this week in security — april 6 2025 edition
THIS WEEK, TL;DR
NSA director ousted at urging of far-right activist
Washington Post ($): Timothy Haugh, a career military official who was appointed to head the National Security Agency and its offensive counterpart Cyber Command a little over a year ago, has been ousted by the Trump administration. Details remain unclear exactly why, but the Post and others report that the removal of the NSA head — who oversees the powerful wiretapping and spy agency — was made at the request of far-right conspiracy theorist Laura Loomer during an Oval Office meeting this week. The firing caught many in Washington by surprise, including lawmakers tasked with intelligence oversight. Not even the DOD had any immediate comment, which seemed to learn about the firing through media reports. Lawmakers stressed this isn't exactly the greatest time to do this amid Chinese hacks and widespread targeting. Meanwhile: CISA continues to brace for further cuts, per Axios and CBS News, as many as 1,300 agency employees, despite the urging of House lawmakers of CISA to take on more cyber, not less.
More: New York Times ($) | Wired ($) | Cyberscoop | CNN | @samsabin
China hackers exploiting fresh Ivanti zero-day
Mandiant: Fresh Ivanti zero-day, served up hot — and already in use by China-nexus hackers targeting customers who run Ivanti's VPN appliance, Connect Secure (another victim of terrible product naming). Mandiant said it found exploitation of the buffer overflow bug (aka CVE-2025-22457) used to drop backdoors and other malware. Exploitation dates back to at least mid-March, per Mandiant, and attributed to an as-yet-unknown China espionage group. It's not clear how many companies were exploited but one to patch regardless. This looks like Ivanti's second zero-day of the year (at least) after a January bug was also found to be under attack.
More: Ivanti | Bleeping Computer | Cybersecurity Dive
Oracle alerts clients to second breach, says login data stolen
Bloomberg ($): Oracle has alerted its customers to a data breach — its second incident in the last month. Per Bloomberg, Oracle told customers that hackers stole usernames, passkeys and encrypted passwords — with some credentials as recent as 2024 — and that the FBI was investigating. Oracle has remained defiantly silent about the breach, which is separate from its Oracle Health/Cerner hack incident — even if both incidents reportedly involve extortion. Bleeping Computer has done some great reporting on this. This will continue to spiral and get worse, because Oracle can't seem to ever handle its scandals.
More: DoublePulsar ($) | CSO Online
~ ~
THE STUFF YOU MIGHT'VE MISSED
How the feds tracked Caesars' $15 million ransom
Court Watch: Court documents reveal how the FBI tracked down and seized millions of the $15 million ransom that Caesars paid to hackers in 2023 following a ransomware attack. Caesars paid the $15 million ransom (negotiated down), but per the court document [PDF], the feds used the ransom payment transaction to follow the money flow — and seize much of the funds as it was transferred from one company-hosted wallet to another. (via 404 Media ($))
Open genetics site openSNP will shutter, fearing authoritarianism
Bastian Greshake Tzovaras: One of the founders of open source genetics sharing site openSNP said in a blog post this week that they're shutting down the site. Greshake Tzovaras said the site will close and all its data will be deleted on April 30, amid concerns of data privacy (amid the 23andMe sale) and "a rise in far-right and other authoritarian governments" that could put the data at risk. I chatted with him for TechCrunch (disclosure alert), as did the good folks at 404 Media ($).
Some companies appear to ignore opt-out privacy requests
Consumer Reports: Companies are required (under more than a dozen U.S. state laws that cover about half of the American population) to offer opt-out mechanisms for users and customers that prevent the companies from selling or sharing a person's personal data for targeted advertising. It turns out that many companies aren't honoring those requests — or flat out ignoring them. Check out the findings [PDF] and learn which companies don't seem to care about your privacy. Better yet, use an ad-blocker!
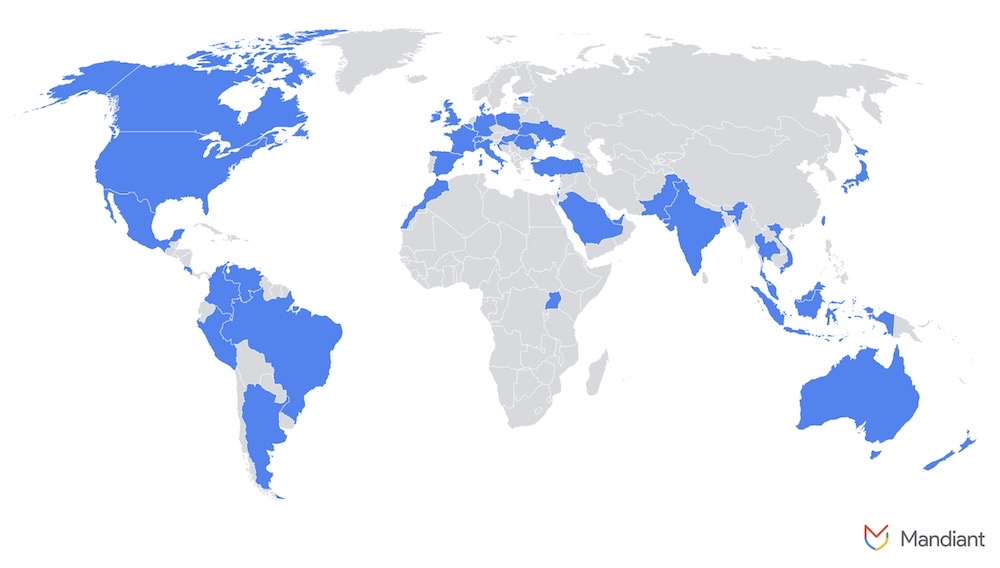
DPRK IT workers now targeting companies in Europe
Google Threat Intelligence: Google's threat intel boffins say hackers working for the North Korean regime, whose task it is to pretend to be prospective employees applying for jobs at big Western firms in order to gain employment, earn a wage, but then also steal gobs of corporate data (aka the "triple threat" of making money, extortion and IP theft), are now actively working across Europe. While the U.S. was a big focus for DPRK IT workers, Google says the DOJ indicting the heck out of some of these hackers has resulted in a shift towards targeting companies in Europe. Here's where Mandiant says the North Korean hackers are targeting:
~ ~
OTHER NEWSY NUGGETS
T-Mobile bug exposed kids' locations: Fresh new nightmare scenario unlocked. A bug in T-Mobile's SyncUP mobile tracker (which can be used in place of a phone app) resulted in some parents logging in and being able to access the names, photos and precise location data of other children. "I would log in and I couldn’t see my children but I could see a kid in California," said one parent to 404 Media. (me: wheezing exhale) (via 404 Media ($), @jasonkoebler)
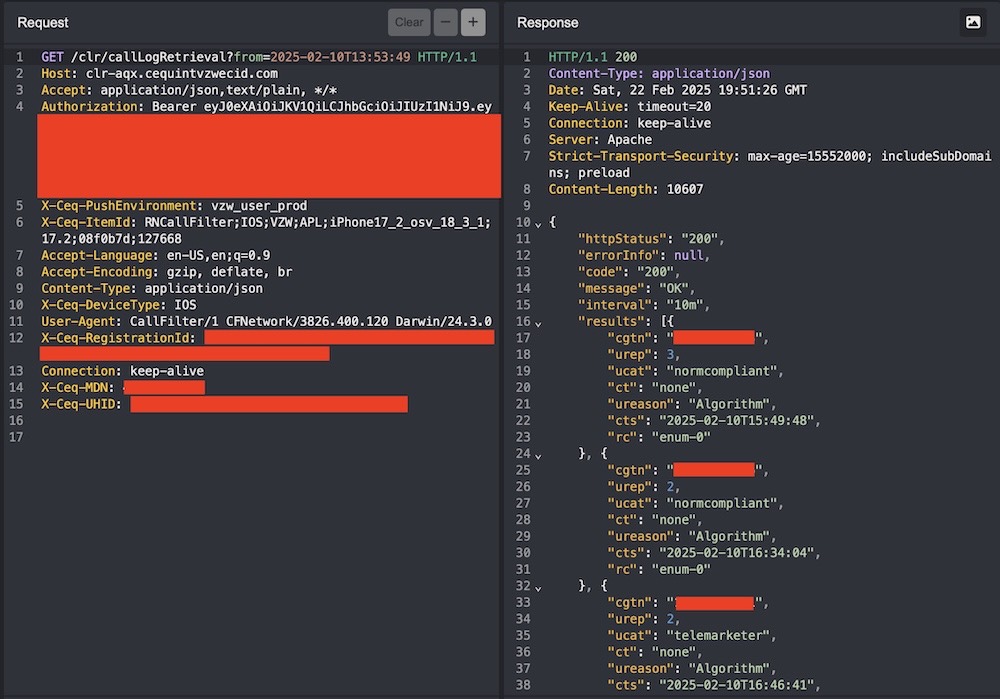
Verizon app bug exposed call records: Incredible research and findings by @Evan_Connelly, who found that Verizon's call filter app had a bug that allowed anyone to punch in someone's phone number and retrieve their list of incoming calls — with timestamps — in large part thanks to a lack of server-side validation of requesting phone numbers. Here's a short but good post explaining the bug, which Verizon has since fixed. (via Evan Connelly, SecurityWeek)
Europcar breach affects 200,000 customers: A breach of Europcar's GitLab repository has exposed the personal information of around 200,000 customers, including names and email addresses. The breached data also includes SQL files and source code. (via Bleeping Computer)
API testing firm exposed customer data: APIsec, a company that provides API security testing to companies, confirmed it secured an exposed internal database containing customer data — including detailed scans of its customers' API endpoints, which researchers at UpGuard found connected to the internet without a password. I spoke with APIsec's founder, who initially said the data in the database was "not usable," but backtracked when I presented him with evidence of exposed customer data. (Disclosure: I wrote this story.) (via UpGuard, TechCrunch)
Move over, Signalgate. It's Gmailgate time: Several members of the White House's National Security Council used their consumer Gmail accounts for government business, including one staffer who shared "sensitive military positions and powerful weapons systems relating to an ongoing conflict," per emails seen by The Post. As for the top national security advisor Michael Waltz, who a couple of weeks ago made (a lot of) headlines by accidentally inviting a journalist to a Signal group chat to discuss bombing targets in Yemen, used his own Gmail account to share "less sensitive, but potentially exploitable information." 🫠 (via Washington Post ($), @John_Hudson)
Seattle airport hack hits thousands: Some 90,000 people will receive notice that their personal information was stolen in a ransomware attack that knocked out much of the Port of Seattle and Seattle-Tacoma International Airport for several weeks during August 2024. The data included government-issued ID numbers, which — you know, for an airport, that's not great. (via KOMO News Seattle)
~ ~

~ ~
THE HAPPY CORNER
A happy Sunday to you! Welcome back to the happy corner. Only good vibes from here on out.
First up; from @micahflee: clean OPSEC advertised, clean OPSEC achieved.

I don't know who needs to hear this, but iPhones and iPads now have an HTTPS certificate viewer in Safari. More from the WebKit blog. In related stats, TIL that more than 87% of all internet connections use HTTPS. The more you know!
Skeezy job alert: Are you willing to hack and take control of Chinese websites for a random person for up to $100,000 a month? This hapless hacker keeps pinging security researchers claiming to have this sketchy job for them, even if nobody can figure out quite what the actual deal is.
And finally this week. Bonus cybercat, plus heartwarming thread.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber-cats-dogs, who are seen here looking absolutely shattered after a long day hacking. Many thanks to Keegan P. for sending in!

Ding dong, it's the cyber-cat gong. Send in your cybercats or non-feline friends! You can email at any time with a photo and name of your cyber cat (or friend) and they'll be featured in an upcoming newsletter. Sent in before? Send an update!
~ ~
SUGGESTION BOX
That's all for this week. Feel free to get in touch if you have anything for the newsletter. I'll never say no to a cyber cat (or friend). This newsletter is run on coffee, your generosity and donations, and cybercats.
Enjoy your week and I'll catch you next,
@zackwhittaker