this week in security — august 17 2025 edition
THIS WEEK, TL;DR
U.S. officials suspect Russia of being behind U.S. court records hack
The New York Times ($): We start with Russia, which U.S. officials this week blamed for a long-running hack affecting the U.S. federal courts filing system, known as CM/ECF (or PACER). Russian hackers went from being merely suspected of orchestrating the hacks to probably doing the thing, making this (at least) the second major hack of the federal courts' filing system since the 2020 SolarWinds hack (also the Russians), say sources speaking to the Times. Per Bloomberg ($), the hackers lurked in the system for years, targeting "sealed documents in espionage and other sensitive cases," including those involving fraud, money laundering, and agents of foreign governments. Politico, which first broke the story, says the bugs exploited this time around were known since the first hack back in 2020. This is arguably the first major cyberattack of Trump's presidency, and so far, honestly, crickets from the White House about it. Trump had face-time with Russia's Putin this week, a rare meeting of the two superpowers, which by all accounts didn't go very well, but would've also been a good opportunity to ask Putin and his cyber cronies to dial back on some of their cyberattacks.
More: TechCrunch | Wired ($) | CNN | Politico
Norway spy chief blames Russian hackers for dam sabotage
The Register: Speaking of Russia, Norway's spy chief blamed Russia for a cyberattack targeting a dam in the west of Norway earlier this year. The breach allowed the hackers to open a floodgate for several hours, spilling the equivalent of three Olympic-sized swimming pools of water out of the dam before the attack was discovered and stopped. It's the latest reported effort by Russian hackers to meddle in other countries' critical infrastructure, efforts that Russia knows all too well. According to Reuters ($), Polish authorities also revealed that they foiled a suspected Russian-backed cyberattack on a large Polish city's water supply, which could have cut off supplies to local homes. Critical infrastructure remains massively underfunded low-hanging fruit for malicious hackers.
More: Reuters ($) | SecurityWeek | VG.no
NetScaler hacks hit Pennsylvania AG, Dutch critical infrastructure
Statescoop: It's looking like the office of Pennsylvania's attorney general is having a rough one after disclosing a "cyber incident," per a statement. According to @GossiTheDog, the breach is linked to the recent NetScaler attacks, which took down the office's email, its website, and phone lines. The same NetScaler bug, disclosed last month and tracked as CVE-2025-6543, is also wreaking havoc in the Netherlands, where critical infrastructure systems were hit (including traffic systems), said the country's cybersecurity center. There are said to be thousands of vulnerable NetScaler devices still on the internet, despite patches being released.
More: Cybersecurity Dive | @shadowserver | @paattorneygen
Def Con's final day drops reams of research and Pwnie Awards
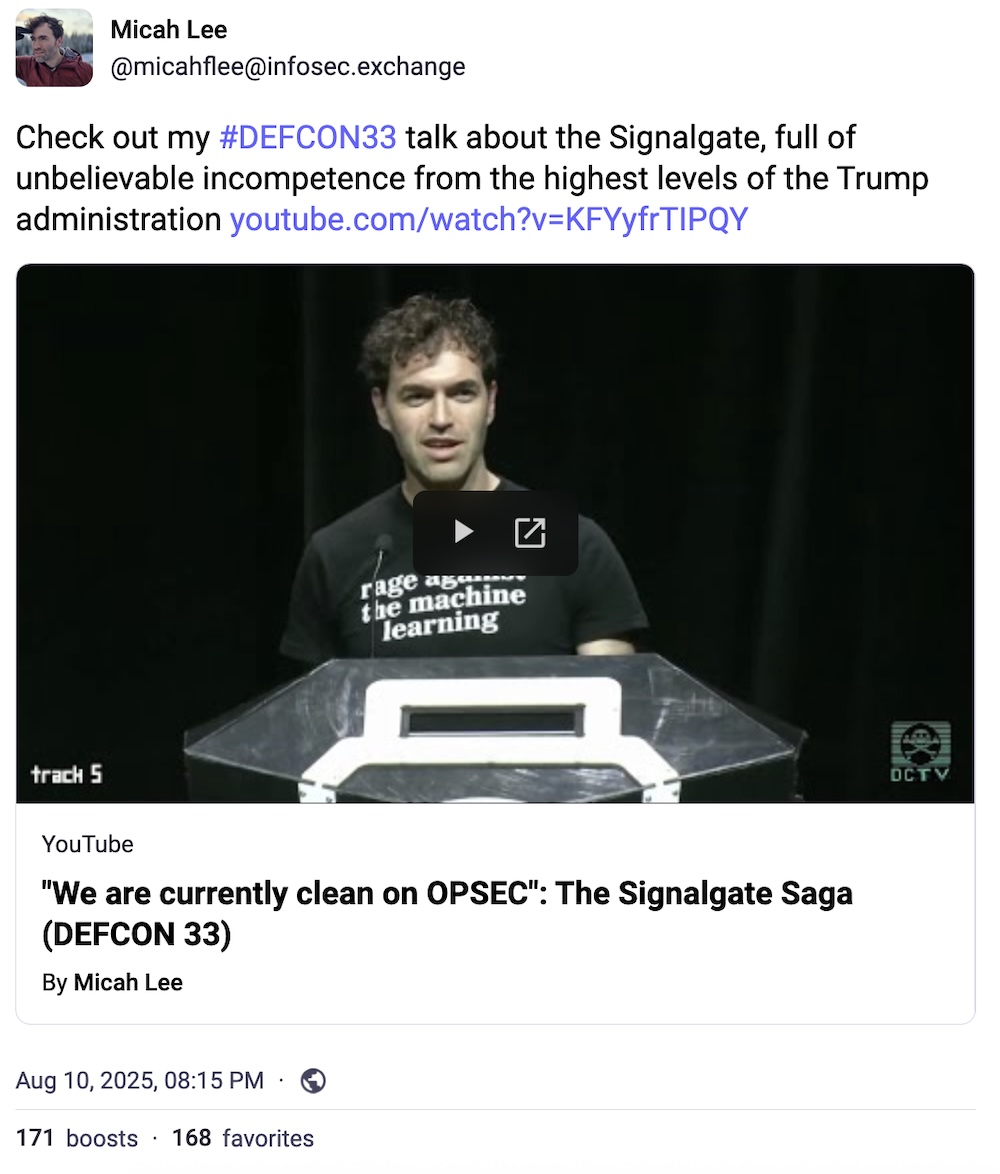
As expected, there was plenty of spillover from last week's Def Con into this week's newsletter, thanks to some top-notch findings revealed last Sunday. We have... *breathes in*... hackers breaching a North Korean hacker's computer and writing about it for Phrack... a hacker found bugs exposing access to a carmaker's centralized car portal, allowing the remote control of some car functions (disclosure: I wrote this!)... a peek inside the gray market of video game hacks... and, the winners of the Pwnie Awards — congrats to @micahflee whose amazing reporting and research on Signalgate won the White House the Pwnie's Epic Fail award. But, this wasn't a Def Con without controversy, as the show faced heat for cozying up to the U.S. military and authoritarian regimes like Bahrain.
More: TechCrunch | Wired ($) | Heise.de | Jack Poulson | @micahflee
THE STUFF YOU MIGHT'VE MISSED
Security pros' paper reveal Iranian cyber threat tactics
Tarah Wheeler: Top security boffs Wheeler et al dive into the many ways that network defenders can get ahead of Iranian hackers, an increasingly formidable group of cyber-actors today. Some of Iran's top hacks rely on simplicity and scale, like email spearphishing. This blog outlines some of the top things to look out for from the perspective of front-line cyber defenders who live and breathe this.
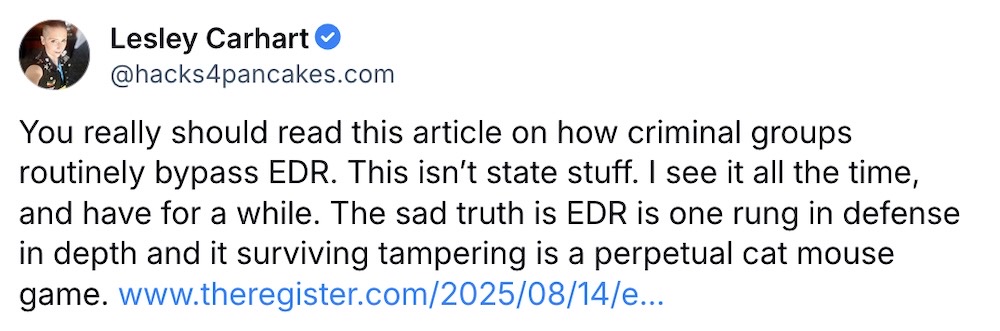
Ransomware gangs have added EDR-killers to their hacking arsenal
The Register: Ransomware gangs are incorporating kernel-level malware capable of disabling endpoint detection (aka EDR) systems and allowing the hackers to steal data and extort victims.At least nine ransomware gangs have been seen using EDR-killers in recent months. "This isn't state stuff," says @hacks4pancackes, referring to criminals using these exploits, not government hackers.
How Apple's XProtect's detection rules have changed over 6 years
Eclectic Light Company: Here is a little look inside how XProtect, the anti-malware engine built into macOS, has changed over the past six years, notably growing its signature list by fourfold.
Security founders discuss lessons in bootstrapping their startups
Dark Reading: I enjoyed this read on startup bootstrapping, especially in cybersecurity, at a time when VC money is flooding the market (and sprinkling everything with AI for the sake of it). Huge respect to those who can bootstrap, but definitely in awe of anyone who stay bootstrapped years in. Thinkst Canary and IOActive, to name a couple, are examples of cyber companies doing things right.
Data broker behind major SSN breach returns. Here's how to opt-out
PCMag: Bankrupt, but not out, National Public Data, the data broker that had a massive breach of Social Security numbers last year, is now back after new (unknown) owners saved the company from going under. As such, National Public Data is back online (yuck) but you can at least opt-out of having your data searchable. (More words from DataBreaches.net.) Meanwhile: The Markup reports that data brokers are hiding their opt-out and privacy tools from search engines, and now at least one U.S. senator wants answers as to why, per Wired ($).
OTHER NEWSY NUGGETS
British bobbies expand face scans with vans: Facial recognition is rolling out on wheels (think local police vans) across the U.K., despite the unreliability of facial recognition and the chronic problem of false positives wrongly identifying suspects. The Register has a good look at how the U.K. government is getting high on its own surveillance supply... (via The Register)
Canadian Commons reports data breach: A breach at the Canadian House of Commons saw information about government employees and devices stolen, per CBC News, citing an unspecified Microsoft vulnerability as to blame for allowing the hackers into a database. It's not clear what the Microsoft bug is referring to, despite warnings about SharePoint and Exchange of late. (via CBC, The Record)
Spilling TeaOnHer users' data in less than 10 minutes: Last week I reported on a super shady dating gossip app called TeaOnHer that publicly exposed users' driver's licenses, which users had to upload before they could access the app. This week I wrote the post-mortem (disclosure alert!) about how I found the easy-to-find bugs within 10 minutes of being sent its App Store listing. Not a flex; the bugs were literally that easy to find. Follow along for the ride and subsequent disclosure. (via TechCrunch, @senatorshoshana)

Warlock gang hacks telco giant Colt: U.K. telco and networking giant Colt has been hacked by the Warlock ransomware gang, with the company taking down its customer portal and voice API platform as a "protective measure." The gang took credit for the breach and is now selling data stolen from its internal network. Colt hasn't given a timeline for its recovery. (via Bleeping Computer, GossiTheDog)
Resettled Afghans hit by second data breach: Thousands of Afghans who were brought to the U.K. after a 2022 data breach (which was kept a secret until July) exposed their data and put them at risk of death from the Taliban, have been subject to another data breach. This time it's the fault of Inflite The Jet Centre, which provides ground services for flights at London airports. (via BBC News)
THE HAPPY CORNER
*trumpets trumpeting* It's back! It's the happy corner, where nobody knows your name (because privacy, obviously).
We start with a cat caption contest.

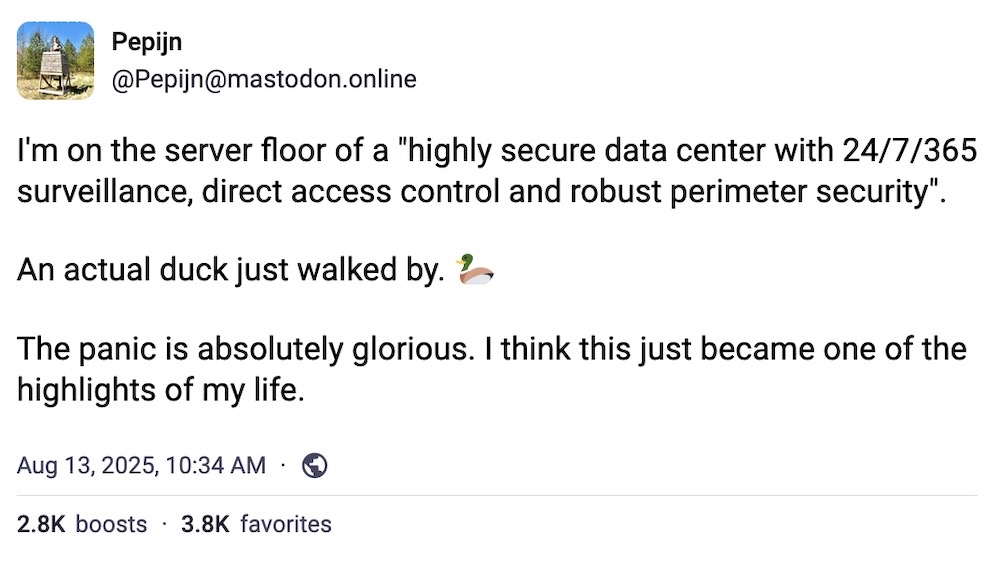
It sounds like the start of a joke, but... A duck walks into a highly secure datacenter... (the thread continues...)
When a flamboyant Waluigi workplace profile picture chooses you.
I absolutely loved this project by Daniel Cuthbert, hacker and photographer extraordinaire, who used a decades-old Sony Mavica MVC-FD88 camera with a 1.44" floppy disk drive for storage, to capture retro-style photos of today's top hackers from this year's Def Con. Very cool indeed!
And lastly, a final and everlasting thank you to Stephanie "Steve" Shirley, who died earlier this month at the age of 91. Steve, as she was known, was a computing and tech pioneer whose early work on women's rights helped to bring in some of the smartest minds the world has ever seen in what was a male-dominated field. Amazing reporting from BBC News, which chronicled some of her life in their obituary. Rest in power, Steve.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
CYBER CATS & FRIENDS
A rare triforce of cats, meet Ray, Moo, and Sis (back to front), who can be seen here scarfing down their dinner after a busy day of hacking. Remember, cybersecurity takes a village and the more eyes the better. Thanks to Tori N. for sending in!

Keep sending in your cyber cats! Got a cyber-cat or a non-feline friend? Send me an email with their photo and name and they will be featured in a future newsletter!
SUGGESTION BOX
And that's it for this week, thank you so much for reading! I'll be back next Sunday with the roundup from the week. As always, feel free to drop me an email with anything about or for the newsletter.
See you next,
@zackwhittaker