this week in security — december 18 edition
THIS WEEK, TL;DR
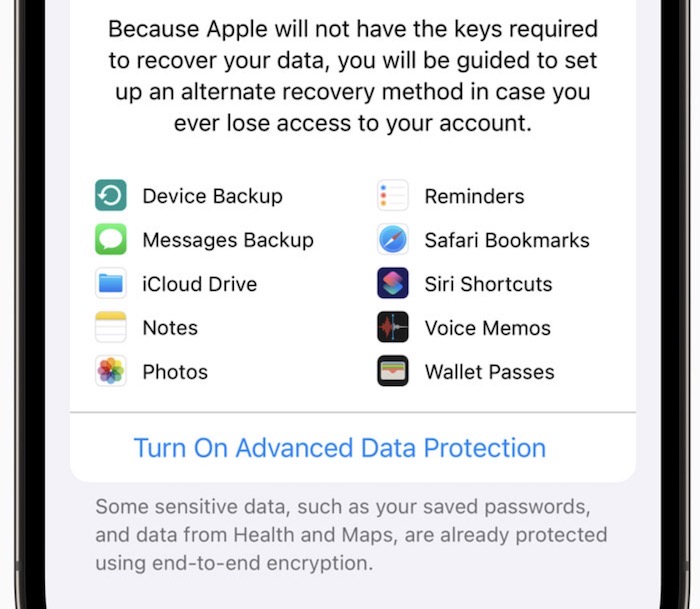
Apple rolls out iCloud encryption to everyone's delight, except the FBI
Techdirt: Remember a few years ago when the FBI tried to compel Apple to build a backdoor so it could hack into a shooter's iPhone? The case collapsed when hackers found a way in, rather than relying on Apple's compulsory assistance. Fast forward five years and now Apple is doubling down on its encryption, closing a loophole long used by feds to acquire iPhone data in the cloud, by finally end-to-end encrypting iCloud Backups with a new update starting with iOS 16.2, released last week. It's a huge move for users who backup to Apple's cloud. Clearly the FBI isn't happy (even though it can still break into locked phones). In a statement, the FBI said it was "deeply concerned" by the "threat" end-to-end encryption poses. (My read: It's like the FBI just locked its keys in the car and now it's cross at the car maker? I digress.) Wired ($) broke the news last week, and that Apple dropped its controversial plan to scan users' photos client-side for child abuse materials.
More: Apple | Wired ($) | Washington Post ($) | Wirecutter ($)
Hackers planted files to frame an Indian priest who died in custody
Wired ($): Wild reporting from @agreenberg on the case of 84-year-old Stan Swamy, who contracted COVID-19 in an Indian jail and died. A forensic examination of Swamy's laptop shows Indian police compromised his laptop and planted evidence, then tried to delete files (to destroy evidence and cover their tracks) just one day before police seized his devices. This isn't even the first time this has happened. Per Wired: "Swamy never touched the files himself. After his devices were seized by Pune City Police, those files were among the digital evidence used to charge him and the other Bhima Koregaon 16 defendants with terrorism as well as inciting a riot in 2018 that led to two deaths."
Background: Wired ($) | SentinelOne | More: Washington Post ($) | @agreenberg
Chinese hackers actively attacking flaw in Citrix gear
Cyberscoop: The NSA said in an advisory this week that APT5, a China-based espionage group, is exploiting a new Citrix zero-day in the wild. The advisory was designed to burn China's ongoing activity by calling it out — and Citrix releasing patches. Citrix was generally praised for its response (even if the feds knocking on your door is an unwelcome surprise). Fortinet also patched a pre-auth RCE bug, and enterprise backup giant Veeam also confirmed it had two security flaws fixed earlier this year.
More: Reuters ($) | NSA advisory [PDF] | TechCrunch
FBI's vetted information sharing network InfraGuard hacked
Krebs on Security: InfraGuard, a program run by the FBI to build partnerships that allow cyber and physical threat information to be shared with the private sector, was compromised. A database of some 80,000 members are for sale on an English-speaking cybercrime forum. The hackers responsible broke in impersonating a financial industry CEO who was vetted by the FBI itself. (Ouch.) See, maybe if the FBI embraced encryption a little more, it wouldn't have its name attached to so many embarrassing headlines.
More: Associated Press | Gizmodo | @fbajak
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Patch Tuesday: Apple and Microsoft fix zero-days
TechCrunch: The mystery of iOS 16.1.2 is over. The iterative iPhone software update released a couple of weeks ago contained an unspecified security fix for pretty much every supported iPhone model going. Two weeks on, Apple said the update fixed a zero-day bug found in WebKit that was "actively exploited" against users running iPhone software prior to iOS 15.1. There's nothing on who is behind the exploitation. However, Google's Threat Analysis Group — which investigates state-sponsored hacking and the like — was credited with discovering and reporting the bug, so if I had to guess, it was probably a nation-state. (Disclosure: I wrote this story!). I have a hunch Google will have more to say on this in the next few weeks. Plus, more from The Register on Microsoft's zero-day fix for a Windows SmartScreen security feature bypass vulnerability.
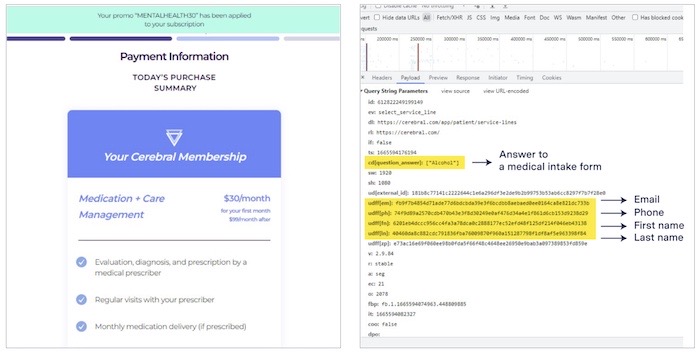
Dozens of telehealth startups sent sensitive health data to Big Tech
The Markup, Stat: An investigation found that 49 out of 50 direct-to-consumer telehealth websites, like WorkIt, are leaking sensitive medical information they collect to the world's largest ad platforms. In one case the reporters found WorkIt was "sending their delicate, even intimate, answers about drug use and self-harm to Facebook." Through visuals, the reporters show how trackers on these sites' pages are transmitting sensitive answers to medical questions — combined with names and email addresses — to Facebook, Google, Snap and TikTok. "Who cares if Facebook knows I take migraine meds," you might think, but not such a great line of thinking for those who live in places where their medical rights and bodily autonomy can get taken away overnight.
Hackers score nearly $1M at device-focused Pwn2Own contest
Dark Reading: Pwn2Own, the zero-day flaw finding contest, is back. Some 63 new vulnerabilities were discovered from the competing teams, including bugs in Canon and HP printers, routers and storage servers. Instead of "popping Calc" (which is how hackers demonstrate their exploits safely), one group exploited a Lexmark printer to play the Mario theme music. The Register, again, has more.
Spyware and surveillance-for-hire industry 'growing globally'
The Record: If you thought the nation-state spyware industry was just limited to a few bad actors like NSO Group, you'd be wrong. Facebook parent Meta has a new report out this week looking at spyware vendors around the world, including in Israel — where NSO, Quadream, and Candiru are based — but also Russia (like Positive Technologies), India (remember CyberRoot?) and the United States (Social Links). Meta reported this activity because its detected threat activity targeting Facebook users. Meta said there is a need for a "whole-of-society response" to tackling the "growing malicious industry."
Hacking the Boston metro's Charlie Card
Bobbyrsec: Vulnerabilities in the contactless payment cards used in the Boston area subway system called the Charlie Card (did anyone else's mind go immediately to The Wire?) allow anyone to ride for free. Here is a fantastic blog post by @bobbyrsec explaining how the bugs work — and how they've existed since at least 2008.

~ ~
OTHER NEWSY NUGGETS
Telstra sorry for leaking 130,000 customers' data: Australia's largest cell carrier Telstra said it's sorry for accidentally publishing names, phone numbers and addresses of 130,000 customers whose personal information was unlisted (and not publicly posted). Their data was subsequently made available through its White Pages listings, which incredibly are still a thing. (via The Guardian ($))
IRS: Hold my data breach beer: Not wanting to be outdone, the U.S. IRS — yes, the tax people — accidentally released the private data of some 112,000 taxpayers. The data was mistakenly published on the IRS' website for at least a couple of weeks. It's the second time the IRS has spilled taxpayers' data in the past few months. (via Bloomberg Law ($))
Xnspy stalkerware spied on thousands: A little-known phone surveillance app called Xnspy, which explicitly promotes its app for spying on spouses, snooped on thousands of Android devices (by way of a malicious app) and iPhones (by using stolen credentials to access iCloud backups). Security researchers @evstykas and @s0lfer found and presented a ton of security flaws in several "stalkerware" families, Xnspy included, many of which are very easy to exploit. Along with leaked data, Xnspy is linked to a Lahore-based group of developers called Konext. (Disclosure alert!) (via TechCrunch)
Banned by FTC, Support King is back: Speaking of stalkerware... Support King, a maker of surveillance apps, was banned by the FTC in 2021 from the surveillance industry after its stalkerware app SpyFone spilled thousands of victims' data. Now, Support King is back — and linked to a new phone spying operation called SpyTrac. Access logs and AWS keys on SpyTrac's server link to Support King and a group of developers based in Sarajevo. After reaching out for comment, SpyTrac went offline. Then, after publication, Support King's website disappeared. Coincidence, it was not. (Disclosure alert!) (via TechCrunch)
Rackspace ransomware'd: Customers affected by a ransomware attack nuking Rackspace's hosted Exchange email are royally pissed at how the web hosting giant handled the incident. In an email to customers, Rackspace seemed to pat itself on the back, saying the incident "was quickly contained and limited solely" to customers' Exchange emails, but made no reference of what it was doing to get their data back. With no sign of backups, customers look like they're out in the cold. There's also a scathing op-ed worth reading. (via Dark Reading, San Antonio Report)
California finance department hacked: And with ransomware front of mind, authorities in California say they were hit by a security incident — likely ransomware, given LockBit is claiming responsibility for stealing dozens of gigabytes of data. The state said it was responding and investigating. Meanwhile, the Cuba ransomware group was found using Microsoft-signed malicious drivers to better target victims with ransomware, a major escalation in the group's technical abilities. (via SecurityWeek, Wired ($))
Booters booted: The U.S. seized 48 websites in a sting aimed at taking down DDoS-for-hire websites, which allow paying users to pummel websites with traffic to knock them offline. Six were charged under U.S. hacking laws. Though, it took a bit of time for the government to actually take down the offending sites... whoops. (via Bloomberg ($))
~ ~
THE HAPPY CORNER
It's the last newsletter of the year (boo!) so here's the last 2022 edition of the happy corner.
First up, the cybersecurity "try-hard" starter pack. (I can relate — I have that exact beard.) Zip up your hoodies, switch your terminal font to green, and get hax0r'ing.

Next up. GitHub is mandating some form of two-factor by the end of 2023. A good, long overdue move.
The most congratulations to @hacks4pancakes, who was awarded the SANS lifetime achievement award this week. Incredibly well deserved! Lesley is an incredible force for good in the security and infosec community, whose contributions are countless and endless. Thank you for everything you do!
And finally. NIST, the government's standards agency, is retiring SHA-1, the aging hashing algorithm due to sunset in... 2030?! I'll be sure to remind you in... seven years.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's incredibly festive-themed cyber cat is Sloane, who is keeping guard of the presents under his human's Christmas tree, a.k.a. IRL threat detection. Many thanks to Velda F. for sending in!

Please send in your cyber cats (or their friends). Email me a photo and their name, and they'll be featured in an upcoming newsletter. Submitted before? Send an update!
~ ~
SUGGESTION BOX
This is the last newsletter of the year! Thank you so much for reading, contributing, sharing and subscribing, it really means so much to me. Wherever you are in the world, I hope you have a wonderful and peaceful holiday season. And a very happy Hanukkah, Christmas, and Kwanzaa for those who celebrate.
I'll be back with a newsletter on New Year's Day. In the meantime, the suggestion box is always open or feel free to email me any feedback.
See you in 2023! 🎉
—@zackwhittaker