this week in security — december 15 2024 edition
THIS WEEK, TL;DR
Zero-day in Cleo Software, used across supply chains, actively exploited
Bleeping Computer: There's a new zero-day in town, and — you guessed it — it's under active attack. Security firm Huntress this week revealed that the pre-auth bug (read: no passwords required) in the widely used Cleo Software, which Cleo fixed in October, wasn't so fixed after all and hackers were still exploiting the bug, aka CVE-2024-50623, to steal data from its file transfer tools. Yes, it's another round of "mass-hacking file transfer software"-ageddon. Huntress and Rapid7 suggested pulling affected servers from the internet until the bug can be resolved. It looks like ransomware actors may be behind this latest round of attacks, just as it was with Accellion and MOVEit, which were similarly targeted because these file transfer tools store vast amounts of sensitive company-stored data. Hundreds of exposed systems are online, according to recent internet scans, given that Cleo is used by some major companies, including biotech and logistics firms.
More: Cleo Software | Dark Reading | The Record | BankInfoSecurity | @cisakevtracker | @gossithedog thread
U.S. says China hacked calls of 'very senior' political figures
Reuters ($): Let's check in with what's happening with Salt Typhoon, the China-backed hacking group targeting telcos and internet firms. Top White House cyber official Anne Neuberger said the group targeted and recorded phone calls of "very senior" U.S. political figures. We know that includes both Trump and Biden/Harris camps. That's on top of a huge amount of phone metadata taken from the Washington DC area. But it's looking like the operation may have been more focused and targeted on senior political figures — at least that's the latest running theory. There was a classified briefing on Capitol Hill this week, and only 67 House lawmakers (out of 435!) turned up to hear the government's classified assessment of the China-backed espionage campaign, suggesting they think the whole thing is "meh," (even if the rest of us are alarmed a.f.) Well, at least some are trying to do something about it, such as announcing a new bill aimed at mandating telcos to implement security requirements to defend against these kinds of foreign attacks.
More: Sen. Ron Wyden | TechCrunch | Politico
DOJ indicts 14 North Korean IT workers that earned $88 million
The Record: The Justice Dept. is throwing the book at 14 North Koreans who prosecutors accused of stealing identities of U.S. citizens to illegally obtain employment as part of an ongoing scam to earn money and steal intellectual property to aid the regime's nuclear weapons program. All because North Korea just loves nukes. It's a reminder that companies should do more to defend against rogue or fake workers, because it's not just money they want, but corporate secrets as well. The DOJ will have to bide its time, as the North Koreans are a little far from their law enforcement's reach. Some are as far as China and Russia, and not just Pyongyang.
More: Justice Dept. | CNBC | BBC News
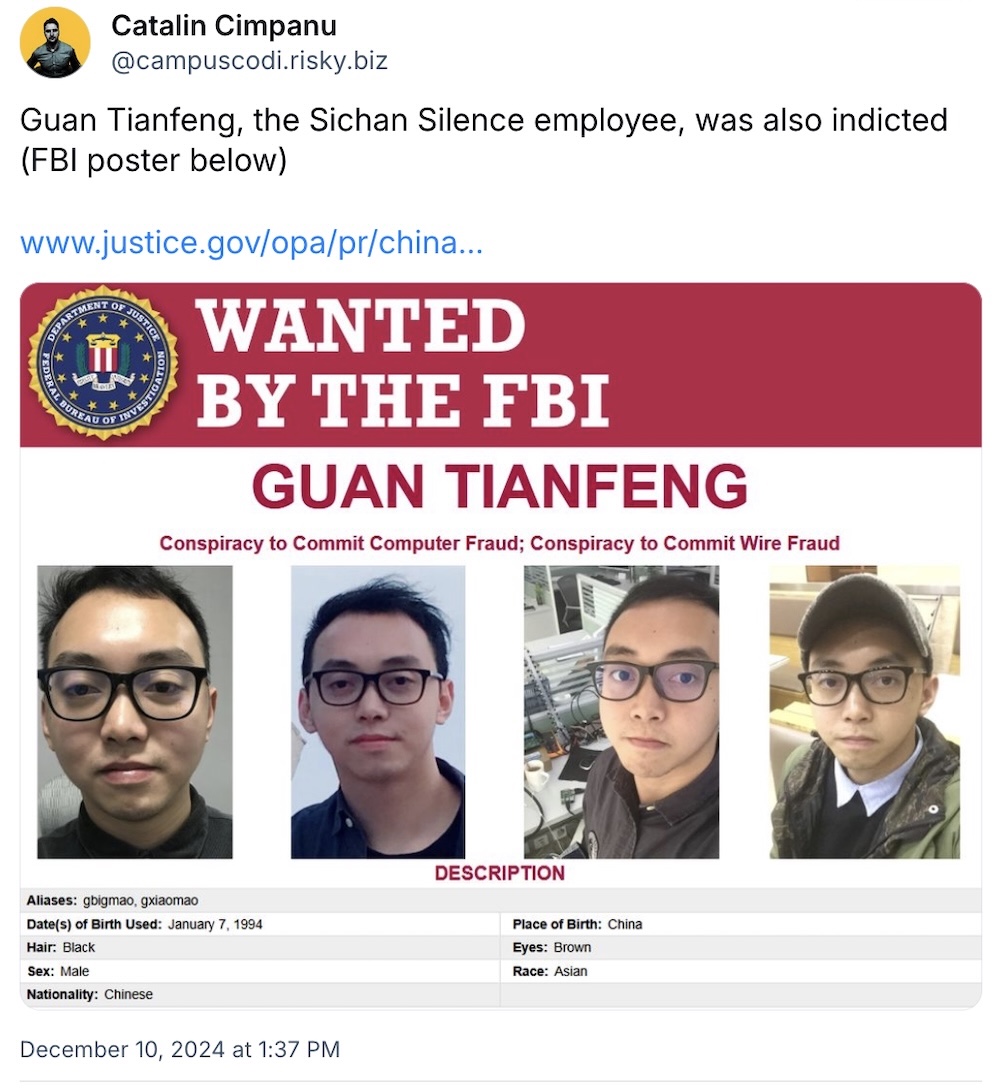
U.S. takes action against Chinese group mass-hacking firewalls
U.S. State Department: A double-whammy from the U.S. feds, after the government took multi-pronged action (indictments! sanctions!) against Sichuan Silence and one of its employees, Guan Tianfeng (now wanted by the FBI) for allegedly breaking into around 81,000 Sophos firewalls around the world. Sophos dropped details of the campaign. Some 23,000 or so firewalls were located in the U.S. — some were protecting critical infrastructure (hence why the feds are involved). The compromises were allegedly for stealing company data — since firewalls are network-edge devices that can be exploited to break into full networks. The feds are rewarding up to $10 million for information about Tianfeng or Sichuan Silence. Another reminder of the close links between some Chinese private entities and Chinese-backed cyberattacks. (Additional reading, see: Flax Typhoon).
More: Justice Dept. | U.S. Treasury | Cyberscoop | @campuscodi
~ ~
THE STUFF YOU MIGHT'VE MISSED
How much do I need to change my face to avoid facial recognition?
Gizmodo: No face swaps (or removals) necessary, and while you might want to invest in a mask and a scarf (it is the winter across the northern hemisphere), your best bet for the most part is to avoid firms, stores and services that rely on facial recognition. Many of the experts who were asked what can be done to avoid facial recognition, the answer was "it depends." But avoiding places where it's employed to begin with is the most effective, if not arduous method.
Yahoo's Paranoids loses 25% of staff this year
TechCrunch: Yahoo has laid off around 25% of its cybersecurity team, known as the Paranoids, over the past year, according to multiple sources. That's around 40-50 people out of 200 employees laid off or lost through attrition since the start of 2024. The company's red team was eliminated as part of the layoffs, we've learned. (Double disclosure alert: Yahoo is my employer, and I co-wrote this story.)
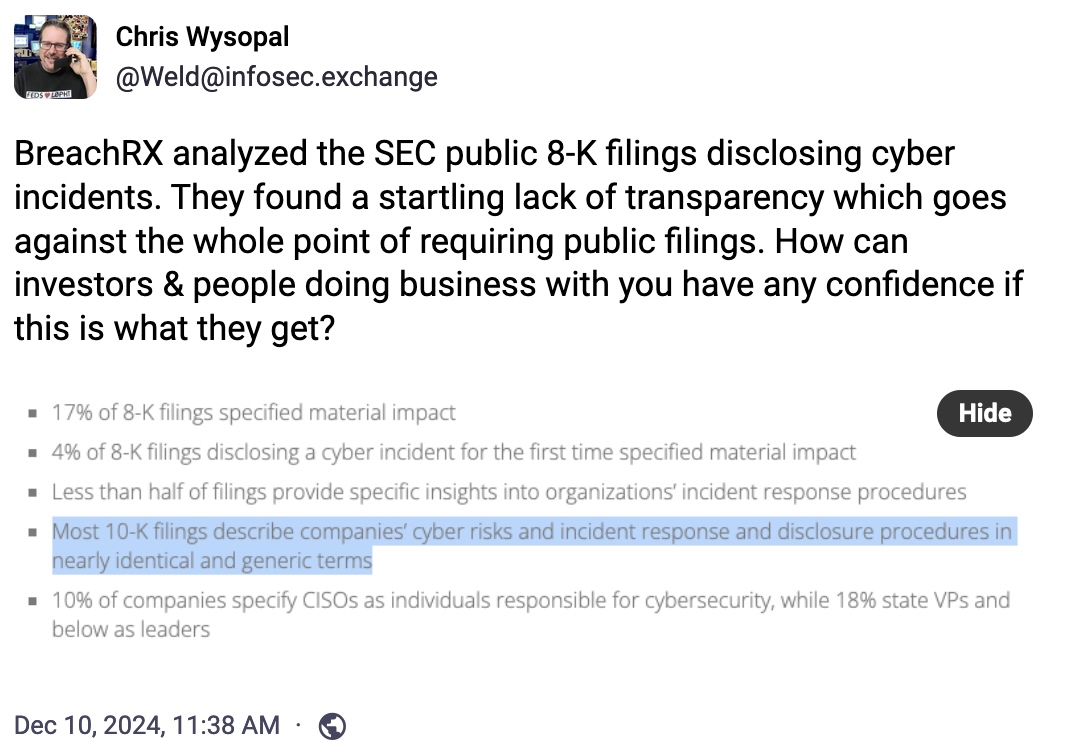
SEC disclosure rules are a hot mess, one year later
Axios: Last December, the SEC began enforcing new cybersecurity disclosure rules; you know, to try to get companies to be more transparent about cybersecurity incidents, like data breaches. Turns out, bzzzt! nope. A new analysis of more than 70 individual 8-K filings reporting cyber incidents shows only around 17% of 8-K filings with the SEC provide specific details about the material impact on a company's business. Most are also just copy-and-paste jobs with near-identical and generic terms. The SEC wanted transparency, and the companies did the barest minimum.
Meet Termite, the ransomware gang taking credit for Blue Yonder's breach
Cyberscoop: There's (yet another) new ransomware gang in town. Termite is taking credit for the ransomware attack that hit Blue Yonder (another supply chain firm). The gang uses a reworked version of Babuk, whose ransomware source code was made public in a leak several years ago. The group is said to be targeting victims indiscriminately. For Blue Yonder's part, the company spluttered out an update on Thursday (after a near-week of silence!) saying its restoration was still in progress.
New EU smart devices rule takes effect
TechCrunch: The European Union's Cyber Resilience Act, now in force, requires firms making products that are sold in the EU to meet certain cybersecurity requirements. The U.K. has a similar law in effect already, and now Europe's getting it, too. Compliance with the rules will start in 2027, but best to get ahead of this one now than face hefty fines for failing to secure your products.
~ ~
OTHER NEWSY NUGGETS
Location broker offers to track people via doctor visits: Another creepy location data firm, Fog Data Science, is reportedly asking police for the address of specific people's doctors so that individuals can be identified in massive datasets storing people's location data. That's per 404 Media ($), which has the docs to prove it. Fears are that the location data can be used against people seeking reproductive care in a post-Roe America. (via 404 Media ($))
Krispy Kreme fills cyber holes: Donut giant Krispy Kreme was forced this week to fill its security holes after finding itself in a jam following a cyberattack. The company said some online orders were disrupted by cowardly custards. At least it was a grand time for headline writers and pun enthusiasts. Honestly, I just dough-nut believe it. (via BBC, The Register)
Patch Tuesday drops fresh zero-day: Brian Krebs has your latest round-up of all the patches you need to know from this month's Patch Tuesday. There are 70 security holes plugged in Windows, with one zero-day under active attack in its Common Log File System, which can grant an attacker "system"-level (aka root) privileges on a vulnerable device. CLFS remains a popular avenue for ransomware gangs of late, per Rapid7's analysis. (via Krebs on Security, @screaminggoat)
Rhode Island hacked: A cyberattack hit Rhode Island's RIBridges system, which the state uses as its centralized benefits eligibility system, including SNAP and food benefits. Looks like there was some communication with the threat actor, which sent a screenshot of the compromised files to consulting giant Deloitte, which developed the system. (So at least we know who to blame for the system's shoddy coding.) Reuters ($) confirmed a ransom was demanded, so likely a ransomware or extortion gang was behind the breach. The state has details on the programs affected and the likely types of data stolen, including Social Security numbers and certain banking information. And right before the holidays? That's callous. (via RI Governor)
~ ~
~ ~
THE HAPPY CORNER
Aaaaand breathe. Or scream! Either way, welcome to the happy corner.
First up, we have to go to extreme lengths to exit Vim. Alternatively, you can yeet your computer into the nearest body of water. That also works.
Privacy buffs and iPhone users. Now you can automatically share photos with friends, family members, or otherwise interested intelligence officers without also revealing your location. Since most phones these days embed your precise location data with your photos, this simple iPhone setting can switch off the auto-location sharing.
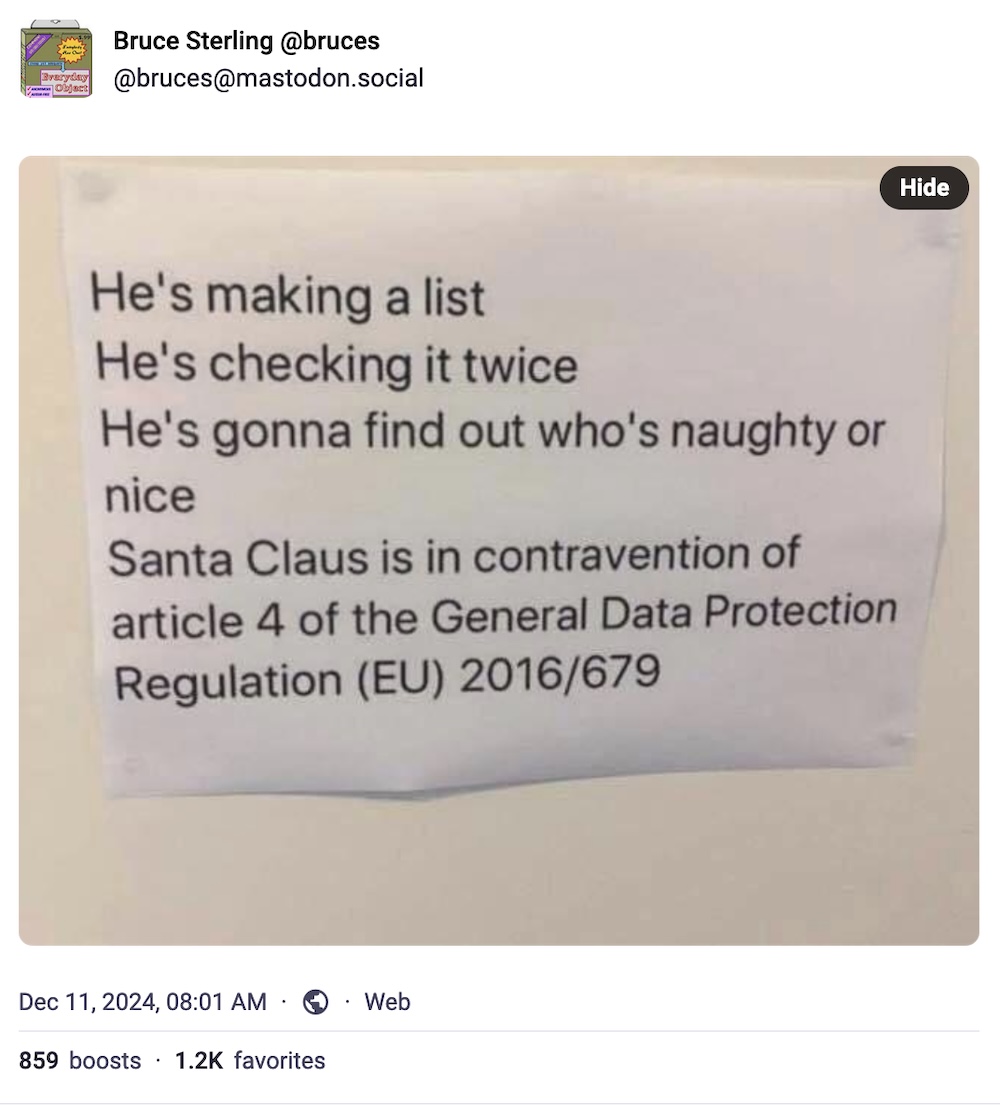
Our annual look at Santa's GDPR compliance — and it's an automatic fail. Again.
And finally, this week: bonus cybercat: Random street cat or secret CIA spy? (C'mon, we all know cats are actually double-agents.)
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Catalino, a very handsome void floof who can be seen here on the left — and, kinda on the right — after climbing up a tree and discovering that security through obscurity doesn't work. That's one cyber-smart kitty. Many thanks to Bill for sending in!

Send in your cyber cats! (or a non-feline friend). You can email them in at any time with a photo, including their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
It's good to be back after a couple of weeks away; thanks for reading! I'll be back with regular newsletter cadence next week as usual, even (especially!) with the holidays coming up. It's a busy time for hackers and spies, too!
If you want to get in touch about the newsletter — or to throw in some good news or a cyber cat — please do!
I'm off to grab a coffee and a Krispy Krem... oh, wait.
From a chilly east coast,
@zackwhittaker