this week in security — december 17 edition
THIS WEEK, TL;DR
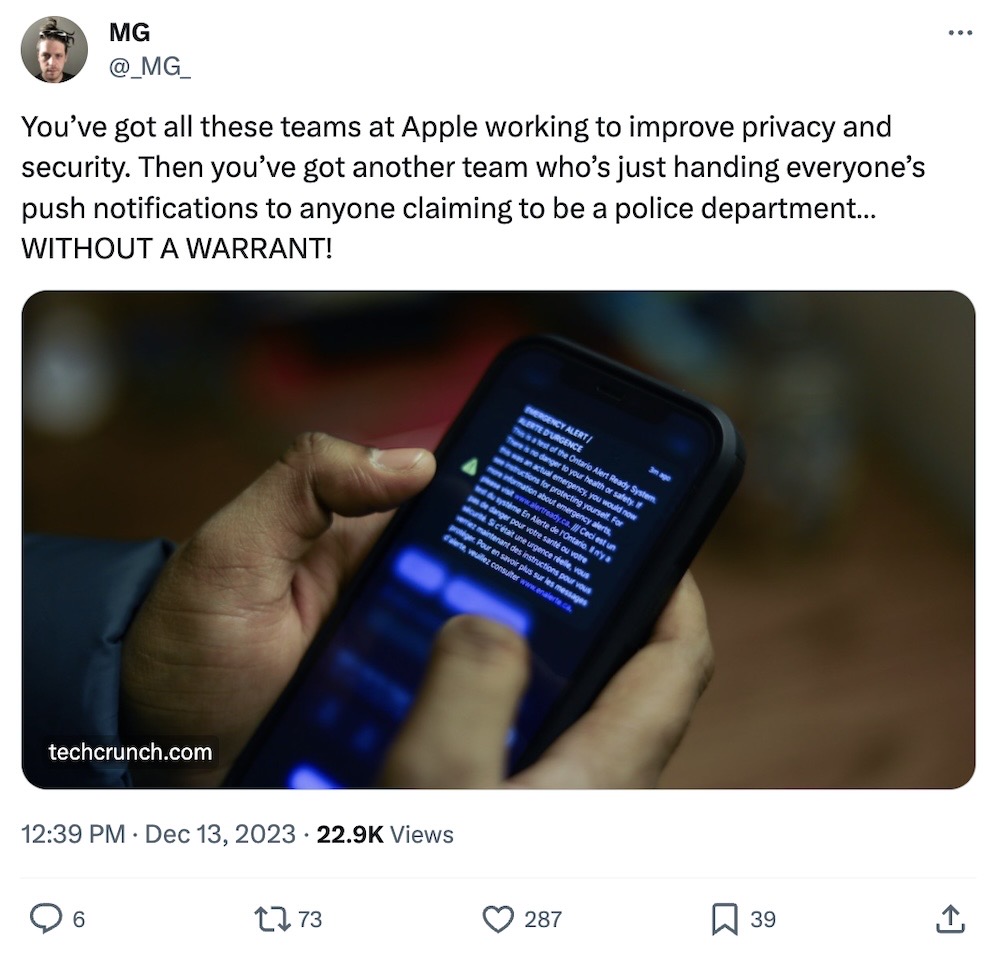
Apple will no longer give push notification data to police without a warrant
Reuters ($): A big week in surveillance. First up: Apple said it will no longer respond to police requests for push notification data and instead will require a court-approved order or search warrant. That's because Apple was turning over users' data in response to subpoenas, which are issued by police departments and are subject to no judicial oversight. Google, for its part, always required a search warrant for this data. App push notifications share with you message content, emails, reminders and more. Sen. Ron Wyden broke the news last week that governments were requesting this data from Apple and Google, since push notifications are routed through their servers, but that the DOJ had largely kept the practice a secret. What happens on iPhone stays on iPhone — well, now it does. (Who thought that marketing campaign was a good idea?)
More: Daring Fireball | TechCrunch | @_MG_ tweets
Google just killed geofence warrants that give police location data
Forbes ($): Google said that it will "soon" begin storing users' location data from Maps on-device, meaning the search and ads giant will no longer store vast banks of users' location data going forward. That effectively closes the loop on geofence warrants, the kind of search warrants that can tell who was in a particular place at a certain time (such as the place of a crime — oh look, it's a rhyme). But that invariably includes entirely innocent people's data. Not even the courts can decide if geofence warrants are constitutional. Google should be praised for ending the surveillance practice, even if geofence warrants are largely Google's fault for creating these huge stores of location data to begin with — all for making ad money, of course. Google still retains a ton of historical data, too. Apple, for its part, doesn't collect location data as it stays on users' devices. As of its last transparency report, Apple said it has returned zero data (that it doesn't have) in response to 13 geofence warrants. That seems to suggest that storing location data on-device does in fact make it more private.
More: Bloomberg ($) | The Verge | Reason | EFF
Debate over U.S. surveillance powers pushed into 2024
The Record: But for the two nuggets of good news this week, it's balanced out by at least four more months of debate about Section 702, the U.S. surveillance law that is about to expire at the end of December. Section 702 powers allow the U.S. to spy on non-U.S. citizens outside the U.S., but this allows the "incidental collection" (😉) of Americans' data, which the feds can access without a warrant. But since nobody in Congress can seemingly decide on anything these days, U.S. lawmakers instead just kicked the program down the road to April, allowing this surveillance to continue on until at least then. What does that mean for the annual FISA certification due in April? Let's hope this just isn't a sneaky way for intelligence leaders to keep their Section 702 powers rolling for a whole year longer.
More: Axios | The Record | The Register
Pharmacies share medical data with police without a warrant, inquiry finds
Washington Post ($): We're not done on the surveillance front... and this might really annoy you — and rightfully so. Some of the U.S.' biggest pharmacy giants — including CVS, Kroger and Rite Aid — are handing over your personal data and sensitive health information to police "on the spot" citing "extreme pressure to immediately respond." (Just going to interject here with a heavy "nope," since this is not a justified reason!) The eight pharmacies told congressional investigators that they each received tens of thousands of legal demands every year, but haven't disclosed them. Look, there is absolutely no excuse here and if America was a little less focused on making gobs of cash for a select few billionaires, maybe we wouldn't be in the surveillance mess that we are today?
More: Congressional letter [PDF] | The Record | Becker's Hospital Review
Ukraine mobile network Kyivstar hit by cyberattack
BBC News: Ukraine's main mobile network Kyivstar said it was downed by a cyberattack this week. Customers were left without phone or internet service, and bank ATMs were unable to function. CERT-UA said it was investigating the incident, which Kyivstar said doesn't appear to have involved the theft of customer data (so far). A group called Solntsepek, said to be linked to the notorious Sandworm unit in Russia's military intelligence wing GRU, took credit for the cyberattack, but Kyivstar denied the "destruction of our computers and servers" as fake. @Zhora, who was until recently the unindicted deputy of Ukraine's SSSCIP, shared a tweet thread.
More: Wired ($) | TechCrunch | Reuters ($)
~ ~
THE STUFF YOU MIGHT'VE MISSED
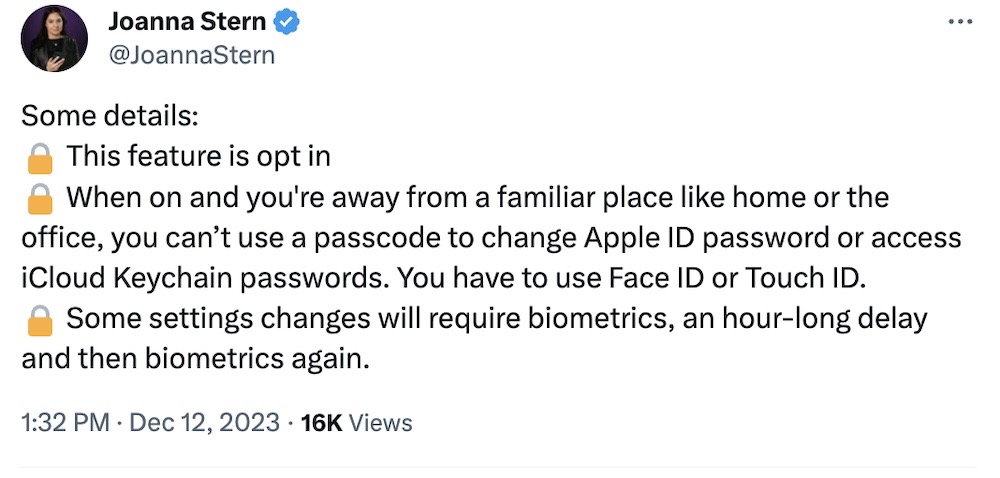
Security change to protect users from iPhone thefts
Wall Street Journal ($): Apple is tinkering with a new feature that would make it significantly more difficult for thieves to break into someone's iPhone. The new feature, currently in beta, is dubbed Stolen Device Protection. As explained by @joannastern, it will block thieves from using a stolen iPhone passcode unless the iPhone is near a familiar place like work or home, and the owner has to use their Face ID or Touch ID (on time delay, and twice!) to change any settings.
Microsoft seizes fraudulent accounts used for cybercrime
Microsoft: Technology giant Microsoft secured a court order to seize websites and infrastructure used by a group of cybercriminals dubbed Storm-1152, which sells access to fraudulent Microsoft accounts for other threat groups used for cyberattacks. Those groups include Scattered Spider, the group allegedly behind the casino and hotel hacks earlier this year. Microsoft named the hackers behind the fraudulent accounts, who are believed to be based in Vietnam. (Maybe that naming-and-shaming will deter them from future hacks?) More from Cyberscoop. Meanwhile, Wired ($) has an inside look at Microsoft's Digital Crimes Unit, which was behind some of the action.
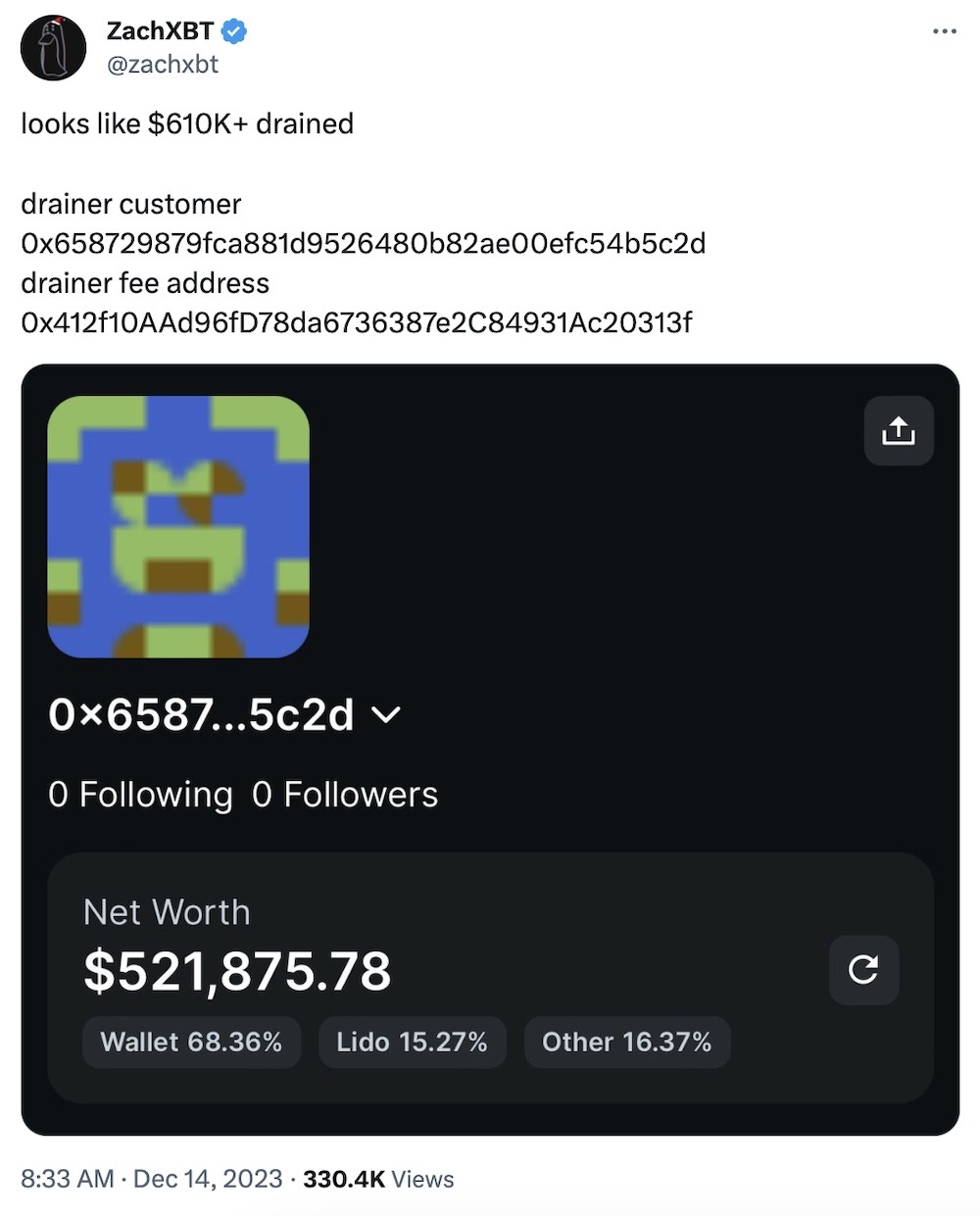
Supply chain attack targeting Ledger crypto wallet leaves users hacked
TechCrunch: Hackers compromised the code of Ledger's Connect Kit, which allows users to connect decentralized apps made by other companies to their Ledger crypto wallet. The cyberattack was spotted pretty quickly, and blamed on someone for compromising the account of a former employee (but why that former employee still had access is unknown at this time). The hacker used the access to modify the code so that it would drain crypto accounts of unsuspecting users. The hacker stole some $600,000 during the few hours the malicious code was active.
~ ~
OTHER NEWSY NUGGETS
FCC votes to tighten telecom breach rules: U.S. telecoms, some of the leakiest companies in the U.S. (see T-Mobile Figs. 1 through 8), will now be subject to stricter data breach notification rules. The new FCC rules will prompt telecoms to disclose when it loses customer data, such as through compromise or "inadvertent" disclosures. The telecom companies aren't happy — not a surprise given they've all been hit by some kind of security incident in recent years. (via FCC)
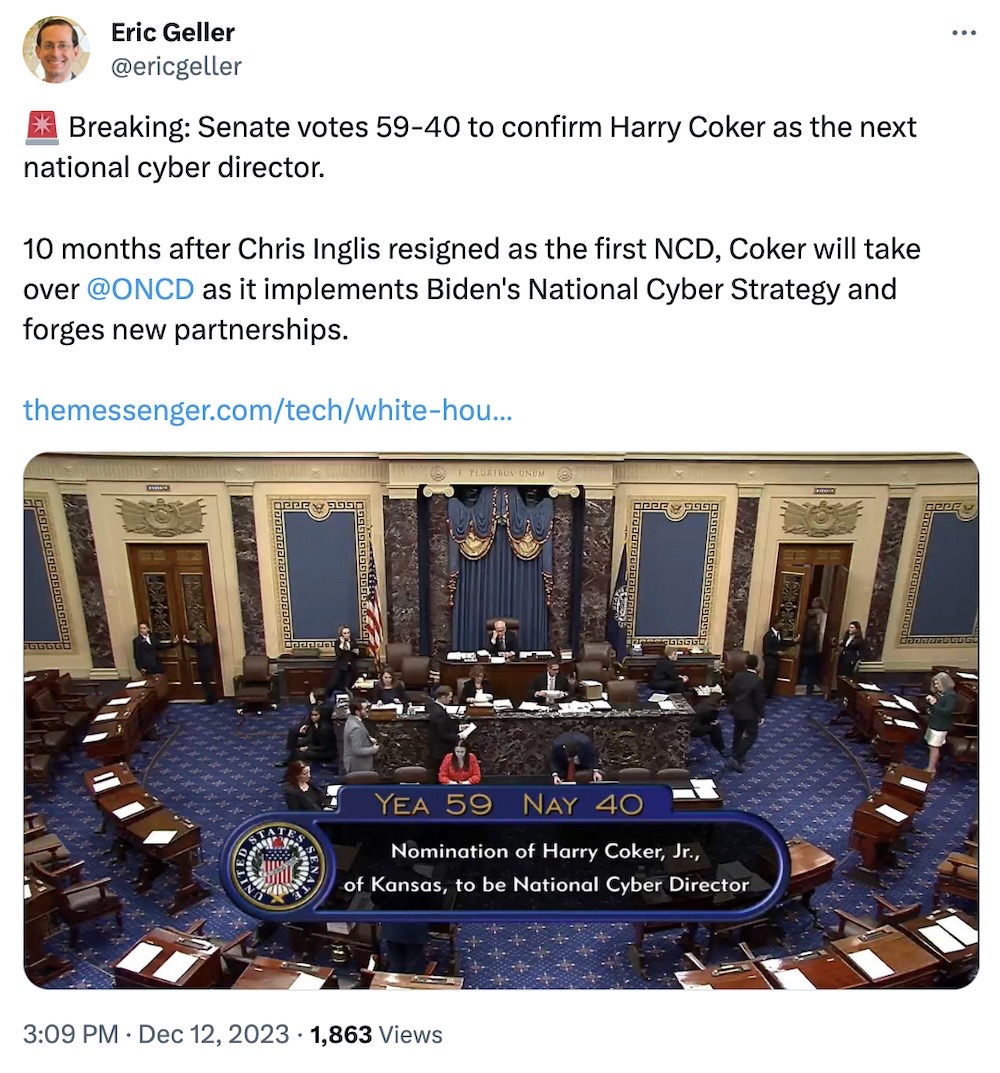
Re: Re: RE: RE: New national cyber director: Finally, the U.S. has a new national cyber director. Harry Coker, a former NSA lawyer, will now head up the Office of the National Cyber Director, after no fewer than two acting heads in the interim. Coker will now implement President Biden's national cyber strategy. (via @ONCD, @ericgeller)
23andMe changes terms to make it more difficult to sue: Just days before 23andMe disclosed that hackers stole about half of its customers' personal and genetic data, 23andMe changed its terms of service to make it more difficult to sue the firm. Lawyers speaking with @lorenzofb said the changes were "cynical," "self-serving," and "a desperate attempt" to protect its own interests from customers' legal actions. Remember: don't give your friends and family a 23andMe kit for the holidays, given the risks that 23andMe and genetic testing kits can have on you and your family. (via TechCrunch)
Hack, hack, who's there? The Ukrainians: The Ukrainian government says it has hacked into Russia's federal tax service and spread malware, resulting in the "complete destruction" of its databases. Per a statement by Ukraine's Ministry of Defense, the Russian tax system was "completely eliminated — the entire database and its backups were destroyed," but not before Ukraine swiped a copy for itself. It poses an interesting question about the role of cyberattacks in war. Russia invaded Ukraine in 2022, which used wiper malware during its assault. It's almost like the Kremlin brought this on itself... (via Ukraine Ministry of Defense)
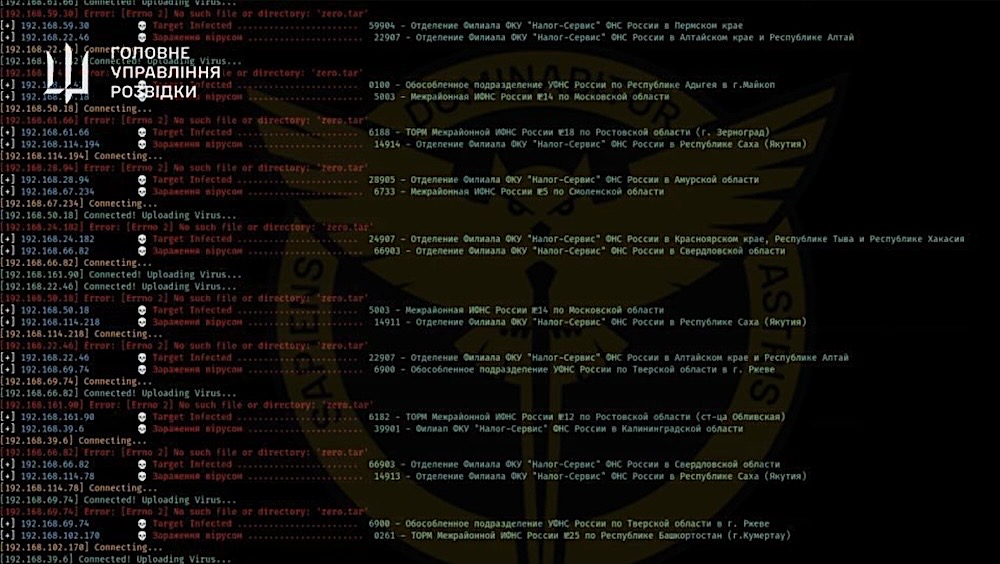
~ ~

~ ~
THE HAPPY CORNER
Buckle up, it's the happy news drive. Safety first, happy stuff second.
Congratulations to Microsoft for a Patch Tuesday without a single zero-day disclosed, aka the "lightest" set of security patches in some four years, by Cisco Talos' count. Of course, there are still critical patches to fix. Patch today!
Discord has added support for security keys, the phishing resistant password replacement. The move makes the online community that little bit a lot more secure. (via @campuscodi)
Some good news out of Utah, where the state's Supreme Court has sided with a defendant who argued the police could not force him to provide the passcode to his phone. (The logic goes that passcodes can't be compelled as they're in your head, whereas biometrics can be since they're, well, literally on you.) That falls largely in agreement with other courts across the U.S. — and while good news for Fifth Amendment aficionados, it's likely still to end up before the U.S. Supreme Court at some point.
And lastly: Bonus Fibonacci cat:
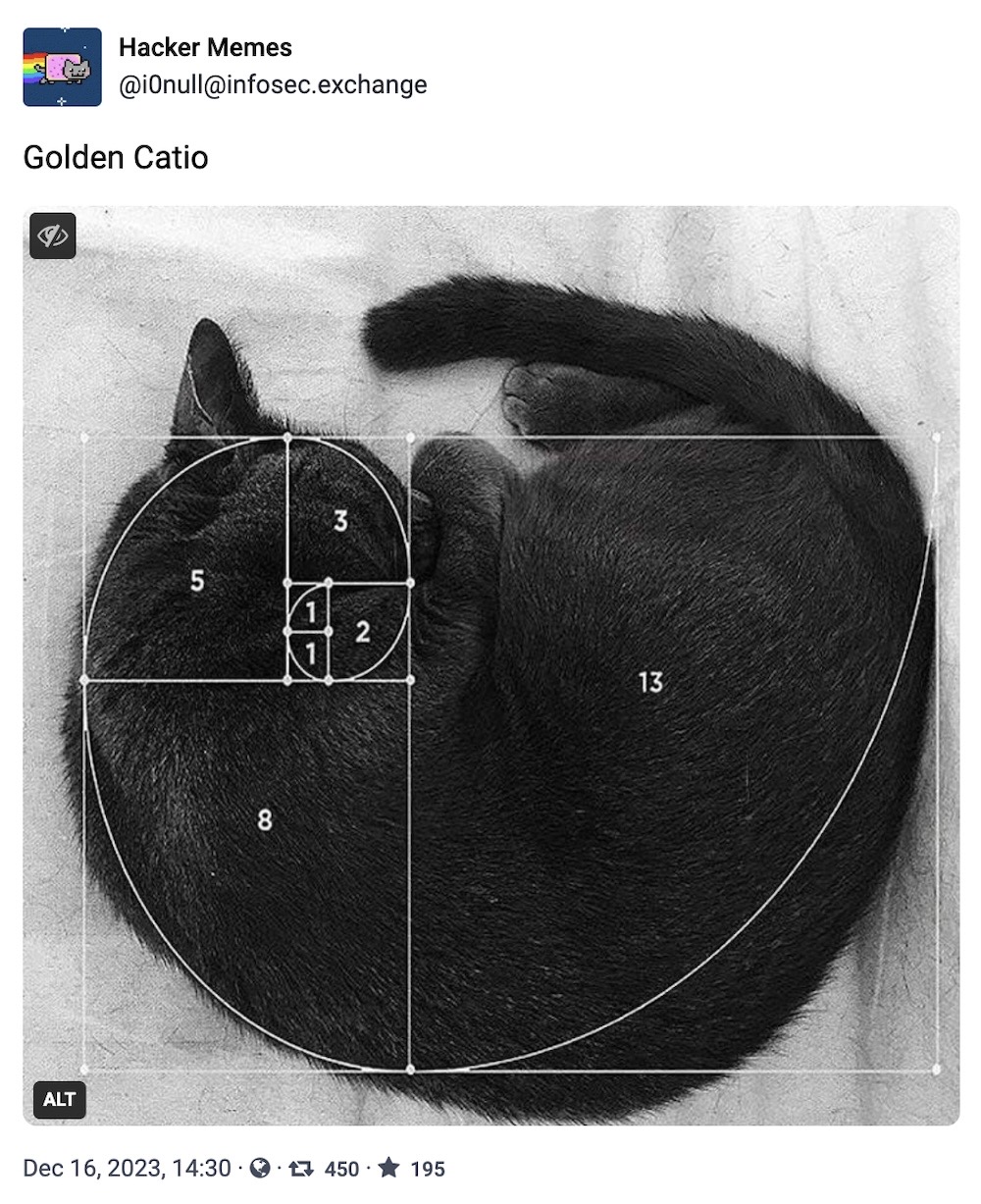
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Thomas. According to his human, Thomas said that work was finished for the day and those APIs were secure (but he was also wrong and his human found a bunch of serious IDORs). Thomas may not be the best good bug hunter but he's great for moral support. Many thanks to James H. for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's it for this busy week. Thanks so much for reading! I will likely be back in a couple of weeks with Christmas fast approaching and the holiday season in full swing. I hope you have a restful, chill, and relaxing time, we've all deserved it after this year!
As always, please get in touch with any feedback or comments. I'll be back at the end of the year with a final edition for 2023, and back to the usual schedule starting 2024.
Peace,
@zackwhittaker