this week in security — august 29 edition
THIS WEEK, TL;DR
38 million records were exposed online — including contact-tracing data
Wired ($): If it isn't the curse of "public by default." This time it's Microsoft's turn after a broad swath of data was left exposed. At fault were Microsoft's Power Apps, which allow users to spin up new web applications really quickly, like vaccine appointment websites during a pandemic, for example. But a lot of these apps were exposing data because Power Apps are set to public by default (as Amazon S3 buckets once were). Researchers at UpGuard found a ton of exposed Power Apps instances and, while no evidence that any of these had data stolen, still publicly exposed a lot of sensitive data, like contact tracing records. American Airlines, Ford, and New York City's MTA had data exposed, according to UpGuard. Microsoft recently changed the permissions on Power Apps instances so that they default to storing data privately.
More: UpGuard | Threatpost
Researchers, cybersecurity agency urge action by Microsoft cloud database users
Reuters ($): More bad news for Microsoft this week, after a separate Azure cloud vulnerability was disclosed. The software and cloud giant warned all users of its Azure-flagship Cosmos DB database service to change their keys. Researchers said it was able to access the keys that control access to databases held by thousands of customers, which Microsoft doesn't control and can't change itself. Ars Technica has a good explainer on the vulnerability.
More: Wiz | @JGamblin
Bahraini government hacks activists' iPhones with NSO Group zero-click exploits
Citizen Lab: Citizen Lab found that the Bahraini government was behind a hacking campaign to compromise critics of the kingdom with NSO Group's Pegasus spyware, which used a new zero-click, zero-day to target at least one Bahraini activist. The exploit takes advantage of a flaw in iMessage, like earlier exploits, but this one bypasses new Apple defenses built into iOS 14, dubbed BlastDoor. Worse, Apple has given no indication that it will or plans to fix the vulnerabilities until iOS 15. In other words, that's tens of thousands of human rights defenders who own iPhones but are no longer safe from their own authoritarian governments. That's two months where so many human rights defenders are at risk of death or being disappeared.
More: Associated Press | TechCrunch | @citizenlab
La Puente man steals 620,000 iCloud photos in plot to find images of nude women
Los Angeles Times ($): A Los Angeles man broke into thousands of Apple iCloud accounts and collected over 620,000 private photos and videos of his victims, according to feds. The man impersonated Apple's customer support staff and tricked victims into providing their Apple IDs and password without Apple noticing. In the end, a California company that specializes in removing celebrity photos from the internet traced the leak back to the man. Which, on top of the Pegasus intrusions and given Apple's recent push to scan device content for CSAM, Apple doesn't look so great from atop its mighty pedestal these days.
More: @matthew_d_green | @caparsons
Hackers are trying to topple Belarus’s dictator, with help from the inside
MIT Technology Review ($): Solid reporting on the Belarusian resistance (or more accurately, hacktivist movement?), following last year's elections, where President Lukashenko won what was widely seen as a rigged election. This tells the story of the Belarus Cyber Partisans, a group of hackers — mostly IT experts from Belarus' technology sector — who have breached and published dozens of sensitive police and government databases as part of a movement to undermine the Lukashenko regime. It's a fantastic read. Also read Bloomberg ($), which also has more. "If ever Lukashenko ends up facing prosecution in the International Criminal Court, for example, these records are going to be incredibly important," said one expert.
More: Bloomberg ($) | @HowellONeill tweets
China's Microsoft hack may have had a bigger purpose than jus spying
NPR: Another great deep-dive by @NPRDina. The piece looks back at Beijing's "Hafnium" attacks against Exchange servers across the U.S. and the world earlier this year. It seems the attacks had more of a goal in mind: to steal artificial intelligence research from companies, governments, and universities. "The Beijing leadership aims to lead the world in a technology that allows computers to perform tasks that traditionally required human intelligence — such as finding patterns and recognizing speech or faces," reports Temple-Raston. This week also saw similar attacks targeting Exchange servers, though it's not clear if China is behind this latest wave. Also read this week, @snlyngaas had an incredible read on Cyberscoop about the case of a Kuwaiti security researcher and a missing $9 million in a country where suppression is considerable and punishments — even for good faith hackers — are steep.
More: Cyberscoop | @snlyngaas | @NPRDina | @WilliamYang120
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Razer bug lets you become a Windows 10 admin by plugging in a mouse
Bleeping Computer: A zero-day discovered in software used by Razer and posted on Twitter opens the door to Windows admin privileges simply by plugging in a Razer keyboard or mouse. Turns out plugging in a Razer device allows Windows to pull the software from the internet, but that software — used by 100 million users worldwide — installs with SYSTEM privileges.
U.S. Army has a contract with Clearview AI, records show
Business Insider ($): The U.S. Army's criminal investigation division (CID) has a contract with Clearview AI, the controversial facial recognition startup that scraped billions of public images from Google, Facebook and YouTube and others to sell surveillance capabilities to its customers. According to documents obtained by @caro1inehaskins, the Army spent $15,000 on the contract. The ACLU is suing Clearview AI under Illinois' biometrics law, and yesterday, a federal judge declined Clearview's motion to dismiss the case.
CISA director wants to spend more time preparing for big hacks
Cyberscoop: One of the first interviews with CISA's new director, @CISAJen landed this week. A big takeaway is that CISA, the Homeland Security unit tasked with cyber defense, wants to break out of the scramble-to-recovery cycle and spend more time preparing for inevitable incidents and reducing their impact. It's a great interview if you're trying to understand how the federal government plans to address some of the bigger cybersecurity issues. It comes in the same week that Apple, Google and Microsoft pledged billions in cyber investments. Which is also to say:
Phishing campaign uses UPS.com XSS flaw to distribute malware
Bleeping Computer: A smart phishing campaign here that relies on an XSS on UPS' website, effectively allowing the campaign operator to send a phishing email to a malicious download that looks like it's hosted on UPS' website. Once the phishing email is opened, the XSS pulls a fake invoice (with a malicious macro inside) from a Cloudflare worker. Simple, but looks effective.
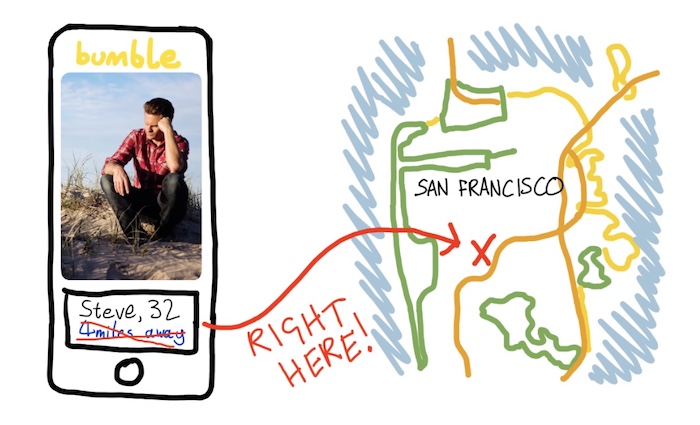
Vulnerability in Bumble dating app reveals any user's exact location
Robert Heaton: Great storytelling of a vulnerability in dating app Bumble that revealed any user's exact location using a trilateration vulnerability. Bumble fixed the bug, but the storytelling here is really something — and really puts a spotlight on how a viable attack scenario might work.
~ ~
OTHER NEWSY NUGGETS
A hacker stole and then returned $600 million
Motherboard: What do you do when you hack and steal $600 million in virtual currency? Give it back, apparently. That's the result of the massive Poly Network heist, which seems to be over, after the company pleaded for the money back. And it... worked. Whatever the reason for the hack, Poly got its money back and learned a valuable security lesson in the process. And that was that.
Hackers leak surveillance camera videos from inside Iran's Evin prison
Zero Day: Iran's Evin prison is notorious for abuse and human rights violations. But videos leaked this week show what happened when prison staff realized their systems had been hacked. Videos in the prison's control room flashed messages like "CYBERATTACK" and "GENERAL PROTEST," per Motherboard. The hacked-and-leaked videos appear to date from 2020 and 2021. The hackers did not say how they broke in — but that they were calling on Iran to release political prisoners held by the state. The full video is here.

Hackers could increase medication doses through infusion pump flaws
Wired ($): A popular B. Braun infusion pump and dock could be manipulated to administer a double-dose of medication of a victim, according to new research. It would take a determined actor a fair amount of work, and requires being on the health care facility's network first. There's no evidence of exploitation, but it shows, once again, that even networked medical devices can pose a risk to their patients, even if small.
Inside a massive cyberattack on a Philippine human rights group
Rest of World: Researchers have traced a month-long DDoS attack against a Philippine human rights group back to an Israeli company’s network. "Billions of requests, thousands of dollars spent on feeding garbage 24/7, night and day," said Tord Lündstrom, the technical director at Swedish cyber non-profit Qurium, which traced the attack back a network operated by Isareli company Bright Data, which runs data centers and proxy networks. Bright Data denied any involvement. It's believed a customer was ultimately to blame, since emails seen by Rest of World show Bright Data acknowledged in correspondence between the company and Qurium that it "did find customers who were targeting this website."
~ ~
THE HAPPY CORNER
And here we go — it's the happy corner.
Some great responses to this tweet: "Scare a security person in five words or less!" ("Military grade" is my personal favorite.)
This week, @OphirHarpaz spoke with Motherboard about her first ever hack: Minesweeper. The podcast is well worth the listen. (And yes, of course there is code.)
In other cool things: If you want (or need) a sign that lights up whenever your webcam is active, here's a project for you — and the code you need.
And, the final word goes to @mzbat, for anyone who needs a professional pick-me-up.
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Lancelot. Just before this photo was taken, Lancelot "helpfully" smushed the keyboard and deleted a bunch of his human's emails. No emails means more time for chin scritches. A big thanks to Jonathan K. for the submission!

Keep sending in your cyber cats (or their friends)! Email with their name and photo here!
~ ~
SUGGESTION BOX
That's all for this edition. Feel free to leave any feedback in the suggestion box or email me at this@weekinsecurity.com. Hope you have a great week, and see you next Sunday.