this week in security — december 1 2024 edition
THIS WEEK, TL;DR
U.S. and U.K grocery stores hit by outages after supply chain ransomware attack
CNN: Happy Thanksgiving to all those who celebrated — except to the miscreants causing holiday chaos at grocery stores and retail chains around the world, thanks to a ransomware attack on supply chain company Blue Yonder. The ransomware attack — not claimed by anyone yet — took out the company's private cloud (its public cloud is unscathed), apparently wiping out critical systems along the way. Starbucks baristas couldn't log hours or get paid, per WSJ ($), some Stop & Shop shelves were left empty ahead of Thanksgiving, and U.K. grocery giants Sainsbury's and Morrisons faced operational hits. Meanwhile, crickets from Blue Yonder since November 24... except to say, "we do not have a timeline for restoration." Not great.
More: Blue Yonder | TechCrunch | NBC News | Cyberscoop | @snlyngaas
Third Snowflake hacker may be a U.S. soldier
Krebs on Security: Absolute mind-bending levels of reporting by Brian Krebs here linking the Snowflake customer breaches earlier this year to a third hacker — and the hacker might well be a U.S. soldier. Prosecutors arrested two hackers allegedly behind the Snowflake breaches, causing huge data spills at AT&T, Ticketmaster, and others. The Canadian newspaper The Record dug into the arrests of one of the accused hackers, Connor Moucka, and how he was caught. It was in large part because he threatened a badass security researcher, who shredded the hacker's opsec to pieces and tracked him down online. FAFO.
More: The Record | @evacide

T-Mobile says it spotted hackers before any sensitive data was stolen
Bloomberg ($): T-Mobile went public with an unusually candid statement: Yes, it had been hacked, as the WSJ ($) had reported (though, it wouldn't explicitly say it) but that no sensitive customer data was taken in the intrusion. Bloomberg got the interview with T-Mobile's CSO, who said the hackers resembled the Chinese hacking group Salt Typhoon (the hackers widely targeting telcos and internet firms) and that the telco spotted the hackers running commands on their routers. So, no "sensitive" data, huh? I asked, and a spokesperson said no contents or metadata of calls, texts or voicemails were taken, all of which it considers "sensitive," thanks in part because of the company's extensive logging. Maybe, just maybe, T-Mobile secured its systems just well enough after the eighth cyberattack in as many years to have avoided, for the most part, a ninth.
More: T-Mobile | Bleeping Computer | Geekwire | @gregotto
~ ~
THE STUFF YOU MIGHT'VE MISSED
Russian authorities allegedly arrest LockBit hacker
Oleg Shakirov: Russian ransomware actors have, for the longest time, gotten away with it in large part because the Russian state doesn't get involved. Until it does. Maybe that's what happened to one particular accused LockBit hacker, aka Mikhail Matveev, who's on the FBI's most wanted list for hacking, well, a lot. Russian media outlet RIA reports Matveev will be tried where he lives in the Russian enclave of Kaliningrad.
7-Zip fixes RCE bug that triggers when opening malicious ZIP
Zero Day Initiative: There's a pretty gnarly bug in file archiving software 7-Zip that can allow remote attackers to remotely run malware on an affected device by opening a malicious ZIP or archive file. Trustwave has a brief explainer. If you haven't patched already, patch today.
Wildlife monitoring tech used to intimidate and spy on women
Cambridge University: Remote controlled cameras and microphones used for conservation science to monitor wildlife are also being misused by local government officials in India, according to Cambridge University researchers, to keep watch on women without their consent. If you've developed tech that collects data, this is a reminder that it can — and will be abused. The paper is online as a PDF.
~ ~
OTHER NEWSY NUGGETS
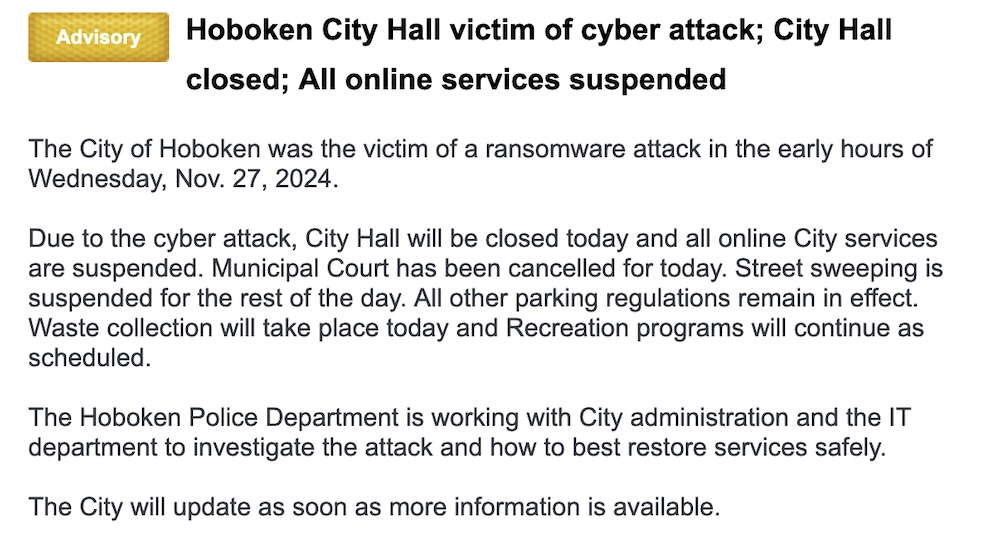
Hoboken? Hobroken, amiright: The New Jersey city of Hoboken was forced to shut down government offices this week following an as-yet-unclaimed ransomware attack. All city hall online services, municipal court, and street sweeping were cancelled as a result. Hoboken — just over the river from New York City — has more than 60,000 residents and is a major regional transit hub. (via The Hoboken Girl)
FTC slaps "AI-powered security scanner" company: Heavy quotes here for a reason, as the FTC says Evolv, a company that claims its AI-powered scanners can detect weapons while ignoring harmless items, will "be banned from making unsupported claims about its products’ ability to detect weapons by using artificial intelligence." Say no more! Although, one thing: research site IPVM and BBC News have been on Evolv for years. Behind many regulatory actions are the journalists whose work uncovered the wrongdoing to begin with. (via FTC)
Investor, recruiter, North Korean IT worker: At Cyberwarcon last week, a key theme was the ongoing threat from North Korea, including IT workers, labeled a "triple threat" for their ability to have already gained employment at "hundreds" of organizations to earn money for the regime, as well as stealing data and extorting companies not to make that data public — all for the central goal of furthering its nuke program. North Korean spies have impersonated a VC, recruiters, and more. I wrote about the talks for TechCrunch (disclosure alert!). Plus: bonus laptop stickers.
~ ~

~ ~
THE HAPPY CORNER
Welcome back to the happy corner; and a quieter than usual one this week for the short holiday week in the United States. And with Christmas coming up shortly, it's no wonder that some kids will do their best to stay off Santa's naughty list. Here's a blast from the past (and bonus Little Bobby Tables, which always makes me laugh).
![Santa Claus post on Mastodon: "A valiant effort has been made by Little Tim this year, who for some reason has decided to change his name to Tim'); INSERT INTO [NiceList] SELECT * FROM [NaughtyList];-- HO HO HO! Nice try Tim. I don't use #SQL, I use several dozen interconnected #Excel spreadsheets, like a professional."](https://this.weekinsecurity.com/content/images/scraped_images/3234b1fa-1472-b741-272c-5bd042dfb9ad.jpeg)
Meanwhile, as someone who's both a British and American computer, I additionally appreciate this reminder about session cookies. Fact check: spot on, bruv.

Laugh, yes, but please don't use "beefstew" as an actual password.
And, last but absolutely not least, while you're at home for the holidays. Routers are little thought-about, easily forgotten, seldom updated and often hacked. Security starts at home!
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber-cat dog is Tallie, who is working towards becoming a therapy dog and can be seen here brushing up on her skills to achieve CGC (Canine Good Citizen) certification. As a pup who strongly recommends that everyone uses MFA (according to her human), Tallie is already a Certified Cyber-cat Dog with top-marks in my books. Thanks so much to @wendyck for sending in!

Send in your cyber cats! (or a non-feline friend). You can email them in at any time with a photo, including their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
A shorter, quieter newsletter for Thanksgiving week. As a programming note, I'll be AFK next week, but will be back in a fortnight with your usual drop of cyber news.
In the meantime, if you see anything for the newsletter that you think would be good to include, please get in touch! If you haven't sent in a cyber-cat (or a recent update), I'd love to hear from you — or from them, of course. Tell your cat, "pssp pss pssp pssp," they'll know what it means.
Back in a couple,
@zackwhittaker