this week in security — august 13 edition
THIS WEEK, TL;DR
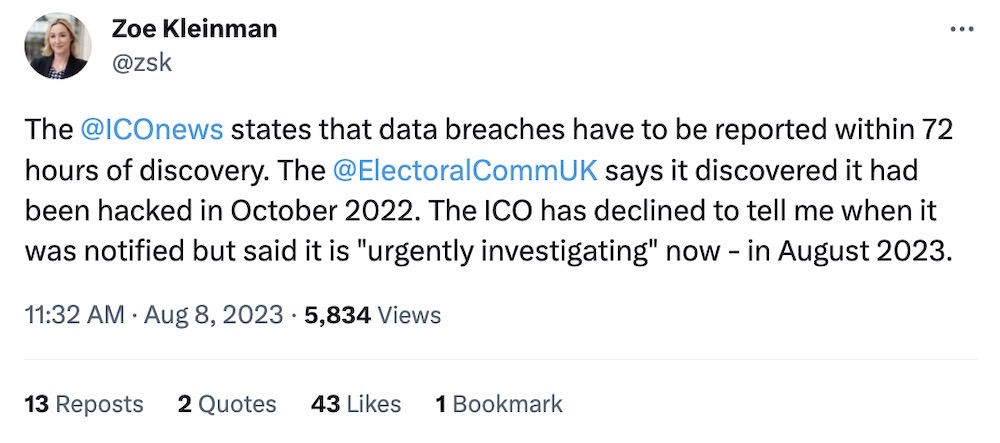
Cyberattack on U.K.'s electoral registers revealed
BBC News: We're going to start in my former homeland, with not great news. The U.K. Electoral Commission, which oversees U.K. elections, said it was hacked, and at least 40 million people had their names and addresses accessed. The breach happened in August 2021 but wasn't detected until October 2022 and publicly disclosed ... this week. Yeah! That doesn't make sense either. The ICO, charged with investigating the incident, couldn't explain why it took so long to publicly disclose. It's still unclear who's behind the attack, but given there was no communication from the hackers, it's unlikely to be financially motivated. (Think espionage!) Although there's no risk to elections, how the hack happened remains a big question. Could it have something to do with a then-unpatched Exchange Server on its network? As with previous major incidents, I parsed the Commission's security incident notice for morsels to understand what went down.
More: Electoral Commission | Ars Technica | TechCrunch | The Times ($)
Hackers accessed 16 years of Colorado public school student data in June ransomware attack
The Record: Every student who went to a Colorado public school between 2004 and 2020 had personal information accessed by a ransomware gang. The massive ransomware attack is one of the biggest breaches of the year so far, affecting thought to be millions of students over the years. The Colorado higher education department, CDHE, said it was investigating. No ransomware group has yet claimed responsibility for the breach. In the same week, Homeland Security granted $375 million in new funding to increase cyber resilience across state and local governments. It's a start, but I can't help but feel that until we have meaningful data and privacy laws, that fund might as well go towards 2-years rolling identity theft monitoring for every student in the land.
More: Colorado Dept. of Higher Education | TechCrunch | Bleeping Computer
Ukraine cyber chief on cataloging cyberwar crime evidence against Russian hackers
Cyberscoop: In an interview with Cyberscoop, Ukraine's cybersecurity chief Victor Zhora discusses the need to document cyberattacks that constitute acts of war. It's a fascinating interview discussing some of the destructive attacks, including the Viasat hack and wipers targeting government websites — and cyber-driven kinetic actions. It comes in the same week Zhora and U.S. cyber agency chief @CISAJen were interviewed by the esteemed @lhn for one of this year's Black Hat keynotes, discussing the Ukraine war and how help from allies is contributing to countering Russian cyberattacks. @ericgeller tweeted the keynote, as did @ram_ssk.
More: The Record | @CISAJen | @ericgeller

Microsoft's role in email breach to be part of cyber inquiry
Bloomberg ($): Speaking of CISA... the cybersecurity agency announced the Cyber Security Review Board's third-ever investigation, this time looking at cloud security, spurred in large part by the hack of government emails via a flaw in Microsoft's cloud. In short, Microsoft lost a set of master keys that, coupled with a flaw, allowed China-backed hackers to forge tokens allowing them into Microsoft-hosted government email accounts. Not great! Sen. Ron Wyden was called for an investigation. A week later, lo and behold, here it is. The CSRB was set up in 2021 by executive order to give actionable advice on how to avoid another global cybersecurity dumpster fire. Its first review was Log4j. (Remember that?) The CSRB also just finished up its second investigation looking at Lapsus$, released this week. This latest probe will likely keep the board busy for the next few months.
More: Homeland Security | Cyberscoop | Reuters ($) | @argv
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
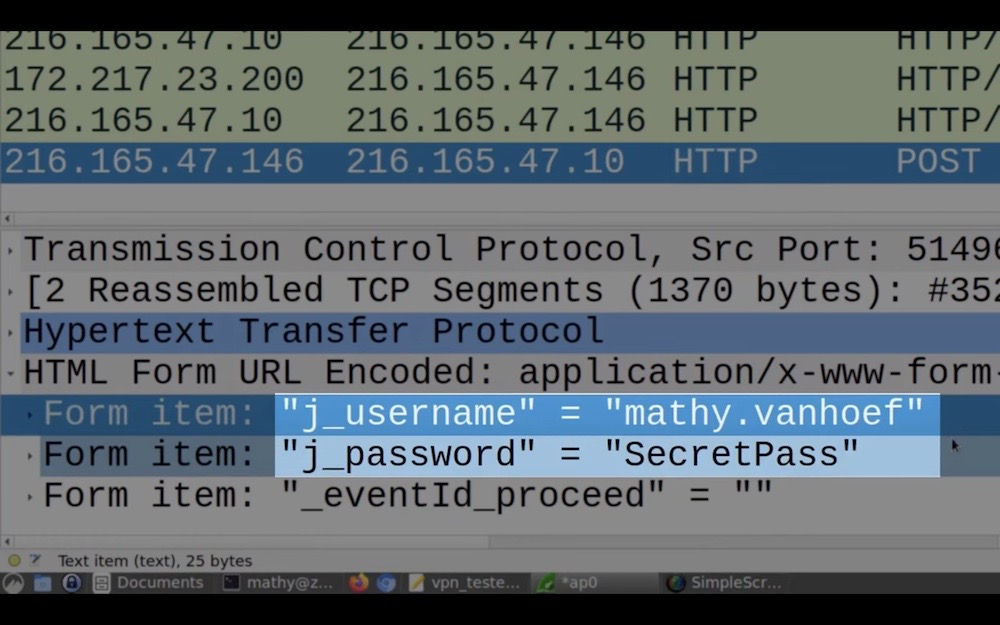
TunnelCrack flaws can expose VPN tunnel traffic
Mathy Vanhoef: Security researcher Vanhoef is back with a new attack, dubbed TunnelCrack, which found that most VPN have at least two widespread security flaws that can trick a victim into sending traffic outside of their protected VPN tunnel — in other words, leaking transmitted traffic. As if you needed another reminder that VPNs do not enable anonymity (but Tor does). More in a toot thread.
How the FBI goes after DDoS cyberattackers
TechCrunch: At the Black Hat security conference in Las Vegas, my TC colleague @lorenzofb interviewed the FBI about its talk looking at how it targets and takes down DDoS networks. It's an interesting look at their methodology and how they choose their criminals to target. "Generally, if you’re big enough to be in the news, you start to be on our radar," one FBI agent said.
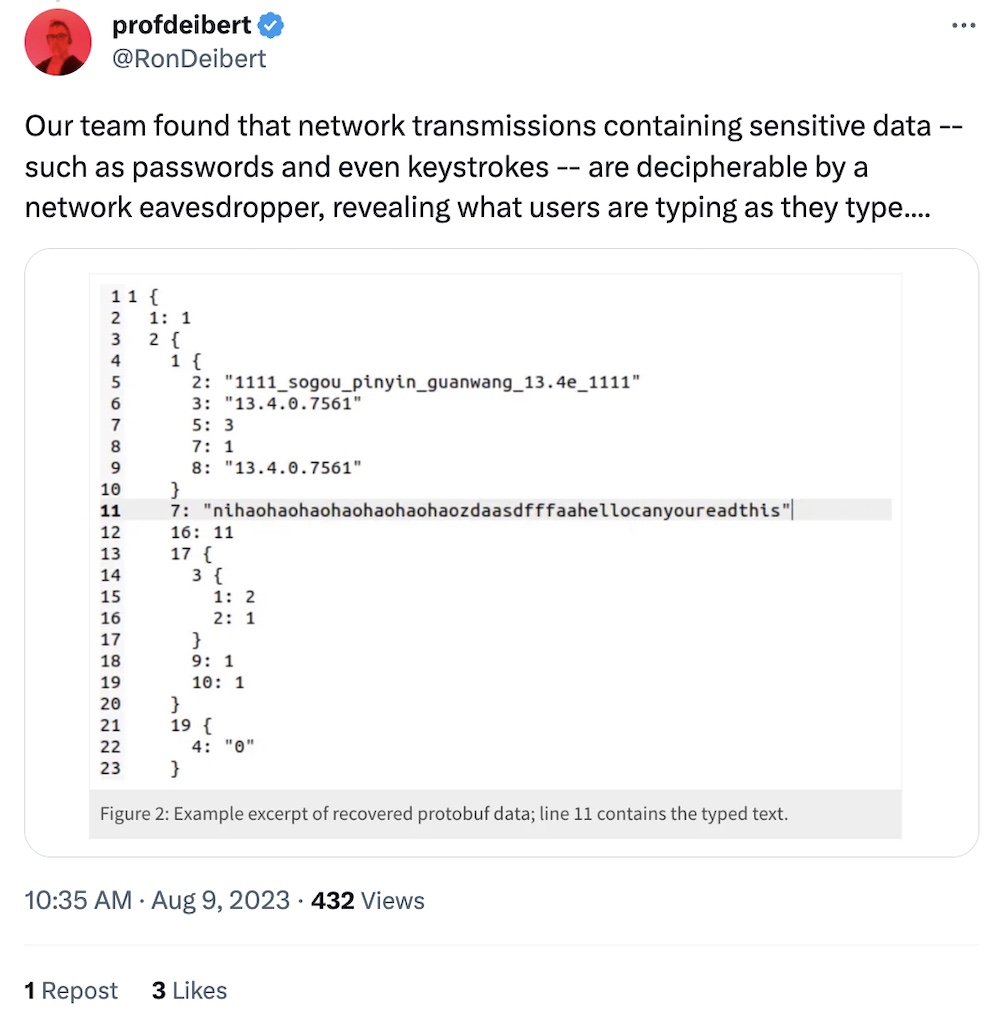
Flaws in Sogou Keyboard encryption expose keypresses to eavesdroppers
Citizen Lab: Researchers this week disclosed flaws in the Tencent-owned software keyboard, Sogou Keyboard, which is used by some 455 million active users. Citizen Lab found that the keyboard contains flaws making the keystrokes that users type "decipherable to network eavesdroppers." That means the company (or anyone on the network) can intercept what people write. Not great for the millions of users in China, which monitors and restricts free speech to the degree it does. Just a reminder that pretty much any phone or add-on keyboard has the capability of collecting and saving whatever you type on it. @jsrailton and @rondeibert have more in the toots and tweets.
Hackers rig casino card-shuffling machines for 'full control' cheating
Wired ($): More from Black Hat: security researchers at IOActive say they found vulnerabilities in casino card shufflers. Yes, it means exactly what you think it does: hackers could learn the exact deck order—and the hand of every player at a poker table. Here's a great @agreenberg long-read for the flight back.
Rhysida blamed on U.S. hospital chain hack
Cisco Talos: A major ransomware attack targeting Prospect Medical Holdings, a major U.S. hospital and healthcare chain, saw patients redirected and services knocked offline. Now, Cisco's Talos has a profile of Rhysida, the ransomware group allegedly behind the Prospect cyberattack. It comes in the same week that U.S. Health and Human Services put out a warning [PDF] about the risk of ransomware attacks from this particular group.
~ ~
OTHER NEWSY NUGGETS
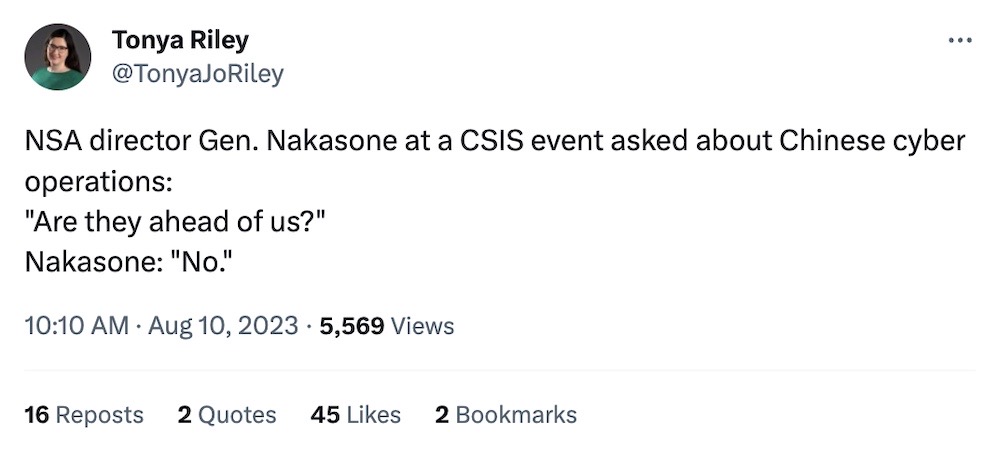
China hacked Japan's sensitive networks: Breathtaking reporting from @nakashimae on a hack by China of Japan's sensitive defense networks. U.S. intelligence "noticed" (heavy wink) the hacks, prompting NSA commander Gen. Paul Nakasone to fly to Japan to alert the defense minister. NSA helped the Japanese — but the problem still isn't fully fixed. The whole piece (and tweet thread) is worth the read. Clearly not the most thrilled the U.S. could be, given Japan is a major ally in the region. And by the sounds of it, Nakasone was having precisely none of it when speaking about China's hacking abilities a recent public event in Washington DC: (via Washington Post ($), @nakashimae)
Northern Ireland police dox own police officers: The Police Service of Northern Ireland says a "major data breach" involved the identification of thousands of officers and civilian staff. The breach was... a fulfilled FOIA request, which "mistakenly" included the personal information of its 10,000 staff. Really not good for those working there, since sectarian violence remains very much a problem in Northern Ireland. To be clear, The PSNI confirmed the accidental disclosure was "human error," before anyone knee-jerk reacts to the situation by wiping out FOIA laws or something equally ridiculous. (via BBC News)
Next-gen security protocol... already failed: Researchers have discovered a fleet of security flaws that largely break a next-generation protocol designed to block the hacking of access systems used at secure military installations. The protocol, known as Secure Channel, was added to OSDP about a decade ago, but researchers at Black Hat found five vulnerabilities and a host of weaknesses that "strongly call into question" the security of OSDP. Spicy. (via Ars Technica, @dangoodin)
Rapid7, NCC layoffs confirmed: Security companies Rapid7 and NCC Group said they have laid off portions of their workforces. Rapid7 let go of hundreds of employees, some 17% of its workforce, and said it would close offices after taking a massive $67M earnings loss. NCC Group wouldn't say how many staff it was cutting, but this latest layoff comes just a few months after NCC cut about 7% of its workforce. (via DataBreachToday, TechCrunch)
U.K. 'delusional' over anti-encryption law: U.K. think tank IEA says the U.K. government's technology minister is "delusional" about her claims that the new Online Safety Bill is not anti-encryption. According to the IEA, the bill — which is anti-encryption, there's no way around it — if passed, will result in "undermining encryption and potentially leading the likes of WhatsApp and Signal to leave the U.K." The IEA added: "There is no magic technological solution in existence or development that can protect user privacy while scanning their messages. It’s a contradiction in terms." And that really should be it, alas, the bill looks like it might actually pass later this year. If you want to read what the delusional minister has to say, you can read it on the BBC. Note that the minister doesn't actually dispute the IEA's concerns. (via IEA)
NOC, NOC, who's there? Take a look at the Black Hat network operations center, or NOC, which supports the Black Hat conference and its some 20,000 attendees. A great write-up here. (via The Register)
~ ~
THE HAPPY CORNER
Breathe in, and out. Feel calm? That's because you're in the happy corner.
Google said this week that it will allow IT admins to start blocking 2G connection in their fleet of Android 14 devices, expected out later this year. It follows Apple, which said it will allow users to block 2G connections in iOS 17 (also out later this year). 2G is riddled with security flaws, some of which can still be exploited to downgrade service and listen in on calls, messages and track locations. Yes, exactly what stingrays can do.
Meanwhile, did anyone actually get to hack the weird Vegas sphere-thingy? Please get in touch. 👀
Congratulations to @mattblaze, Susan Landau and @stevebellovin for winning the 2023 Usenix Association Lifetime Achievement Award.
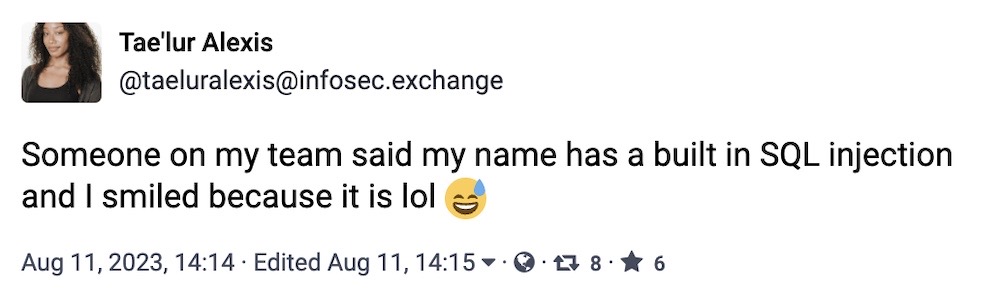
When @taeluralexis tooted this, I almost fell off my chair laughing, because I will always be reminded of Little Bobby Tables, which never fails to make me laugh.
If you, like me, have been wondering where the White House cat is, Politico finally gets answers to the mystery. Politico has the back story.
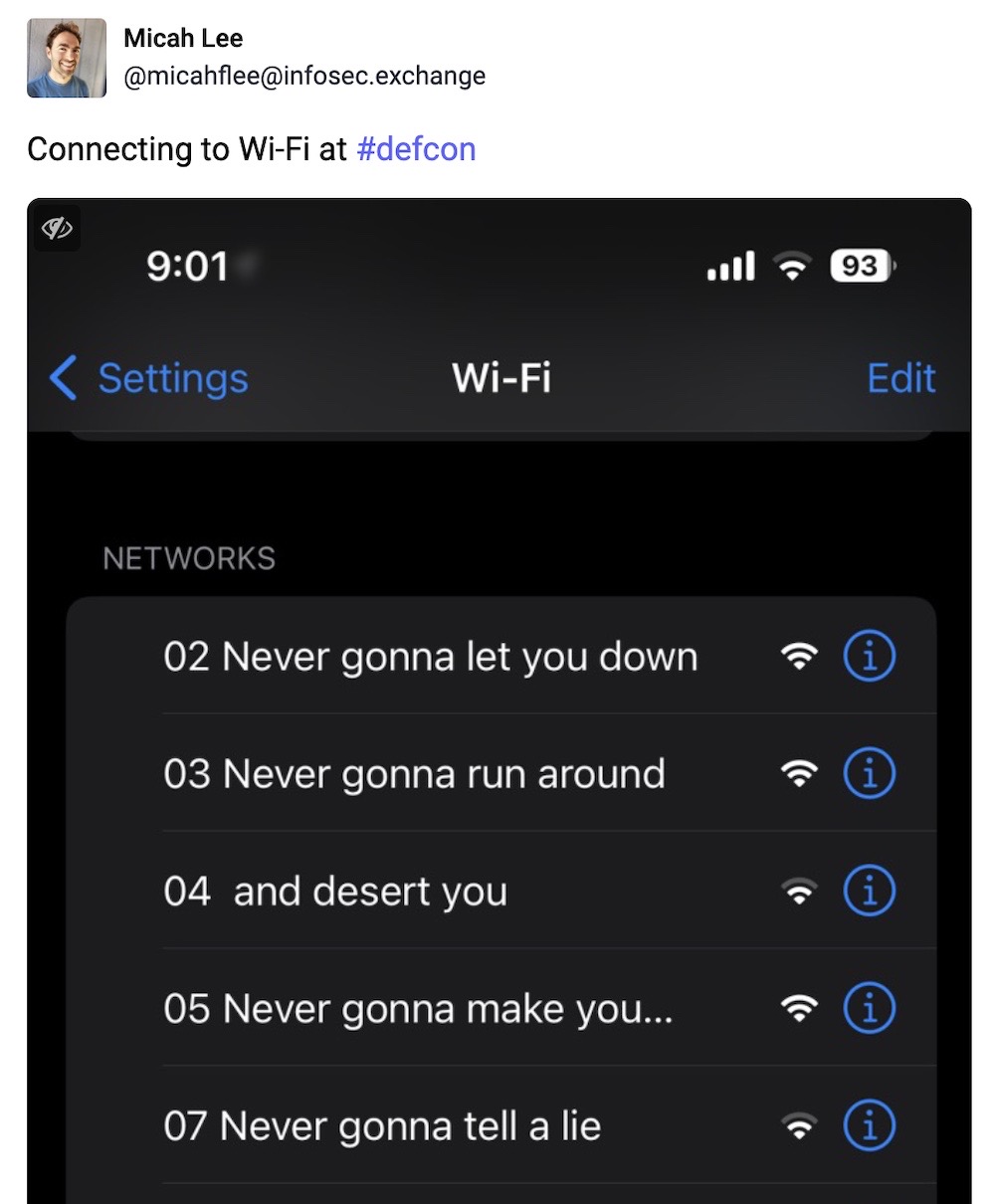
And finally. For those leaving Vegas today, rest assured that the entire conference was rickrolled at least once.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Ash, who is (in their own way) supporting their human while they do OWASP training. A very good cyber cat. Thanks to Mihaela M. for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it for this week. Hope you enjoyed this incredibly busy newsletter. If you liked this week's dispatch, please share with a friend or colleague! In the meantime, I'll catch you again next week. As always, feel free to drop me an email with any feedback you have.
Until next time,
—@zackwhittaker