this week in security — august 4 2024 edition
THIS WEEK, TL;DR
Ransomware gangs exploiting newly patched VMware ESXi flaw
Microsoft: Several ransomware gangs have for months exploited a now-patched flaw in VMware ESXi servers that can be used to gain full admin control of the ESXi hypervisor. The research by Microsoft shows the zero-day bug (at the time) was used to steal or encrypt data from their victims. The bug, known as CVE-2024-37085 was easily exploited by creating a new domain group named "ESX Admins," which allows any user of the group (and new ones) to become admin without authentication. Ransomware and extortion gangs (including Scattered Spider, aka "Octo Tempest") are increasingly targeting ESXi hypervisors because once encrypted, they can cause massive amounts of damage — resulting in equally massive ransom demands. In one case, Microsoft said it saw one threat group exploit the flaw to deploy ransomware on a North American engineering firm.
More: Microsoft | Cyberscoop | SecurityWeek | Bleeping Computer | @malwarejake
U.K. slaps Electoral Commission for massive hack of 40M voter details
ICO: The U.K.'s data protection watchdog responded to one of the biggest breaches (by size) in its history — some 40 million voter registration records (names and addresses) — with a flop and a fizzle. The ICO said in its report this week that the Electoral Commission failed to update its on-premise Exchange email system — even months after critical security fixes for ProxyShell were released and automatically installed — and as a result got compromised by what the then-Conservative government later blamed on China-backed hackers. According to the ICO, had the Commission "taken basic steps" to protect its systems, "it is highly likely that this data breach would not have happened." And yet no fine, just a reprimand, which is little more than a public scolding. Yes, the breach was entirely preventable. For its part, the Electoral Commission admitted it messed up.
More: BBC News | Bleeping Computer | The Guardian ($) | @GossiTheDog
Cyberattack hits blood-donation non-profit OneBlood
CNN: Rough week for the folks at OneBlood, who are operating at a "significantly reduced capacity" despite a ransomware attack. CNN reports that the blood donation nonprofit, which serves hundreds of hospitals across the southern and eastern U.S. — Alabama, Florida, and Georgia, and the Carolinas — is resorting to manual labeling and other processes. "The blood supply cannot be taken for granted," the nonprofit said. It's the latest ransomware attack to target the healthcare sector — and one that particularly hurts local communities. Ransomware carries on, but The Register looks at the down-and-out LockBit, which seems to have struggled to stay active and relevant after U.K. officials doxxed the gang's leader. That's how you handle ransomware.
More: OneBlood | Axios
Jailed cybercriminals returned to Russia in historic prisoner swap
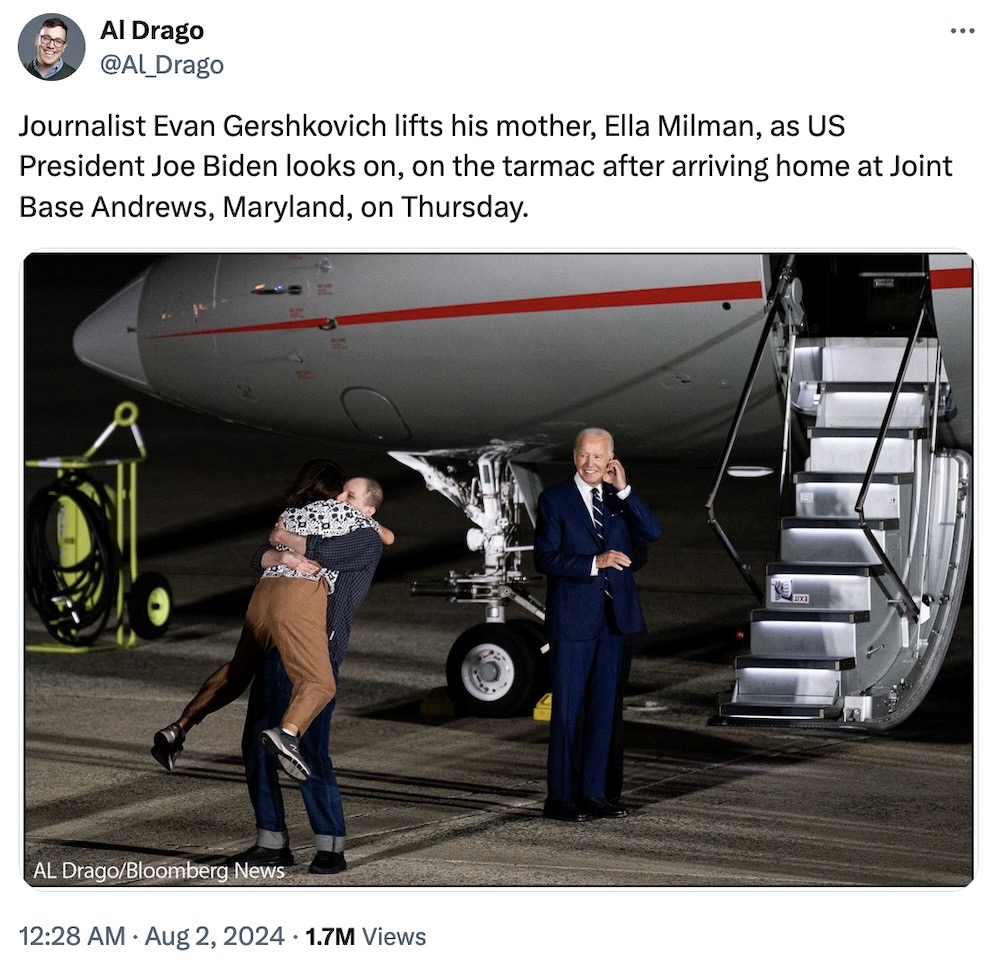
Cyberscoop: Three U.S. citizens held illegally by Russia are now home after years away from their families. A highly complex, multi-nation prisoner swap this week saw at least two Russian cybercriminals, Vladislav Klyushin and Roman Seleznev, both of whom had been convicted of financial crimes in the U.S., returned to Russia in exchange for several Western prisoners held in Russia, including WSJ reporter Evan Gershkovich. Ars Technica has a deeper dive on the two hackers' backgrounds. And it was absolutely worth it to get innocent people home. Olaf Scholz, the chancellor of Germany — which had the most to give up in this prisoner swap — said he made the decision to go ahead by "balancing the interest of the state in enforcing the sentence with the freedom and the risks to the health and, in some cases, to the lives of innocent people detained in Russia." On that note, here's that incredible photo of Gershkovich hugging his mother for the first time in more than a year.
More: KrebsonSecurity | Cyberscoop | Ars Technica | @sulliview
~ ~
THE STUFF YOU MIGHT'VE MISSED
Another DDoS briefly hobbles Azure (again)
Bloomberg ($): Cloud and tech giant Microsoft blamed a DDoS attack (see KTY1-HW8) for causing hours-long outages across its Azure cloud platform. Microsoft said the attack began on Tuesday and caused widespread outages — its second in as many weeks. Instead of absorbing the junk traffic and mitigating the incident, Microsoft's tech accidentally "amplified" the attack instead. Whoooops. Microsoft has been a touch more open about DDoS attacks targeting its cloud since its massive "nothing to see here" DDoS attack last year.
Homebrew security audit sees bugs found and fixed
Trail of Bits: Homebrew, the so-called "missing package manager for macOS," got its latest security audit performed by Trail of Bits. The result allowed Homebrew to fix some bugs that might've otherwise gone unnoticed. Homebrew said of the 25 bugs, 16 are fixed and three are in process.
Hacker gets free laundry for life
404 Media ($): Michael Orlitzky bemoaned his building's CSC Serviceworks-powered laundry machines, and sought to figure out a better solution. Turns out with a bit of wire manipulation, short circuiting the red and black wires on the coin-drop mechanism, and bingo, your free laundry awaits. Orlitzky quietly published details of the bypass on his blog last year, and will feature in a Def Con talk this coming week. CSC didn't comment, which isn't a huge surprise, because if all of this sounds somewhat familiar, you're thinking of the two university students who also figured out a way to get free laundry from CSC machines.

Bumble, Hinge bugs allowed anyone to pinpoint users' locations
TechCrunch: Researchers say they've figured out ways to extract the near-precise location data within about 2 meters from Bumble and Hinge apps by way of oracle trilateration, a technique that can be used to triangulate someone's location. Other apps, like Grindr, allowed location triangulation within 110 meters — thereabouts a city block in urban areas. The apps fixed the issues in 2023 after they were reported.
Georgia website bug briefly exposed voter data
Associated Press: Well this isn't good. A bug in a new Georgia state website briefly exposed information about a voter's date of birth, driving license number and last four of their SSN — which just so happens to be exactly what you need to cancel someone's voter registration in the state(!). The bug lasted less than an hour, but come on, people! It's utterly bizarre that voter registration data is semi-public to begin with; it's a boon to doxxing, and only seems to benefit the politicians. This is in the same week that 4.6 million records of much of the same data except relating to Illinois voters were left exposed on the internet, per Wired ($). There was no password on the exposed file storage. Extreme face-palm.
~ ~
OTHER NEWSY NUGGETS
Biden admin on cyber, as told by top cyber folks: Cyberscoop looks back at the past four years of the Biden administration's big moves on cyber — to both praise and criticism — as told by the dream team of top U.S. cyber officials that were tasked with taking on the big cyber challenges — including CISA's Jen Easterly, deputy NSA Anne Neuberger, and National Cyber Director Harry Coker. (via Cyberscoop, @timstarks)
HealthEquity hides data breach notice: If you searched for HealthEquity's public data breach notice, you might not find it, since the workplace benefits administrator hid its notice using 'noindex' web code to make it invisible to search engines. Not cool! (Disclosure: I wrote this story.) The breach affects 4.3 million people, and includes names, addresses, Social Security numbers, and more. (via HealthEquity, TechCrunch)
Millions notified of Cencora data breach: U.S. pharma giant Cencora had a data breach earlier this year, which included health diagnoses, medications and prescriptions, that it collects from working with drugmakers like Abbvie, Bayer, Pfizer, and others. But Cencora has steadfastly refused to say how many individuals it's notifying. By searching and collating data breach notices from states that require companies to disclose the specified number of individuals to be notified, we found at least 1.43 million people have been notified so far. (That's already ranking as one of the worst health data-related breaches this year.) Cencora, for its part, says it's served 18 million patients to date — if you were wondering just how bad this could get. (Disclosure [again]: I also wrote this story!) (via TechCrunch)
Bausch borked its breach: Another pharma data breach, this time it's Bausch Health, another company that got their data stolen during the Snowflake customer data thefts. @josephcox reports that Bausch knew about the theft of data — including medical DEA numbers (for prescribing controlled substances) and prescriber details — for some time, but only confirmed it after malicious hackers attempted to extort the company. (via 404 Media ($))
~ ~
THE HAPPY CORNER
At last... it's the happy corner and where all are welcome.
A rare cyber-Olympics crossover moment from this week, from which we got a brand new meme.

Moving on. It's hacker summer camp this week in Las Vegas. (I won't be at Black Hat or Def Con, alas!) Many of you will be — so have fun, and I hope you enjoy the week of talks, hacks and shenanigans. Do take care of yourselves, and hydrate!

For those who are heading to Vegas, remember you can opt out of facial recognition on domestic flights regardless of if you're a citizen. No reason to give your face print to the airlines and the government for no reason; you can't ever get it back. Opting out is easy (and allowed!), the airline just checks your passport instead.
And, your final moment of zen.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Corrie, aka supervisor over her human. Apparently, Corrie is definitely one to give good purr-formance feedback, especially if coaxed with a treat or two. Many thanks to Tindra for sending in!

Keep sending in your cyber cats! You can drop a quick email with a photo of your cyber cat (or non-feline friend!) with their name, and they will be featured in an upcoming newsletter. Updates are also very welcome, send them in!
~ ~
SUGGESTION BOX
That's all for this week, thanks so much for reading! Safe travels to everyone heading to Vegas. And for those who are stuck at home (in my case, it's been a yucky week of COVID), hope you have a quiet and peaceful week.
I'll be back next week with everything you need to know and more from the shows and beyond. In the meantime, feel free to reach out any time — cyber cats, fun things, and anything in between — I love hearing from you!
Onwards!
@zackwhittaker