this week in security — april 27 edition
THIS WEEK, TL;DR
UnitedHealth hackers stole health data on most people in America
TechCrunch: It's the headline we never wanted to see, but were bound to get eventually. Thanks to the consolidation and merging of massive healthcare companies that result in mega-corps like UnitedHealth-owned Change Healthcare handling some half of all U.S. patient records, we now have one of the largest data breaches in U.S. history. UHG, the largest insurance giant in the world, says the ransomware gang that broke into its Change subsidiary stole health and patient data on "a substantial proportion of people in America." Change still hasn't disclosed the number of, well, tens if not hundreds of millions of people who are affected, but said that process will likely take some time because of the massive amounts of stolen data it has to go through. (Disclosure: I wrote this story!) UHG told me in a statement that it paid a ransom — but wouldn't say if it was the first, or the second ransom it paid, because of course reams of stolen Americans' health data are still out there. No amount of ransom payments will get that back. UHG CEO Andrew Witty, who made $21 million in compensation in 2022, is testifying to lawmakers on May 1.
More: U.S. HHS | Bloomberg ($) | BankInfoSecurity
Suspected Chinese spies hacked Cisco firewalls to access government networks
Wired ($): Sources tell Wired that China-backed spies are behind a wave of network intrusions in government networks around the world exploiting vulnerabilities in Cisco firewalls. Yes, it's yet another round of zero-days targeting edge devices (think VPNs, firewalls, and other security gear at the edge of corporate and government networks), which are increasingly the weak security link that are letting bad actors break into networks. Cisco's own intelligence unit Talos dropped details of the two zero-day vulnerabilities in Cisco's Adaptive Security Appliances, which are now patched and customers should update.
More: Cisco | Cisco Talos | NCSC [PDF] | SecurityWeek
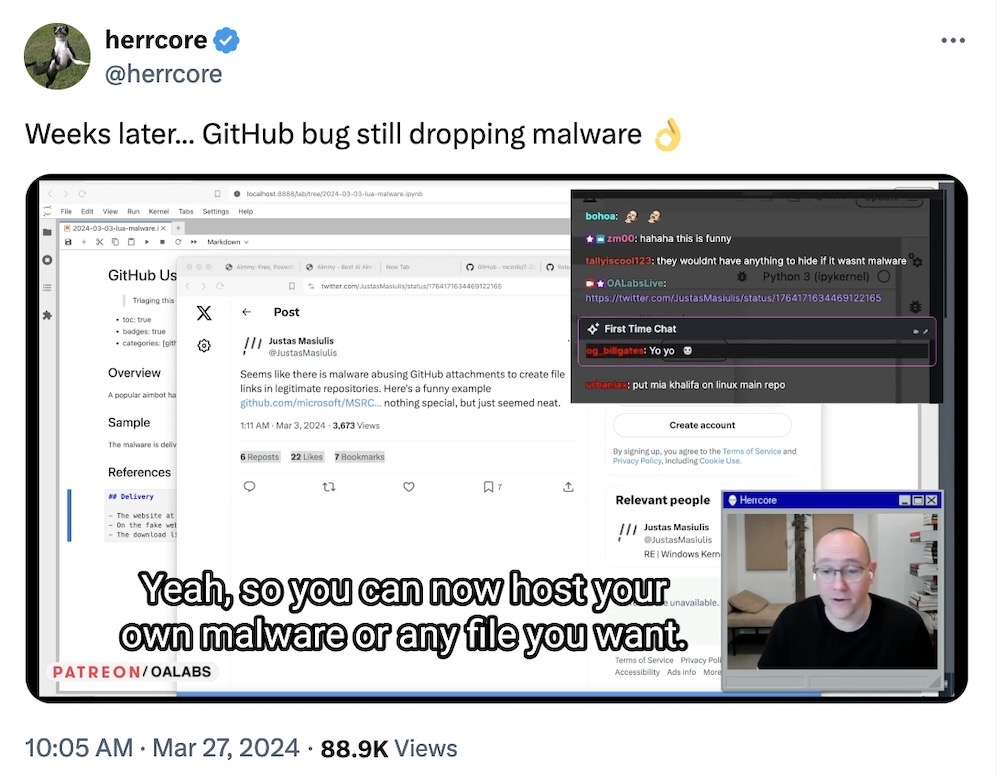
GitHub comments abused to push malware via Microsoft repo
Bleeping Computer: Microsoft is really struggling with security. After a rash of hacks from China and its (still!) ongoing intrusion of Russian spies, there's no wonder that U.S. government agencies are losing trust in the tech giant. The latest snafu is how threat actors are exploiting a flaw or "design decision" in GitHub that makes malware look like it's associated with Microsoft's official code repo and "making the files appear trustworthy." Whoops. Bleeping Computer explains how this bug works and how threat actors are actively using it to distribute malware disguised. It looks like Microsoft quietly removed the malware but hasn't said anything about the problem... cool. For those using GitLab, note that you're also affected.
More: Axios | DataBreachToday | @Ax_Sharma tweets | @herrcore
~ ~
THE STUFF YOU MIGHT'VE MISSED
BlackBerry won't fix MDM authentication flaws
Matt Burch: Interesting research by Matt Burch, aka @emptynebuli, who found authentication issues within BlackBerry's mobile device management (MDM) software, which by all accounts is pretty important software when managing fleets of entire devices. BlackBerry (yes, still a company), called the bugs intended by design and seems like it has no plans to fix them. Burch also released Dauthi, an attack framework that performs authentication attacks against various MDM platforms, including BlackBerry's.
Google and Apple are making passkeys insufferable
William Brow: Passkeys are a great, unphishable authentication technology that should have taken the world by storm, but this scathing rebuke of Google and Apple's rollout and handling of the passkey user experience details the many difficulties their users are having — including randomly lost passkeys. I love using passkeys when they work, which is often because I — like many others — rely on using a password manager to store my passkeys, and not letting Google and Apple store them on my behalf. "If you really want passkeys, put them in a password manager you control. But don't use a platform controlled passkey store, and be very careful with security keys," writes @firstyear. The whole blog is worth the read.
Hackers infected antivirus users that delivered updates via HTTP with malware
Avast: For years, hackers abused a weakness in eScan antivirus to deliver users with malware (the irony isn't lost here) because the antivirus delivered updates over unencrypted HTTP. That allowed the hackers — thought to be associated with the North Korean regime — to perform adversary-in-the-middle attacks that replaced genuine updates with malware. Guess what the North Korean hackers were looking for? Crypto, of course! For All Your Nuclear Weaponry Needs!™ Ars Technica has a good explainer, as always.
~ ~
OTHER NEWSY NUGGETS
Odd byproduct of a cyberattack: The city of Leicester was hit by a cyberattack a couple of months ago. Internal documents stolen, public service outages... and bizarrely, the street lights are still stuck on, even during the day. The city council confirmed the lights outage on-age(?!) was caused by a "technical issue connected to the recent cyber attack." (Actually, there's a good reason for the lights failing on, as to prevent a safety issue of lights not going on at night.) (via Leicester Mercury)

U.K. Snoopers' Charter 2: The Snoopening: Hellbent on huffing as many surveillance powers as they can, the U.K. just followed in the U.S.' FISA footsteps by expanding its own spy powers. The Investigatory Powers Bill aka Snoopers' Charter, now expands internet surveillance and the ability for the U.K. government to block security features it doesn't like. That has yet to be tested in a real-world scenario, but buckle up for another round of crypto wars, no doubt. (via The Register)
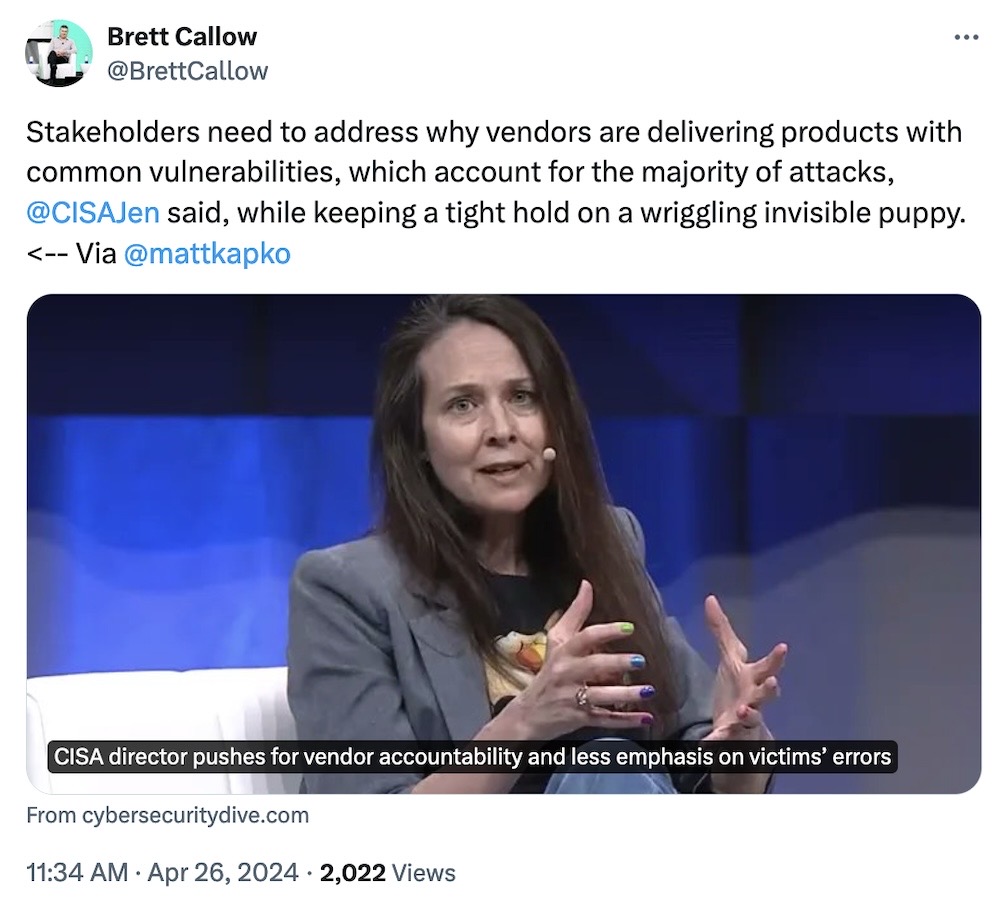
CISA wants vendor accountability: CISA director Jen Easterly said this week that while there's plenty of talk about villains and victims, it's time to talk about hardware and software vendors and holding them accountable for the buggy tech that gets people hacked (including the federal government). That makes sense in theory, but so many tech giants are owned by private equity firms that are basically accountable to noone, there's little incentive to fix. Meanwhile, spot the wriggly invisible puppy! (via Cybersecurity Dive)
iSharing? More like everyone-sharing: The popular location tracking app iSharing, which has 35 million users to date, had bugs that exposed the precise locations of every user — even if the user wasn’t actively sharing their location data with anybody else. The bugs were easy to find (and thankfully easy to fix), but took a while because the developers seemed to lose the security researcher's report. I helped to nudge things along, but couldn't resist playing guinea-pig. I asked Eric Daigle to try the bug on a phone we had, and he plucked our location seemingly out of thin air. (via Eric Daigle, TechCrunch)
Kaiser exposed data to advertisers: California-based health giant Kaiser is notifying around 13 million members that it shared their data with advertisers as members browsed Kaiser's website and mobile apps. Blame the little invisible tracking pixels that track users' activity for "analytics" but also collect real people's searches for medical conditions, prescriptions and other things that can identify their sensitive health information. Not great! HHS has been on a push to get health tech companies to stop doing this, after a rash of telehealth services were caught doing the same thing during the pandemic. (via SFGate, TechCrunch)
GM's sneaky data sharing: Another reminder that your car is likely collecting heauuugeee amounts of data on your driving patterns and selling that data to your insurance company. GM enrolled drivers into its data sharing program — without telling them — and of course, GM says this is a "bug" (😉). Of course, @kashhill brings receipts. (via The New York Times ($))
~ ~
THE HAPPY CORNER
And scene. This is the happy corner.
Just a handful of things to consider... and this guide by The Verge on how you can delete the data that Google stores on you is a must-read and a fun action item for this weekend. Time to set up those auto-deletes! (h/t: @cyberlyra)
This week I'm reading Byron Tau's book, Means of Control, a deep dive into the world of today's surveillance and all of the creepy ways that data brokers, ad giants and governments spy on the masses. Tau, a former WSJ reporter now with NOTUS, has a great excerpt from the book from February. Grab yourself a copy and then throw your phone into the abyss, you won't be needing it.
And on that note, this closing thought:
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's three-for-one cybercat special features Misty, Sadie, and Rosie, who can be seen here monitoring their human's house for any squirrel-based back doors. Keep up the good work, kitties. Thanks so much to Nick F. for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's everything you need to know from the week. Thanks for reading! I'll be back in a couple of weeks after taking a break next Sunday.
If you have any comments, questions, thoughts or feedback, feel free to reach out to me via email any time.
Gone phishin'...
@zackwhittaker