this week in security — april 20 2025 edition
THIS WEEK, TL;DR
Whistleblower describes how DOGE may've taken sensitive federal data
NPR: We start this week with absolutely belter reporting from NPR's @jennamclaughlin on a whistleblower's report from within the IT department of the National Labor Relations Board (NLRB), who provided revelations about DOGE's activity at the agency to federal and congressional investigators. My blurb here just isn't going to do the story justice; you have to read it through (or however you want to consume). This is ultimately a story about DOGE as an insider threat, not just at an agency that has gobs of data capable of holding powerful billionaires accountable for their oft-terrible actions. A big charge is that DOGE exfiltrated sensitive data from the agency (for reasons as yet unclear), while disabling logs, designing backdoors, and potentially exposing attempts by a Russian-based IP address to login to the NLRB's systems. It's not clear where the exfiltrated data went in the end or who has access to it, but from a workers' rights perspective, the threat is "immediate and existential." Meanwhile: remaining staff at the U.S. Defense Digital Service, which built fast tech fixes from inside the Pentagon, plan to resign this month en masse, effectively shutting down the decade-long program.
More: NPR | NBC News | Reuters ($) | @jennamclaughlin

Chris Krebs vows to fight Trump's federal investigation
Wall Street Journal ($): Former CISA director Chris Krebs is leaving SentinelOne to fight back against the Trump administration's federal investigation into him (and others), amid the ongoing use of the executive branch to retaliate against Trump's critics and opponents. The WSJ had the scoop; SentinelOne confirmed in an updated statement, which didn't exactly (or explicitly) throw its support behind him. The response from the cyber industry (read: wants to make money) was largely silence vs. the cyber community (read: wants to make the world better) which was far more vocal, and journalist Brian Krebs (no relation) does a grand job of breaking down what's happening. But as some are noting, if not to speak up now, then when? The massive chilling effect on cyber at very least has the potential to be huge — then, who's going to be targeted after Krebs?
More: Chris Krebs LinkedIn post | Luta Security | KrebsOnSecurity | Rud.is | Cyberscoop | Forbes ($)
CISA funding chaos threatens future of vulnerability database
Wired ($): Moving on from governme....oh come on. OK, let's keep this brief. Hours before the all important CVE Program's federal funding was about to expire, CISA jumped in at the last minute to save the day with a funding reprieve... sort of... not before a somewhat organized panic scramble resulted in offshoot efforts to save the all important CVE database of disclosed security vulnerabilities. One of those that popped up includes the new CVE Foundation, which aims to "secure the future" of the program. The whole "will it/won't it shut down" this week was a reminder of how important tracking vulnerabilities is for its relatively small cost (of about ~$30 million), but that these days the federal government won't necessarily help for the long term. Thousands of security bugs are discovered every year and noted in the CVE database, but a long-term and stable funding solution still hasn't been found.
More: Nextgov | The Register | Reuters ($) | Bleeping Computer | @k8em0 | @jgamblin | @ddimolfetta posts
CISA warns of security fallout from Oracle Cloud breach
CISA: Just kidding, because whoever is still left at CISA (amid further reported cuts) put out an alert this week seemingly to handle Oracle's scandal (since the company is doing a two-thumbs up fantastic job of it /sarcasm) warning that companies who rely on Oracle's Cloud should take action because Oracle clearly isn't. Oracle has steadfastly denied a breach of its cloud... until it couldn't any longer... but even then is more interested in protecting its own reputation (which, I know, I wrote that and laughed) than helping its customers remediate from downstream bad-times. "The nature of the reported [Oracle] activity presents potential risk to organizations and individuals," writes CISA. If you haven't taken action, now would be a really good time. CISA has some advice for both organizations and end-users.
More: Cybersecurity Dive | The Register
~ ~
THE STUFF YOU MIGHT'VE MISSED
TLS/SSL certificates will be limited to 47 days in 2029
Digicert: CA/Browser Forum, a body of web browser makers and TLS/SSL certificate providers, have voted to cut the maximum lifespan of newly issued TLS/SSL certificates to just 47 days by mid-March 2029. The argument was that shorter lifespans will limit the abuse of stolen certificates, which can be used to impersonate websites and online services. The Register has some extra yarn for context.
Silicon Valley crosswalk buttons hacked to imitate Musk, Zuckerberg, Bezos
TechCrunch: A handful of those audio-enabled traffic crosswalk buttons across Silicon Valley were hacked to include AI generated voices to sound like billionaire bosses Elon Musk, Mark Zuckerberg, and Jeff Bezos. All signs point to hacktivism, and default passwords — yes, in the year of 2025. (Disclosure: I wrote this story!) More also from Palo Alto Online, plus @deviantollam explainer.
Android devices will self-restart for security
Android: Per Google's latest release notes, Android devices will receive a security update that will self-restart devices after three consecutive days of non-use. The idea goes that phones locked from boot-up are more difficult to crack into than phones that have been unlocked by the user at least once. Apple rolled out a similar feature for iPhones and iPads some months ago. 9to5Google explains a little about how this feature works.
23andMe bankruptcy draws congressional probe over data fears
The Record: U.S. House Oversight lawmakers are looking into the bankruptcy proceedings of 23andMe, the failed genetics testing firm that lost control of literal gobs of data in 2023 during a massive breach. The fears include a sale of genetic and DNA data to China, or other adversarial nations, and may ultimately prompt a national security review, per Bloomberg ($). As for what the lawmakers plan to actually do (if anything) remains to be seen.
~ ~
OTHER NEWSY NUGGETS
Internet's dumpster fire hacked: 4chan, one of the grossest corners of the internet, was hacked and much of the online forum remains offline. Internal data was leaked, including IP addresses about ostensibly anonymous users and email addresses of moderators and "janitors." Predictably, the hack itself became a meme. One janitor confirmed to TechCrunch that the data appears real. (via Wired ($) | Daily Dot)
New Apple zero day under attack: The fruit-themed tech giant rolled out fixes for two zero-day bugs, which Apple says may've been "exploited in an extremely sophisticated attack against specific targeted individuals on iOS." But because the bug is in CoreAudio, an audio component used across various Apple platforms, a bunch of other products are affected — including Macs, Apple TVs and Vision Pro headsets. No idea who's behind this particular campaign, except to note that Google's researchers focused on investigating government-backed threats discovered the bug... so, go figure. (via Apple)
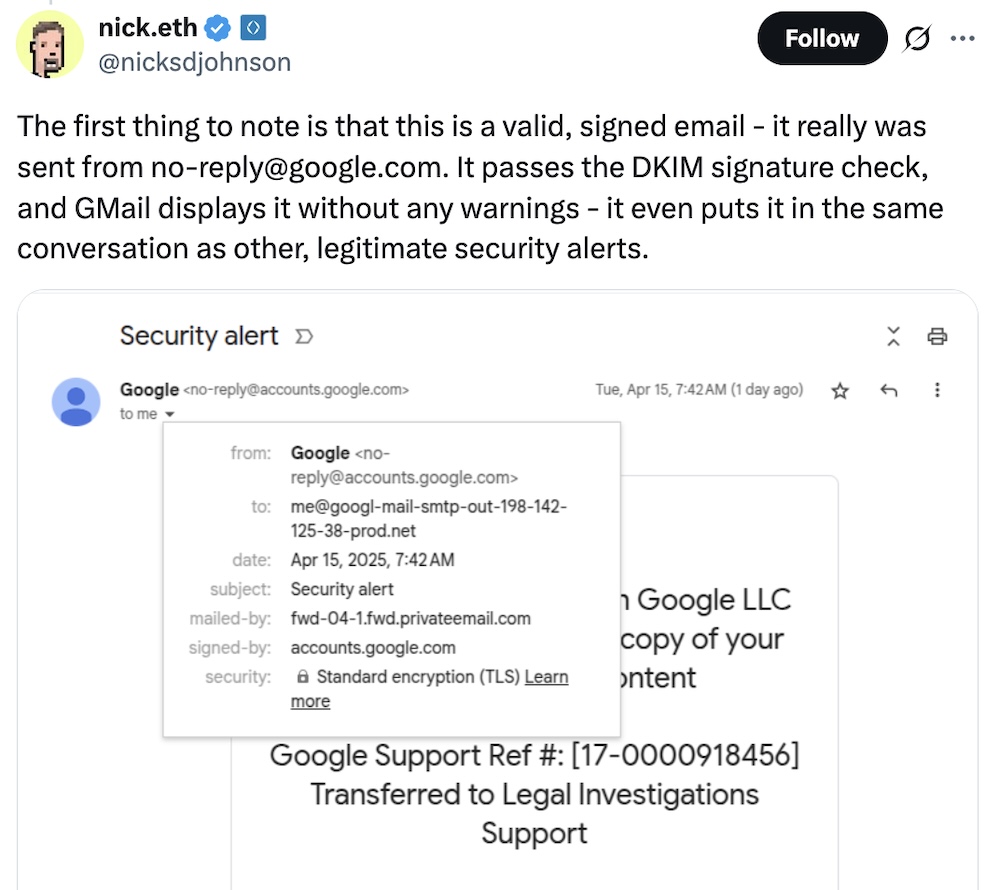
Google subpoena? Nope, sneaky phish: Here's @nicksdjohnson disclosing what looks like a very smart, advanced phish that relies on tricking an unsuspecting victim into thinking Google was notifying them about being subpoenaed for account information. Even though the email was cryptographically signed as coming from Google itself, it's actually an attempt to steal Google account credentials. Good threat thread here. Google reportedly plans to fix the issue on its end at least. Be careful out there! (via @nicksdjohnsom, EasyDMARC)
EFF blasts Florida anti-encryption bill: Florida state senators voted 21-0 to advance an anti-encryption bill for a Senate floor vote, which — if passed — would allow law enforcement in Florida to demand access to a user's social media account with a subpoena (which are issued by police and usually aren't signed by a judge, unlike warrants). The bill was presented under the guise of child safety, but the EFF blasted the bill as "dangerous and dumb." Personally, I think any lawmaker who advocates for encryption backdoors should first be required to open up their own devices and online accounts for inspection. (via TechCrunch, Florida Politics)
Bags o' breaches: Round up, round up, we've got breaches to blast through. Govtech giant Conduent finally confirmed hackers exfiltrated data from its systems during a January cyberattack. Car rental firm Hertz also reported a breach that included customers' personal information, driver's license data, and payment card information, affecting at least 100,000 people (but allegedly not millions, per a spokesperson). Insurance firm Lemonade confirmed that a bug on its website exposed driver's license numbers. And, live events company Legends International said thousands of employees and customers had personal data stolen, including Social Security numbers and more. (via StateScoop, The Record, SecurityWeek)
~ ~
~ ~
THE HAPPY CORNER
Rejoice! It's the happy corner. Only good vibes here on out.
That moment when you realize you actually have quite a lot in common with the Linux kernel.
A much-needed bonus cybercat after a stressful week in the world.
And lastly, this week, some wise words from Skeletor.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber-cat-kitten special is Westley (gray) and Princess Buttercup (white and gray), who are incredibly cute but you might not think that when you realize they swiped your passwords and your Social Security number... oh, and your car keys for good measure. That's some effective cyber-catting! Thanks so much to Sean K. for sending in!

Send in your cybercats or non-feline friends! You can email at any time with a photo and name of your cyber cat (or friend) and they'll be featured in an upcoming newsletter. If you've sent in before, you're welcome to send in an update!
~ ~
SUGGESTION BOX
That's it for a busy week in... well, pretty much every direction. A very happy Sunday to you, and hope you have a great rest of your week.
Please drop me a note by email if you have anything you want including in next week's edition. And if you missed the survey, I'd love any feedback you can share!
Diving back into cyber land,
@zackwhittaker