this week in security — august 3 2025 edition
THIS WEEK, TL;DR
Senate votes to approve U.S. national cyber director
Nextgov: The Trump administration (finally) has its first Senate-approved cybersecurity official, Sean Cairncross, the new national cyber director, following a 59-35 vote on Saturday. Cairncross, by his own admission, doesn't have a technical background but will now oversee the office, first set up during Biden's term, as the government's director of cyber policy across all federal agencies. If the White House also gets its way, it's also on track to get its pick of CISA director passed in the Senate, now that Sen. Ron Wyden has agreed to lift the hold on Sean Plankey's nomination after the agency confirmed it would release a long-withheld report detailing the state of security in the U.S. telecoms sector. This comes at the same time that U.S. states are saying they are increasingly wary of the federal government's cuts to cyber under Trump. At least two states, Arizona and New York, said these cuts are hurting their states and their ability to withstand cyberattacks as they effectively "go it alone."
More: Nextgov | Cyberscoop | NBC News | TechCrunch | @ericjgeller
Top lawyer at NSA is fired at urging of far-right influencer
The New York Times ($): From one government department to another... things are looking pretty bleak at the NSA. The U.S. eavesdropping agency is now without its top lawyer after its chief counsel April Falcon Doss was fired, which was blamed on far-right influencer Laura Loomer. (Loomer, well known for chaining herself to the doors of Twitter's HQ, previously took credit for the earlier ousting of the agency's director and its deputy.) Doss, who is well known in cybersecurity and privacy circles, has been the agency's top lawyer since 2022. Several lawmakers sounded the alarm on Doss' firing, not least because the role of the NSA's chief lawyer is critical for signing off on surveillance and hacking operations, which the NSA now doesn't have. This is one of the most powerful spy agencies in the world and presently rudderless. This happened in the same week that the U.S. Army Secretary rescinded a job offer at the U.S. Military Academy at West Point to the former CISA director Jen Easterly, who served in the Army, at Loomer's demand, as the purge of the U.S. government's institutional cyber knowledge continues.
More: Politico | MSNBC | @pwnallthethings | Jen Easterly (LinkedIn)
SharePoint exploit now seen in ransomware attacks
Cybersecurity Dive: Security researchers at Palo Alto Networks said they are now seeing ransomware attacks as part of the mass-hacks targeting on-premise SharePoint servers, aka CVE-2025-53770. According to reports this week, close to a hundred state and local government systems were targeted in the wake of the attacks. China-backed hackers were among the first to exploit the bug in hacking campaigns, leading to a key question of how they discovered the bugs so quickly. ProPublica, which previously reported on Microsoft's use of engineers in China for national security projects, is now reporting that Microsoft's support for SharePoint is handled by another China-based engineering team — though, there's no evidence of wrongdoing. All of this comes at a time when Microsoft is trying to repair its image following security scandals in recent years, with some calling into question (with colorful headlines) its own secure-by-design initiative.
More: Reuters ($) | ProPublica | Heise.de
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.K. age checks are blocking legitimate content and rely on AI guess work
BBC News: If you thought any of this age verification calamity was dying down, think again. Ostensibly "adult" content, like news reports on Gaza and Ukraine, are getting caught up under the U.K.'s new age checks system that took effect last week. Some online services are bucking the trend and using common sense by not relying on third-parties to do government ID age checks. But it's clear these age check requirements weren't thought out and are having real knock-on effects by preventing access to legitimate content. Now we're relying on tech companies using AI to guess someone's age — I'm not kidding — and if it guesses wrong, you have to upload your ID. Australia is next on the age checks list, so let's hope they don't face the same headaches as the U.K. and others have.
Google to disclose bug timelines within one week of discovery
Project Zero: Google's elite group of zero-day bug hunters, Project Zero, said it has started publicly announcing when it has started the clock on a 90-day bug disclosure period. By disclosing that "a bug" (without sharing specific details, of course) has been found in a particular product and with a timeline for disclosure, it hopes to help others who rely on that software to be ready for patches.
ShinyHunters said to be behind Salesforce data thefts
Bleeping Computer: A series of Salesforce-related data grabs of late, including at Qantas, Allianz Life, and luxury brand LVMH, was reportedly carried out by the ShinyHunters group. Bleeping dives into the group's latest activities, which relies on voice phishing to break into these cloud-stored CRM systems, and how this activity differentiates from Scattered Spider, which launched similar attacks around this time. Solid read. (via @ransomwaresommelier)
Sex toy maker Lovense exposed user email addresses and accounts
BobDaHacker: A security researcher said they found bugs in Lovense's API that exposed user email addresses, and put accounts at risk of takeovers, prompting store retailers to pull the company's sex toys from their shelves. (I confirmed the email disclosure bug and wrote about this for TechCrunch, disclosure alert!) The company eventually fixed the bugs but not without having a legal-related temper tantrum in the process.
Authorities seize BlackSuit ransomware gang's infrastructure
Lower Saxony State Criminal Police: A little sprinkling of good news from German authorities: U.S. and European police seized the infrastructure of BlackSuit, a prolific ransomware gang (formerly Royal), which hacked over 180 victims and netted over $500 million. The seized data will now be used to help identify other individuals associated with the gang. (via @campuscodi)

Defected North Korean IT worker talks about their work
BBC News: The BBC has an interview with a North Korean IT worker, who was able to defect and tell their story. I bring up this threat on the semi-reg because of how widespread and global this issue is. Spotting this kind of activity is tricky, but one increasingly popular tactic is getting interviewers to go outside with their phone or laptop with their video on, as this makes it more difficult to deepfake someone else. Or, of course, ask your suspected North Korean interviewer to say something mean about Kim Jong Un. (It works!)
~ ~

~ ~
OTHER NEWSY NUGGETS
Scramble as Dropbox, Microsoft drop passwords: Dropbox has announced it will discontinue Dropbox Passwords, the company's password manager, at the end of October. Meanwhile: If you haven't taken action already, well, welp, as Microsoft Authenticator dropped support for passwords on August 1 and stored passwords deleted. (via The Register, Associated Press)
Privacy for thee, but not for me: Senators may soon vote on a bill that would allow lawmakers to scrub some of their information about their houses and travel from the internet. Of course there are genuine risks with having your information out there, but if only these senators could think a little outside the box and expand this provision to all of America, we'd be in a much better place. (via Rolling Stone, Tech Policy Press, @evacide)
Two-year-old PaperCut flaw under attack: CISA has added a two-year-old vulnerability (CVE-2023-2533) in printer management software PaperCut to its list of known exploited vulnerabilities, after evidence emerged that the bug is being used in active hacking campaigns. The bug allows malicious hackers to remotely run arbitrary code on an affected system. (via SecurityWeek)
More Tea spilled: The Tea app breach gets even worse. After last week's publicly exposed bucket left 72,000+ images of selfies and IDs online, a second breach exposed users' private direct messages. This app has already been considered a "privacy nightmare." Incredibly, the app remains in the top spots on Apple's app store, despite the reporting, which seems odd given how (allegedly) pro-security and privacy Apple claims to be. (via 404 Media ($), Daring Fireball)
ChatGPT convos indexed by search engines: Nothing you share with AI is ever truly private, but it's especially problematic when Google begins indexing some of your ChatGPT queries. That's exactly what happened when users hit "Share" on the AI chatbot, not realizing that this was publicly sharing the user's prompts and making them indexable by search engines. OpenAI apologized. (via Fast Company ($))
Google says it wasn't backdoored: In a stunning display of poorly executed comms, Google reluctantly and begrudgingly admitted this week, on the record, that the company has not been ordered to backdoor its encrypted services at the request of U.K. authorities, like Apple has been. Ron Wyden asked other tech giants if they had been backdoored, but Google refused to answer — even Meta flat out said it hadn't been ordered to make a backdoor. Google eventually acquiesced and confirmed it hadn't been — but maybe had they just told the lawmaker what he wanted to hear first time around, we wouldn't have wasted an entire news cycle on this. (via Washington Post ($), TechCrunch)
~ ~
THE HAPPY CORNER
Alright, that's the news done with. Let's have some fun in the happy corner. Rejoice!
First up, shout out to the excellent @selenalarson for the amazing work chatting with local seniors about cybersecurity. This is great to see because a lot of scams these days are designed to target older folks, but helping them to be aware and know what to look out for can be enormously helpful for keeping them, their friends and family cyber-safe.
Funnily enough, in somewhat tangentally related tweets:
Ever wondered what happens if you plug in a keyboard to the back of a bus seat? Maybe not actually this, but I still cracked up anyway.
TIL: Cats are not subject to corporate non-disclosure agreements. Also, TIL: you can probably hack into most companies with just a piece of sashimi.
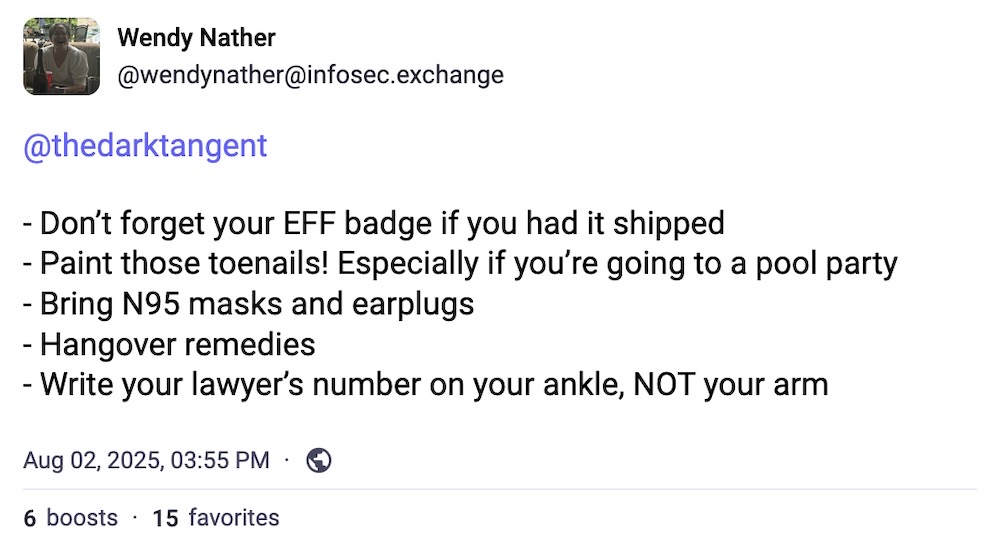
And lastly, this week... if you're heading to Las Vegas for Black Hat and Def Con, have fun! And — for the love of all that is holy — hydrate! And while we're on the subject of summer camp, here's your mini check-list from security veteran @wendynather, who always has your back.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Sage, this week's cyber cat, who... sssshhh... don't wake her, she's probably plotting her next major hack. Thanks so much to Matt B. for sending in!

Keep the cyber cats coming in! Got a cyber-cat or a non-feline friend? Send in an email with their photo and name and they will be featured in a future newsletter!
~ ~
SUGGESTION BOX
That's all for this week's bumper edition of ~this week in security~! For all those heading to Vegas, safe travels (and keep your devices safe, too). I'll be back next week with your roundup from the show's best research as told to reporters; (I won't be there this year, but if you have anything to share with me, drop me an email!)
Catch you next,
@zackwhittaker