this week in security — april 27 2025 edition
THIS WEEK, TL;DR
Hegseth had unsecured internet line in Pentagon office to connect to Signal
Washington Post ($): We have to start here this week because, sigh... *pinches bridge of nose* ...folks, he only went and did it again. Several weeks after the U.S. Secretary of Defense Pete Hegseth shared sensitive war plans in a Signal group chat that mistakenly included a journalist, the Post and the AP found Hegseth was also sharing war plans over Signal that included his wife and brother, among others. He was also using a "dirty line" (aka a regular internet connection), but from his official office in the Pentagon in order to use Signal on its desktop app, leaving commenting cybersecurity and records-keeping experts aghast. Signal is great, don't get me wrong, but it's not cleared for government use, crucially because the devices that Signal runs on (you know, regular phones) are more susceptible to malware and spyware than the much-more hardened systems designed for classified use. What a mess... and this raises more questions about government security (or lack thereof) with sensitive information. If I had a nickel for every scandal involving the top U.S. defense official sharing war plans on Signal, I would have at least two nickels.
More: Emptywheel | New York Times ($) | NPR | TechCrunch

Ex-CISA chief: Trump actions risk 'dangerously degrading' U.S. cyber defenses
Jen Easterly / LinkedIn: Former CISA boss Chris Krebs has been in the news of late after Trump ordered a retaliatory federal investigation into him for publicly disputing Trump's false claims of electoral irregularities during the 2020 presidential campaign. Yet, we heard practically crickets from the cybersecurity industry, fearful that Trump will come after them as well. Now, Krebs' successor at CISA, Jen Easterly, has posted on LinkedIn with a pointed message but without naming names: Trump's actions are putting the nation's cyber defenses at risk of being "dangerously degraded." Easterly's comments are really worth the read as folks head to RSA this week; and I'd encourage you to take the time. "If we fail to stand up for leaders being punished for telling the truth, for doing their jobs with honor—then we're not leading; we're calculating." Easterly said that as folks head into RSA, now is the time to think about what brings us all together. (Psssts loudly: Easterly is talking about people!)
More: New York Times ($) | Reuters ($) | Cybersecurity Dive | All Rise News
Two major health-related breaches hit millions across the U.S.
TechCrunch: Two of the largest healthcare-related data breaches of the year (so far; we're still only in April!) have come forward. Blue Shield of California revealed that it had been sharing personal and some health-related information of more than 4.7 million patients with Google over a period of several years, thanks to misconfigured website trackers. A ton of healthcare firms got caught by this during the pandemic when telehealth rocketed, not that it excuses it. Google wouldn't say if it would delete the data, but was happy to use the information for advertising against affected patients. Meanwhile: Connecticut's Yale New Haven Health system, the state's largest, told me this week that it's not disputing that it was hit by ransomware (in other words, it was hit by ransomware) during a March cyberattack and that it's notifying 5.5 million people of the breach regardless. (Double disclosure: I wrote both of these stories!)
More: Yale News | The Register | San Francisco Chronicle
~ ~
THE STUFF YOU MIGHT'VE MISSED
Crypto scams and losses lead FBI's annual cybercrime report
NBC News: Scams involving cryptocurrency were top of the FBI's annual report [PDF] on cybercrime across 2024. The feds say scam victims were mostly folks who are 60 and older, which lost a collective $4.8 billion in crypto scams, including pigbutchering. It's pretty bleak reading, but probably a reminder to especially folks that unless you're actively involved with cryptocurrency right now, you're probably better off that way — at least for the sake of avoiding scams. More via @molly0xfff.
Google won't ditch third-party cookies after all
Ars Technica: Well there goes the best part of a half-decade's worth of work... Google has scrapped its long-standing plans to move away from third-party cookies. In 2019, the advertising giant (75% of Google's revenues comes from advertising) said it was going to pull the plug on third-party cookies by rolling out its Privacy Sandbox. In the end, making money off of all of our data seems far more important to Google than, well, anything else apparently. A good blog from Lukasz Olejnik, with a quick read on what this means.
Microsoft Recall is back: Slightly better, but not by much
DoublePulsar ($): Remember that time Microsoft rolled out a software update that would screenshot everything on a user's display, including passwords and credit card numbers, and allow them (or malware, naturally) to access all of that data at any point in time? Microsoft called it Recall, and it went down with customers as you'd expect — which is to say, not great. Now it's back, and at least Recall is opt-in, which is better than what it was, and while somewhat improved on the security front, it's not by much. The product still presents significant security risks. The good sir @GossiTheDog has a fun read on this. Meanwhile... this could be fun to watch:
Yale student exposes data leak in college dating app
Alex Schapiro: Excellent research and findings from Alex Schapiro, who found that a student-founded dating app called Cerca is a hot mess of security bugs that exposes the private information of thousands of its users. Schapiro handled this like a pro and reached out to privately disclose the issue, but Cerca didn't alert its users. Schapiro's first line says it all: "Startups Need to Take Security Seriously." Yale News also wrote up. We need more students like Schapiro, and fewer who are focused on making a quick buck at the expense of their fellow students' privacy.
Hacking a smart bike to make it work again
Francisco Presencia: Here's a fun read on hacking a dead e-bike and reviving it back to life. Turns out in this case, the bike's lights wouldn't work without the app (me: 😑), so @FPresencia fixed it and posted the results. What would've otherwise been a hunk of wasted metal got a much-needed recycle.
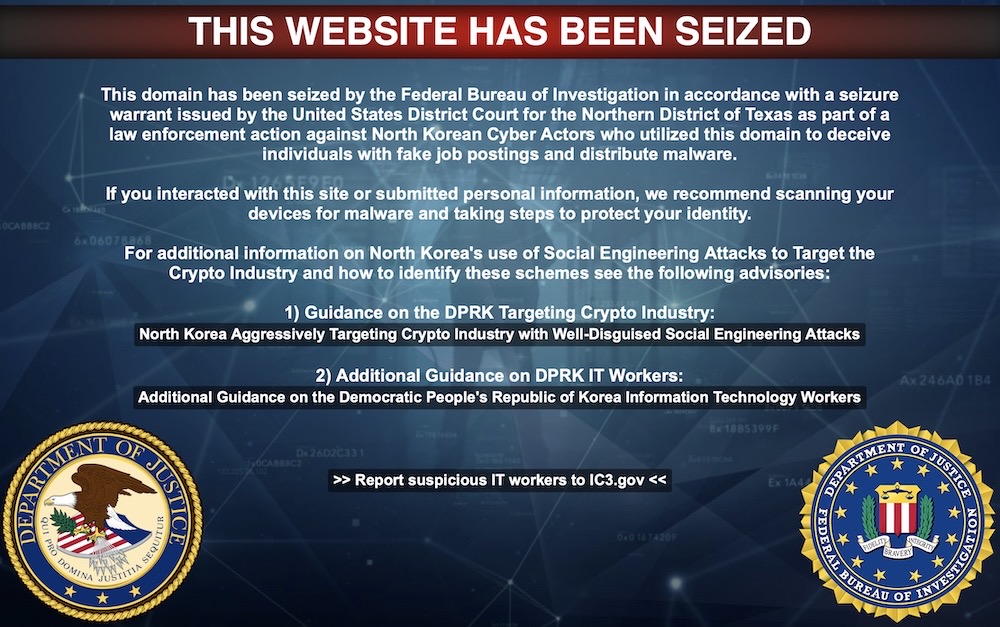
North Koreans created U.S. firm to dupe crypto developers
Reuters ($): Regular readers know that stealing crypto to make nukes is the primary goal of the North Korean regime. Now, its cyber spies are getting even more brazen by setting up actual U.S. entities in violation of sanctions, with the aim of duping crypto developers into installing malware to steal their funds, per researchers. Three businesses were identified, and one of them's been seized by the FBI already. Due diligence is important here: North Koreans are everywhere these days — and they're getting really good at infiltrating companies. In related news: Okta's threat unit has a blog post on how North Koreans are using AI services, and Trend Micro looks at the overlaps with Russian infrastructure.
~ ~...and... while I'm here humbly asking for a moment of your time...
~ ~
OTHER NEWSY NUGGETS
Employee snooping tool spills millions of screenshots: Employee monitoring snooptech WorkComposer, which monitors and takes screenshots of what employees do on their computers, left an open Amazon S3 bucket exposed to the internet containing 21 million unredacted screenshots from over 200,000 unique users. (Hmmm, for some reason the 'Microsoft Recall buzzer' just went off.) Another reason not to use these horrendously invasive snooping tools, because now all of WorkComposer's corporate customers have to file data breach disclosures... (via Tom's Guide, Reddit thread)
Top African, Korean telcos hacked: Two major telcos revealed hacks this week. MTN Group in Africa said a hacker claimed to have access to some internal systems, although few details about the breach itself. Meanwhile, South Korean phone giant SK Telecom said some customer data was leaked due to malware but said it's replacing SIM cards to some 23 million users as a result. (via MTN Group, SK Telecom)
U.K. moves to block Global Titles abuse: Sticking with phone networks for a hot second, the U.K.'s comms regulator said it's put in place new measures to block the misuse of global titles, a critical technology used by phone companies for routing of messages and other data across the world. Global titles have been misused by malicious actors (think surveillance vendors) to intercept messages, calls and location data. Ofcom has more on what measures it's putting in place. (thanks to @campuscodi for spotting)
This is not just any 'cyber incident': U.K. retail giant Marks & Spencer says it's been hit by an unspecified cyberattack, which hit grocery order pickups and some contactless payments. Now, per a note with London's stock exchange, the retailer has stopped customers picking up orders amid ongoing delays and outages. M&S reported 32 million customers last year, so... welp? (via BBC News)
BreachForums is seized ...back again offline: The notorious cybercriminal forum BreachForums mysteriously dropped offline, but appeared to have been revived on a Finnish domain, alleging that the previous domain had been seized by the FBI (which, if true, would be at least the third time in BreachForum's history) and that the forum had to start again. But not everyone's convinced. Could the new site be a police honeypot? BreachForums' new domain didn't last long, presumably thanks to Finnish authorities. (via OSINT Team ($), @cR0w)
Alleged Scattered Spider hacker extradited: Tyler Buchanan, a not-so-wee lad from Scotland, was extradited from Spain to the U.S. this week to face justice for alleged involvement in the Scattered Spider hacking group, which ripped through dozens of major tech giants (and the occasional casino) during a year-long hacking spree. We may end up hearing more specifics about the hacks themselves when the case goes to trial — assuming it does, of course, and that Buchanan isn't either pardoned or disappeared, which seems largely the two judicial outcomes in America these days. (via Bloomberg ($))
TP-Link faces natsec probe: And lastly, also from Bloomberg ($), router maker TP-Link is under the national security spotlight as it faces an apparent criminal antitrust probe in the United States. The scrutiny began during Biden's term, and is said to focus on its tech and national security risks to large tech companies. For reference, it kinda sounds like the government is trying to "pull a Huawei," of sorts. (via Bloomberg ($), @Kate_OKeeffe)
~ ~
THE HAPPY CORNER
Welcome, welcome, welcome. This is the happy corner, and the vibes are zen. Now that the weather is getting a little warmer here on the east coast, it's a lot easier to wind down and touch gra...

Oh, never mind then.
It's been awhile, but here's the latest update to What Can Doom Run On? and this week it turns out it's... own custom operating system? And it's called... TacOS?! This is just brilliant and what looks like an incredible amount of work. Truly amazing stuff.
Moving on... this is probably the worst kind of printer jam.
And lastly, this week. You wouldn't pirate a font... or... would you? It turns out the now-infamous anti-piracy campaign may have itself used a pirated font. Absolutely no notes here, this is chef's kiss perfect.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Murphy, who looks absolutely exhausted after a long-day convincing executives to switch on MFA. Not 98%, not 99%, but 100% across the board. Keep up the good work, Murphy. Thanks so much to Matt S. for the update!

Please send in your cybercats or non-feline friends! You can email at any time with a photo and name of your cyber cat (or friend) and they'll be featured in an upcoming newsletter. If you've sent in before, you're welcome to send in an update!
~ ~
SUGGESTION BOX
And that's about as much as there is in the news. Let's see if we can avoid another national security leak from within this week? What a mess...
As always, thanks so much for reading. It's a joy to bring this newsletter to you every week. Feel free to get in touch by email, it's good to hear from you, and please do let me know what you think about the newsletter in the survey if you haven't already.
Catch you later,
@zackwhittaker