this week in security — april 7 edition
THIS WEEK, TL;DR
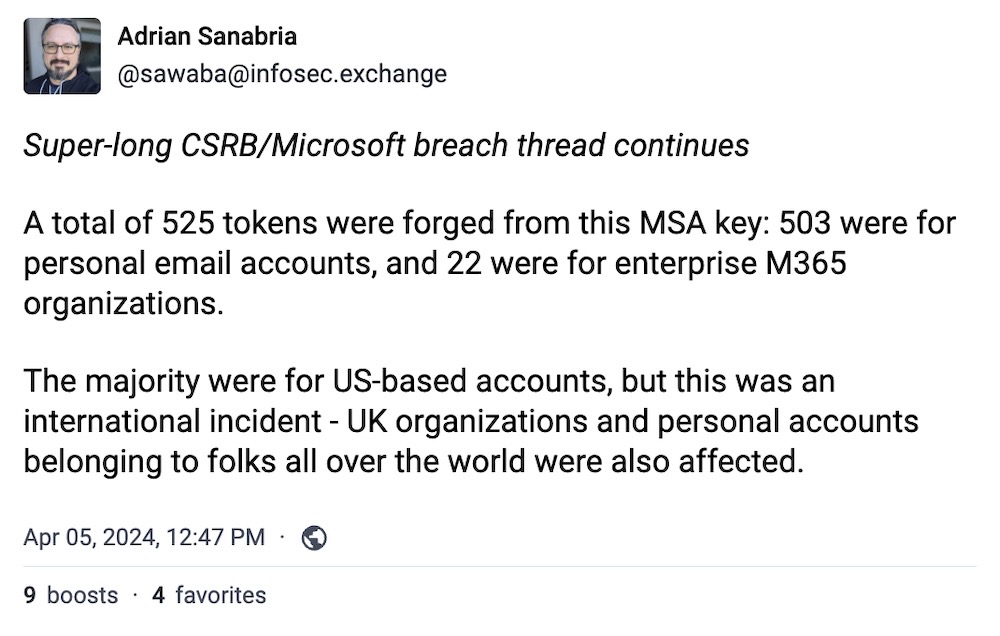
U.S. cyber board rips Microsoft for 'cascade' of failures in Chinese hack
Washington Post ($): Remember that Microsoft email cyberattack? No, not that one. You know, the big email breach? No, not that one either. We're actually talking about the 2023 stealthy espionage campaign that allowed Chinese hackers to steal an email signing key from Microsoft, which acted like a skeleton key for everyone's Microsoft-hosted emails, including highly protected U.S. government accounts. Or, as the Cyber Safety Review Board described the incident in its official post-mortem, the theft of the email signing key was caused by a "cascade of avoidable errors" on Microsoft's part. The theft of that email key allowed the subsequent raiding of sensitive government inboxes. Hate to spoil the surprise, but Microsoft still isn't 100% sure how its key leaked and the root cause may never be known, the CSRB report says. Much more analysis from @ericgeller and @sawaba on the report's findings.
More: CISA | Associated Press | The Verge
The mystery of 'Jia Tan,' the xz backdoor mastermind
Wired ($): We're now into week two of the xz backdoor saga, with all eyes on Jia Tan, the developer who planted a backdoor in the common xz compression utility in many Linux distros and now-accused nation state 'persona' allegedly behind the years-long campaign. If successful, Tan would have backdoored much of the world's heavyweight servers... if their backdoor code wasn't caught in time by a lone Microsoft engineer. Given the time, effort and patience, security firms point the finger of blame at a likely nation-state actor — perhaps one of the usual suspects, China, North Korea, Russia, or maybe others — behind the effort. All eyes are now on the open source community, or rather, the big tech giants sapping resources without investing or supporting the community. Open source is free and massively underfunded (or appreciated). Big Tech makes billions off the backs of ordinary people — especially open source developers — and Big Tech can and should do more to support open source.
More: 404 Media ($) | The Intercept | SecurityWeek
Google to delete records from 'incognito' tracking
BBC News: Google Chrome's incognito mode wasn't really what it was billed to be. In this day and age of ubiquitous web tracking and monitoring, it's pretty difficult to escape Google's massive data collection efforts. Google's ostensibly "private browsing" mode promised to stop collecting data on its users, but still did — including analytics, cookies, and apps — and a class action suit finally took Google to task. The class action settlement — if approved by a judge later this year — would force Google to delete the data it shouldn't have ever collected. Google, for its part, said it was "happy" to delete old data that it claimed was never associated with individuals. This was ultimately a lawsuit fought over marketing — and all the reason why companies should not claim something that is patently false. Using incognito mode to prevent online surveillance is like relying on a raincoat to protect you from lava. If you want to browse the web anonymously, use Tor.
More: Wired ($) | Reuters ($) | The Guardian
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
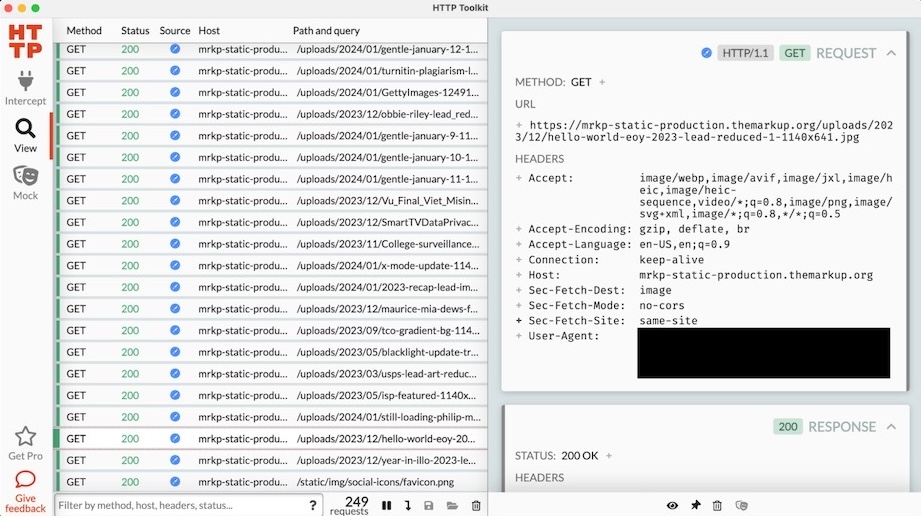
Here's how you can test your kids' smart toys for privacy flaws
The Markup: Once again, The Markup delivers the goods on how it carries out technical tests to verify the security and privacy claims of kids' toys, and other technologies. Using tools like HTTP Toolkit and IoT Inspector to intercept the traffic between Wi-Fi and Bluetooth-connected devices, you can analyze the network traffic to ensure that the data flowing across the internet is in fact secure (or not leaking private information). Sometimes it's good just to check that a device isn't spitting out gobs of data, which The Markup also found.
Poland launches inquiry into previous government's spyware use
The Guardian: A new Polish administration — some of whom were subject to Pegasus spyware targeted by members of the previous government, no less — said it will begin notifying victims whose phones were tapped during the previous administration, run by the Law and Justice party. Pegasus can extract all of the data from a phone from over the internet, and is believed to be sold exclusively to governments. In Europe, that's Poland, but also Hungary, Spain, and Germany.
Zero-day exploits get costlier as companies harden products
TechCrunch: Exploit-selling startups are offering millions of dollars for previously undiscovered tools and vulnerabilities that can hack into iPhones, Android devices, WhatsApp and Apple's iMessage. Over the years, the price of these exploits has gone up as tech companies are investing more in security, and vulnerabilities are getting more difficult to find. More from @lorenzofb.
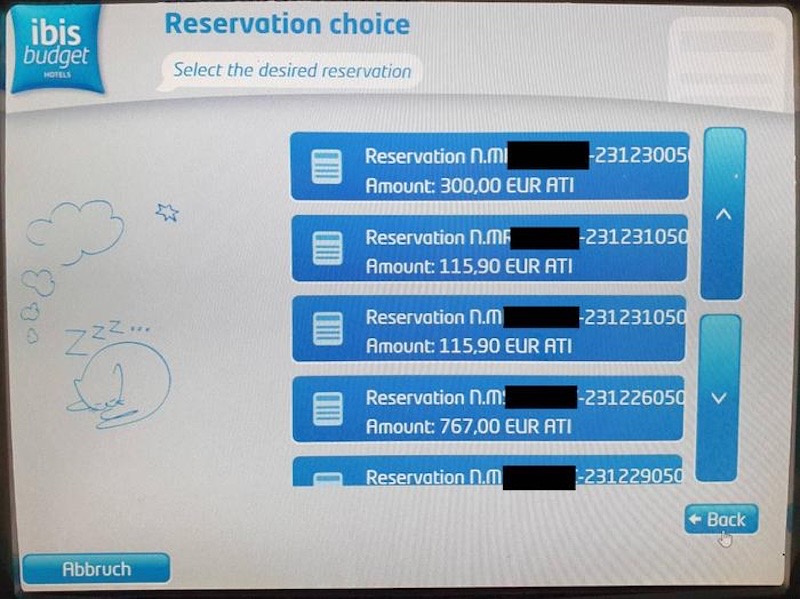
Hotel self check-in kiosks exposed room access codes
SecurityWeek: Self check-in kiosks at Ibis Budget hotels across Germany and other European countries had a vulnerability that exposed keypad codes for entering guest rooms, according to new research by Swiss IT security firm Pentagrid. Patches were rolled out within a month of the firm discovering and reporting the bug. The bug was found by mashing the digital display with dashes, instead of the booking ID, which returned guest access codes. Whoops!
Omni Hotels says widespread outages caused by cyberattack
The Record: Speaking of hotels... Omni Hotels & Resorts says a March 29 ongoing cyberattack is causing outages across its network. The company, which operates dozens of hotels and resorts across the United States, said it shut down certain systems to "protect and contain its data." More on Omni's website.
~ ~
OTHER NEWSY NUGGETS
Hack back, get recognized: BBC has an interesting story on how Ukraine is celebrating and awarding vigilante hackers who target Russia in response to the Kremlin's ongoing invasion and occupation of Ukraine. The story details one 53-year-old hacker, who goes by Voltage, who was recognized for their help in targeting Russian systems and targets, as well as stealing data from hacked webcams — some of which helped reveal the mass movement of Russian tanks towards Ukraine. It's believed to be the first time a country has awarded hackers for malicious and possibly criminal hacks. But this was also an illegal and criminal war that Russia started, so go figure. (via BBC News)
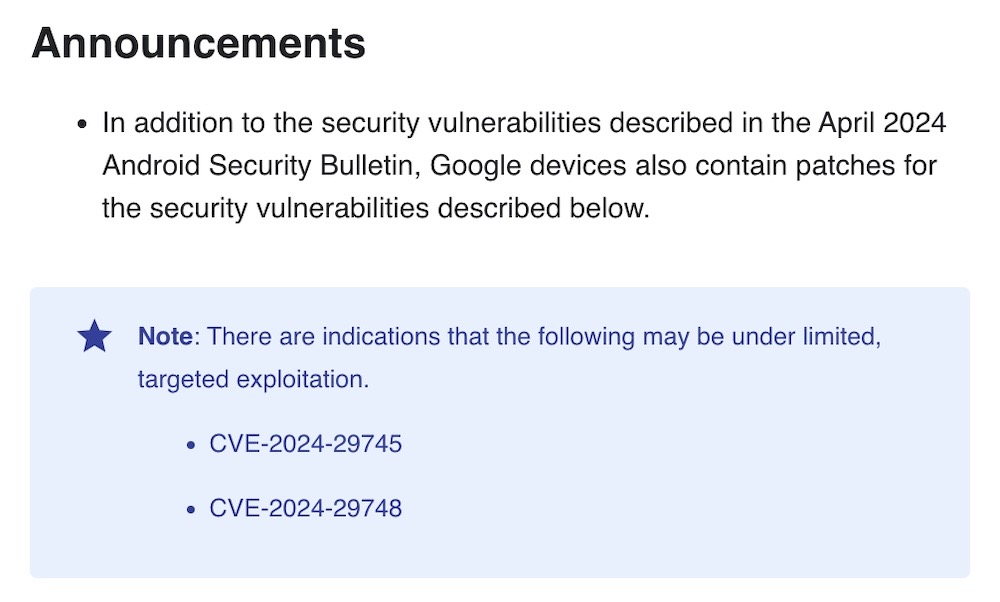
Pixel phones targeted by forensic zero-days: Two vulnerabilities found in Google's Pixel phones are being actively being exploited in the wild by forensic firms. (It's not just spyware makers, remember...) Google has fixed the two flaws, CVE-2024-29745 and CVE-2024-29748, which Google said were under "limited, targeted exploitation." The folks at @GrapheneOS have a great thread on these bugs. It's worth noting that the bugs are not specific to Pixel phones. (via Pixel Security Bulletins, @GrapheneOS)
New day, new theft of government data: The Security Department is investigating a possible cyber incident after a threat actor claimed to steal sensitive information from government contractor Acuity, which confirmed an incident. Specifics of the data breach have yet to be revealed, so expect more to come. Some of the data apparently includes information of federal employees. (via Bleeping Computer)
CISA sounds Russian cyber alarm: U.S. cybersecurity agency CISA quietly issued an emergency directive this week warning civilian federal US. government agencies about the ongoing cyberattack at Microsoft by Russian-backed hackers targeting executive email inboxes. (See? It's not easy keeping track of these Microsoft breaches!) CISA has not made the directive public — yet — for reasons unclear. Microsoft continues to try to mitigate Russian SVR hackers from its systems, at a time when the federal government's reliance on Microsoft's technology is under increasing scrutiny. (via Cyberscoop)
~ ~
THE HAPPY CORNER
At last. It's the happy corner. *dances*
First up, CISA has a new page on digital security for high-risk communities, including activists, journalists, human rights defenders, and more. It's a pretty great resource for folks who fear targeting from cyber threat actors (and governments). Meanwhile, @runasand has a couple of blogs out this week looking at the U.K.'s guidance for high-risk individuals, as well as analysis of Norway's recent threat assessment.
For those (hopefully) looking to the skies for this Monday's eclipse, University of Oklahoma PhD student @burgwx has a really cool cloud cover forecast tool. Note: there's no HTTPS, so expect a browser error. (via @sohan)
This week I was extremely lucky to get an early copy of @josephcox's new book, DARK WIRE, the true story of how the FBI ran its own startup, Anom, to wiretap the criminal underworld. It's the inside scoop of how the feds tapped into the comms of tens of thousands of criminals — hitmen, money launderers, drug traffickers — and the implications for everyone else's privacy. The reporting is out of this world and the storytelling is exquisite. Preorder today!

And finally. This post got deeply embedded into my brain, just like when I overheard someone at Shmoo last year describing DNS as "Dennis."
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Didi, this week's cyber cat. This is the face of a content and happy cat, knowing full well that they're using strong unique passwords in a password manager and MFA on everything. It's good to feel cyber-secure. Many thanks to Dan K. for sending in!

Send in your cyber cats! Feel free to drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's all for now! I hope you enjoyed this week's newsletter. As always, you can get in touch by email with any suggestions, feedback, or any other cool stuff you want to send in. It's always great hearing from you — and especially your cyber cats.
Catch you next Sunday,
@zackwhittaker