this week in security — august 11 2024 edition
THIS WEEK, TL;DR
McLaren hospital giant reports second ransomware attack in two years
Detroit Free Press: What's that sound? Oh, it's the sound of McLaren Health Care, a hospital system around Michigan with revenues of over $6.5 billion, getting hit by ransomware for the second time in as many years. You might also hear the sound of millions of patients whose data might be compromised as a result, not to mention the widespread disruption. McLaren was hit by the INC ransomware gang this time around, but shows healthcare remains a target of cybercriminals even as their profits continue to bulge — all at the sake of cybersecurity, clearly. The INC gang is known to target Linux machines. Back in 2023, McLaren disclosed a breach involving 2.2 million people thanks to the ALPHV gang. Good luck for anyone searching for the McLaren security incident notice, though — a brief look at the web page's source code shows it's deliberately hidden from search engines.
More: McLaren Health | Bleeping Computer | MLive | WILX
Cyberattack knocks school MDM provider offline after student devices wiped
TechCrunch: A cyberattack on Mobile Guardian, a U.K.-based provider of school MDM software (for remotely managing student devices) was hacked and thousands of student devices in Singapore were unenrolled and wiped, losing student data, and prompting the Singapore education ministry to remove the app from student devices. (Not good, exams are coming up!) The outage remains ongoing, with students around the world unable to access their files. A student weeks earlier warned of a major security flaw in Mobile Guardian's software that allowed any signed-in user to create a "super admin" account, allegedly granting access to Mobile Guardian's user dashboard. The student reported the bug, and Singapore's education ministry said the bug was fixed and ruled out any involvement in Mobile Guardian's cyberattack, but the student said the bug was of sufficient simplicity that he fears there are other bugs of similar exploitability. More to come, no doubt. (Disclosure: I wrote this!)
More: Mobile Guardian | Straits Times | Reddit | @doomwrench
Security firm ADT confirms breach after customer data leaks online
Bleeping Computer: ADT, the company that makes security products for your home, was itself hacked — with intruders making off with ADT customer data, including their email addresses and home addresses. ADT disclosed the incident in a SEC filing, but refused to say when the incident happened, for how long the incident ran on for, and how many are affected, but hey, there goes ADT's "most trusted" claim flushed down the toilet never to be considered again. A post on a cybercriminal forum suggests around 30,000 people may be affected.
More: U.S. SEC | SecurityWeek
CISA's Easterly calls software flaws a 'product defect,' urges liability regime
Inside AI Policy: It's hacker summer camp in Las Vegas, and it sounds like it's been a blast. On the Def Con stage this week (after keynoting at Black Hat), U.S. cybersecurity agency CISA's chief Jen Easterly led with much of the same message: Software vulnerabilities are product defects, and it's about time that we treat them as such. The takeaway: "flaws" let vendors off the hook, when it's their lack of software quality control that's resulting in massive flaws and major cyberattacks. "We don’t need more security products, we need more secure products," said Easterly, while muddling mint for a cocktail on stage. Record profits and mass layoffs, but so long as the shareholders are happy... we see you, cybersecurity industry, and enough already! Having @CISAJen at Black Hat and Def Con is important for (and appreciated by) the infosec community, and from the audience's reaction, it shows.
More: Cyberscoop | The Register | @CISAJen

~ ~
THE STUFF YOU MIGHT'VE MISSED
Democratic VP pick Tim Walz has 'notable record' on cyber
Cyberscoop: Minnesota gov. Tim Walz has a record that includes "substantial work" on cybersecurity, according to the policy wonks at Cyberscoop. While serving as governor, Walz published an executive order while directing state agencies to upgrade their defenses and use powers to protect critical infrastructure from cyberattacks. And, he signed into law a data privacy bill for all Minnesota residents that takes effect next year. Good to know!
Trump campaign claims it's victim of foreign hack after leak
Washington Post ($): Meanwhile in entirely unrelated news, the Trump campaign was hacked by someone but the campaign has so far pointed (without evidence) to Iran, probably because days ago Microsoft said Iran was back on its efforts to target U.S. election candidates. The Post ($) said emails were stolen and internal files – including a vetting document on Republican VP candidate JD Vance. It looks like we're in for a DNC-style hack and leak operation akin to 2016. More on this from Emptywheel, whose analysis is always solid.
Project Zero says it will take 'all of us' to end zero days
Decipher: In fitting theme with CISA chief Easterly's comments about software security flaws, it looks like zero-days — the security flaws that vendors have no time to fix — aren't going away any time soon, either. Per Natalie Silvanovich, a security engineer at Project Zero, Google's elite team of expert zero-day hunters, said "challenges around the quality of software, patching, transparency and mitigations" remain even today, and that "security research is not enough to end the era of zero days." Yes, we need companies to stop pushing out shoddy code at the expense of security. Really great interview here.
New Android zero-day under attack, says Google
The Record: And... it looks like an Android zero-day is under active exploitation, according to Google. The bug, known as CVE-2024-36971, affects the Linux kernel, which allows malicious actors to remotely run code (read spyware) on an unsuspecting victim's device. The bug was fixed during Google's August round of security patches.
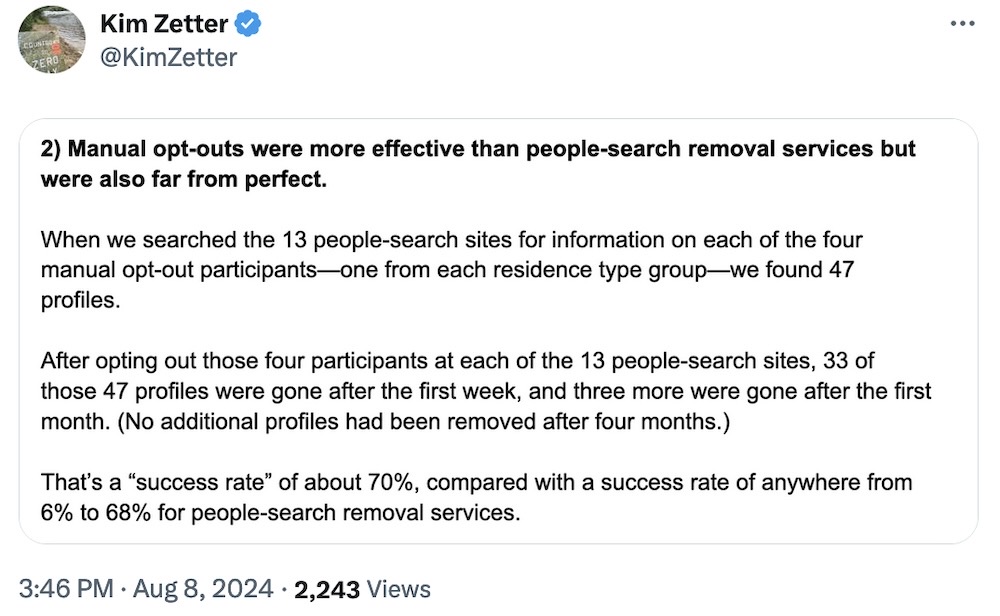
People-search site removal services aren't always effective
Consumer Reports: Data savior @yaelwrites is back with new research revealing that people-search site removal services (which let you pay to remove your personal information) aren't always that effective. Working with the awesome folks at Tall Poppy, the research shows manual opt-outs are far better than most auto-removal services. Where's that big ass data broker opt-out list when you need i... oh! It's right here. More from Consumer Reports' blog, as well.
~ ~
OTHER NEWSY NUGGETS
You know what's ESXi? Patching your systems: Some 20,000 VMware ESXi virtualization servers are on the internet but unpatched, according to data from the Shadowserver Foundation, and that could put thousands of organizations at risk. A new bug mentioned last week allows threat actors to gain full access to a vulnerable ESXi instance. You really want to get ahead of this one, as ESXi servers are top targets because of the wealth of data they store. (via SecurityWeek, @Shadowserver)
Another election portal bug discovered: Late last month, the Associated Press reported a bug in a Georgia state election portal that could have (albeit briefly) been used to unregister voters in the state. Not great! But then this week ProPublica reported another bug in the Georgia state website that could've been exploited to bypass the need to submit a driver's license number to submit a voter cancellation request... by using the browser's tools to simply delete the box where you enter the driver's license number. Welp. (via ProPublica)
Mudge at DARPA? What is this, 2010? Peiter "Mudge" Zatko, the cybersecurity leader who had spells at DARPA, Twitter, and most recently Rapid7, is... back as the new chief information officer at DARPA, the agency he was at some 14-15 years ago. Here's a blast from the past, and @dotMudge confirming the news. (via Nextgov)
Boldend snapped up by cyber firm: Offensive cyber startup Boldend, a firm that reportedly makes malware creation tools and cyber tools used for Wi-Fi exploitation, was acquired by a little-known cyber firm called Sixgen. The company doesn't say much about what it does aside from a ton of corporate word salad, but claims Boldend's only customer is the U.S. government, so go figure. (via Forbes ($))
'Ello 'acker: The U.K.'s Home Office was confirmed as a victim of the ongoing Russian cyberattack on Microsoft's systems that saw the hackers gain widespread access to Microsoft-hosted emails of its executives and customers. The Home Office, which hosts its email with Microsoft, reported the incident to the U.K. data watchdog, which confirmed the incident to The Record. Russia's SVR, its foreign intelligence service, was blamed for the cyberattack. U.S. federal agencies had data compromised by the breach, as well as other Microsoft customers, but this is the first known instance affecting the U.K. government. (via The Record)
Secrets, secrets everywhere: @BillDemirkapi is a brilliant security researcher who's found gobs of secrets online — passwords, API keys and tokens — belonging to a wealth of companies, which if found by cybercriminals could be used for wide scale hacking. In a Def Con talk this weekend, Demirkapi explained how he found this huge wealth of secrets, and spoke with Wired ($) about his findings and why there are no easy fixes to this seemingly never-ending problem. (via Wired ($))
~ ~
THE HAPPY CORNER
Fiiiinalllly. It's the happy corner.
First of all, a major congrats from the entire hacker community to Sam Watson, who took home a bronze medal for speed climbing at the Olympics in Paris, climbing 15 meters in less than five seconds. (Blink and you'll miss it!) Watson also beat his own world record while proud father and hacker @RayRedacted watched on. What an amazing feat!

A shout-out to the awesome folks at the Harvard Cyberlaw Clinic who have an updated security researcher's guide to leak risk now out, with a much updated revision for the post-Van Buren ruling at the Supreme Court (which was pretty good for hackers). The guide is a necessary must-read for all practicing security professionals. (via @kendraserra)
Thanks to the big push into #SecureByDesign by CISA, close to 200 firms have signed up to the government's pledge to build software with security first and foremost and baked in by default, per Nextgov. The pledge is on CISA's website, aka a list of companies that you should consider giving money to over companies that aren't on this list!
And, scene:
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber-catdog (quelle surprise!) is Ginger, who as you can see here is gnawing on a well-deserved bone, otherwise known as an advanced persistent treat. Many thanks to Jason T. for sending in!

Keep sending in your cyber cats! You can drop a quick email with a photo of your cyber cat (or non-feline friend!) with their name, and they will be featured in an upcoming newsletter. Updates are also very welcome, send them in!
~ ~
SUGGESTION BOX
And that's all for this week. Thanks for reading! Safe travels to everyone heading home from Vegas this weekend. I'll be back next week with your usual roundup of news and other wonderful things. Feel free to get in touch any time by email!
(BTW: If you're eligible to vote in the U.S. but haven't yet registered, this weekend would be a good time to do it! And, don't forget to keep a close eye on your status.)
All the best,
@zackwhittaker