this week in security — april 3 edition
THIS WEEK, TL;DR
How one Ukrainian IT specialist exposed a notorious Russian ransomware gang
CNN: Incredible reporting on a Ukrainian cybersecurity expert who fights "with a keyboard and mouse" by exposing files, tools, and internal chat logs belonging to Conti, the notorious Russian-linked ransomware gang. The Conti leaker "quietly lurked on the hackers' computer servers and would pass along information on the group's operations to European law enforcement officials," per the report. The doxes were so effective that the FBI asked him to stop, fearing it would make it more difficult to track them. Also this week, reporting from the Wall Street Journal ($) exposes the inner workings of the Trickbot cybercrime enterprise, a pro-Russia hacking group, thanks to a Ukrainian researcher who infiltrated the group's servers.
More: Bleeping Computer | @snlyngaas tweets | @dnvolz
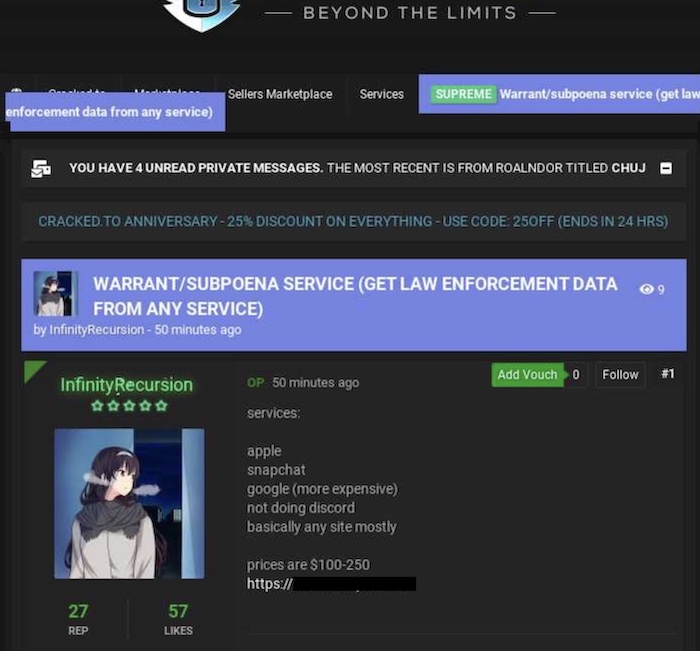
Apple and Meta Gave user data to hackers who used forged legal requests
Bloomberg ($): Well, they finally did it: hackers associated with a group, some of which now operate as part of Lapsus$, tricked Apple and Meta into turning over user data by supplying fake subpoenas sent from hacked email domains belonging to law enforcement. The hackers specifically exploited the "emergency data request" system, which allows the quicker turnover of data under emergency situations — often to prevent loss of life. Discord also fulfilled a forged legal request. The use of forged legal requests was first reported by Krebs on Security.
More: @brettcallow | @Riana_Crypto
Zero-day flaw found in Java Spring Framework
Dark Reading: A bad bug found in a popular Java web application development framework puts a ton of web apps at risk of remote attack. The bug, named Spring4Shell, affects Spring, whose maintainers confirmed the bug. Patches are out, just after a zero-day exploit was posted to Twitter — then deleted. @dangoodin001 has a good tweet thread on the "disaster that wasn't."
More: Spring | Cisco Talos | Ars Technica
How Intrusion Truth is unmasking China’s state hackers
Zero Day: @KimZetter is back with a long-read on Intrusion Truth, the anonymous person or group behind a series of doxes of high-level Chinese cyber spies — some of which have proven to be pretty accurate, with U.S. Justice Department indictments dropping soon after. A compelling read, and featuring conversations with Intrusion itself (or themselves).
More: Zero Day | @kimzetter
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
People are getting scam texts from... themselves
Motherboard: We've all had weird spam in our time, but more people seem to be getting spam from... themselves. It's what appears to be part of a widespread scam aimed at getting people to click on a phishing link that comes from the target's own number. Many Verizon customers appear to be affected, which seems to be having trouble doing anything about it.
Mystery GPS tracker found on an EFF supporter's car
Electronic Frontier Foundation: Why did an EFF supporter's car have a GPS tracker on it? Did they have a stalker? No, it turns out a GPS tracker was installed to their vehicles by car dealerships, but weren't activated until the buyer paid for services. @cooperq ripped the device to bits and figured out how it works — and left open a ton of questions about the sort of data that's being stored on the device regardless of whether it's activated or not. Very creepy.

Safari vulnerability allowed for Gatekeeper bypass
Jamf: An interesting newly discovered bug in macOS, dating back to as far back as Safari 14 on Big Sur, allowed for an attacker to bypass in-built Gatekeeper protections in macOS, which protect the operating system from automatically opening apps and files downloaded from the internet. The researchers found the bug as what appeared to be an intended feature from a popular game hosting site, but turned out to allow unauthorized code without a pop-up prompt.
Google Project Zero explains how NSO's ForcedEntry exploit escapes the iOS sandbox
Google Project Zero: Google, with help from Apple and Citizen Lab, analyzed a sample of NSO Group's "ForcedEntry" exploit, which can remotely compromise an iOS device for the purpose of installing the Pegasus spyware. This blog post explains the sandbox escape part of the bug.
Ronin Network: What a $615m hack says about the state of crypto
BBC News: A hack of the Ronin Network, a key platform powering the game Axie Infinity, had $615 million in cryptocurrency stolen, in one of — if not the biggest cryptocurrency hack to date. Hackers used private keys to exploit a bug in the Ronin bridge. (A bridge lets people convert tokens to ones that can be used on another network.) A lot of people lost a lot of money, once again because of weaknesses in poorly coded and unaudited software, explains Bloomberg ($).
~ ~
OTHER NEWSY NUGGETS
Major Ukraine ISP hit by DDoS: BBC News reporting major disruptions at one of Ukraine's largest telecoms, Ukrtelecom, following a DDoS powerful enough to affect its core infrastructure. Forbes ($) spoke with Victor Zhora, Ukraine's deputy head of state infosec protection, who said the incident at Ukrtelecom as the "most severe" cyberattack since the start of the Russian invasion in February. That's presumably including the mass modem bricking attack at Viasat...
Viasat attack caused by Russian wiper malware: Speaking of Viasat... SentinelOne security researchers found evidence that the Viasat satellite network — which went down over Europe and Ukraine just as Russia was crossing the border — was downed by destructive malware dubbed AcidRain, which they think is ultimately linked to the GRU. Viasat told TechCrunch that the findings were “consistent with the facts in our report,” which it had published a day earlier, which you can read here and Cyberscoop parsed here.
Browser-in-a-browser phishing linked to Ghostwriter: Google TAG dropping new IOCs on threat activity and actors it's tracking with regard to the war in Ukraine. Among the new data drop is Belarus-linked threat actor Ghostwriter, otherwise known as UNC1151, which was found using the same browser-in-a-browser phishing technique that I mentioned last week. The technique relies on imitating an OAuth login popup using HTML and CSS.
It's Section 702 renewal time (again): Every few years key U.S. surveillance powers come up for renewal — and this time it's the notorious Section 702 (of the Foreign Intelligence Surveillance Act), the core powers that U.S. intelligence rely on for warrantless snooping on communications. The powers are set to sunset in December 2023 unless lawmakers act, reports The Record. That's a year and a half away — plenty of time for a spirited debate that will only be ignored in favor of inevitable sweeping reauthorization like every other time this has happened. Maybe this time we can hope for real reform, if not least to protect Americans' rights from their own government?
Wyze bug ignored for two years: A relatively simple-to-exploit bug in those cheap Wyze cameras allows remote access to the contents of its SD card in the camera via a webserver that doesn't require authentication to access. Per Bleeping Computer, which outlines the two-year-long process by BitDefender to get Wyze to fix the bug — only to have security updates pushed only to newer devices, leaving 2017 models still vulnerable. Wyze said it takes "all security concerns seriously," which as you know is corporate code for "dgaf".
~ ~
THE HAPPY CORNER
The happy corner overfloweth this week.First off, @_MG_ drops some red-team knowledge bombs on circumventing multi-factor protections. Think like a hacker, defend like a pro. A solid tweet-thread to peruse.
Meanwhile, I call this piece: "Authenti-cat-ion."

Can Grafana run Doom? The answer we never needed to know, but yes, apparently, it can.
And @netspooky made some ~spooky~ router art using Wireshark.
To send in good news for the happy corner, please reach out to: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cats are Finn (left) and Tamo (right) when they were tiny. They're much bigger today and doing great, even leaving mice on their human's terrance on occasion. Just be glad they're not dragging your keyboard out, too. Many thanks to @DieZuckerbude for the submission!

Keep sending in your cyber cats — and their friends! Drop an email here with their name and photo, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all I can pack in this week — many thanks for reading! Feel free to drop any feedback in the suggestion box or email me any time.
Hope you have a great week. Don't forget to send in your cyber cats! (If you've submitted before, I'd love to hear from you again.)
Same time next weekend,
—@zackwhittaker