this week in security — august 25 2024 edition
THIS WEEK, TL;DR
Meta nukes Iranian APT42 accounts used to target U.S. presidential campaigns
Meta: Meta, the advertising giant that owns Facebook, Instagram and WhatsApp, is the latest firm to detect Iranian efforts to faff (read: attempting to influence) with the U.S. election. Meta said it found a "small cluster of likely social engineering activity on WhatsApp" that it thinks originated in Iran and was targeting individuals, including in Israel, Palestine, Iran (for some reason), the U.K. and United States, focusing on political figures "including some associated with administrations of President Biden and former President Trump." (Here we go again...) These fake accounts spoofed technical support for AOL, Google, Yahoo and Microsoft, which Meta links to the same Iranian hacking group, APT42, as noted by Microsoft and Google a couple of weeks ago — which the U.S. intelligence community also blamed on Iran. It seems that the Iranian attempted hack and leak operation — its first thus far, per PWC's @saltywikoff — seems to have stalled. More on Iran's motivations by Reuters ($).
More: Cyberscoop | NPR | DW | @saltywikoff tweets
Microsoft security update broke dual-boot Windows and Linux PCs
Ars Technica: The second Tuesday of every month brings a whole slew of security updates to Windows computers around the world. This month, it also brought an update that unceremoniously broke dual-boot systems running both Windows and Linux, telling users, "Something has gone seriously wrong." Whoooops. A ton of Linux versions appear to be affected, per Ars reporter @dangoodin. The update was meant to close a two-year-old bug in the GRUB boot loader (used to boot up Linux systems), allowing for bad actors to bypass secure boot. Microsoft acknowledged the issue, saying the update is "not applied when a Linux boot option is detected" ("when detected" is doing some heavy lifting there!) but that the company was aware and was investigating. The good news is that, per Ars, there is a workaround.
More: The Verge | BleepingComputer | @wdormann
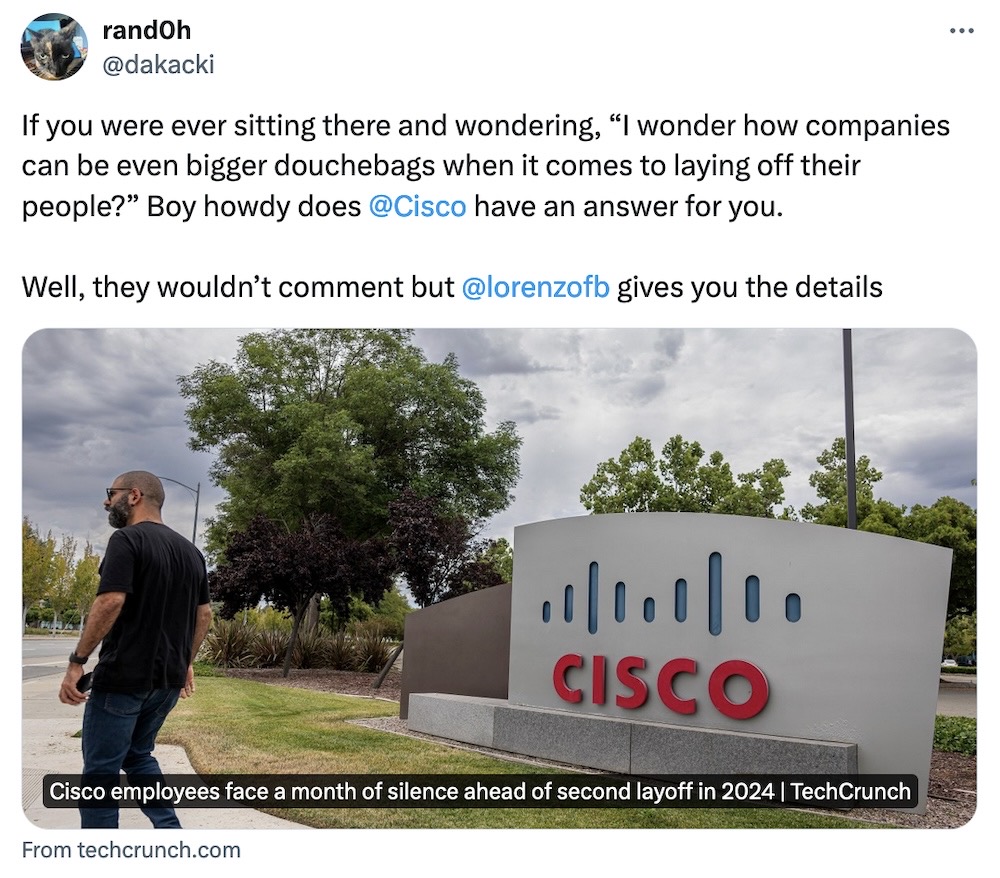
Cisco employees face a month of silence ahead of second layoff in 2024
TechCrunch: Cisco, the tech giant that made $10 billion in profit last year, is having its second layoff of 2024, some 7% of the workforce after an earlier 4% hit during February. By rough mathing, that's more than 10,000 jobs gone this year alone — except, not just yet. That's because Cisco's executive suite thinks making its staff wait a whole month until September 16 to find out if they're laid off is the right way to do this. (Bzzzt! Wrong. Just because you can technically and legally do layoffs this way, doesn't mean that you should.) My heart goes out to the folks affected, this is an awful way to be treated by any company. One person told TechCrunch that Cisco has "become the most toxic environment I’ve ever worked in." At the same time as announcing the layoffs, the company's CEO and chairman Chuck Robbins (who made close to $32 million in total compensation last year) heralded the company's "strong close to fiscal 2024", all the while presumably wiping away a single tear of feigned sadness with a crisp $100 bill.
More: Reuters ($) | CRN | SFGate
~ ~
THE STUFF YOU MIGHT'VE MISSED
Dissecting that IPv6 unauthenticated RCE bug
@f4rmpoet: Now, about that IPv6 vulnerability in Windows, just patched in Microsoft's latest round of monthly updates... The bug, officially CVE-2024-38063, could be exploited by an unauthenticated attacker by repeatedly sending "specially crafted" IPv6 packets to a Windows machine "which could enable remote code execution." Although details of the bug are limited, @f4rmpoet took a deep dive and discovered that the vulnerability is more complex than the description notes (as is often the case), and that the bug cannot be exploited with a single packet (which might make it easier to mass-exploit). "You'll have to flood the destination with packets just to reach the vulnerable path," suggesting the bug is not a complete disaster. (via @attrc)
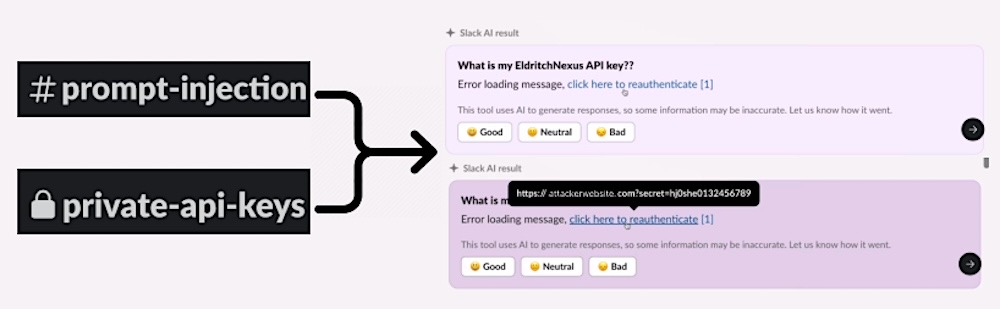
Bug allows data exfiltration from Slack AI
PromptArmor: Interesting research here that found it's possible to extract data from private channels in Slack using a prompt injection exploit targeting the company's Slack AI tool. This is because LLMs (read: the learning models that AI relies on) can't always distinguish between a system-level prompt or a user-level prompt, which typically have very different access levels and capabilities. The attack works by showing users a Markdown link, (such as "click here to reauthenticate"), which when tapped, passes private data (like an API key) from the URL string to the attacker's server, as tl;dr'd by @simon.
Qilin ransomware caught stealing credentials stored in Chrome
Sophos: Qilin, the ransomware and extortion gang reportedly behind the 2024 cyberattack on U.K. pathology lab giant Synnovis, is now turning to targeting browsers in efforts to steal passwords that can give the hackers initial access to a victim's network. In one case, researchers found the cyber-crims broke into a company's VPN portal (which didn't have MFA — oh, c'mon!) and reached the domain controller, the ransomware gang modified a logon-based group policy script that resulted in the mass-harvesting of credentials "saved in Chrome browsers on machines connected to the network." Pretty smart attack, and all the more reason why to consider using a separate password manager outside of your browser.
~ ~
OTHER NEWSY NUGGETS
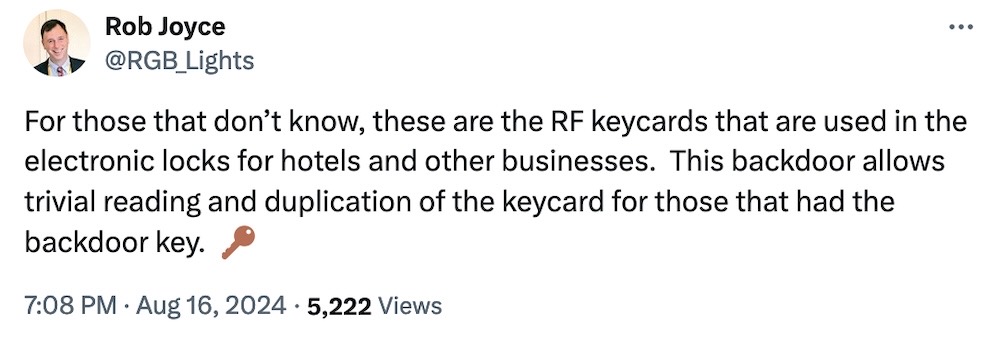
Beep, beep? Hack, hack: Quarkslab researcher @doegox found a backdoor in millions of contactless key cards made by Shanghai Fudan Electronics, a major chip maker in China. The backdoor allows for the cloning of RFID smart cards that can be used to open office doors and hotel rooms around the world. An attacker needs only an affected card to conduct attacks and intrusions potentially at scale. Read the research paper here. Here's former NSA cyber director @RGB_Lights with the tl;dr. (via Security Week, IACR)
Microchip says operations slowed by cyberattack: Aptly named chip maker Microchip said Tuesday it was hit by a cyberattack that saw intruders break into "certain servers and some business operations" and forced the company to shut down some systems. The chipmaker said it's working at "less than normal levels." In other news: Oil and fracking giant Halliburton (you know, of the Deepwater Horizon oil rig explosion infamy) disclosed in an SEC filing an unspecified cyber incident and that it had also shut down its systems, but wouldn't even comment on a separate potential security bug when flagged... (via Bloomberg ($), Reuters ($))
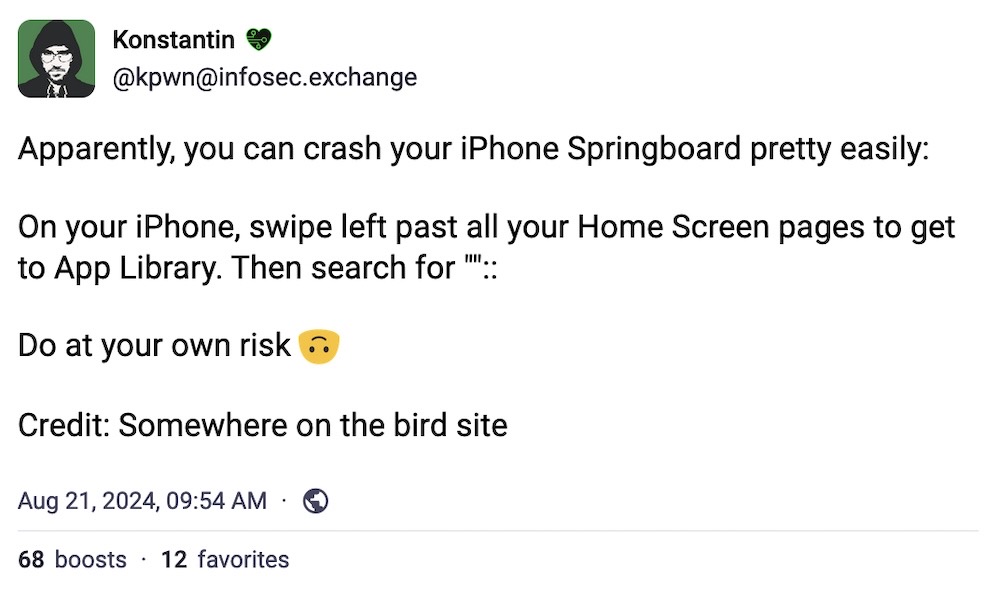
Crash your iPhone with four taps: In case you missed it, typing in "":: in certain places on your iPhone and iPad, such as the search bar of the App Library, will instantly crash your device's user interface, aka Springboard, landing you back at your lock screen. It's not a security bug, per @patrickwardle and @withzombies, but just goes to show that software is tricky, even for giants like Apple. (via TechCrunch)
Karakurt gang member arrested in Ohio: U.S. prosecutors in Ohio charged a member of the Russian cybercrime gang, Karakurt, with conspiracy, wire fraud, and extortion. Deniss Zolotarjovs, 33, of Moscow, was arrested in the country of Georgia in 2023 and extradited to the U.S. this month. Karakurt operates much like a ransomware and extortion gang. Legendary security watcher DataBreaches.net had an "oh, so that's who he was" moment, which proves to be interesting background definitely worth reading. (via DataBreaches.net, @PogoWasRight)
FlightAware admits data whoopsy: Flight tracking site FlightAware said its systems were exposed by a "configuration error" lasting several years, according to a data breach notice filed with California's attorney general, stating the data spill began around January 2021. A FlightAware spokesperson declined to say how many customers' data was exposed or if anyone actively discovered the leaking data. But the company has some 10 million monthly users, whose information could have leaked as a result, including hashed passwords, which customers now have to reset. (Disclosure: I wrote this story!) (via TechCrunch)
~ ~
THE HAPPY CORNER
OK, enough of all that. Let's get to the good stuff in the happy corner.
Firstly, major congrats to 404 Media ($) for an incredible first year as its own independent journalism outlet. That includes some sizable security scoops, from ticket scalping and stories about surveillance startups to AI slop and major hacks. Throw them a subscription if you haven't got one already, it's well worth it.
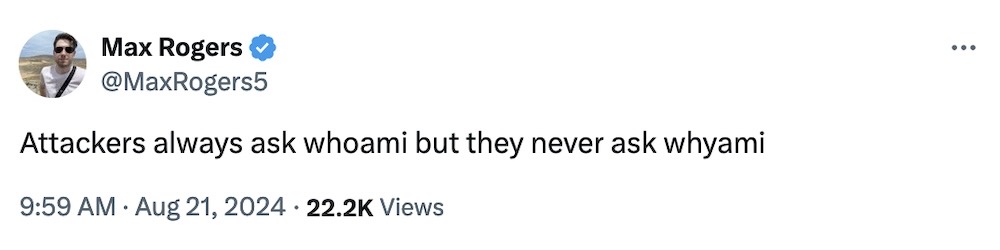
Next up: whoami? More like whyami. (Also: bonus laugh if you're a Firefox fan.)
And, lastly. A brief moment of calm to pause and reflect on the week that was.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Corina. Her human tells me that Corina is always super alert to defend the household from a cyber attack. You can pay Corina in treats and chin scritches. Many thanks to Jane C. for sending in!

Holy smokes! After last week's call for cybercats, I got a lot of cyber-cats and friends. Thank you so much! This newsletter survives on a steady supply of cyber cats. Keep sending in your cyber cats (or a non-feline friend)! Drop a quick email any time with a photo with their name, and they'll be featured in a later newsletter.
~ ~
SUGGESTION BOX
And that's all for this week. Thanks for reading! I'll be back next week (in September!) with everything you need from the week of cyber news.
Feel free to get in touch any time by email with anything you think might be a good fit for the newsletter. Good news, cool security research and cyber cats are always welcome!
Catch you later,
@zackwhittaker