to support the bill (which makes sense!) because the bill would allow the Commerce Secretary to ban or force a sale of pretty much any technology that is deemed a risk to U.S. national security. That includes... a lot of things. VPNs, apps, or any other app that people rely on security and privacy. And it still doesn't stop anyone overseas from buying Americans' data from U.S. data brokers. Sigh. I'm starting to think that the lawmakers are actually very much part of the problem here... It turns out that ignorance isn't bliss. It's just ignorance.
More: Lawfare | Electronic Frontier Foundation
Android app from China executed zero-day exploit on millions of devices
Ars Technica: What is this, zero-day week? Remember a couple of weeks ago when Google flagged Chinese e-commerce giant Pinduoduo's app as malware? Per Ars: "Android apps digitally signed by China’s third-biggest e-commerce company exploited a zero-day vulnerability that allowed them to surreptitiously take control of millions of end-user devices to steal personal data and install malicious apps." New findings suggest the incident could have been anything from a supply chain attack, a leaked key obtained by an outsider, the work of an insider, or the intentional distribution of malicious code by internal staff. Pinduoduo has some 800 million users, so the removal of its app from Google Play — given some of its non-Play distributed apps were compromised — seems like a solid precaution given the circumstances.
More: Bloomberg ($) | @lukolejnik
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Contract shows FBI bought mass internet data
Motherboard: The FBI previously purchased access to "netflow" data from Team Cymru, which obtains the data from ISPs in return for threat intelligence but also sells that data to the government. Netflow data collects metadata on traffic as it flows across a network device, which can be used to identify a hacker's infrastructure, but potentially also tracking traffic through private networks, like VPNs. Remember, the FBI is supposed to get a warrant for this data, but increasingly purchases it to get around that requirement.
Twitter obtains subpoena forcing GitHub to unmask source-code leaker
Ars Technica: GitHub has until April 3 — so, tomorrow (if you're reading this Sunday) — to provide details on a user called "FreeSpeechEnthusiast," who published portions of Twitter's source code months ago but was only recently noticed. Twitter, once a defender of free speech and expression under previous management, asked a California court to issue a subpoena to the Microsoft-owned GitHub to identify the leaker, which the court approved. GitHub removed the code but hasn't yet provided details of the leaker to Microsoft. It'll be interesting to see if it does, especially given how much Twitter's current owner claims to care about "free speech" (air quotes emphasis).
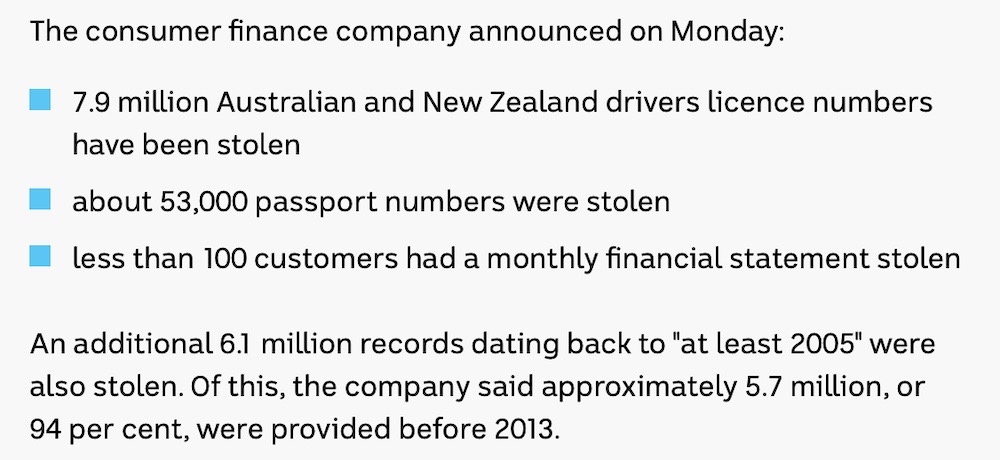
Australia's Latitude Financial hacked with millions of records stolen
ABC News Australia: Millions of records have been stolen from Latitude Financial, one of Australia's biggest financial institutions. Close to 8 million drivers license numbers and 53,000 passport numbers were stolen on Australians and New Zealand residents. Some of the data goes back to at least 2005. The hack was announced on March 16, which massively underestimated how many people were initially affected as ~330,000 customers.
Meet North Korea's APT43, a hacker group dedicated to cybercrime
Mandiant: You know what the North Korean regime loves more than nuclear weapons? Doing cyber crimes to steal money to invest in nuclear weapons. That's basically the modus operandi of APT43, a newly doxed state-backed hacking crew that engages in cybercrime — the theft of cryptocurrency, mostly — to fund their espionage operations with the end goal of funding its nukes.
How North Korean hackers netted $14m in two hours by ATM jackpotting
BBC News: Speaking of North Korea... Here's a detailed story about how North Korean hackers pulled off a daring (arguably impressive) 2018 hack involving an ATM "jackpotting" attack, where ATMs are effectively emptied by spitting out cash. The heist was pulled off in part by the hackers breaking into a bank's systems. There was just one problem: one thing they couldn't change was the amount they could withdraw, and so the hackers needed people to physically take money out of the ATM. That's when the hackers recruited some people as "movie extras."
Samsung fixes Exynos zero-days discovered by Google
Android Authority: Exynos-powered Samsung phones will soon get patches for remotely exploitable flaws, discovered by Google in March. Samsung downplayed the bugs but said the fixes will land in Samsung's April security updates, expected soon. But as others have noted, Samsung hasn't fixed all the disclosed bugs just yet.
Children’s data feared stolen in Fortra ransomware attack
TechCrunch: The Fortra mass-ransomware attack continues to widen after the hackers responsible claimed a new victim: children's virtual mental health care startup Brightline. The Clop ransomware gang says it will leak the stolen data from Brightline "soon." Brightline has yet to acknowledge the incident. News only came to light after its partner, healthcare giant Blue Shield, disclosed that some 63,000 individuals had data compromised in the breach.
~ ~
OTHER NEWSY NUGGETS
Exchange Online to block emails from vulnerable on-premise servers: Microsoft is moving to make it more difficult for vulnerable, on-premise Exchange email servers to send email to healthy Microsoft-hosted Exchange Online servers. The idea is to push on-premise customers to patch to the latest, up-to-date versions of Exchange following a spate of attacks targeting legacy systems in recent years. In the end, Exchange Online won't accept incoming emails from vulnerable servers. (via HelpNetSecurity, Microsoft)
Online voting provider paid for academic research to sway lawmakers: Reporting by @yaelwrites found that Democracy Live, a maker of online voting systems known to contain security flaws, made the case to lawmakers that online voting is safe. (Pretty much every election security expert will tell you that no, it's not.) Democracy Live cited a letter from academics supporting their case. But the company didn't disclose that one of the people who signed the letter was a paid consultant for Democracy Live and another was a university employee previously paid by Democracy Live for work leading up to the letter, including an unpublished study. Incredible reporting here. (via CyberScoop)
Secret trove offers rare look into Russian cyberwar ambitions: A consortium of journalists got their hands on thousands of documents leaked from a Moscow-based contractor NTC Vulkan, which works with Russian intelligence agencies to launch cyberattacks and conduct surveillance. The files also offer a rare glimpse into the work of notorious Kremlin-backed hacking group Sandworm, responsible for at least two widespread power grid outages in Ukraine in recent years. Sekoia also has a run-down of what's in the files. One of the consortium's reporters, @hatr, discovered why one of the files had a reference to APT Magma Bear. A name given by CrowdStrike, perhaps? Apparently it was just a joke by the creator of the file itself. Just breathtakingly good research and journalism here. (via The Washington Post ($))
Capita outage fuels fears of breach: Another classic case of an unspecified outage sparking fears of a cyberattack. This time it's Capita, an outsourcing group that supports U.K. councils, the military and the National Health Service. Capita staff were unable to access IT systems on Friday, including their own email. It's not clear if the outage is resolved, or what caused the outage. Capita is one of the U.K. government's biggest outsourcers, and runs call centers for a ton of businesses, including cell carrier O2, car giant BMW and water supplier Thames Water. One to watch, I assume. (via The Guardian)
India looking to solve its Pegasus "PR problem": India is looking for a new spyware it can deploy that has a "lower profile" than Pegasus, developed by NSO Group and currently effectively banned from doing business in the United States. India hasn't ever confirmed it's a Pegasus customer, though the spyware has been found on phones belonging to journalists, academics and opposition political leaders around India, and since NSO only sells to governments... you can probably put two-and-two together. A dozen rival firms are reportedly seeking the government contract worth $120 million, aka India's "PR problem," as it has been described. (via Financial Times ($))
~ ~
THE HAPPY CORNER
Hello, welcome to the happy corner. A mish-mash of fun from the week.
If you, like me, are wondering why @matthew_d_green was sent a huge box shipped from Vietnam, look no further. See, blockchain can be useful for some things, especially apparel.
Meanwhile:
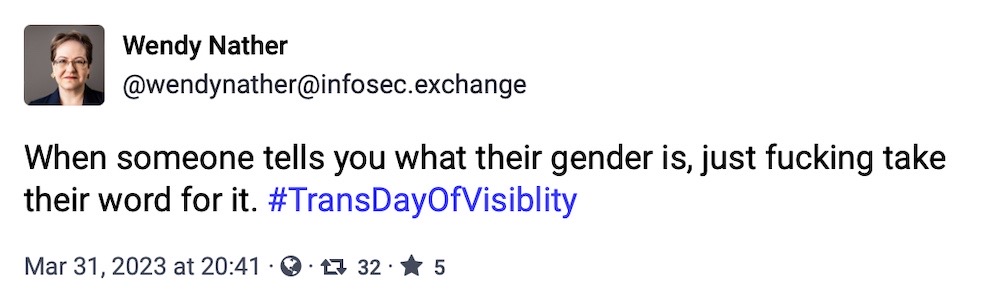
And finally, this week. Hope everyone had a great Trans Day of Visibility this Friday, a day dedicated to celebrating and recognizing trans folk around the world. 🏳️⚧️
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Akasha, this week's cyber cat. He's a very handsome one-year old stray. His contributions to cybersecurity include closing his human's work laptop then laying on it and absorbing the heat. If they fit, they sit. Many thanks to Ryan S. for sending in!

Keep sending in your cyber cats (or their friends). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for now! A busy one. My email is open if you want to get in touch. I'm off to grab some breakfast. If you enjoyed this week's newsletter, please share with a friend!
Same time next week, friends.
—@zackwhittaker