this week in security — august 22 edition
THIS WEEK, TL;DR
T-Mobile confirms it was hacked, tens of millions of accounts affected
Motherboard: Getting hacked once is never fun, but five times in as many years and you might want to ask yourself what's really going on. Enter T-Mobile, which this week confirmed it was breached — again — after a seller on a known criminal forum claimed to have records on as many as 100 million T-Mobile accounts, including names, phone numbers, Social Security numbers and driver's licenses (for credit checks) and IMEI numbers. Motherboard first covered the sale, which prompted T-Mobile to kick into gear — only to admit days later that Motherboard's original report was pretty much on the money. T-Mobile confirmed (and continues to update) some 61 million current and former account details were accessed in the incident. Bleeping Computer, citing the hacker, said T-Mobile's systems were compromised by way of accessing a production Oracle database over the internet.
More: Motherboard | T-Mobile | Wall Street Journal ($) | @briankrebs
Apple says researchers can vet its child safety features. But it's suing a startup that does just that
MIT Technology Review ($): Really solid reporting by @HowellONeill on the Apple-Corellium lawsuit, which Apple recently settled... and then started again. Although the case is largely about copyright, it's really about Apple's defense of iOS security. But Apple appealed its own settlement (which it can do, apparently?) to continue the case after Corellium announced a $15,000 grant to help examine Apple's recent CSAM detection claims. Which is weird because Apple has both said it wants researchers to examine its technology, but then will sue a startup that's offering to do just that. @HowellONeill has a good tl;dr thread, too, but the full piece is really worth the time.
More: The Register | @HowellONeill tweets | @selenalarson tweets
We built a CSAM detection tool like Apple — we concluded it was dangerous
Washington Post ($): Speaking of things going not great, Apple is facing a blast wave of criticism from security researchers and — you know, the sort of people who have been actively researching this stuff for years. More than 90 policy groups called on Apple to halt the child sexual abuse materials (CSAM) detection and message-scanning technology, fearing it could be abused by authoritarian governments. Apple meanwhile says the system has safeguards, including manual review. But academics @jonathanmayer and @anunaykul separately sounded the alarm this week, because they had built a similar CSAM detection tool and concluded that it was "dangerous." And it wasn't through a misunderstanding of how Apple's version of the technology works: "The problem is, we understand exactly how it works."
More: Ars Technica | Reuters ($) | TechCrunch
BlackBerry resisted announcing major flaw in software used by millions
Politico: BlackBerry this week announced that old but widely used versions of QNX software, which is used in hundreds of millions of devices like cars and hospital equipment, are vulnerable to a kind of memory allocation vulnerability called BadAlloc, which Microsoft revealed back in May. So why is this news, when other companies affected by BadAlloc went public months earlier? Per new reporting, BlackBerry dragged its feet and resisted making a public announcement, until CISA got involved. And probably for the best, since CISA's argument was that it would've been difficult to alert every consumer unless the government stepped in.
More: ZDNet | The Register | @ericgeller | Background: Dark Reading
The FBI's warning to Silicon Valley of spies and espionage
Protocol: Silicon Valley firms are, unsurprisingly, a target for espionage, so that's why the FBI out in San Francisco is quietly warning and briefing companies — from startups to venture firms — about the threat posed by spies from adversarial nation states trying to steal information or recruit employees to spy. The FBI uses the so-called Delta Protocol (no relation to COVID-19) as a way to help companies defend from a range of threats, including intellectual property theft.
More: @bizcarson | @thegrugq
The Taliban have seized U.S. military biometrics devices
The Intercept: It's pretty much the nightmare scenario for many Afghans currently under Taliban occupation after a swift offensive across the country took the U.S. by surprise. Many Afghans who helped Western forces, like interpreters and translators, are trying to flee the country and the Taliban's oppressive rule. Allied forces know who these people are by way of biometric databases with their retina scans over the past 20 years. But now that the Taliban have taken control — along with the Allied force's hardware — it's feared these could be used by the Taliban to target individuals using biometric data left behind by the U.S. forces and Afghan government. The BBC also looks at the implications of the biometric data getting into the Taliban's hands. It comes as Facebook and other platforms rolled out new features to let Afghans lock down their profiles fearing retaliatory attacks from Taliban fighters.
More: BBC News | Cyberscoop
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
America's secret terrorist watchlist exposed on the web without a password
Bob Diachenko: Discoverer of exposed data, @MayhemDayOne, found what appears to be a copy of the U.S. terrorism watchlist, containing about 1.9 million names, stored on a server with a Bahrain IP address. The watchlist indicated if a person was on the U.S. no-fly list and other sensitive information. Gizmodo covers the story well, given there are known cases where innocent people are added, or reformed individuals are unable to get off the list.
Apple's double agent
Motherboard: Wild reporting by @lorenzoFB. Apple had a mole in the jailbreak community, who advertised leak data and passed on information as an informant to Apple's Global Security team, an Apple unit made up of former U.S. intelligence officers that almost exclusively hunts for leaks. The mole gave Apple names of people who bought prototypes from gray-market vendors. But then Apple refused to pay him, and that's when things really went downhill.

macOS 11’s hidden security improvements
Malwarebytes: Here's an interesting look at some of the new hidden security features and improvements in macOS 11. It's a pretty good guide for anyone interested in how macOS' security works behind the scenes.
Blackbaud, which paid off a ransomware group, fails to get California suit dropped
The Register: Blackbaud, an education tech company that was hit by a major ransomware attack in 2020 and paid the ransom in its wake, has failed to get a lawsuit under California's recently enacted privacy law thrown out. The company was accused of not doing enough to prevent the 2020 attack and downplaying in the aftermath. A judge in South Carolina tossed out some of the claims in a class-action suit, but allowed state plaintiffs to sue under CCPA, California's GDPR-like law, which could see the company liable for $750 per violation.
How to hack Apple ID
Medium: @zemnmez found some fascinating security flaws in the Apple ID login process, which allowed him to show in a proof-of-concept how he could take over an Apple ID. It's a long read but it's a solid one, and one that granularly explains the full exploit chain. Apple paid just $10,000, which is 2.5x lower than for creating an app that can access "a small amount of sensitive data." One of the world's wealthiest companies, and it's scrimpy with researchers who keep its billion-plus users safe. "We take security seriously," etc.
~ ~
OTHER NEWSY NUGGETS
Millions of web camera and baby monitor feeds are exposed
Wired ($): Well, this isn't good. A vulnerability in an SDK called ThroughTek Kalay, used by tens of millions of devices to connect smart home devices to their apps, allowed remote access to a video feed from the app, such as a baby's crib or security footage. Attackers have to be on the same network as a vulnerable device, but CISA issued an advisory.
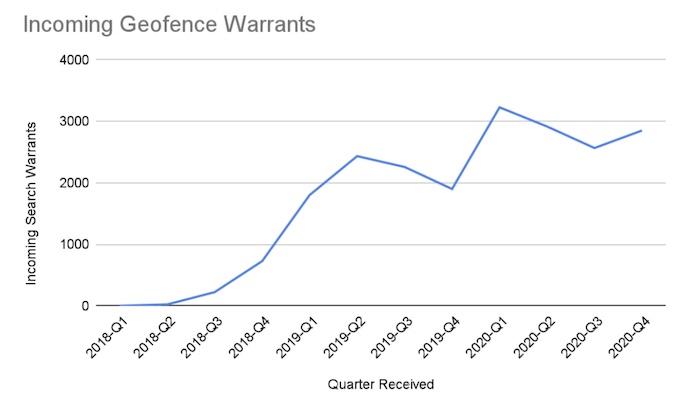
Google says geofence warrants make up one-quarter of all U.S. demands
TechCrunch: After years of lobbying by civil liberties and privacy groups, Google has finally published the number of geofence warrants it's received since 2018. The numbers are very basic, but it shows thousands of geofence warrants served on the company every quarter — in some cases representing one-quarter of all U.S. legal processes that Google receives every month. Geofence warrants are largely unique to Google because the company stores so much location data on its billion-plus users, and police are frequently using this data to figure out who — specifically whose phones — were at the scene of a crime. (Disclosure: I wrote this story.)
Interview with CEO of Positive Technologies, accused by the U.S. of hacking for the Kremlin
Forbes: A good interview with Yury Maksimov, the majority owner and (now former) CEO at Positive Technologies, which was earlier this year was sanctioned by the U.S. amid accusations that it supported Russian intelligence, charges that the company denies. It's a good read — and some skepticism is probably warranted — though not the reporting itself. In fact, @iblametom confirms earlier reporting by @kimzetter that Positive is ENFER, a codename designated by the Atlantic Council in a report that accused ENFER/Positive of taking malware from an attack on a Russian organization and allegedly repurposing it for future intrusions. Fascinating read.
Cloudflare says it mitigated a record-breaking 17.2M rps DDoS attack
The Record: Cloudflare said it's mitigated a DDoS attack, made up of a botnet of more than 20,000 infected devices, peaking at about 17.2 million HTTP requests a second (rps), which is about three-times the size of the previous record holding event. Good to know that Cloudflare mitigated this one. Not so good to know that DDoS attacks at this scale are happening.
~ ~
THE HAPPY CORNER
Happy Sunday, and especially to those who read this section first.
Something I didn't know until last week: Shodan, the search engine for exposed databases and servers, has a "me" feature that lets you check to see if your IP address is exposing any ports to the internet — which is cool! If you get a 404 page, that means nothing was found.
If you ever needed a reason to help a hacker out, this is why. This is a lovely story, and great to see @ngenge_senior working on some cool things!
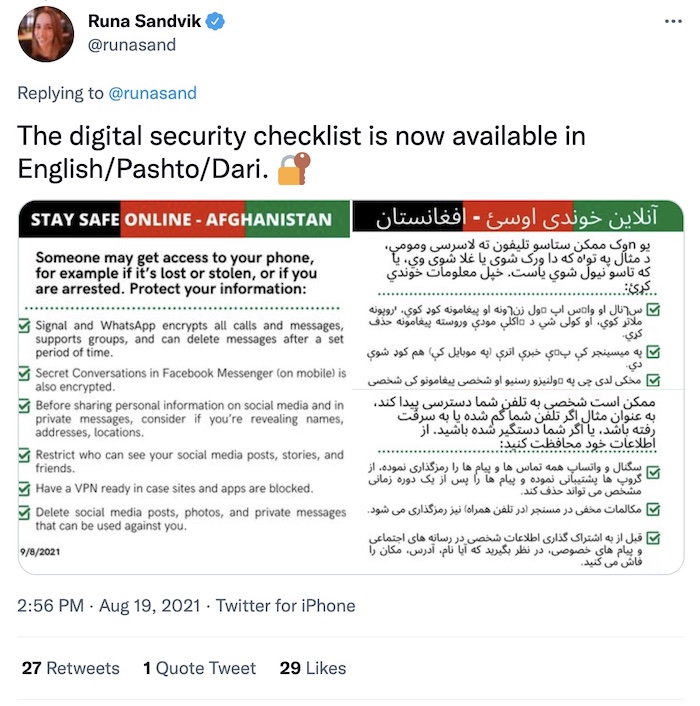
A quick one for anyone who might be reading in Afghanistan (or anyone in an area of the world who needs help locking down their online life). Here's a short digital security checklist made by @runasand and @msuiche to help anyone who needs it. (It's also available in Pashto/Dari.)
And, ~this week in security~ hit 9,000 subscribers this week. Absolutely stoked. I can't thank you all enough for reading and supporting the newsletter over the years.
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
Meet Tornade ("tornado" au francais), this week's cyber cat. According to her human, she's not so much into cybersecurity but she does love keyboards (especially when it's being used). So, a hacker-by-proxy? A big thanks to Antoine V. for the submission!

Don't forget to send in your cyber cats (or their friends)! Email with their name and photo here!
~ ~
SUGGESTION BOX
And that's it for this week. Many thanks to you for reading (and subscribing). As always please feel free to drop any feedback in the suggestion box or email me at this@weekinsecurity.com. Be well, and see you next Sunday. Take care.