this week in security — april 23 edition
THIS WEEK, TL;DR
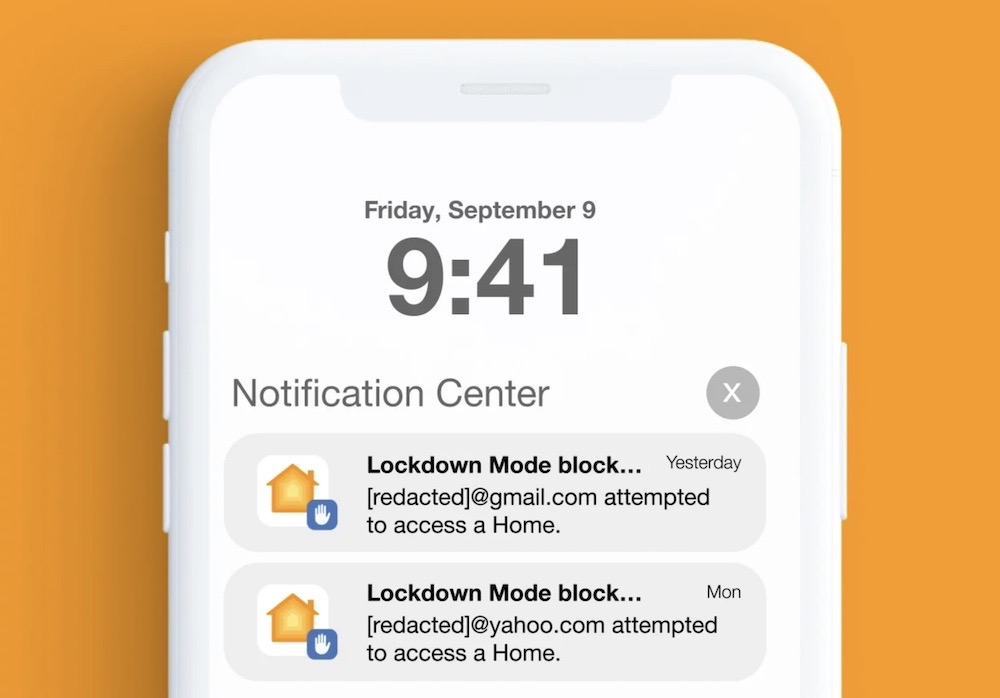
Pegasus spyware returns in 2022 with a trio of iOS 15-16 exploits
Citizen Lab: Bombshell findings from the Toronto-based digital investigative group show NSO Group, purveyor of the Pegasus spyware, developed at least three new exploits targeting iOS 15 and iOS 16 in 2022. The targets include members of Mexico's civil society, including two human rights defenders tasked with investigating military abuses, which isn't a huge surprise given that Mexico is a major Pegasus customer, as the New York Times ($) profiles in more detail. The exploits target iMessage (its messaging app) and HomeKit (for controlling smart home devices), to punch through an unpatched iPhone's defenses. But(!) it turns out that Apple's high-security Lockdown Mode blocked at least one of these attacks from running, showing that the anti-spyware feature worked to block an active intrusion attempt. Apple fixed the flaws after hearing from Citizen Lab.
More: New York Times ($) | Washington Post ($) | R3D | TechCrunch
Another supply chain attack blamed for 3CX's supply chain attack
Zero Day: @kimzetter takes a look at the latest findings by Mandiant, which has evidence that enterprise phone maker 3CX was compromised by an initial, earlier supply chain attack. 3CX is a phone powerhouse; it has 600,000 enterprise customers and some 12 million daily users. North Korean hackers are blamed for breaking in by using a tainted software download from another company that a 3CX employee is believed to have installed, allowing the compromise of its network. Complicated, right? Luckily there's a timeline of events to break down how the mass-hack came to be. All of this, it seems, was to target cryptocurrency companies (since that's how North Korea funds its nuke-building program). This entire story is worth exploring, if not least to be aware that these kinds of long-tail attacks do exist — and that 3CX isn't the only compromised victim here!
More: Mandiant | 3CX | Wired ($) | Krebs on Security | The Register
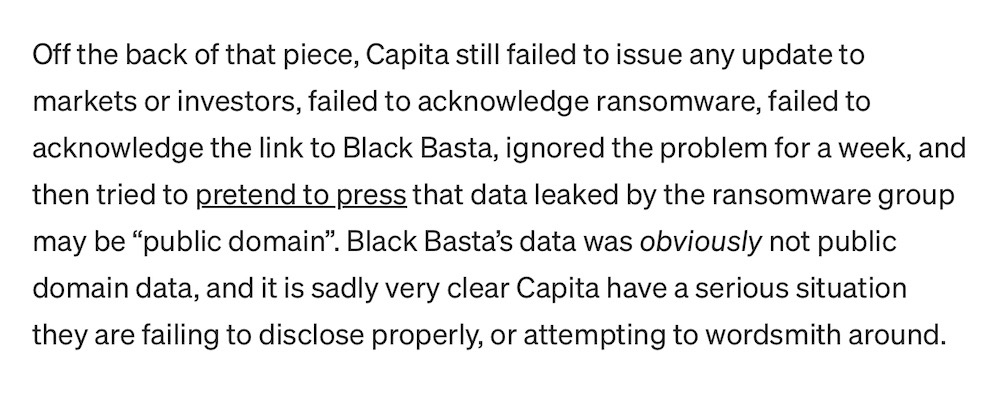
Capita admits it was hacked a week before outage
The Guardian ($): Capita, one of the U.K.'s biggest outsourcing firms, was hacked as far back as March 22, a week before its massive outage that transpired to be ransomware. A Russia-based gang called Black Basta has taken responsibility and posted some of the stolen data (I've seen it, and can confirm other reporting). Capita has said very little in its disclosure, but Capita is huge and helps to run a ton of U.K. public services. Clearly things aren't going well. U.K.'s National Cyber Security Centre sounded caught off-guard as it is "still trying to understand the impact" of the breach." Yeah, like everyone else, including Capita. Thankfully, @gossithedog has an explainer on what Capita isn't telling you, its customers or vendors — so go have a read, because it's spicy.
More: Capita | The Times ($) | DoublePulsar | TechCrunch | BBC News
~ ~
THE STUFF YOU MIGHT'VE MISSED
DC Health Link data breach blamed on human error
Associated Press: Here's a big whoops. A recent spill of personal information affecting thousands of Washington DC's health insurance exchange — including lawmakers — was caused by human error. More than 56,000 people had information compromised in the spill at DC Health Link because of a server "misconfiguration." The exposed data was spotted and subsequently sold on a cybercrime forum. You'd think (or hope) that given this breach affected U.S. lawmakers directly, they'd surely want to act. Alas, this is America: temper your expectations. @brfreed watched the congressional hearing so you don't have to.
Experts say Congress should do more to regulate U.S. data brokers
Cyberscoop: Privacy advocates said lawmakers should do more to regulate the multibillion-dollar data broker industry, which buys and sells the bulk of Americans' data. Yes, all the while Congress breathlessly goes on about TikTok, U.S. data brokers are freely selling your data — including location and health data — to anyone and everyone they can — and it's totally legal. Hopefully soon it won't be.
Cyber giant Group-IB exits Russia
Group-IB: Cybersecurity company Group-IB, which last year discovered the mass-targeting of tech companies, says it's fully exited Russia, a year after Putin's unjustified and unprovoked invasion of Ukraine and two years after arresting the company's founder on treason charges. It's still not clear for what reason Group-IB's founder, Ilya Sachkov, was imprisoned, and Group-IB's blog post says suspiciously little about the whole affair. BBC News reporter @joetidy says Sachkov will be held in custody until at least the end of June.
LockBit gang testing ransomware for macOS
Data Breach Today: The Russia-linked LockBit ransomware group is said to be testing a new macOS ransomware. That's the bad news. The good news is that so far the malware isn't even close to being ready, since the code is pretty crap. According to macOS security wizard @patrickwardle, "as it stands [LockBit's macOS ransomware] poses no threat to macOS users."
~ ~
~ ~
OTHER NEWSY NUGGETS
ICE, ICE (abuses of power) baby: A huge trove of documents obtained by Wired reveal hundreds of investigations by the U.S. immigration enforcement agency into misuse of agency databases. ICE agents are accused of stalking, harassment, and even passing privileged information to criminals for money. At least 14 of the investigations were considered criminal, including one case of an ICE agent misusing a database to threaten a coworker and illegally accessing a detainee's medical records. (via Wired ($))
Former CFPB employee exposed consumers' data: A former employee at the Consumer Financial Protection Bureau forwarded an email to their personal account containing the confidential information on 256,000 consumers and at least 45 financial firms, the agency confirmed as a "major incident." The employee no longer works at the CFPB. It's not clear why the employee forwarded the data, or why the breach — which happened on March 21 — wasn't disclosed sooner. (via Wall Street Journal ($))
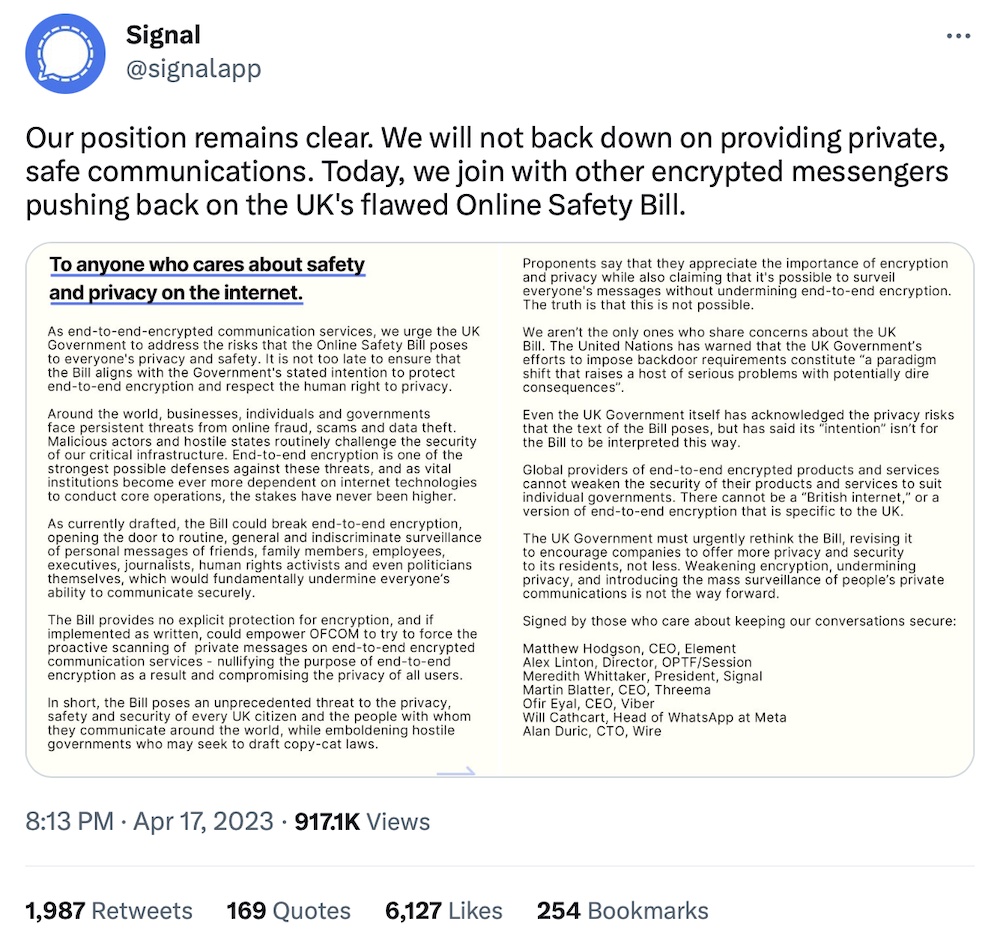
E2EE apps' position 'clear': WhatsApp, Signal and other end-to-end encrypted messaging apps will absolutely walk from the U.K. if the government in London passes the Online Safety Bill, which — look, anyone who's been around long enough knows that anything "online safety" is pretty much an effort aimed at undermining encryption. The U.K. is taking another stab at the grotesque surveillance measures, which experts and critics say would allow the government to demand access to encrypted messages. The latest letter reaffirming their position was signed by leaders of Signal, Threema, Viber, WhatsApp, Wire, and others. (Let's not forget that these are the very same British lawmakers who religiously use WhatsApp to avoid public scrutiny. One rule for them! The hypocrisy is staggering.) (via BBC News)
Mullvad received search warrant, gave police nothing: VPN provider Mullvad said it was subject to a search warrant (for the first time) by police in Sweden with the intention to seize computers with customer data. But Mullvad said it doesn't store any customer data, and police left empty handed. I have extreme skepticisms about VPNs generally (as you should — know their limitations!) but it's good to see that companies don't need to survive or make money off people's data. Remember: You can't give, leak or spill data that you don't have! (via @briankrebs)
~ ~
THE HAPPY CORNER
Happy weekends to all, and welcome to the happy corner. Keeping things light since 2018.
Head on over to CJR for a long-read profile of @runasand, featuring: pizza, cats, sharks, pole dancing, and defending at-risk people from digital harms.
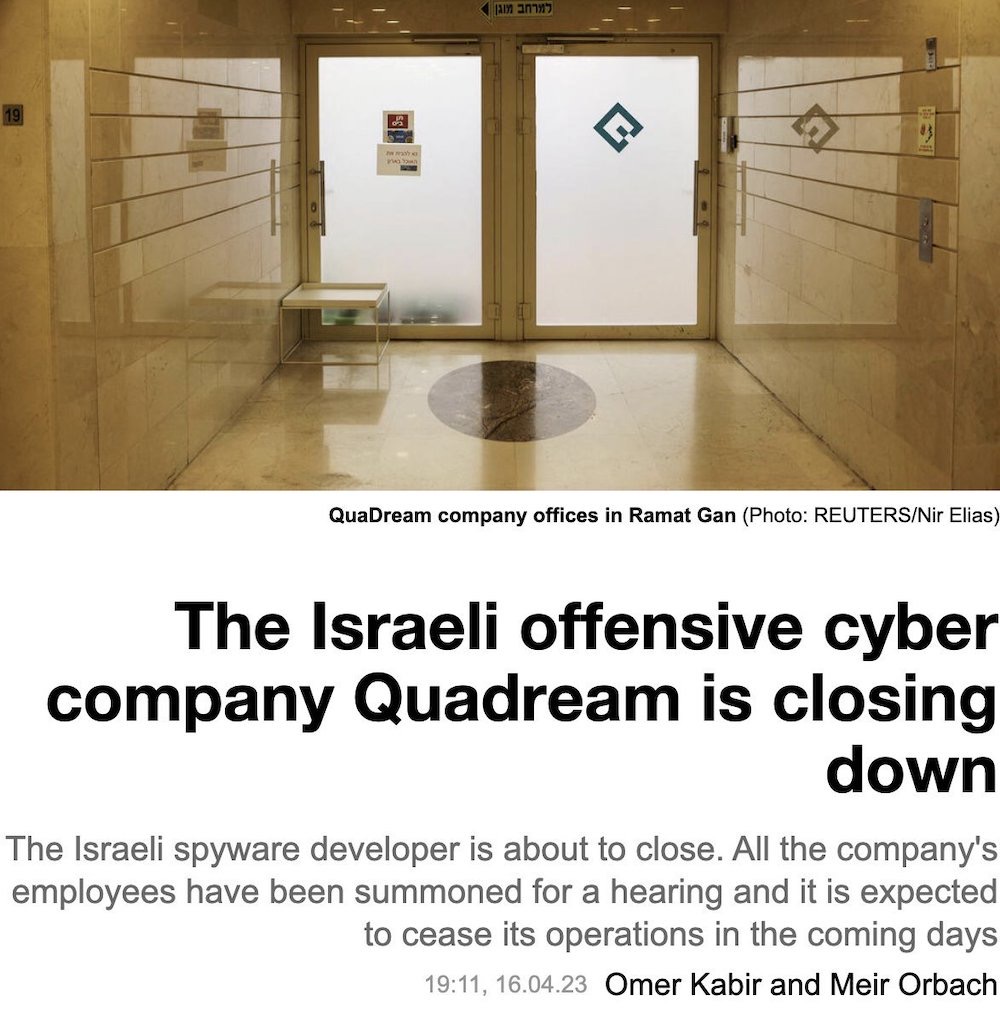
Some excellent news: Spyware vendor QuaDream reportedly closed down after Citizen Lab's exposé on its iPhone-exploiting spyware. Calcalist ($) has the story. One spyware maker shut down, so many more to go.
As if you needed any more good news on the spyware front, the Biden administration's recent kibosh of human rights-infringing spyware is "upsetting the market," with some spyware makers claiming they might not be able to stay in business. Cue the sound of the world's tiniest violin. 🎻
And finally, this week. Microsoft has updated its threat actor naming convention. China is typhoon-themed, Russia is blizzard-themed, and Iran got lumped with names like "Marigold Sandstorm" and "Cotton Sandstorm," which kinda sound like adult entertainers? (Last minute add to the newsletter: @agreenberg has a good rant in Wired ($) about this.)
But if you want some fun of your own, head on over to @thepacketrat's cyber threat actor naming system, dubbed the Cyberthreatarator. I got "Grim Somali Wild Ass." Seems fitting.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is this extremely handsome long boy named Tennessee (after the cartoon, not the state). Many thanks to Jeri D. for sending in!

Don't forget to send in your cyber cats (or their friends). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week — thanks for reading! If you have any feedback, drop me an email. I'm off to get some brunch in the neighborhood.
Have wonderful weeks. See you in the mentions,
—@zackwhittaker