this week in security — august 20 edition
THIS WEEK, TL;DR
Chinese spies who read State Dept. email also hacked GOP congressman
Washington Post ($): More fallout from the Microsoft cloud hack, which saw China-backed hackers steal a Microsoft key allowing them access to Microsoft cloud-hosted email inboxes of high-ranking government officials, including the Commerce Secretary and a U.S. ambassador. On Monday, the FBI alerted @RepDonBacon, a Republican member of the House Armed Services committee who has pledged to "work overtime" to pass a defense aid package for Taiwan ahead of a possible future invasion by China, that his emails were also compromised by Chinese spies. The FBI won't say why it took all this time to notify Rep. Bacon, given Microsoft learned of the breach back in May, when the State Dept. discovered improper access to official government inboxes and came knocking on Microsoft's door. It comes in the same week that the White House ordered federal agencies to get their cyber s(h)ituations under control after a June deadline came and went, with several government departments having "failed to fully comply" with an earlier executive order prescribing critical security practices.
More: Reuters ($) | CNN | South Morning China Post
Another 4 million people affected by MOVEit mass-hacks
Data Breach Today: If you thought that was bad... The MOVEit mass-hacks continue, with another huge batch of data stolen — Colorado saw its state health care agency's MOVEit instance hacked, with 4.1 million people's data stolen as a result. The agency blamed IBM, which was running the MOVEit instances as part of its engagement with the state. Several other IBM customers were affected, including Missouri's Dept. of Social Services, even though IBM still hasn't publicly acknowledged its MOVEit systems were raided. Per Emsisoft, the number of affected organizations affected by the mass-hacks stands at 728 as of Sunday, affecting at least 47 million people. Remember, that's just those who have disclosed; the real number is going to be significantly higher.
More: Emsisoft | Bloomberg Law ($) | Health IT Security
Exploitation of Citrix ShareFile flaw spikes as CISA issues warning
SecurityWeek: Flip the "number of days since the last file transfer tool flaw" back to zero, as another corporate tool was popped. This time it's Citrix's ShareFile, which allows an unauthenticated attacker to remotely compromise an instance's storage zones. CISA is sounding the alarm on the vulnerability, warning federal agencies to patch ASAP. Details of the flaw were made public back in June by Assetnote, but there has been a "significant spike" in attacker activity since then, per GreyNoise. Let's hope this isn't Clop round four, after the ransomware and extortion group previously hacked three file transfer services: Accellion, Fortra, and MOVEit.
More: CISA | AssetNote | TechCrunch | GreyNoise
Why U.S. tech giants are threatening to quit the U.K.
BBC News: Solid piece by BBC tech editor @zsk on breaking down just what's at stake with the threats made by U.S. tech giants to leave the U.K. over several controversial bills, including an anti-encryption bill and others. WhatsApp and Signal have said they would leave the U.K. if the anti-encryption Online Safety Bill passes, which they say will mandate backdoors in their products. To be clear: these are tech companies saying they would rather walk away from a market than undermine the security of an entire population. This isn't about U.S. companies stamping their feet in an attempt to sway a foreign government, but showing that the U.K. isn't a safe place for technology businesses to operate, particularly security companies or those offering secure messaging apps.
More: Electronic Frontier Foundation | @AlecMuffett tweets
~ ~
THE STUFF YOU MIGHT'VE MISSED
How a hacking crew overtook a real in-orbit satellite at Def Con
Cyberscoop: At this year's Def Con, hackers were tasked with breaking into an actual live satellite zooming over earth at thousands of miles per hour. According to Space.com, the teams were "tasked with hacking into Moonlighter in order to bypass the satellite's restrictions on which targets on the ground it can observe, command it to take a picture of that target and then download that image to a ground station." (You can see that photo below.) As you can see, the team mhackeroni (amazing name) — which won the capture-the-flag competition — managed to pull it off.

Real estate markets scramble following cyberattack on listings provider
Ars Technica: Those working in the real estate world (or looking to buy or sell a house) might have found themselves stymied for days after an apparent cyberattack targeting an online service used to track home listings. The cyberattack targeted Rapattoni, a software and tech provider that supplies Multiple Listing Services to regional estate groups across the U.S. for providing instant access to data on which homes are coming to market. Some users say they "can't list new homes, change prices, mark homes as pending/contingent/sold, or list open houses." More by local Cincinnati news outlet WCPO.
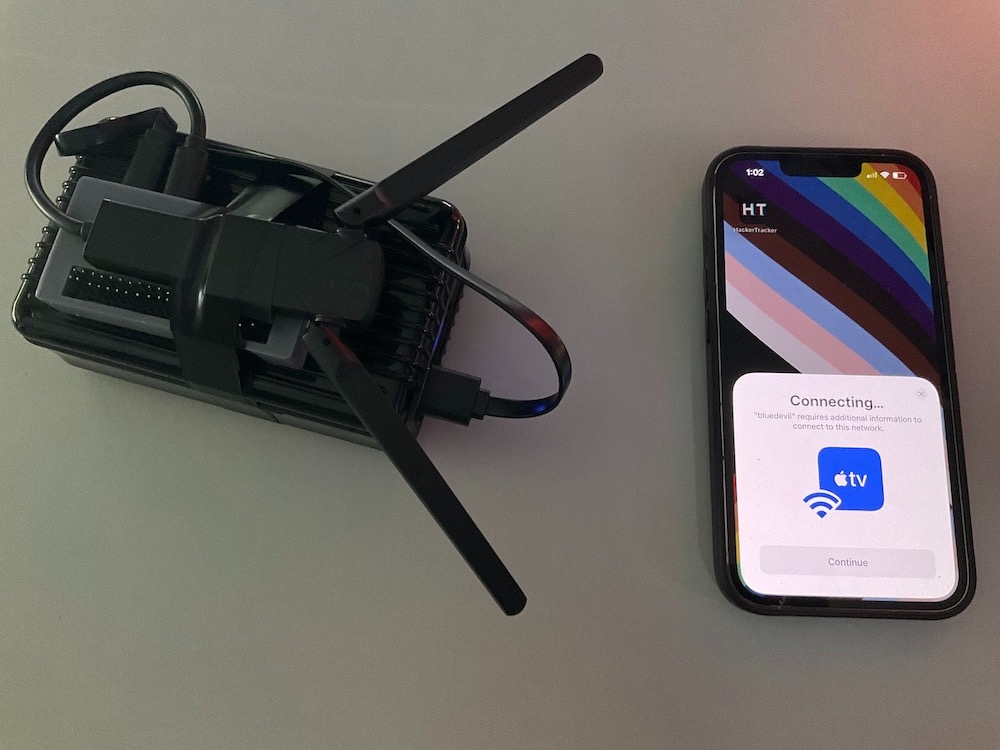
This $70 device can spoof an Apple device and trick you into sharing your password
TechCrunch: For those wondering around Def Con trying to figure out why their iPhone kept alerting them to join an Apple TV, or, more curiously, share a password. A researcher took credit for the stunt, which didn't thrill everyone, but they explained how they pulled it off — with $70 worth of equipment.
~ ~
~ ~
OTHER NEWSY NUGGETS
Clorox kills 99.9% of viruses, but not ransomware: Cleaning supplies maker Clorox said in an 8-K filing it was hit by a cybersecurity incident that caused its operations to go offline and is "expected to continue to cause disruption." What sounds like it could be a ransomware attack, Clorox hasn't commented further since August 14. (via Reuters ($))
NY Finance Dept. shares staff PII in emergency test: Who hasn't accidentally sent the wrong attachment in a really serious work email? But have you ever accidentally shared the home address, cell phone number and personal email addresses of more than 1,700 of your colleagues by botching a test of the emergency notification system? Well, someone certainly had a rough week. A roster of personal information was emailed to employees during the test. NY officials declined to comment further, likely because someone's getting seriously told off. (via The City)
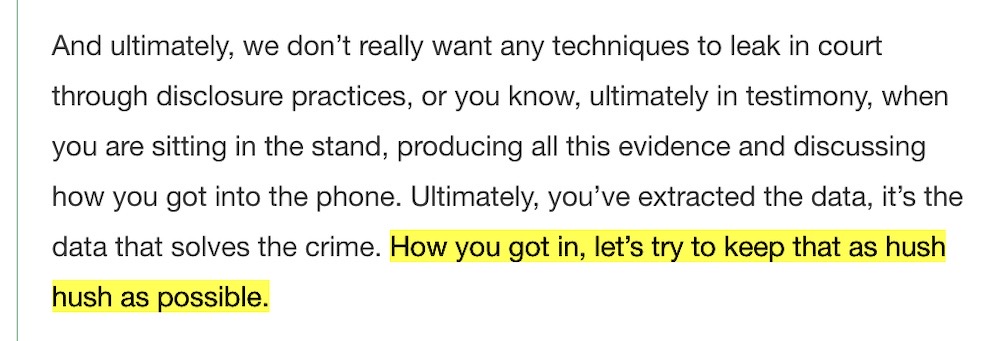
Cellebrite asks cops to keep its phone hacking tech 'hush hush': According to a leaked Cellebrite video for training its law enforcement customers, the company asks cops to keep its phone hacking technology "hush hush" — a secret — citing secrecy to protect the company's trade secrets. But the video also encourages cops to withhold details of how they broke into a suspect's phone in court, troubling lawyers. "We don’t really want any techniques to leak in court through disclosure practices, or you know, ultimately in testimony, when you are sitting in the stand, producing all this evidence and discussing how you got into the phone,” the video says. Of course, we published the full transcript for you to read. (via TechCrunch)
Secureworks hit by 15% layoffs: More layoffs this week after Secureworks confirmed that 15% of its staff would depart following a company re-org focused on trying to "deliver profitable growth." As usual, companies keep forgetting that it's their poor decision making that results in layoffs, not the workers themselves. Not really sure when laying off people became acceptable in modern society, when it should be executives (and their paychecks) facing the music. For Secureworks, it's the second round of layoffs this year. (via WSJ Pro Cybersecurity ($))
~ ~
THE HAPPY CORNER
And that's the news handled. Let's move onto the good stuff in the happy corner.
First up, another real-world example of admin/admin in the wild:

Meanwhile, rough week for red teamers:

And, for no other reason than I can, here's a bonus cybercat from the personal Whittaker collection.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This is Magnumpy, an incredible kitty and amazing character who recently passed away peacefully in the arms of his loving humans, who dearly miss him. Raise a glass to Magnumpy, a forever cyber cat. Many thanks to Ollie K. for sending in.

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
Well that was a shorter than usual newsletter, clearly a shortage of news following Black Hat and Def Con! At least in cybersecurity, no news is good news.
Same time next week? As always, feel free to drop me an email with any feedback you have in the meantime.
All my best,
—@zackwhittaker