this week in security — august 18 2024 edition
THIS WEEK, TL;DR
FBI probing alleged Iran hacking targeting Trump and Biden-Harris campaigns
Washington Post ($): Since as early as June, the FBI has been investigating suspected Iranian hacking attempts targeting the two presidential campaigns ahead of the 2024 election. Now both Microsoft and Google say Iran is ramping up attacks targeting the two campaigns. It looks like (so far) the Biden-Harris camp wasn't compromised, but the Trump campaign was, likely by way of hacking the email account of one of Trump's closest advisors, per CNN. Iran really doesn't want Trump to win the election, which might be why there was an attempted hack-and-leak operation akin to Russia's activity in 2016. Yet... that hasn't happened, possibly because media outlets learned the lessons from yesteryear by not inadvertently publishing stories that amplify the leaker's messaging. BBC News has a good explainer on Iran's hacking efforts (and those of other countries).
More: CNN | Washington Post ($) | Wired ($) | AP | @bing_chris | @nakashimae
U.S. appeals court rules geofence warrants are unconstitutional
TechCrunch: A little slice of good news before the fold: A federal appeals court for the Fifth Circuit (covering Louisiana, Mississippi and Texas) split with a decision from the Fourth Circuit last month, by finding that geofence warrants are incompatible with the Fourth Amendment. That effectively puts a bar on geofence warrants across the states. Geofence warrants let police draw a shape on a map and obtain (from Google and other tech companies) location data of anyone in that space at a given time, such as a crime scene. The Supreme Court might hear the case and come to a final decision, but it's unlikely in this case since the case could get heard again at the appeals court level. Law prof. Orin Kerr says the decision could have a significant impact on digital warrants for data held by tech companies. The ACLU, which argues geofence warrants are unlawful, disagreed with Kerr's analysis of the findings but the debate is worth the read.
More: MSNBC | Lawfare | Volokh Conspiracy | EFF | @granick
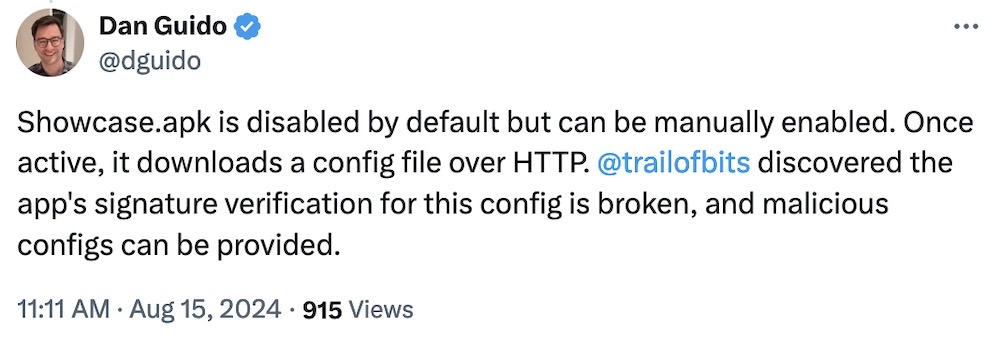
Nearly all Google Pixel phones exposed by bug in hidden Android app
Wired ($): A bug in a Verizon app (read: bloatware) found in Google's flagship Pixel phones put users at risk of manipulation and takeover. The bug found in an Android software app called Showcase.apk (which runs at the system level but invisible to users) was developed for Verizon for putting phones in a demo mode for storefronts, but researchers at iVerify found the app has deep system privileges that could be used for compromising the device. Google said it's taking the app out of Pixel devices in the coming weeks amid concerns it could be abused. Palantir (of surveillance fame) said it's banning Android phones on its enterprise for now, fearing the bug. The saving grace is that physical access to a device is needed to exploit it (that we know of, and so far), which doesn't help those whose phones might've been stolen or put through a police forensics tool. Clearly a big enough risk to rip out the danger code from the stock Android phone before it could be abused.
More: Washington Post ($) | iVerify | @cryps1s
~ ~
THE STUFF YOU MIGHT'VE MISSED
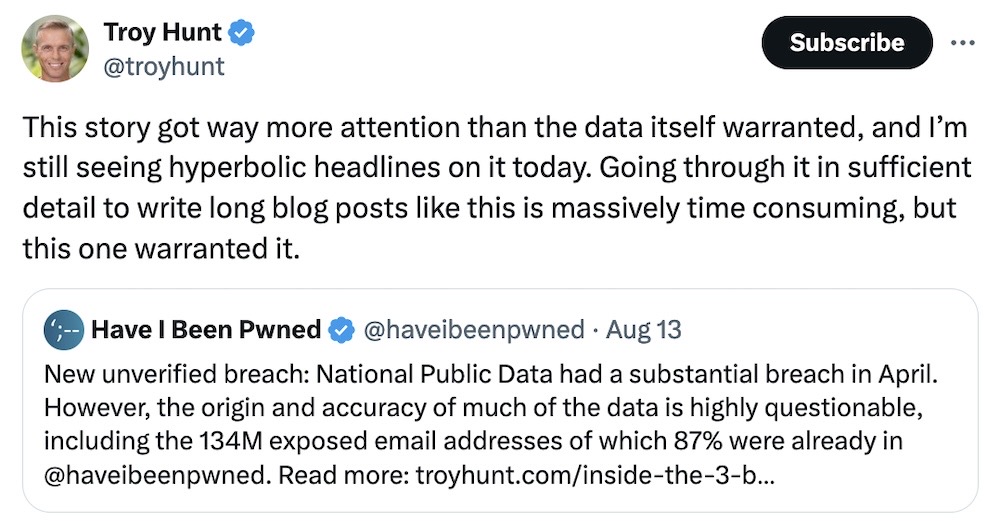
The multi-billion Social Security number breach that wasn't
Troy Hunt: For the past few months, there's been a data breach floating around cybercrime forums claiming to have somewhere in the region of 3 billion records and Social Security numbers on millions from an apparent data broker called National Public Data. The data looked deeply suss and only some of the data checked out during verification efforts. But, of course, breathless headlines because it's an easy (read: lazy) story to write, but the data isn't all accurate. The data broker admitted a breach this week, and Troy Hunt analyzed the data, finding about 133 million unique email addresses with 87% in HIBP already, but that doesn't mean there's necessarily evidence that your SSN was actually breached. The big lesson? As long as there are data brokers, this data will get scooped up and inevitably lost or stolen, regardless of its accuracy.
Six zero-days lead Microsoft's August Patch Tuesday
KrebsonSecurity: Alright, it's that time again — Patch Tuesday — the monthly slew of security patches. Microsoft led the releases with fixes for six zero-day vulnerabilities under active attack. SecurityWeek also has a guide on what's new and patchable. One not-yet-exploited bug, officially CVE-2024-38063, says an "unauthenticated attacker could repeatedly send IPv6 packets, that include specially crafted packets, to a Windows machine which could enable remote code execution." Not great, but details of the exploit aren't out just yet.
Gym lockers are hackable, company sends legal threat
Wired ($): Digilock said it has fixed vulnerabilities that allow its widely used electronic lockers (found in gyms, offices and schools) can be hacked and unlocked, thanks to keys that can be extracted from lockers and used to open other lockers in the same location using a tool like a Flipper Zero. Digilock sent a cease-and-desist letter to the security researchers who were presenting at Def Con last week. Thankfully, the good folks at the EFF (we stan!) stepped in, the company rescinded its legal threat, and the talk went ahead.
GPS tracking company hacked, internal tools expose user locations
maia arson crimew: Hacker maia arson crimew gained access to an internal tool used by a GPS tracking company called Trackimo that allowed the looking up of the location history of other people's devices. The full write-up goes down a wild rabbit hole of OSINT. 404 Media ($) also has a write-up.
~ ~
OTHER NEWSY NUGGETS
Feds pull the plug on another ransomware gang: The FBI in Cleveland nuked a ransomware operation from orbit this week after seizing the website and infrastructure of the Radar/Dispossessor group. The gang hacked dozens of companies over its lifespan. It's a rare win in the whac-a-mole fight against ransomware, and clues suggest the gang may have roots or links to Germany, given German police were involved. Cue the seizure splash screen, which the feds seem to be having increasing fun with. (via Justice Dept., FBI)

$60 million lost to wire transfer scam: I genuinely feel sorry for the poor soul who inadvertently wire transferred $60-or-so million from a company's coffers into a scammer's bank account. (But really; not the employee's fault, if measures weren't in place to prevent this kind of fraud!) Orion disclosed the loss in an 8-K filing with regulators. These kinds of fraud schemes, including business email compromise scams, are really smart and can be difficult (but not impossible!) to defend against. (via SEC 8-K)
What it looks like to wiretap the world: If you've read Dark Wire by journalist @josephcox, you'll know all about the FBI's surveillance system for reading messages Anom, the encrypted phone company that it had backdoored. The system the FBI built is called Hola iBot, and Cox published new screenshots demonstrating the system. Nerd out over what looks like (tbh!) a neat-looking case management system that looks like it could've been built by a scrappy startup. (via 404 Media ($))
T-Mobile slapped for one of many, many breaches: A U.S. Treasury committee that scrutinizes foreign investment for national security risks, called CFIUS, fined T-Mobile $60 million — CFIUS' largest fine to date — for failing to prevent a data breach between 2020 and 2021. The data breach was related to a "small number" of law enforcement information requests, but seemingly unrelated to the multiple data breaches at T-Mobile during that time that affected over 77 million people. (via Reuters ($), CFIUS)
Spyware firm self-owns in takedown effort: A few weeks ago, spyware app mSpy had a data breach, which linked the operation to Ukrainian tech firm Brainstack. When I contacted the company for comment, Brainstack didn't dispute its link to mSpy but didn't confirm it either. Now, Brainstack sent a takedown notice trying to get FlockiNET, the web host that hosts DDoSecrets, the leak site that hosts the mSpy data breach, to pull DDoSecrets offline. In that takedown notice, Brainstack confirms it's justified in complaining because the hosted data includes "corporate data belonging to mSpy, a brand of our company." Chef's kiss stupidity right there. (via FlokiNET, @zackwhittaker)
~ ~
THE HAPPY CORNER
Just a couple of things from the happy corner this week.
People were still leaving Def Con after a week of hacks and fun and @kilograhama5 already managed to get Doom running on the Def Con badge. Genuinely very impressed, though of course not surprised, since this community can do anything when it puts brainpower to something.

Speaking of Black Hat and Def Con, there was a lot of controversy about room searches (and their efficacy). Of course, the folks at 404 Media ($) got the leaked guide that hotel staff are using to look for "hacker gear." Such "hacker gear" (he says about as broadly as possible) includes — wait for it... a USB stick.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Tori, who can be seen here taking a huge bite out of cybercrime. Thanks so much to Cynthia B. for sending in!

Please, please, please send in your cyber cats! The supply is running very low! Drop me a quick email with a photo of your cyber cat (or non-feline friend!) with their name, and they will be featured in an upcoming newsletter. Updates are welcome!
~ ~
SUGGESTION BOX
That's all for this week — thanks for taking the time to read! Hope you enjoyed the newsletter. As always, you can get in touch any time by email — and please do send in your cybercats (or their friends!). It really is the highlight of my week.
Until next time,
@zackwhittaker