this week in security — august 8 edition
THIS WEEK, TL;DR
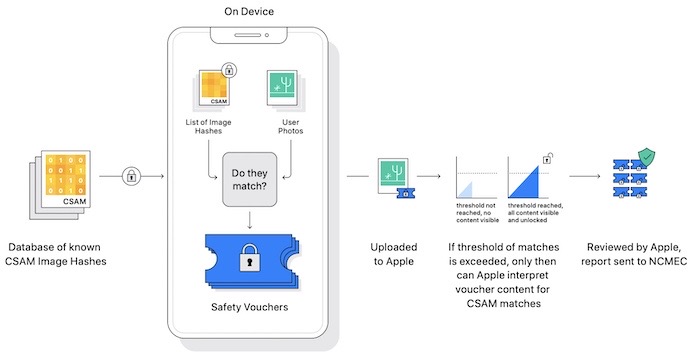
Apple confirms it will begin scanning iCloud Photos for child abuse images
TechCrunch: Apple this week announced it will later this year begin scanning iCloud Photos for child sexual abuse material (CSAM). Most tech giants already scan for illegal content in their clouds, but Apple's iCloud is encrypted — so it's figured out a way to do it on the device in a way that it claims is more privacy-minded. I wrote about how it works (disclosure!), and it begins with iOS 15 and macOS Monterey in the U.S. later this year. But the announcement — leaked a day ahead of the embargo lift by @matthew_d_green — angered a broad swath of people, because algorithms are often flawed and frequently get things wrong. So, there is a lot to unpack with this, but Wired ($) explained the arguments extremely well. @rondeibert has a good tweet thread on the concerns that this could be a backdoor to greater surveillance down the line, which Apple has rejected and said was the "screeching voice of the minority" in a leaked internal memo, no less. But given its concessions in China before, what's to say it wouldn't bend again? Worse, what's to say that nation states using powerful spyware like Pegasus couldn't abuse the system and plant incriminating materials — like has happened before?
More: Motherboard | TechCrunch | @spencerdailey | @matthew_d_green | @mattblaze tweets
Federal cybersecurity defenses not strong enough to protect American data, Senate report warns
CBS News: Federal agencies are failing on the cyber, according to a new Senate report. The audit says DHS, State, and the Social Security Administration are relying on outdated technology and ignoring security patches (if they're even available any more) — which they say could lead to security breaches. The report is a pretty damning rebuke of federal cybersecurity.
More: Cyberscoop | NBC News | @dellcam
Your Facebook account was hacked. Getting help may take weeks — or $299
NPR: This was an incredible @shannonpareil read. On Facebook, you are the product and information about you is sold to advertisers, making the company literally billions of dollars every quarter. So when people's accounts get hacked, you'd think Facebook would want to help. But it doesn't — and leaves customers stranded because of a massive backlog of reports processed by Facebook's low paid workers. Unless, that is, you shell out $299 for an Oculus, a VR headset owned by Facebook, so you can get a foot in the door to Facebook's customer support system. "The only way you can get any customer service is if you prove that you've actually purchased something from them," said one victim. This is a really good read and yet another example of why Facebook is just rotten to its core.
More: @shannonpareil | @craigsilverman
Disgruntled ransomware affiliate leaks the Conti gang’s technical manuals
The Record: An allegedly disgruntled member of the Conti ransomware-as-a-service group leaked manuals and technical guides used by Conti to train affiliates on how to hack into and navigate a victim's network before exfiltrating data and encrypting files. A ton of screenshots also contained details of IP addresses and servers that Conti used to host its Cobalt Strike command and control servers (for now), which might help some network defenders protect their systems.
More: @campuscodi tweets | @vxunderground | @gossithedog
Critical Cobalt Strike bug leaves botnet servers vulnerable to takedown
Ars Technica: Speaking of Cobalt Strike servers... researchers found a bug in Cobalt Strike, the pentesting platform used by red teamers (but also some criminals to launch attacks, boo!). The bug was found in how the Cobalt Strike server communicates with the Beacon, a small client-side tool that's implanted on the target's computer. Exploiting the bug triggers a denial-of-service condition, effectively knocking out the server's memory and forcing the operation to stop. Patches are out for legitimate customers, but will take a while before criminals get their hands on the patches, putting criminal operations running pirated copies of Cobalt Strike at risk.
More: SentinelOne
Hospitals still use pneumatic tubes — and they can be hacked
Wired ($): Pneumatic tubes might sound like an antiquated technology from yesteryear, but one model — the TransLogic PTS — is still in wide use, buried into the walls of thousands of hospitals in North America for transporting blood and lab samples from one end of the hospital to another. As you might expect, they can also be hacked. Nine vulnerabilities found by security firm Armis in the TransLogic controller could let a hacker take over a system, take it offline, access data, reroute deliveries, or otherwise sabotage the pneumatic network. Patches are now out.
More: ZDNet | Cyberscoop | @lilyhnewman
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Anne Neuberger explains why the White House didn't ban ransomware payments
Cyberscoop: By now, we know that disrupting the economics of ransomware payments is likely the best option forward for taking on ransomware groups. Some say ban paying the ransom altogether. But the National Security Council's Anne Neuberger said while she thought initially banning ransom payments was a "good approach," it turns out that a ban would drive some of those payments underground and make it harder to maintain visibility and gather intelligence. Much of what the Biden administration has in its back pocket is the threat of "action" against Russia, which gives some of these groups safe harbor.
Evidence suggests Darkside rebranded as BlackMatter after Colonial hack
Chainalysis: Speaking of which... it looks like the Darkside ransomware group has rebranded as BlackMatter. If you recall, Darkside went underground after the Colonial Pipeline ransomware attack, which it was blamed for. @chainalysis, which follows the money of ransomware groups, says its blockchain analysis confirms the rebrand. "This is part of a trend in which ransomware groups shut down & reemerge with new names, often after law enforcement actions or media scrutiny." The confirmation comes shortly after Emsisoft's CTO @fwosar said an analysis of the BlackMatter decryption tool reveals code overlaps with Darkside, adding weight to the theory.
jFrog finds malicious PyPI packages stealing credit cards and injecting code
jFrog: Software house jFrog says it's found several Python packages in the PyPI repository that contained code designed to steal data from victims, including credit cards, and inject malicious code. jFrog estimates that the packages have been downloaded more than 30,000 times, and has a detailed run-down of how the malicious code works.
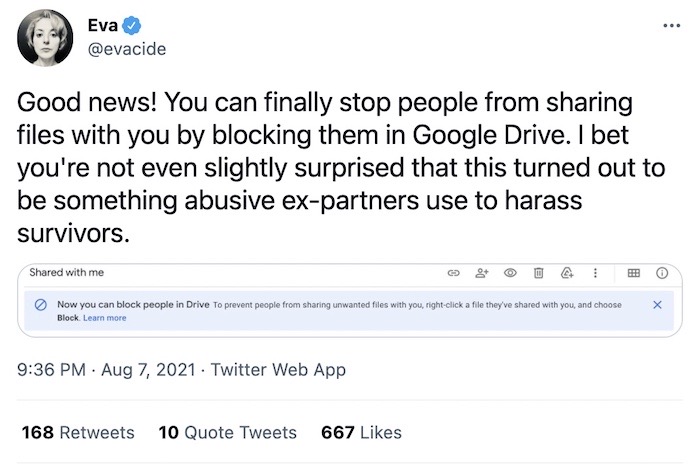
Google will let you block users from sharing unwanted files
Eva Galperin: After last week's news about Google Drive's upcoming security changes, Google will now let you block people from sharing unwanted files with you. A long-overdue feature for anyone who's been spammed or harassed as a result.
All the Pwnie Award winners in one tweet thread
Dhiraj Mishra: This year's Black Hat's Pwnie Awards are out. @RandomDhiraj has all the winners in a tweet thread. Naturally, Cellebrite got the Lamest Vendor Response for its response to @moxie's discovery of several security bugs in its phone-hacking equipment.
Researchers decide 'Hacker Summer Camp' is too risky as Covid-19 cases spike
The Record: Given the ongoing pandemic and the rise of the Delta variant, it's no surprise that a lot of folks are staying away from Vegas this year. @kansasalps looks at the fallout and who's going and who isn't. For all of the folks at Hacker Summer Camp this year — please stay safe. For those who stayed at home, few can blame you.
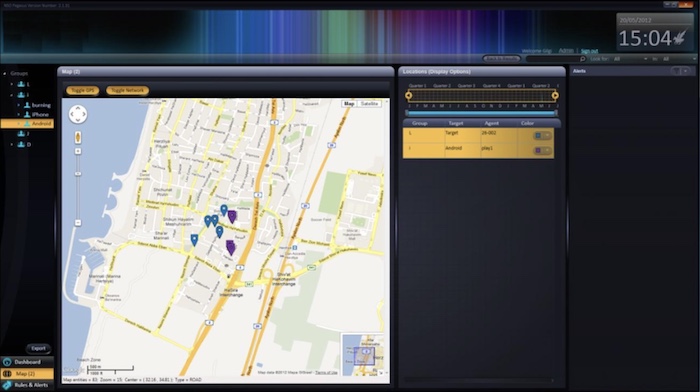
A leaked Pegasus manual shows how the spyware works
Zero Day: @kimzetter is back with another look at NSO Group's Pegasus spyware, thanks to a leaked manual slated to be from around 2016. The manual explains how Pegasus works, what it collects, and more. That said, it's been several years since, so things are likely to have changed, but this gives a really good foundational understanding of the technology. Zetter also quotes @botherder, head of Amnesty International's Security Lab, which conducted the forensic investigations for the Pegasus Project. You should also read his blog post about the mental toll of the work, and how the spyware industry grew power through a lack of regulation.
~ ~
OTHER NEWSY NUGGETS
Messaging apps have an eavesdropping problem
Google Project Zero researcher @natashenka found several flaws in a number of messaging apps — including Signal, Facebook Messenger, and Google Duo — that can allow interaction-less remote eavesdropping. The bugs are all fixed, per @lilyhnewman, but more may be lurking.
Hackers shut down system for booking COVID-19 shots in Italy's Lazio region
Hackers attacked and shut down IT systems of the company that manages COVID-19 vaccination appointments across the Lazio region around Rome, an area with a population of about 6 million people. Its systems were shut down for the time being, and warned that inoculations could be delayed. Yeah, not at all cool.
Courts order handover of breach forensic reports welcomed by consumers, feared by defendants
This is a really good read. In the past year, there have been three cases where judges have ordered companies to turn over their internal forensic reports, which contain specific details about how they were breached. In all three cases, the judges dismissed the hacked companies' arguments that the reports were legally protected. This move is particularly feared given these companies worry that these reports could be used against them. Yeah, like when there are cases of clear negligence. This is definitely one to watch.
Watch a hacker hijack a capsule hotel's lights, fans and beds
Fantastic work here by a hacker who found a number of vulnerabilities in a system used by one unnamed "capsule" hotel (which are common in Japan) that allowed him to switch on and off lights, ventilation, and even the beds that convert to a couch. The hacker, who goes by the handle Kyasupā, found the bugs after a rough night because of a loud and obnoxious neighbor in another capsule. Luckily, Kyasupā got his own back. There's also a video you're not going to want to miss.
Google fired dozens of employees for data misuse
Google fired 36 employees in 2020 for security-related issues, such as mishandling of confidential information — such as transferring it to outside parties — while others were caused by improper access to customer or employee data. Google fired dozens more across 2018 and 2019, according to a leaked document. @sheeraf and @ceciliakang reported in their new book that Facebook fired 52 employees for improperly accessing user data between 2014 and mid-2015.
Microsoft tests Super-Duper Secure Mode for Edge
What a name. "Super-Duper Secure Mode" is a new feature in Edge that will remove the Just-in-Time (JIT) compilation, used for optimizing JavaScript performance, which will help to remove the overall attack surface of the browser. Tests show that there's very little change in performance as a result. The feature is still in experimental mode, but Edge preview testers can switch on the feature here.
~ ~
THE HAPPY CORNER
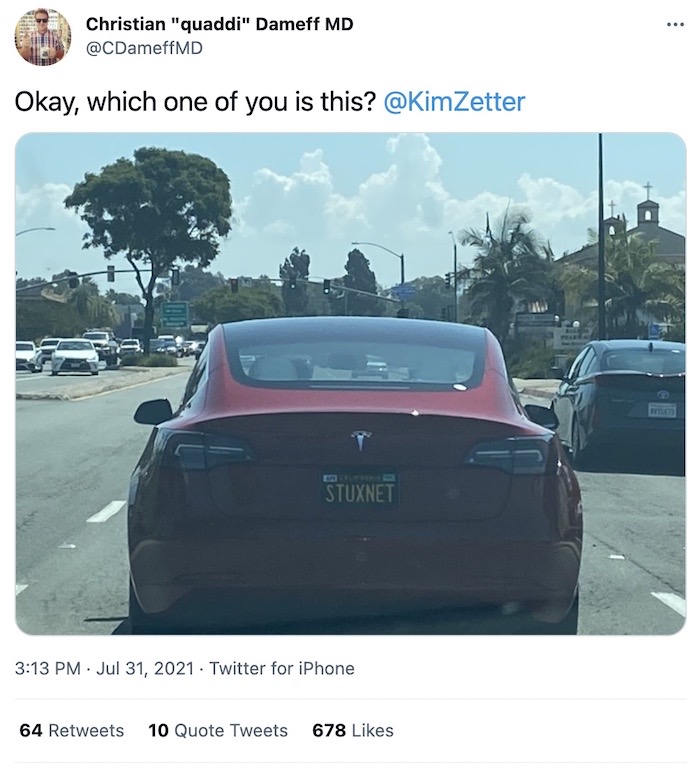
Right, onto the good stuff. First, nice license plate, whoever you are in San Diego. Great find by @CDameffMD.
Shout out to the Def Con crew for putting out complimentary menstrual products in the bathrooms during the event (as spotted by @0xNBE1). Credit where it's due. We should see this more often!
And, this short and snappy tweet thread is a great example of how companies should respond to phishers. It took just six minutes for Namecheap to pull down one infringing site. (Granted, no company is perfect, but Namecheap has really stepped up its game.)
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
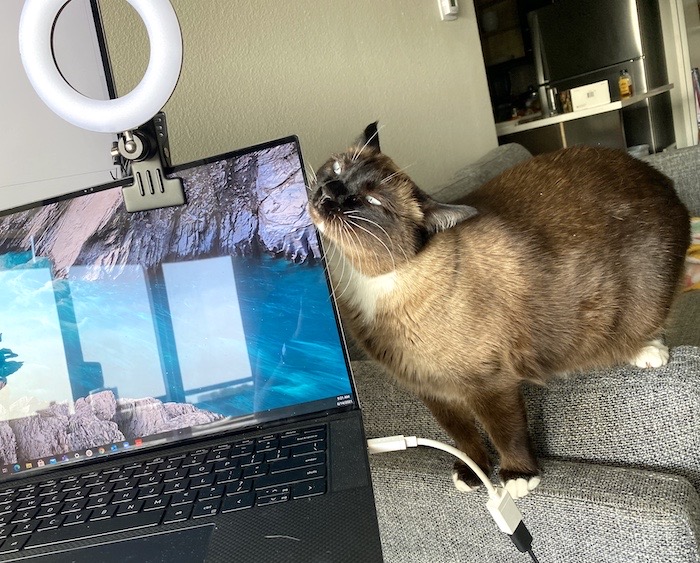
This week's cyber cat is Eleanor, who as you can see is attempting to brute force the closure of her human's laptop in the hope that it will result in an extortion payment of treats. Who could possibly resist? A big thanks to @skeletorskelton for the submission.
Send in your cyber cats (or their friends)! You can email them in (with their name and photo) here!
~ ~
SUGGESTION BOX
What a busy one. Phew. Many thanks for reading! As always, feel free to drop any feedback in the the suggestion box or email me at this@weekinsecurity.com. Take care, folks, and be well.