this week in security — august 10 2025 edition
THIS WEEK, TL;DR
Black Hat kicks off annual 'Hacker Summer Camp' week in Las Vegas
Welcome, and happy Hacker Summer camp week to all those who celebrate! It's that time of year where hackers from around the world descend on Las Vegas to see and hear new cybersecurity talks and research. Black Hat kicked off by featuring keynotes from Citizen Lab's director, who warned of rising U.S. authoritarianism at a time when hackers can fight back, and the ACLU's top surveillance lawyer, who called for better privacy and better care of our data. Thinking about people, their data, and how to protect it was a key theme at the show, with NSA top brass warning small defense businesses to shore up their security, and others are helping security leaders plan for the worst. The show also dished out some fun new findings, like hacking satellites; uncovering privacy flaws in Apple's new AI features; and a bug that left Dell laptops exposed to hacks, per Reuters ($). There are plenty of photos from the show, so you, like me (who wasn't there this year), can live vicariously through others who were on the ground.
More: HelpNetSecurity | The Register | Cyberscoop | Wired ($) | TechCrunch | @pjhillier | @metacurity
Def Con hacking conference follows as new research drops
And as soon as Black Hat is done, it's time for Def Con, the slightly more chill and laid-back affair compared to Black Hat. The Register had a great tl;dr ahead of the week. Def Con founder Jeff Moss chatted about the show's history, as well as with ex-NSA director Paul Nakasone, who — albeit slightly tipsy — warned about the "new direction" we're collectively moving in. But we also saw some top research from the show, including how a school vape detector turned into a wiretap, per 404 Media ($); how a low-cost quantum sensor could advance the field according to Wired ($); and how hackers are helping to protect critical infrastructure, like water systems. Plus, a story from me about how a prolific SMS scamming operation netted thousands of stolen credit cards (disclosure alert!). And... if you think I was kidding last week about plugging in a keyboard into a bus... think again. (FYI, there may be more from Def Con next week as the show finishes at the same time this newsletter is written!) The happy corner below has some especially good news from Def Con...
More: 404 Media | Wired ($) | ABC News | TechCrunch | @kevincollier
Air France, Cisco, Google, and KLM hit by Salesforce data thefts
Bleeping Computer: What do Air France, Cisco, Google, and KLM have in common? They've all had data stolen from their Salesforce instances. Google became the latest corporate giant to admit it had some customer data stolen from a Salesforce server, attributing the hack to ShinyHunters. Google said in an updated blog post about the hackers that they were likely preparing a leak site to extort victims into paying them. (@Metacurity has a copy of the breach notification.) By all accounts, there's a fair number of affected companies so far. Cisco also said it had data popped in a suspiciously similar way. Bleeping Computer connected the Air France and KLM breaches to Salesforce, too. Of course, the excellent DataBreaches.net parses some of the latest developments, including the new victims. Whenever this supposed leak site comes out, expect it to make waves.
More: WWD ($) | TechCrunch | @campuscodi | @troyhunt
U.S. Courts warns of new hack affecting PACER federal courts system
Politico: OK, what year is this, 2021?! Nope, it's the year 2025 and we're back with yet another hack of the U.S. Courts record filing system, aka PACER. Politico broke the news this week that PACER, and many of the "sealed" and non-public files within — including witnesses and testimony — may have been accessed during a sweeping hack affecting multiple states. It's not yet clear who's to blame, but last time it was the Russians exploiting the SolarWinds software. This time it could be the same or anyone else in between, including state actors or non-affiliated cybercriminals. The U.S. Courts confirmed the breach soon after Politico's story, saying it's made security progress since the last hack (but evidently, not enough). I feel like there is a lot more to this story, and we may learn more soon.
More: U.S. Courts | Fedscoop | DataBreaches.net
THE STUFF YOU MIGHT'VE MISSED
SonicWall says dozens of attacks linked to 2024 bug, not zero-day
SonicWall: SonicWall said the five-alarm alarm over recently observed exploitation of its customers' firewalls devices was related to the older CVE-2024-40766 bug, which is already patched and not caused by a zero-day as first believed. That said, SonicWall said there have been around 40 incidents detected so far related to exploitation of the bug.
CISA sounds alarm about spicy Exchange security bug
CISA: U.S. cybersecurity agency CISA is warning about a new bug in self-hosted Exchange servers, aka CVE-2025-53786. If exploited, the bug can allow malicious hackers with a foothold already on the on-premise server to pivot to a victim's cloud-based systems in hybrid configurations. The bug hasn't come under exploitation yet, but CISA says it's serious enough to require government agencies to patch by... Monday. If you're affected, you should as well!
Mobile app library caught leaking users' personal data
Cossack Labs: An unnamed code library used in a mobile app for analytics was leaking customer data to its backend, including passwords and tokens. The library is now fixed. Apps can be packed with trackers and bits of code used by developers for analyzing bugs, for example, but can also contain logs and other sensitive information collected from the app. A reminder to be careful about what code you rely on, it can burn you (and your customers).
Encrypted chat apps caught spilling unencrypted data
DataBreaches.net: Broxis and Chatox claim to be secure messaging apps that tout their encryption, but both apps — owned by the same developer — were spilling their backend database containing reams of unencrypted names, usernames, passwords, chat messages and attachments... woooof. Who needs a repeat of Signal-gate, said nobody ever?
uBlock Origin Lite comes to Safari users
Apple App Store: The maker of one of the web's favorite open-source ad blockers, uBlock Origin, has released (for iOS 18.6 and later) a lite version for Safari users. That's huge news for users who want to browse the web free of ad trackers and other web snoops. (Additional shoutout to Wipr2, another excellent ad blocker with a history of privacy-preserving awesomeness.)
Microsoft's new NLWeb protocol hit by embarrassing bug
Medium ($): Security researcher Aonan Guan has already found a pretty glaring security bug in NLWeb, the new protocol that allows AI-style search for any website (me: so half the time it'll get it wrong?). The flaw allows any remote user to read sensitive files on the server, like API keys. Worse, the bug is a path traversal, meaning it's easy to exploit with a malformed web address (aka "three dots to root")... which, if you haven't seen researchers ripping into their ease of exploitability, you're missing out. Microsoft has since fixed the bug. The Verge has more.
OTHER NEWSY NUGGETS
Infostealers on the NHS network: Thousands of employee login credentials for accessing the U.K.'s National Health Service have been swiped by infostealing malware, putting the health network at risk of hacks. Infostealers are usually installed by way of a legitimate-looking but malicious app that's packed with password-stealing code. The NHS says it uses multi-factor authentication, which — sure, great — but a lot of infostealers also steal session tokens and cookies, which can be used to bypass MFA. (via Bloomberg ($))
Deux hacks, très mauvais: Two of France's largest phone providers have been hacked in recent weeks, the latest is telecom giant Bouygues, which confirmed a breach affecting the personal information of 6.4 million customers (out of about 27 million mobile users). (Disclosure: I wrote this story.) The breach page is hidden by "noindex" code so it's effectively hidden from search engines (companies: don't do this). Orange was hacked in late July, causing disruption to services, though little was disclosed at the time. (via Bouygues, TechCrunch)
San Francisco under tech bro surveillance: If you want to enjoy California without having your face, likeness, and conversations recorded by tech bros wearing AI hardware pins and wearables that watch and listen to everything you do, maybe avoid San Francisco for the foreseeable future. (via San Francisco Standard)
California mulls banning surveillance pricing: Staying with California... A new state bill would ban tech companies from using discriminatory surveillance pricing to jack up costs and fees using phone data. If the bill becomes law (and there's still a way to go), it would prevent car-sharing giants like Uber and Lyft from using a person's low phone battery or location data to artificially increase the cost of a car share under the assumption that the user will accept the fee. (via The Markup)
Senators slam UHC for (more) security failings: A pair of U.S. senators sent a letter this week ripping into health tech company Episource after a breach affecting over 5 million people's personal and protected health information. Episorce is owned by UnitedHealth — yes, the same insurance giant responsible for the biggest healthcare-related data breach in history. Now UHG is on the hook for this latest breach. (via Healthcare Finance, U.S. Senate)
TeaOnHer, a rival Tea app for men, also spilled users' data: First there was Tea, an app that allows "verified" women to post about men they date, which was hideously coded and exposed the government IDs that women uploaded to login to the app. Now, there's TeaOnHer, an app for men to talk about women. What could go wrong...? Except, well, everything. For TechCrunch (disclosure alert!), I wrote about how the app had at least two major security flaws that we found were exposing the private data of its users, including driver's licenses and more. From leaky apps to a flawed fish tank, please stop vibe coding your stuff and actually put security first. (via TechCrunch)
THE HAPPY CORNER
A very warm welcome to all! This is the happy corner.
First up this week, feel free to use this free and reusable "get out of meeting" card, courtesy of @evacide.
TIL: If you've ever wondered why some malicious hackers try to use regular apps, like Slack, Discord, and Telegram as their command and control servers, it's so that the network traffic blends in with the rest and is more difficult to identify. Here are some cats that illustrate the point.
Congrats to former CISA head Jen Easterly who joins Huntress as an adviser. Easterly told Axios she was eager to join to help secure "target rich, resource poor" organizations, like the critical infrastructure sector, which keeps the lights on and the water running.
Someone made a browser-ready version of Windows XP (and docs to go with it), if you want some instant early '00's nostalgia.
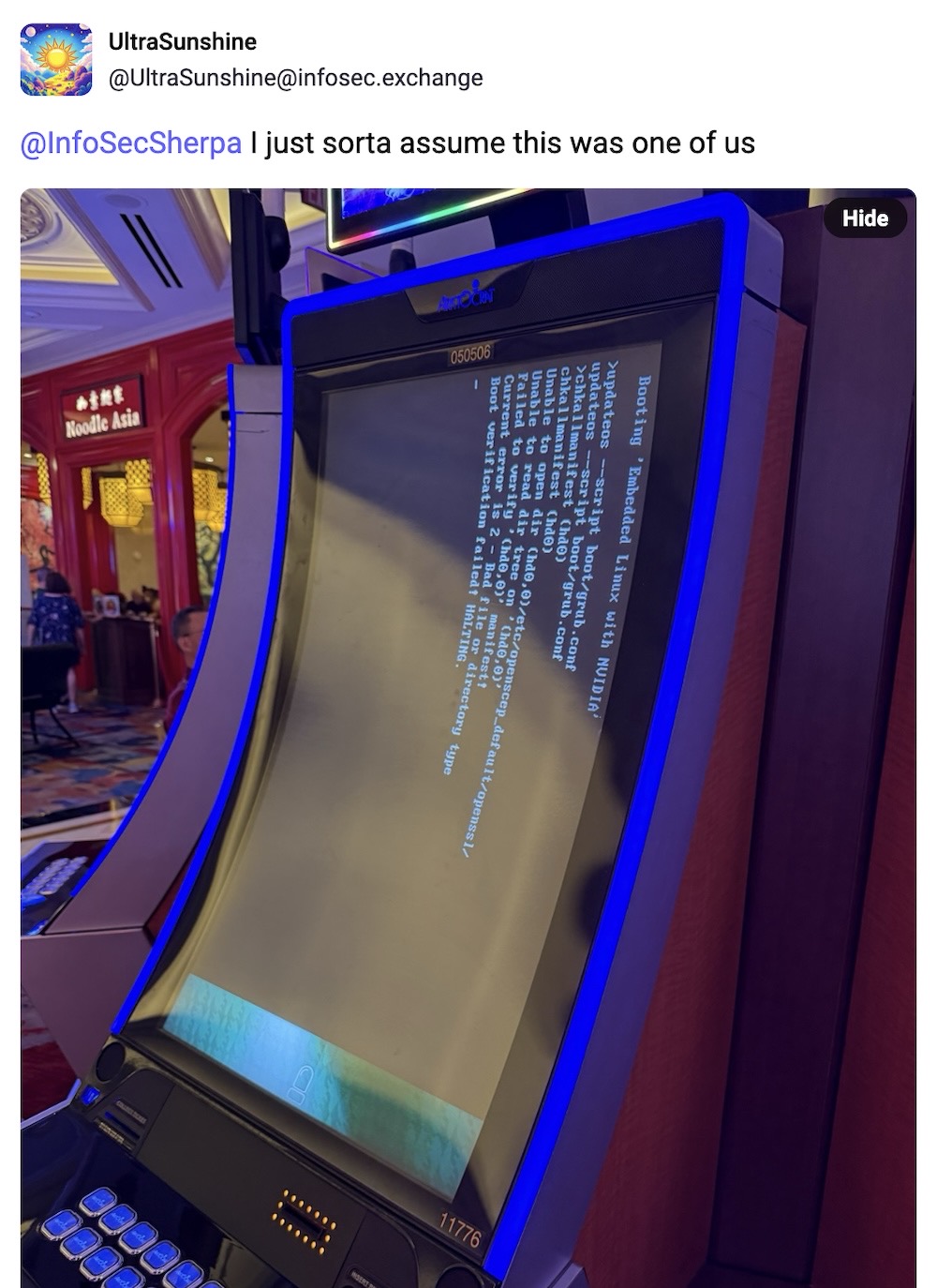
*in a very loudspeaker voice* "Can the hackers on the casino floor please stop interfering with the equipment... thank you."
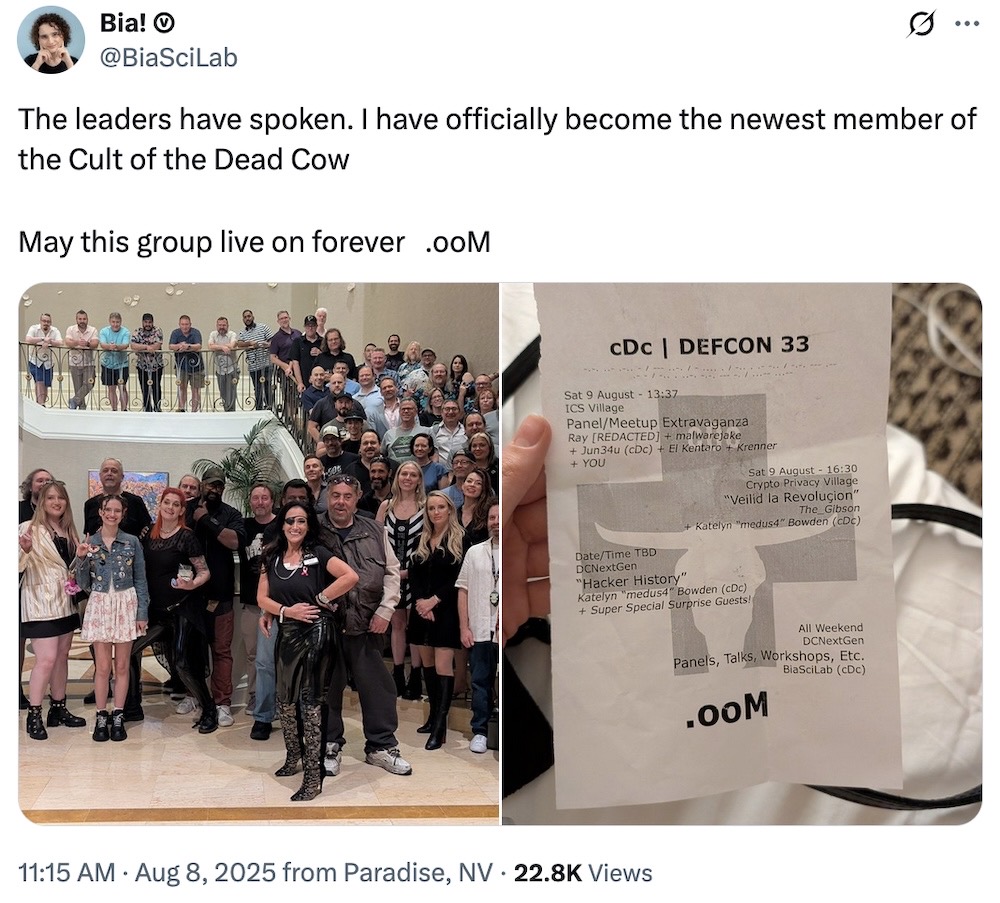
And... finally, but absolutely not least. A major congrats to hacker extraordinaire @BiaSciLab, the newest member of the Cult of the Dead Cow, the hacker supergroup that helped shape and change the world. What an absolutely incredible and well-deserved recognition for someone who is already leading the next generation of hackers! (via @RayRedacted, @medus4_cdc)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
CYBER CATS & FRIENDS
This week's two-for-one cybercat special features Batman (top) and Arya (bottom), who can be seen here snoozing in the sun after a long day hacking. Zzzzzz. Thanks so much to Emily Y. for sending in!

🚨 Send in your cyber cats! 🚨Got a cyber-cat or a non-feline friend? Send in an email with their photo and name and they will be featured in a future newsletter!
SUGGESTION BOX
That's it for this week, I hope you have a great rest of your day and weekend. For those heading home after Vegas, travel safe. If you saw anything from the shows you want me to highlight next week, drop me an email, I'd love to hear from you.
This newsletter was brought to you by some strong coffee, my cat Theo who was curled up by my side for much of the morning, and some glorious weather here in the New York area.
I really appreciate you for reading. I'll catch you up next Sunday with everything you need to know from the week.
All my best,
@zackwhittaker