this week in security — december 1 edition
THIS WEEK, TL;DR
Utilities targeted in cyberattacks have been identified
Wall Street Journal ($): This rather under-appreciated story of the week revealed that the FBI was investigating cyberattacks against smaller energy and utility targets dating back to August. The attacks may still be ongoing, the report said. These smaller utilities are at dams, locks, and other smaller but important infrastructure. The attacks tried to trick victim organizations into opening a malware-laden email, which released remote control malware on the computers. Several utilities across Washington, Michigan, Maine and California were identified.
More: @selenalarson | @chrisrohlf | @tomkozlik
Islamic State propaganda machine shut down
BBC News: Europol has shut down a massive propaganda effort by the so-called Islamic State on messaging app Telegram. Close to 2,100 accounts and bots were purged from the platform on November 22 and almost 3,000 the next day. The effort was part of a wider coordinated effort to reduce the amount of terrorist material on a number of sites and platforms, including Google, Instagram, and Twitter. BBC's Monitoring service said it saw a slight resurgence but most of the groups and content had disappeared.
More: Europol
How China targets Uighurs 'one by one' for using a mobile app
ICIJ: By now, the atrocities against the Uighur Muslim population in Xinjiang cannot be ignored. But how did China detain so many people in such a (relatively) short amount of time? An unprecedented leak of classified Chinese government documents reveal that Beijing targeted users of the Zapya app. It's not known how Beijing uses the app to target individuals, but police often use the presence of an app to detain people. And it's not confined to the mainland. "Uighurs inside and outside China now live with the knowledge that their communications are constantly monitored by the authorities," writes the Consortium. Truly harrowing stuff.
More: ICIJ 'China Cables' | @ICIJorg | @mx_boenke
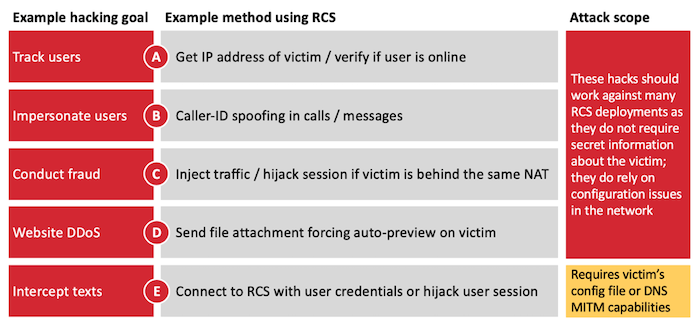
Telcos are deploying RCS. It's just as flawed as SMS
Motherboard: SMS is horribly insecure, so carriers want to replace it with Rich Communication Services (RCS), a new messaging protocol largely used on Android. But researchers say that RCS flaws expose users to text and call interception, phone calls spoofing, and leaking location data — making it just as bad as SMS security. The research was carried out by SRLabs. At least 100 cell carriers are already affected, including the big four in the United States.
More: SRLabs | @josephfcox
It’s way too easy to get a .gov domain name
Krebs on Security: Turns out it's remarkably easy to obtain a .gov domain name, even though they're meant to be for federal, state and local government institutions. It's a wild ride of a story, with potentially catastrophic consequences: while his source accepts that their actions may have constituted wire fraud, it was all to prove that obtaining a .gov domain was not as difficult as it should have been. Just think how valuable a .gov domain would be in the hands of cybercriminals or state-backed actors.
More: Gizmodo | @zackwhittaker
DHS plans to force agencies to set up vulnerability disclosure policies
Cyberscoop: Long overdue, but a highly welcome move. Homeland Security plans to force federal agencies to set up their own vulnerability disclosure policies, per a draft order published on Wednesday. It's hoped the move will help set up consistent rules across government for reporting security vulnerabilities while giving researchers legal protections. In a tweet, @k8em0 praised the effort, noting that the vulnerabilities disclosed cannot be used for offensive purposes.
More: Schneier on Security | @konklone tweets
U.K. authorities take down Imminent Methods malware site
BBC News: Britain's National Crime Agency, with help from international partners, has taken down a site run by Imminent Methods, where more than 14,500 people had bought and downloaded spying tools. The malware, known as Imrat, let anyone who bought it — for a measly $25 — to infect devices, letting them get access to webcams, data, and more. The remote-access trojan (RAT) was used "to commit serious criminality" including "fraud, theft and voyeurism."
More: Imminent Methods [seized] | Bleeping Computer
~ ~
THE STUFF YOU MIGHT'VE MISSED
Banning strong encryption makes you less safe from criminals
The Center for Internet and Society: @Riana_Crypto released a full-blown assault on the recently renewed push to ban strong encryption following reports that have seen governments more eager than ever to legislate in under the guise of protecting children and preventing terrorism. It's a great read for anyone who wants to hear the sensible, logical argument why banning strong encryption will only make things worse. "The cat’s out of the bag. The genie is out of the bottle. The horse has fled the barn. Whatever metaphor you pick, here’s the truth: Strong encryption is here to stay, and making it illegal won’t make it go away," wrote Pfefferkorn.
California's DMV makes $50M a year selling drivers' personal data
Motherboard: A document obtained by Motherboard reveals California's drivers' license authority makes $50 million a year by selling personal and private information on drivers to third-parties, including private investigators. That's a huge amount of information that you can't even opt-out of. "The DMV takes its obligation to protect personal information very seriously," the statement said, which is entirely nonsense if you read Motherboard's reporting.
Your cell carrier is the biggest location guzzler
USA Today: A refreshingly well-done story from a mainstream outlet: yes, Apple and Google let you control your phone's location better than ever before, but it's not a panacea. All behind the scenes, your phone is pinging your location data back to your cell carriers — and we all know they've been selling that location data to the highest bidder for years. AT&T stores the data for five years, compared to T-Mobile in second place, which stores it for two.
Amazon's Ring planned neighborhood 'watch lists' built on facial recognition
The Intercept: Documents show that Amazon's Ring doorbell cameras were to be used to create neighborhood "watch lists" where users would be alerted if someone was deemed suspicious was detected within camera-shot of the doorbell. BuzzFeed reports that Ring doesn't offer in-house facial recognition yet, but that police are keen to add the technology on their own.
~ ~
~ ~
OTHER NEWSY NUGGETS
Google has warned 12,000 individuals about state-backed hacks
Google says it's warned 12,000 people in just three months between July and September who it suspects were targeted by state-backed attacks. That's roughly consistent with existing data, it said. Google's Threat Analysis Group (TAG) monitors close to 270 threat groups from dozens of countries. The revelation was published in a blog post this week,
Alberta judge opens the door for 'stingray' critique
Stingrays, or cell site simulators, are used by law enforcement to track phones and intercept calls and texts, but the technology is shrouded in secrecy — to the point where prosecutors have dropped cases rather than disclose how the technology works. Now a court in Canada is allowing the defense counsel to challenge the use of the technology, potentially allowing for the greatest critique of their use in years.
The fall and rise of a spyware empire
The new owners of fallen hacking team, the aptly named Hacking Team, wants to rebuild the former empire. MIT Technology Review ($) talks to Paolo Lezzi, who bought the company, and discusses its plans to become a surveillance powerhouse once more. It's a good, but uncomfortable read for anyone who values human rights but knows that these kinds of technologies are in use by democracies and despots alike. @howelloneill also has a good tweet-thread on the story.
Louisiana's ransomware disaster is far from over
The southern state is still reeling from a massive ransomware attack that crippled some of its core services, including its Office of Motor Vehicles, Department of Health, and Public Safety, which are still trying to get back on their feet. It's believed TrickBot is to blame. Ars looks at the challenges that the state still has to overcome.
~ ~
THE HAPPY CORNER
Love it or loathe it, DNS-over-HTTPS (DoH) is here to stay. The DNS encryption technology makes it more difficult for internet providers and anyone else on the network to snoop on your internet traffic. ZDNet has a run-through of how to enable DoH across your browsers.
@nicoleperlroth has a personal story about the time she was the middle-seat on a plane to San Francisco. It turns out she was sandwiched between the two founders of what was then a tiny startup called Crowdstrike. It's a long but fascinating tweet thread talking about conspiracy nuts who think the DNC server is in Ukraine but... actually is in the DNC's basement (below).

Meanwhile, @hexadecim8 found some extremely trashy (sorry!) hacker fan-fiction and wow, it is something. If you need a laugh, it's guaranteed.
And finally, have you ever seen an dialing combination lock spinner? Now you have. In case you are wondering, its average safe opening time is about six hours.
If you want to nominate some good news from the week, feel free to reach out.
~ ~
THIS WEEK'S CYBER CAT
This week's cybercat is Bamboo. He likes to hang around while his human works at the computer. Bamboo is also a big fan of laying on the keyboard. That's a denial-of-service condition! A big thanks to @raulmillan for the submission! (You may need to enable images in this email.)

Please send in your cybercats. Right now we have zero cybercats in the bank. It's a drought! You can send them here. They will always be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this week! A big thanks to everyone who reads and supports this newsletter. As always, the suggestion box is open for feedback. Have a great week, and see you next Sunday.