this week in security — august 27 edition
THIS WEEK, TL;DR
The secret weapon hackers use to dox nearly anyone in the U.S. for $15
404 Media ($): Well this is one hell of a way to launch a new media company... Millions of Americans have no choice but to opt-in to the grubby credit bureau data sharing system because that's just how America rolls, but hackers have found a way into the data supply chain, reports @josephcox for 404 Media, the new site Cox and former Motherboard reporters recently founded. Hackers are sharing access to bots that spit out credit headers, which is particularly sensitive credit data containing most Americans' credit reports and other sensitive information. Cox also found hackers obtained data on high-profile individuals, including President Biden and Elon Musk. This game of whack-a-mole between the credit agencies and the hackers will likely continue on. The Consumer Financial Protection Bureau — responsible for regulating credit header data — has been urged to stop the sale of this sensitive consumer data. Absolutely brilliant reporting here. Full disclosure: I have already subscribed to 404 Media; and you should too if you can!
More: Bloomberg Law ($) | Forbes ($) | @josephcox | @evacide
Danish hosting firm says it lost all customer data after ransomware attack
Bleeping Computer: Cloud hosts CloudNordic and Azero say that customers have "lost all data with us" after a ransomware attack wiped out its datacenter systems and backups (yikes). It's not clear which ransomware gang is behind the breach, but both companies said that the infection crashed their shared network. The only(?) bright spot is that data likely wasn't exfiltrated from its systems, even if it was still rendered absolutely unusable or unreadable. What made matters worse is that during a datacenter move, the hosting company moved an infected system into its new datacenter, which "unfortunately wired to access our internal network that is used to manage all of our servers." It was from there that the hackers could "encrypt entire disks." CloudNordic said it "had no knowledge" that there was an infection. Both companies appear down at the time of this newsletter, though both said they would try to recover users' systems — albeit without their data.
More: TechCrunch | DCD | ITPro | Radio4 (dansk)
U.K. court says teenagers carried out hacking spree
BBC News: A U.K. court says an 18-year-old was a member of the notorious Lapsus$ hacking group, whose jury was asked to find whether the teenagers were members of the group — not if they had criminal intent. The case is complex in large part because U.K. reporting rules mean we can't name all of the defendants due to their age. The 18-year-old who was named, Arion Kurtaj, was a key member of Lapsus$, but was ruled unable to stand trial. Lapsus$ was — for a time — a significant hacking force, targeting Uber, Nvidia and Rockstar Games. Who knew that a bunch of teenagers could cause so much trouble? Well, CISA's CSRB post-mortem report into the mass Lapsus$ hacks — released this month — goes into more details about just how they pulled it off. The lesson here? Secure your systems, and never underestimate a bored teenager.
More: Bloomberg ($) | SecurityWeek | The Verge
~ ~
THE STUFF YOU MIGHT'VE MISSED
WinRAR users urged to update after critical flaws found
CSO Online: WinRAR, one of the most popular software apps in existence, dropped a new version this month with fixes for two major security flaws. The first allows remote code execution on a victim's device. The second is an actively exploited zero-day that targeted traders to steal funds. Update today!
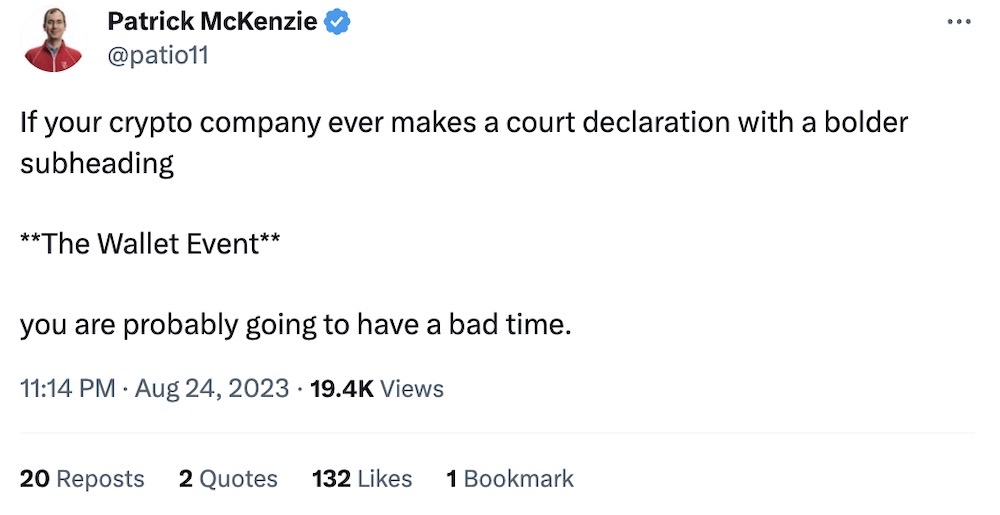
Crypto startup goes bankrupt after losing password to $39M physical wallet
404 Media ($): You know it's a bad day when you can sum up your entire bankruptcy filing as "The Wallet Event," but that's exactly what happened to one buzzy crypto startup, Prime Trust. The company went out of business after losing the password to its physical crypto wallet that stored close to $39 million in assets. Oh, and the alleged embezzlement. Almost forgot to mention that! @patio11 has a good tweet thread on the case.
Poland investigates cyberattack on rail network
BBC News: Polish spy agencies are investigating a possible hacking incident involving the country's railways, according to Polish media as reported by the BBC. Dozens of trains were disrupted in the north of Poland, apparently interspersed with recordings of Russia's national anthem and a speech by Putin. Having your train home delayed is bad enough, but having to listen to some washed-up racist authoritarian endlessly drone on about the "old Soviet days" is enough to drive anyone up the wall.
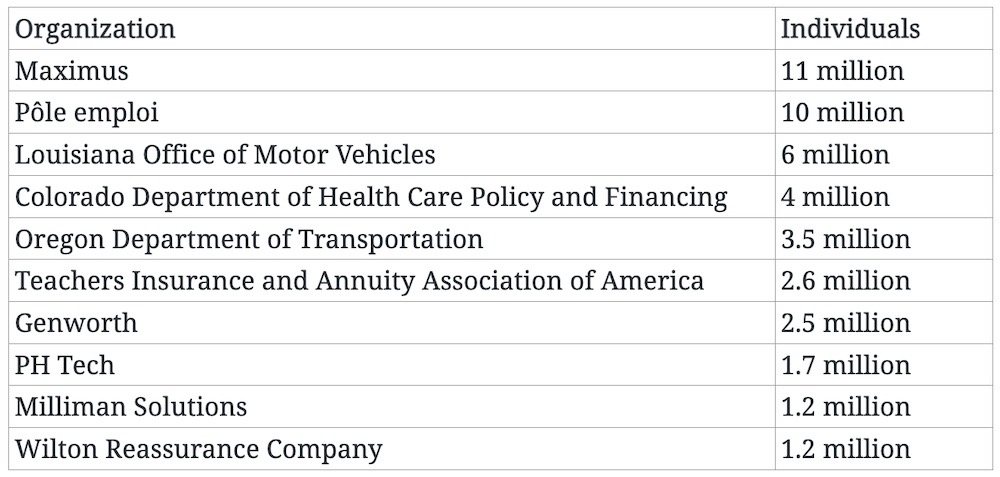
MOVEit, the biggest hack of the year, by the numbers
TechCrunch: New data this week shows that the MOVEit mass-hack and extortion incident now affects at least 1,000 organizations, a new milestone for the largest hack of the year so far, ensnaring some 60 million people at least. That's because only a handful of organizations have come forward — and that includes several states: Colorado, Louisiana, and Oregon with multi-million sized data breaches of residents' data. My TC colleague @carlypage breaks down the MOVEit mass-hack by the numbers. More from Emsisoft, which has been tracking the data.
~ ~
OTHER NEWSY NUGGETS
Huge cyber-takedowns in Africa: An international law enforcement operation across two-dozen African countries led to the arrests of 14 people and the takedowns of hundreds of malicious IP addresses and malware hosters, according to Interpol, which claims it has identified more than 20,000 suspicious cyber networks. The international feds claim the networks were linked to $40 million in losses. That includes darknet site takedowns, 185 Gambian IPs found connected to malicious activity, and three arrests involving an online-based art scam. (via Cyberscoop)
Violation de données de Duolingo: Scraped data of 2.6 million Duolingo users was posted to a hacker forum this week. According to the post, the data was scraped from a publicly exposed Duolingo API. Duolingo confirmed the spill, which reporters said included both public and non-public information, such as email addresses. The exposed API is still public though, and Duolingo hasn't explained why this is (still) the case. (via The Record, Bleeping Computer)
Prospect says hospitals still offline after cyberattack: It's been more than two weeks since Prospect Medical Holdings said it was hit by a cyberattack that has all the hallmarks of ransomware (though the hospital chain giant hasn't yet confirmed this — or really much else, actually). Its hospitals are still offline and elective surgeries, outpatient appointments, and blood drives have been delayed. Prospect, which made several billion in revenue in recent years, doesn't know when it'll be back online. I would love to know how much was actually spent on cybersecurity, though I'm guessing "clearly not enough" is the closest we'll get to an accurate answer. If you want to read what ProPublica discovered about Prospect's profit-driving back in 2020, it's worth your time. (via Associated Press)
Kroll hacked after SIM-swap: Security consulting giant Kroll confirmed it was hacked recently after an employee was SIM swapped and that access was used to steal internal data for multiple cryptocurrency platforms relying on Kroll in their ongoing bankruptcy proceedings, including BlockFi and FTX. If you guessed eighth-time-hacked telco giant T-Mobile, you'd be right. Kroll called out T-Mobile in its statement, accusing the company of giving the Kroll employee's phone number to a threat actor "without any authority from or contact with Kroll or its employee." (via Kroll, KrebsonSecurity)
~ ~
~ ~
THE HAPPY CORNER
OK, enough with all that. Let's move onto the good stuff. Just a couple of things this week:
Belated FOMO from Black Hat as @lhn got to hang out with New York DJ duo The Chainsmokers to chat about... *checks notes* their recent investment in phone security app iVerify, which landed $4M in seed funding after graduating from an incubator at security firm Trail of Bits. Here's the Wired ($) story of their conversation, which — as you might imagine — dives into why two DJs of all people would want to invest in a cybersecurity startup.
And, finally. Absolutely no notes here.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's two-for-one cyber cat special is Finn and Stevie, who are in-house two-factor authentication. Give them a treat for their troubles. Many thanks to Jenn K. for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's it from me for now. Thanks for reading and subscribing! As always, please drop me any feedback to my email.
Have a wonderful week,
—@zackwhittaker