this week in security — august 1 edition
THIS WEEK, TL;DR
A controversial tool calls out thousands of hackable websites
Wired ($): PunkSpider, a search engine that crawls the web for vulnerable websites, is back a decade after it was first conceived. PunkSpider will let anyone search websites for known vulnerabilities, which the researchers hope will encourage website owners to fix them before malicious actors exploit them. (I guess it comes down to who can search the fastest?) This is an extreme version of "carrot and the stick," granted, but not everyone is thrilled with the idea, even if it's already helping some major websites find and remediate simple but potentially damaging flaws. It's a controversial project, and even its creators are aware of the risks that PunkSpider brings. "But we need to try something new," they said.
More: @a_greenberg tweets | @weldpond
Secret documents reveals new Iranian offensive cyber unit
Sky News: Documents obtained by Sky News have revealed a new Iranian offensive cyber unit, dubbed Shahid Kaveh, a part of Iran's Revolutionary Guard. The documents show how the unit could use an offensive cyber attack to sink a cargo ship or blow up a fuel pump at a petrol station. The documents were verified by Mandiant and describe "simple, opportunistic attacks" against potential targets. @haynesdeborah, who reported this story, cited a source as saying that the unit was "creating a target bank" to be used whenever [Iran] sees fit."
More: @haynesdeborah | @ridt

Apple releases fix for iOS and macOS zero-day, 13th this year
The Record: (Un)lucky number 13. That's how many zero-days exploited in the wild that Apple has fixed this year, according to @campuscodi. The bug, known as CVE-2021-30807, already has proof-of-concept code out. A blog post describing the bug in more detail can be found here. The bug was found in IOMobileFrameBuffer, a kernel extension for managing the screen frame buffer, which if abused could run malicious code on the vulnerable device. If you haven't already, update your Apple devices today.
More: The Register | Saar Amar | Apple
French authorities confirm Pegasus targets, providing first independent government verification
NPR: NSO has reportedly cut off some of its government customers from Pegasus as the company investigates "possible" misuse of the spyware. It comes after the Israeli government "visited" NSO's offices this week (less a raid, apparently). NSO says it has 60 customers in 40 countries — many considered authoritarian regimes — serving mostly intelligence agencies, law enforcement and some military customers. French authorities meanwhile confirmed traces of Pegasus spyware on several phones of French targets, which is the first government to independently confirm Amnesty's findings from the Pegasus Project. @runasand has an English-language tweet thread on the Le Monde story, which is in French.
More: Le Monde | @razhael
Meet Paragon, a U.S.-funded Israeli startup that 'hacks WhatsApp And Signal'
Forbes: Speaking of spyware makers... move over NSO, there's yet another new secretive surveillance startup in town. Paragon was founded in 2019 by ex-Israeli intelligence officers, is based in Tel Aviv, backed by Battery Ventures, and has 50 employees, but very little else is known about the company, which gives police the ability to steal encrypted instant messages from a number of apps — including WhatsApp and Signal. But it looks like Paragon is at least trying to avoid some of the trouble that NSO has faced by selling to countries that aren't authoritarian or non-democratic. Yeah, that worked so well for everyone else, too...
More: @jsrailton | @marwasf
Justice Department says Russians hacked federal prosecutors
Associated Press: And, a quick throwback to the SolarWinds espionage attack. The U.S. Courts confirmed this week that dozens of court systems — including the Southern District of New York (where a lot of big indictments drop) — were hacked by the Russian spies behind the campaign. We knew that the courts were hacked back in January, but now the scale of the breach is coming to light. The hackers gained access to at least one Office 365 email account in 27 U.S. Attorney offices between May-December 2020. It's feared that the Russian spies may have obtained sensitive or confidential documents that could jeopardize court cases
More: BBC News | Justice Department
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Kaseya "did not pay" ransom to get REvil decryptor
Kaseya: So that's that then? Except it doesn't really answer how Kaseya got the universal REvil ransomware decryption tool, which everyone seems to be asking. If you recall, Kaseya was hit by a supply chain attack that delivered ransomware to some of its customers. It did, however, say that it got the tool from a third-party. (A friendly government, maybe, or one trying to curry favor?) And Kaseya still won't comment on the NDA it's making its customers sign before they'll be allowed to decrypt their files. So many ethical questions...
Cyber job listings excluded Colorado workers after salary transparency law went into effect
Cyberscoop: A pay transparency law went into effect in Colorado, and now a ton of cyber job listings won't hire in the state. The Equal Pay for Equal Work Act went into force in January, and advocates say it's a powerful tool for closing the gender wage gap. But some companies like Contrast Security and Rackspace are excluding Colorado from their hiring plans. Both (predictably, and cowardly) declined to comment. This was solid reporting by @TonyaJoRiley, if not extremely frustrating to read.
From stolen laptop to inside the company network
Dolos Group: So what can you do with a stolen laptop? Can you get access to that company's internal network? Yes, absolutely, and this post shows just how it's done.
British Columbians' personal information for sale online after health company extorted
CTV News: Another day, another extortion attempt. This time it's Homewood Health, a mental health services provider in Ontario, which was hacked and data stolen. Now the data is online for anyone to download. It's not known how many people are affected so far. Reminds me of the Vastaamo breach in Finland in 2020.
Here’s what that Google Drive 'security update' message means
Ars Technica: If you got an email about a "security update" that will be applied to your Google Drive, it's a real email. On September 13, Google will roll out a new security update to make it tougher to guess Google Docs links. (Yes, those links are guessable!)
~ ~
OTHER NEWSY NUGGETS
Hacker downloads close to 300,000 Estonian ID photos
Less than ideal news from Estonia, where a hacker obtained close to 300,000 names and identity photos after a break-in of the state's information systems. The culprit is reportedly a resident of the capital, Tallinn. The data alone wasn't enough to do anything with, officials said. Estonia is one of the most digital nations in the world.
Turn off, turn on: Simple step can thwart top phone hackers
Turning your phone off and on again can help thwart some phone hacking efforts. That's because restarting your phone wipes the temporary memory in your phone where malware can lurk. It's been reported that phone malware struggles to gain persistence, making phone reboots an effective tactic against some attacks (though, less so with zero-clicks, which can just be sent to reinfect a target again). Some Android phones come with an auto-restart feature as standard.
QR codes are here to stay. So is the tracking they allow
QR codes are all the rage these days. (Thanks, pandemic.) You see them everywhere, especially restaurants. But many QR codes are packed with tracking code, raising concerns among privacy folk. But it's not clear what these QR codes are actually tracking or where your data goes because privacy laws are so far behind in the U.S. In many cases, yes, you can still ask for a paper copy of the menu (and you probably should).
~ ~
THE HAPPY CORNER
There isn't much by way of good news this week. (You know you can always get in touch?) But this did, admittedly, make me chuckle.
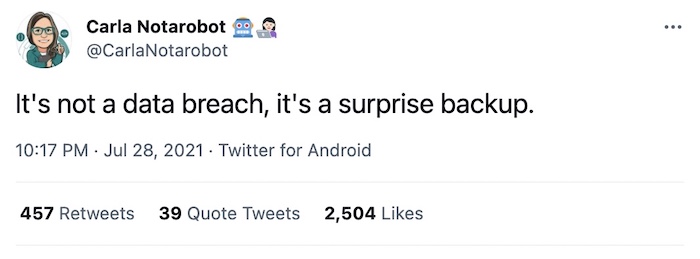
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Luna. Here she is brushing up on her audit preparation plans, and judging you for not doing the same. A big thanks to Wendy N. for the submission!

Please keep sending in your cyber cats (or their friends!). Send in a photo with their name here!
~ ~
SUGGESTION BOX
That's it for this week. Any comments or feedback, feel free to drop them in the suggestion box or email me at this@weekinsecurity.com. Have a great week — see you next Sunday.