this week in security — april 21 edition
THIS WEEK, TL;DR
Senate votes to reauthorize and expand Section 702 of FISA
The Verge: And that was that. After years of bickering and even more years of warnings from privacy and civil rights advocates, both the U.S. House and Senate passed bills reauthorizing the controversial surveillance law known as FISA. The law, which now heads to the President's desk, expands the definition of an "electronic communications service provider," vastly broadening who can be compelled to surveil for the government. Efforts to amend FISA with privacy protections for Americans whose communications "inadvertently" (heavy wink) get caught up in the foreign-targeted collection ultimately failed, with Democrats and Republicans both ramming through the bill into law past midnight early on Saturday morning. So late, in fact, that the law technically expired for a hot minute — not that it really meant anything, since the annual certification that the feds actually rely on was done earlier this month and will last until 2025. All to say, great, now we're stuck with a law that practically everyone hates because our lawmakers are toothless and useless. But hey, at least we can try again in 2026 when FISA next expires.
More: Washington Post ($) | NOTUS | @charlie.savage.nyt | @LizaGoitein tweets
Crickets from Chirp Systems after smart lock key leak
KrebsOnSecurity: The U.S. government issued an alert this week warning that "smart" locks (emphasis on smart, because, well...) found in 50,000 dwellings nationwide contain hardcoded keys that can be used to remotely access any lock. Yes, that's right — one key to rule them all, and you'd think that Chirp Systems, the maker of these "smart" locks would respond and fix the issues. Alas, no — hence why the government stepped in. Smart locks let you remotely open and close them from your phone, but would you trust one with your home security? It's not like security experts haven't been warning about this for years. If @hacks4pancakes ever tells you something, listen.
More: CISA | The Register | @briankrebs
Palo Alto releases fix for critical firewall zero-day
SecurityWeek: Palo Alto Networks has become the latest maker of security things to face the zero-day music after malicious hackers — believed to be a nation state — began exploiting a vulnerability in the software that powers its firewall devices. You know, the devices that are supposed to block bad actors from getting into a network, not actively letting them in. (If anyone's getting flashbacks to the Ivanti or ConnectWise zero-days, you're not far off.) Palo Alto continues to urge customers to patch their systems as soon as possible as some earlier mitigations (think disabling telemetry) weren't effective. Shadowserver Foundation, which collects and analyzes the web for malicious activity, says there's about 22,500 or so vulnerable IPs out there as of around Thursday, so get patching (and for many of you, threat hunting).
More: Bleeping Computer | TechCrunch | @simontsui | @stevenadair
The U.S. government has a Microsoft problem
Wired ($): Microsoft keeps getting hacked, and now it's starting to piss off the federal government, which relies on Microsoft to keep its emails and documents secure* (*terms and conditions apply). @ericgeller dives into the many problems that the government faces — not just Microsoft — as it handles its scandal of having its emails stolen once again. As Geller notes, "Microsoft's dominance has prompted concerns that it represents a single point of failure, concentrating America’s technology dependence in such a way that hackers could easily sabotage essential services by targeting one company’s products." It's almost like Microsoft is too big to fail at the federal level (yet continues to try), but customers can't escape — even if they want to — describing a "lack of leverage" against the tech and cloud giant. Really interesting stuff here. Bloomberg ($) takes a more optimistic approach.
More: @ericgeller tweets
~ ~
THE STUFF YOU MIGHT'VE MISSED
Experts say ransomware may worsen as Western hackers work with Russians
CBS News: 60 Minutes dove into the Com, also known as The Community, a loose-knit subculture of mostly native English-speaking hackers that use violence, threats, hacking and social engineering to get their payday. Much of the report (and transcript) focuses on Scattered Spider, who broke into the casino giant MGM and other companies. But the Com is a far, far bigger and wider threat that faces the U.S. for their ability to carry out massive hacks with few resources. This is a good primer for anyone with an interest in understanding where cybercrime is today.

XZ backdoor was likely not an isolated incident
OpenJS Foundation: The folks at the OpenJS Foundation and Open Source Security Foundation warned this week that the stealthy, multi-year effort to plant a backdoor in the popular XZ utilities used widely in Linux distros is "likely not an isolated incident," and warned of more open-source project takeovers in the future. The foundations warned of a "similar suspicious pattern" flagged in two as-yet-unnamed other JavaScript projects and flagged the potential security concerns to the appropriate authorities. The post also includes a helpful guide for folks on what to look out for in social engineering takeover attacks. More from Reuters ($).
CVENotifier parses vulnerability feeds and sends keyword alerts
Shantanu Ghumade: Here's a neat project developed by @dark_warlord14: For those wanting to keep ahead of CVE and vulnerability details, CVENotifier parses a ton of RSS feeds for keywords (that you choose) and sends Slack notifications when a new vulnerability drops. Throw this in a shared Slack channel and you're onto something. (via @campuscodi)
UnitedHealth ignores lawmakers' request to send executive to testify
The Record: UnitedHealth, the health insurance giant that makes billions in profit by denying millions of Americans' much-needed healthcare, continues to rebuild its systems after a massive ransomware attack earlier this year. Companies downstream are facing financial ruin, all the while UHG made $100 billion in revenue during the first three months of the year. Congress is rightly angry and demanding answers from UHG — yet, UHG declined to send an executive to testify at a congressional hearing this week. Why would it, when UHG is still — still — trying to figure out how and when it's going to disclose that massive, massive data breach of patient records? For the first time, UHG admitted that the hackers actually stole "some quantity" of patient data. Now we just have to wait for the number to drop.
Google bumps Sandworm from threat group to APT
Google, Mandiant: APT44 graduated as a fully fledged advanced persistent threat group this week, officially linking the gang to a unit within Russian military intelligence. The cyber espionage and digital destruction unit more commonly known as Sandworm has been linked to power cuts targeting Ukraine, water facilities in the U.S., disrupting the Olympic Games, and more. Google and Mandiant dropped their dossier on the hackers, warning that Sandworm is a "dynamic and operationally mature threat actor that is actively engaged in the full spectrum of espionage, attack, and influence operations." More via @gabby_roncone and @danwblack.
~ ~
OTHER NEWSY NUGGETS
'Ello 'ello 'ncrypted: A new U.K. cybersecurity law covering Internet of Things devices goes into effect next week on April 29. The law requires that all internet-connected devices have to meet basic cybersecurity requirements. The new requirements mean devices can't have default passwords and must state the final date for receiving software updates. The U.K. government's advice can be found here (plus a bonus PDF guide) and Which?, as always, has a great explainer for consumers. (via NCSC, h/t @campuscodi)

Duo says upstream telco metadata stolen: In a note to customers, MFA security giant Duo said one of its telephony suppliers that it uses to send MFA codes by SMS was hacked on April 1 (not a joke). The threat actors made off with some data about customers' phones — including phone number, phone carrier and country. Duo said MFA codes weren't exposed, and Duo didn't name the hacked company, but warned of a risk of social engineering attacks targeting Duo customers. (via Cisco Duo)
Delinea flubs security patch: Privileged access management firm Dilinea (previously Thycotic) scrambled to patch a critical authentication bypass vulnerability (not good!) in its Secret Server, which stores and rotates a company's credentials. Turns out security researcher @straight_blast spent months trying to disclose the bug but Dilinea said since Yu wasn't a customer, he was ineligible to open a vulnerability report. (What in the living f...?) Yu kept going and informed CERT, which also got ignored. (via SecurityWeek, Medium)
World-Check swiped for a second time: A financially motivated criminal hacking group took credit for the theft of 5.3 million records from World-Check, a database used by banks and organizations for screening potential customers for links to financial crimes, terrorism, sanctions and corruption. (Disclosure: I wrote this story!) Much of the data is sourced from public records, but the database itself is confidential — so nobody really knows if they're on the list, which isn't fun when you have your bank account shut down as a result. Plenty are, despite having no connection to criminal activity. World-Check was stolen before. (via TechCrunch)
~ ~
THE HAPPY CORNER
And not a moment too soon: it's the happy corner.
@IanColdwater found out that what you name your cat matters. I will never not laugh at Little Bobby Tables for this exact reason.
Next up, major kudos to this cat for alerting her human to a DDoS attack in the middle of the night. Take a couple of minutes to read this heartwarming story, it's my favorite of the week.
@vxunderground has an excellent — and informative — tweet on malware masquerading, which fans of cats, corn, and cybersecurity can all enjoy.
The folks at Nettitude jailbroke a Cisco email security appliance to run Doom as a proof-of-concept, and scooped up a CVE in the process. Are we starting to run out of things that Doom can run on...? Nah.
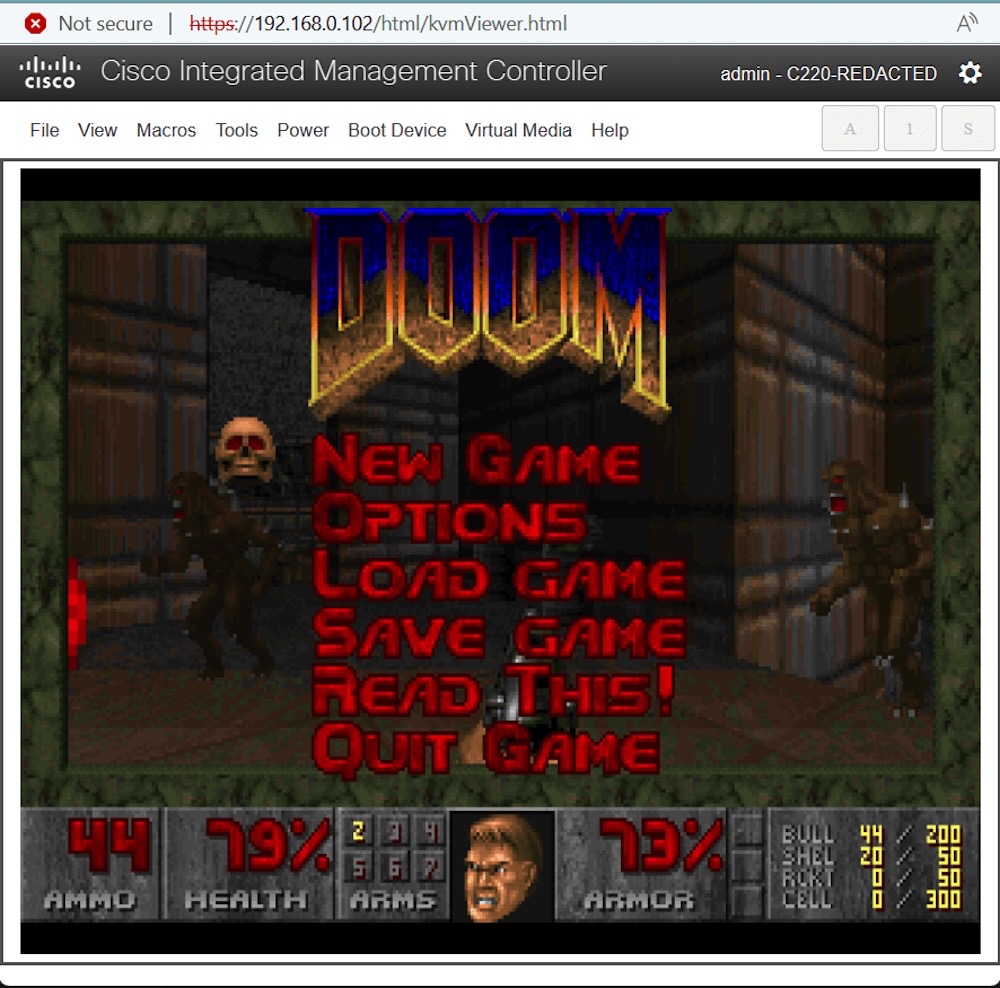
And finally, this week, from one Doom to another.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week last century's cyber cat is Buddy, who can be seen in this retro blast-from-the-past 1998-dated digitized photo playing DX Ball on her human's laptop. Buddy was her human's hacking buddy and laptop warmer for 20 years. Thanks so much to Lisa P for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
~ ~
SUGGESTION BOX
That's it from this week's newsletter. Hope you enjoyed! As always you can reach out to me via email with any suggestions, or feedback you want to share.
I'm off to grab some breakfast and enjoy this glorious east coast springtime doom. Weather, I mean weather!
Chat next week,
@zackwhittaker