this week in security — december 10 edition
THIS WEEK, TL;DR
Governments spying on Apple, Google users through push notifications
Reuters ($): Unidentified governments are snooping on smartphone users by way of their push notifications, according to Sen. Ron Wyden in a letter to the DOJ, calling on the U.S. attorney general to lift the gag provisions that hindered public discussions of this widespread surveillance. Thanks to Wyden's letter, Apple said that as a result now it can publicly disclose that it received subpoenas demanding this data. It's because many (though not all) push notifications are routed through Apple and Google servers, making the contents (and other hidden metadata) obtainable by legal process. Some apps already use their own push notification systems or end-to-end encrypt their push notifications, and therefore aren't affected. Google, meanwhile, has said suspiciously little about the practice, though apparently Google at least requires a court order before it turns over data (which isn't a good look for Apple). According to Wyden, several governments are employing this surveillance technique. 404 Media ($) and TechCrunch found examples of subpoenas used to get someone's notifications.
More: DocumentCloud | TechCrunch | Washington Post ($)
Binance crackdown seen as 'unprecedented' bonanza for crypto surveillance
Wired ($): Binance, one of the world's biggest cryptocurrency exchanges, is under extreme DOJ scrutiny for its weak money-laundering laws that allowed hackers and cybercriminals to use Binance for illegal purposes. Now, as part of the settlement deal, U.S. crypto cops will have access to pretty much the entire company's database of transactions and suspicious activity reports (SARs) to scour for illegal activity. One former SEC attorney called the move a "24/7, 365-days-a-year financial colonoscopy," allowing U.S. authorities to hone-in on the "very small, small group of users that use crypto for illicit purposes," per Binance's chief compliance officer.
More: Wall Street Journal ($) | @a_greenberg
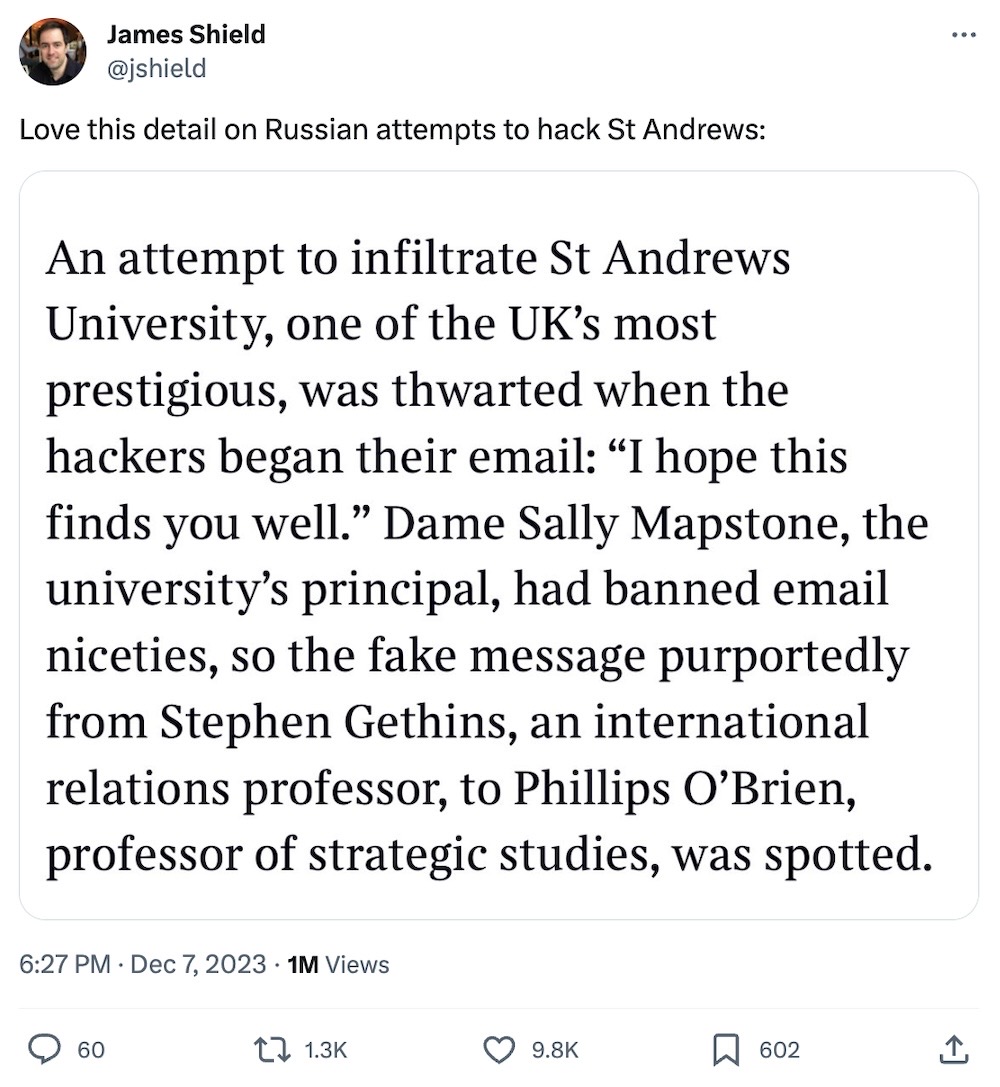
Russia accused of years-long cyberattacks on U.K. and U.S.
BBC News: Russian state-backed hackers have been targeting British politicians and others for years, and now the U.K. is calling them out on it. The hackers — publicly known as the Callisto Group (aka Seaborgium or Coldriver) — stole emails, and targeted journalists and created spoof accounts online. It's not believed to have successfully interfered with the democratic process — not that there is much there, these days — but has "acquired a vast amount of data" used for undermining Western governments at large during hack-and-leak operations. The hackers are linked to the FSB, one of Russia's spy agencies. Several U.S. government departments were also snooped on as part of the espionage campaign. And they almost got away with it — if it wasn't in part for one U.K. university principal outright banning email pleasantries years earlier, which is apparently exactly how one of the hackers' attempts got spotted.
More: Justice Department | U.S. NCSC | Washington Post ($) | @juanandres_gs
~ ~
THE STUFF YOU MIGHT'VE MISSED
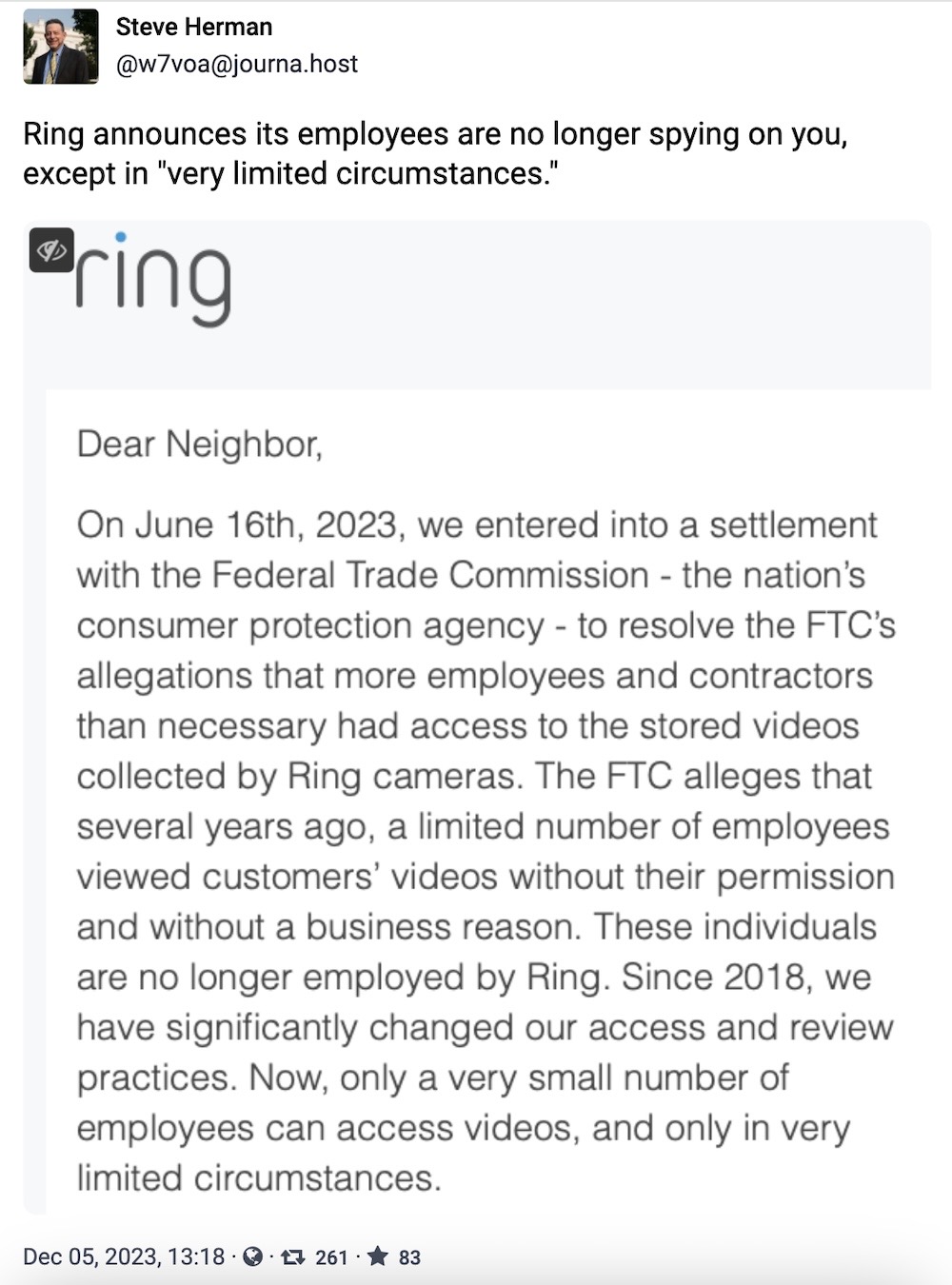
Ring will only spy on you in "limited circumstances"
Steve Herman: In case you missed it, Amazon-owned surveillance company Ring settled with the FTC earlier this year over allegations that staff and contractors had broad and unrestricted access to customers' videos for years. Ring was told to pay $5.8 million to settle the charges, which included allegations that a Ring staffer improperly accessed sensitive customer videos of women — which is exactly what happens when companies don't encrypt their customers' data, even from their own employees. If you get a message this week from Ring, don't be surprised. But do note that Ring employees can still spy on your videos, but "only in very limited circumstances." Heavy-eye-wink.gif.
Bugs in fleet management software 'ignored by vendor
Cyberscoop: Researchers say a major flaw in a fleet management software (think: remotely managing and tracking your vehicles) can allow hackers to "manipulate a fleet of vehicles at once," such as shutting them down, despite having months of warnings to fix the flaws. The bug impacts the Syrus4 IoT gateway, made by Digital Communications Technologies (DCT), which can be exploited using just an IP address and a few lines of Python, to obtain live locations, detailed engine diagnostics, speakers, airbags, and more. The bug is tracked as CVE-2023-6248.
Close to two-dozen security bugs found in widely used IoT and OT routers
Forescout: Speaking of vulnerable IoT devices... Forescout has new research exploring some 21 new vulnerabilities in Sierra Wireless cellular routers and other open source components. Some 86,000 of these routers, used in national health systems, retail, vehicle tracking(!) and waste management, are vulnerable — with less than 10% of affected routers already patched against known vulnerabilities. Some 90% cannot be patched anymore, the researchers say. Welp.
Reuters takes down blockbuster hacker-for-hire story after Indian court order
404 Media ($): Reuters says it has taken down its blockbuster investigation into an India-based hacking-for-hire firm, Appin, after receiving a court order on Monday from a district court in New Delhi. Reuters says it "stands by its reporting and plans to appeal the decision," but in order to take it down, Reuters may have faced some serious risk or threats to its reporters on the ground in India. Reuters hasn't commented on the incident. The Modi government has chipped away (in some cases with a sledgehammer) at press freedoms in recent years, often because of thin-skinned government officials who can't handle criticism. The Indian government really doesn't want you to read this archived copy of the Reuters story.
Ex-Uber CSO on why he 'had to get over' shock of data breach conviction
TechCrunch: My esteemed colleague @carlypage chatted with ex-Uber chief security officer Joe Sullivan at Black Hat Europe in London this week about his recent conviction of failing to report a huge data breach to the FTC as required by law. Sullivan described his shock as he was convicted: “We thought we were going to win the trial," he said. The first-of-its-kind verdict hit Sullivan hard, despite having letters from 50 CISOs in support of his case, which drew mixed opinions. This interview is fascinating. Sullivan says he is no longer bitter, and is instead looking ahead at how to fix the "broken" cybersecurity industry.
~ ~
OTHER NEWSY NUGGETS
New Relic says stolen creds allowed staging hack: Tech infrastructure company New Relic said its internal staging environment was accessed by hackers who obtained an employee's stolen credentials. New Relic, which hosts information about how its customers use its service (including logs), said no telemetry or application data sent by customers was hosted on the compromised system. Some customers were notified that some data was accessed, though it's not clear how many customers were ultimately affected. (via New Relic, SecurityWeek)
Firmware attack on boot-up affects most PCs: Hundreds of Windows and Linux computer models from virtually every hardware maker are at risk of hacks that allow malicious firmware to execute during boot-up. These cyberattacks are nearly impossible to detect or remove and can be exploited with "relative ease." The bugs, dubbed LogoFAIL, are made up of two-dozen newly discovered flaws that have lurked for decades, but can be exploited by injecting malicious code into the manufacturers' logos during the boot process. With a nearly identical logo replacement, it's "game over for platform security," said the Binarly researchers. (via Ars Technica)
U.S. misses own incident response requirements deadline: U.S. federal agencies have made some progress in preparing to respond to cybersecurity incidents, but the U.S. government's watchdog, the GAO, says 20 federal agencies still haven't reached the so-called "tier three" advanced level for cyber event logging. That includes the Departments of Commerce, State, and Justice. A 2021 executive order mandated federal agencies beef up their logging to help identify and remediate cyber threats, but the remaining majority of agencies cited things like a lack of staff for lagging behind the deadline. (via FedScoop, GAO)
'R' is for ransom-every-where: K-12 schools in Maine, Indiana and Georgia were battling ransomware attacks this week that caused outages and the leaking of sensitive data, continuing an ongoing trend of hackers targeting critical sectors like education. The oddly upbeat school superintendent of the Henry County Schools district, which includes some 44,000 students, said student and employee systems weren't breached (the usual caveats apply: yet, and that they know of), but that other historical data was stolen. BlackSuit, the ransomware gang that rebranded from Royal (likely to avoid sanctions), claimed responsibility for the cyberattack. There've been at least 246 known ransomware attacks on K-12 schools this year, per @uuallan, up from 147 known incidents in August alone. Not good. (via The Record)
~ ~
THE HAPPY CORNER
Ding, dong! It's the good-news gong.
QR codes are all the rage, thanks to contactless everything during the pandemic. But ever wondered how QR codes are actually made?

Moving on: Meta (aka Facebook) said it's begun rolling out end-to-end encryption for one-to-one messages and voice calls across Facebook and Messenger. Meta has been promising to do this for years, with governments urging Facebook to pull back — as it would make it more difficult to access encrypted messages (yeah, that's the point). Better late than never.
This subway sign had incredible foreshadowing.

A major congratulations to @marcia, the internet's favorite digital rights lawyer, for completing her masters in creative writing (with distinction!) from the University of Cambridge. What an amazing accomplishment, and incredibly well deserved! 🎉 🥳
And finally, this closing thought of the week.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Sooty, who is helping with incoming calls while their human works from home. There's nobody I would want more to answer my call for help. You're doing great work, Sooty. Many thanks to Chris H. for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
Aaaaand I'm outta here, that's it for this week's edition. Thanks for reading! Please do get in touch by email if you want to drop by with any feedback or comments.
I'll be back next Sunday, catch you then? In the meantime, I hope you have a wonderful week.
Have a good one,
@zackwhittaker