this week in security — april 9 edition
THIS WEEK, TL;DR
Western Digital discloses network breach, My Cloud service down
Bleeping Computer: If you're a Western Digital customer and you can't access your cloud-stored files, it's not just you. WD said in a press release that it experienced a "network security" incident (code: cyberattack) that's looking eerily like ransomware. We have yet to confirm ransomware since WD hasn't said much — or anything, really — beyond its status page that's lit with red. Customers who backed up their data with WD should probably start to think worst-case (though some customers are able to get access to their local files again while its My Cloud service remains offline). Most of the company's services were broken or hit by the outage, including SanDisk products, and much of WD's website displayed "503" errors during the week.
More: Reuters ($) | TechCrunch | MyCloud Status | @westerndigital
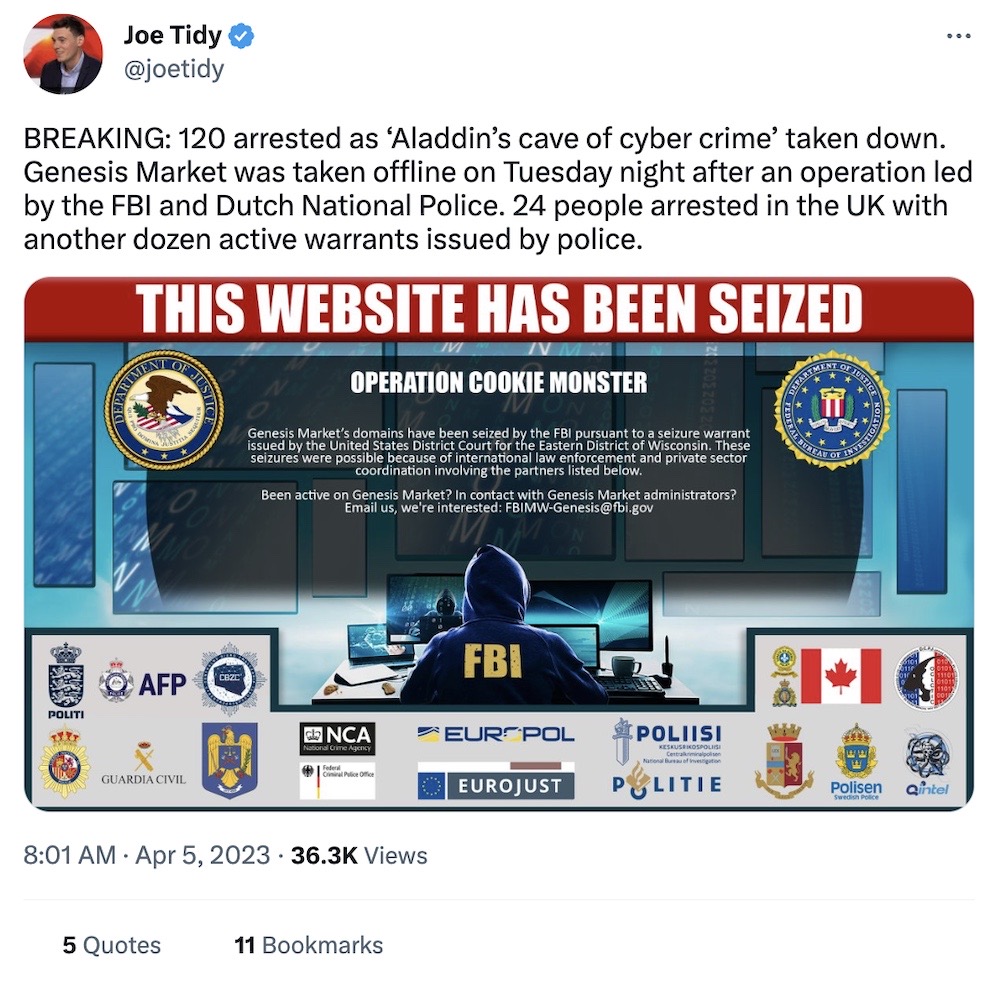
Genesis Market cybercrime forum shut down by police
BBC News: This week international law enforcement took down a global criminal marketplace for stolen logins and credentials, Genesis Market. The operation was named Operation Cookie Monster for a good reason: tens of millions of credentials, including session cookies, were for sale on the market, allowing buyers to break into online accounts as if they were the person themselves. No two-factor needed (since session cookies are set after 2FA is authenticated). The FBI, which participated in the effort, provided millions of victim email addresses to Troy Hunt, who runs Have I Been Pwned, allowing victims to check if their data was compromised. More from the National Crime Agency, which apparently can't spell the name of the market it just helped to seize. That's quite a few marketplaces that have all shuttered in recent months...
More: National Crime Agency | Trellix | Troy Hunt | @briankrebs toots | @joetidy tweets
Alcohol recovery startups Monument and Tempest shared patients' data with ad giants
TechCrunch: Remember a few weeks ago when mental health startup Cerebral was caught sharing millions of patients' data with advertisers by way of near-invisible trackers on its website and app? Now two more startups are caught up in "Healthcare Tracking-Gate" (as I'm going to call it). Two alcohol recovery apps, Monument and Tempest (which Monument bought last year) shared more than 100,000 patients' personal data — including survey responses containing information about a person's alcohol consumption — with Google, Facebook, Microsoft and Pinterest. That's despite its own website claiming that survey answers are "protected" and "used only" by its care team. This data sharing went on for years — since January 2020 for Monument and since late 2017 for Tempest. They had one job and couldn't even do that. All of this follows Stat and The Markup's work last year, dredging up dozens of startups into the bright light of transparency. Now, the U.S. government department overseeing the health privacy space (clearly caught off guard) is now trying to mop up the mess. (Disclosure: I wrote this story!)
More: PopSci | The Verge | DocumentCloud (breach notice)
Pentagon investigating leak after classified war plans leak on... Discord
Bellingcat: Who hasn't accidentally pasted their password into Slack before? You've never mistakenly dropped a cat photo in an email to your boss instead of the PDF they asked for? Whomst among us hasn't posted classified Five Eyes documents to the open internet to show off to all your internet friends? (Case in point, see below.) Both the Times and the Journal say they've seen the posted docs, which first appeared on a... Minecraft Map Discord server in early March, but nobody seemed to notice until they were reposted to social media. Some of the leaked documents include information related to spy satellites and war strategy plans related to Ukraine. U.S. officials are scrambling (obviously). Interestingly, some of the leaked data was actively modified to decrease Russian casualties and increase Ukrainian estimates of war deaths. Some are suggesting the leak is part of a Russian disinformation effort. Wouldn't be the first time, but Discord? Really?! If you thought that was unlikely, example number two from January: "Military documents relating to the F-16 fighter jet were shared by a player attempting to win an argument." We'll be keeping an eye on this one!
More: New York Times ($) | Wall Street Journal ($) | @AricToler
Sex traffickers used Life360 to control victims
Forbes ($): Sex traffickers are using "family tracking" apps like Life360 for controlling and abusing people, described by one U.S. attorney as turning a victim's phone into an "electronic leash." The app has long drawn scrutiny over its security, privacy, and data practices, including the selling of precise location data on its near-50 million users. (Gross.) Forbes has the receipts, showing how Life360 is used to follow a person's "every move." Life360's CEO Chris Hulls told Forbes that this issue has "never once come up at an exec level." Then either they're part of the problem since executives clearly have no idea that their products are used for abuse (which is on them), or that the executives are willfully ignoring it (also on them). Life360 later admitted that it knew of at least four cases related to sex trafficking in the past year. Solid reporting by Forbes' @iblametom.
Archive: The Markup | More: @iblametom tweets | @newblackman
~ ~
THE STUFF YOU MIGHT'VE MISSED
Reporter gets SIM swapped, mercilessly tracks hacker
Insider ($): @averyhartmans was SIM swapped while vacationing. The classic telltale sign: service suddenly drops. Someone hours away had walked into a Verizon store with a fake ID to steal her phone number. Hartmans spent eight months tracking down the hacker with some help along the way. The horrible reality is that: "My identity theft was made possible, in no small part, by the very companies and officials who were supposed to prevent it." Yeah, exactly! Phone giants like Verizon (and plenty of others in the story) are notoriously crap at handling data issues. Accepting fake IDs is clearly one of them.
Biden's cybersecurity 'dream team' undone by internal strife
Bloomberg ($): This was breathtakingly good reporting by @katrinamanson and @williamturton, who spoke with dozens of current and former White House officials who told them that Chris Inglis, the inaugural White House national cyber director — effectively the person who advises the President on all things cyber — left his post after battles and clashes with, well, one other very senior cybersecurity official in particular.
Arrested and extradited over a false face match
New York Times ($): If you want to feel the nuclear heat of the pure unadulterated fury of injustice, read this New York Times piece about how Randal Quran Reid, a Black man living in Georgia, was arrested on warrants related to accusations he was involved in thefts in a state he had literally never been to. Reid spent a week in jail before he was let free. The cause? A bad facial recognition match, specifically Clearview AI (and extremely bad policing). For those interested in building a facial recognition system that identifies smug-looking morally bankrupt CEOs with links to white supremacists, I can think of one certain CEO who would get a 100% match.
What happens when your AWS keys are leaked?
Xebia: Have you ever wondered what happens behind the scenes when Amazon's digital squirrels find your AWS cloud keys on GitHub? This blog post explains how it works — by deliberately leaking some AWS keys. A fun experiment!
Apple ships urgent iOS fixes for zero-days under attack
SecurityWeek: Apple has shipped iOS 16.4.1 with an emergency fix for all iPhones and iPads running the latest software. @donnchac said the bug was part of an exploit chain, which was discovered in the wild with Google TAG, which investigates government hacking. This is one of those times where you should update immediately (yes, rare bold!). I'm sure we'll hear much more about the impact of these exploits very soon...
~ ~
~ ~
OTHER NEWSY NUGGETS
ICE should chill on the subpoenas: An agency database obtained by Wired ($) shows that ICE is using an obscure subpoena authority — so-called 1509 summonses — that are explicitly and exclusively meant for investigating imports or unpaid customs duties, but are being served on schools and abortion clinics to obtain records without a warrant. Very concerning stuff, and great reporting here by @dmehro. Relatedly, I saw a sizable group of people in Manhattan on Friday outside LexisNexis' headquarters protesting the data broker's $22 million contract with ICE, which also allows it to get data on immigrants without a warrant. I have to say, it was heartening to see people taking up active protests against data abuses. (via Wired ($))
Hackers could remotely open garage doors, company borks fix: A security researcher found a series of flaws in Nexx smart garage door openers that allowed anyone to remotely open garage doors over the internet. Both the researcher and Motherboard, which first reported the story, tried to disclose the bug to Nexx, which refused to fix only until the bug was disclosed. That's when things went even more south, as Nexx screwed up the fix by disabling all internet access to the device — rendering it effectively useless for many of the customers who bought it. (via Motherboard, Sam Sabetan)

Have some malware with your tax return: eFile.com, an IRS-authorized tax preparation service provider, was found serving JavaScript malware for weeks. Weeks! Worst time for it, too, since Tax Day is around the corner here in the United States. eFile.com's website was serving the malware up until April 1 at least. Looks like the payload was a malicious executable. (An analysis of the malware can be found on SANS.) (via Bleeping Computer)
Tesla cameras are snooping: The cameras in Tesla vehicles can capture "highly invasive videos" and images, which are shared with Tesla staff, who passed them on to other employees. That's according to extensive reporting by Reuters ($). So that's Teslas, Roombas, to some extent Eufy... maybe let's just assume that anything with a camera and an internet connection is going to be uploading your data to the internet and accessible by someone at the other end. This news also comes in the same week that a security researcher found a bug in a Tesla internet-facing internal system that allowed access to the Tesla Retail Tool, which stores "confidential IT and business information," including device and web logins for ISP and utility accounts. (via Reuters ($), Evan Connelly)
Fortra seeks good PR after ransomware attack: Microsoft and Fortra, the owner of the Cobalt Strike pentesting tool, are using court orders to take down cracked copies of Cobalt Strike that have been used in malware operations for years. Yes, that's also the same Fortra that was recently hit by a ransomware attack that it's absolutely, desperately trying to pretend isn't a thing (though it absolutely is) — even though the attack has already exposed a million patients' data and 140,000 Social Security numbers. As the excellent @campuscodi notes, "All it took was for Fortra to get owned for the company to care about the Cobalt Strike abuse. Guess they needed to positive PR all of a sudden." (via Microsoft)
U.K. criminal records office was hacked: ACRO, the U.K. criminal records office, admitted that the "website maintenance" it had claimed for more than two weeks was in fact a cyberattack, also known as A Huge Fib™. ACRO provides docs to British nationals whose criminal records are attached to visa applications abroad. (via The Record)
MSI hit by cyberattack: MSI, a maker of motherboards and chips — not "Massive Security Incident" as I initially thought — was hacked, and more than a terabyte of databases, source code and BIOS tools were stolen. In a statement, the company urged users to "obtain firmware/BIOS updates only from its official website," after a gang claimed on its dark web site that it has all the tools necessary to "develop a potentially malicious BIOS and then digitally sign it." In other words, MSI is asking users not to accidentally hack themselves by installing dodgy updates. (via The Register, @ravirockks)
~ ~
THE HAPPY CORNER
Happy Sunday, Easter, Passover, and Ramadan. Welcome to the happy corner.
First off, slava Ukraini but especially to the Ukrainian hackers who broke into an account used by a pro-Russian blogger to raise $25,000 to send drones to Russian troops, and used the blogger's credit card to send him a huge shipment of sex toys instead. "The hackers claim that they ordered the sex toys on AliExpress using [the blogger's] credit card," per @gluley, who has more on the story. The blogger "planned to simply return the items," but found out that the store — for understandable reasons — doesn't offer refunds for sex toys. Chef's kiss, no notes.
Did you know that you can boot and run a Windows 95 PC inside Minecraft and play Doom? Old news, but news to me.
Congrats to former NYT/Wirecutter privacy and security journalist @thorin, who joins the EFF as its new resident privacy and security activist, which'll include working on the EFF's Surveillance Self-Defense, an already excellent resource that will only get better.
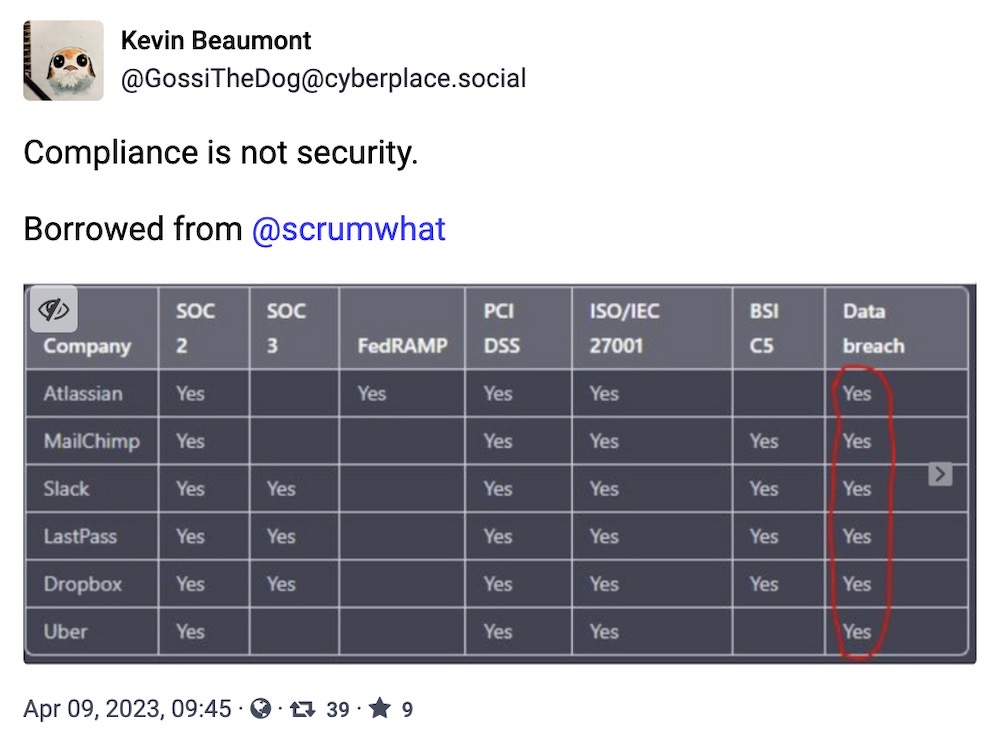
And, finally. A friendly reminder from your neighborhood porg that compliance alone won't protect you from a data breach.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Keope, a two-month old kitten, who clearly has a long way before they can call themselves a fully-fledged cyber cat. That's not even the right kind of keyboard for hacking, little one! Thanks for sending in, Enrico F.!

Keep sending in your cyber cats (or their friends). Send in a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
....Aaannnd I'm out! Thanks so much for reading — and sorry that this week's newsletter was a little later in the afternoon than usual. Hope you liked this week's dispatch. My email is always open if you have any feedback. Enjoy your week!
Catch me on Mastodon if you're there,
—@zackwhittaker