this week in security — december 22 2024 edition
THIS WEEK, TL;DR
WhatsApp wins ruling holding spyware maker NSO liable for hacking
Washington Post ($): Breaking news from Friday: Spyware maker NSO Group will be on the hook for damages in a case brought by WhatsApp-owner Meta, according to a summary judgement from a federal court in California, after finding NSO had essentially hacked into Meta's systems by sending its malicious spyware through its servers over a thousand times to targeted WhatsApp users. The ruling found that the case can proceed to trial only to determine how much damages should be. The case began after WhatsApp found evidence that more than 1,400 WhatsApp users were targeted with NSO's spyware back in 2019. It's not known which governments authorized the hacking, but NSO has plenty of countries that use its spyware. The ruling was called a "decisive blow" to NSO Group.
More: Reuters ($) | Court Ruling [PDF] | @jameeljaffer | @davidakeye
Serbia used Cellebrite tools to unlock phones then plant spyware
Amnesty: Speaking of spyware... damning findings from Amnesty, which found evidence that spyware was planted on a journalist's phone after a routine police traffic stop, only to find later that his phone had spyware planted on it. Forensic analysis shows Cellebrite tools were used to unlock the journalist's phone without their passcode and that access was used to plant the spyware. The spyware, dubbed NoviSpy, was found on more phones belonging to civil society, suggesting that the spyware is "used widely" by Serbian police and authorities, potentially on hundreds if not more phones. TechCrunch and 404 Media ($) had great coverage, who also spoke with the journalist directly. In the same report, Amnesty (and Google's zero-day hunting unit) confirmed it had ultimately gotten fixed a Qualcomm zero-day unearthed in October, which Amnesty says was used by Cellebrite to unlock various phones. There's a good lesson here: if you're ever forced to give up your device to cops (passcode or not), assume the worst and get your device checked (more on this later).
More: Project Zero | Washington Post ($) | @DonnchaC tweets | @_sethJenkins
Ascension says 5.6M hit by May ransomware attack
Reuters ($): Earlier in May, Ascension (which owns over 140 U.S. hospitals) was hit by outages and disruption for weeks following a cyberattack. Months later, the healthcare giant confirmed that the ransomware attack allowed hackers to steal medical data on 5.6 million people, including lab test results, procedure codes, and more. That (by my count) is the third largest healthcare related data breach of 2024, per the Dept. of HHS ongoing figures. That's a drop in the ocean to Change Healthcare's 100M+ data breach.
More: TechCrunch | Milwaukee Journal Sentinel | The Record
U.S. weighs ban on Chinese-made router in millions of American homes
Wall Street Journal ($): The U.S. government is said to be weighing the prospect of banning Chinese-made TP-Link routers across the U.S. next year. Why? Because the routers have been frequently targeted by hackers to launch cyberattacks — including China, which is where TP-Link devices are manufactured. The company "routinely" ships devices with security flaws, per authorities, though the U.S. has never outright said (or provided any evidence) that TP-Link routers are a direct security threat. Which, this might be fair to some extent — but can we not say much the same about routers made in the U.S.? CISA's latest report on the top routinely exploited flaws last year were found in... Cisco routers (see: The Record for more). Instead of playing whac-a-mole with the ban hammer, maybe we should listen to folks like CISA who have been telling us for quite some time now to build security in devices by default? Anyone... anyone...?
More: CSO Online | @WeldPond
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hackers stole $5.3M in crypto from stolen LastPass vaults
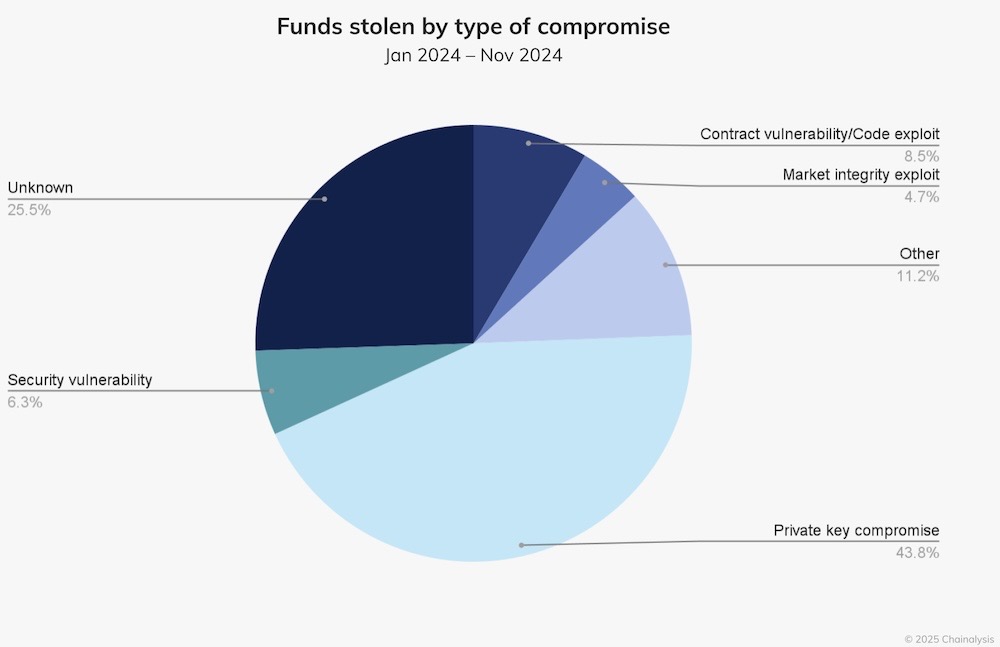
ZachXBT, The Block: The LastPass breach of December 2022 is the gift (to hackers) that keeps on giving (them your cryptocurrency). Around 40 customer password vaults from yesteryear, which were stolen during the 2022 hack, have since had their master passwords cracked, allowing access to the credentials stored inside — including those of crypto accounts and the like. (This is because prior to the breach, LastPass' complexity requirements for master passwords were, well, crap.) That's allowed the long-game hackers to steal at least $5.3 million in crypto in recent weeks by using those cracked credentials which the owners hadn't changed, according to top crypto investigator @ZachXBT speaking with The Block. Per Chainalysis, hackers have stolen $2.2 billion (with a b!) in 2024 alone, with North Korea remaining a major thief.
New critical Apache Struts flaw exploited to find vulnerable servers
Bleeping Computer: A new Apache Struts2 bug just dropped, and this one looks like it could be problematic. The new bug (tracked as CVE-2024-53677) — since patched — can allow attackers to manipulate file-upload parameters to enable path traversal (an increasingly common bug these days!) that can be used to remotely plant malicious code on an affected system, allowing the attacker to run commands on the server and more. The bug reads similarly to CVE-2023-50164, which came out a year ago. (Time flies!) Some are exploiting the bug using public proof-of-concept code, so affected customers should update today. More from SANS.
Reviver digital plates can be jailbroken to display false numbers
Wired ($): Digital license plates that can hide your license plate (or spoof someone else's) sounds like something you'd get in an action movie. It's also highly illegal. But the good folks at IOActive found digital plates made by Reviver are vulnerable to firmware modification that allow exactly this. The 65,000 plates in circulation can't be fixed, per @agreenberg, but the bug will be fixed in plates going forwards.

Why Apple sends spyware victims to this nonprofit security lab
TechCrunch: If you're one of the unlucky few whose iPhones are targeted by government spyware, Apple will notify you and tell you to take the matter seriously (you should!). But Apple won't help or forensically analyze your device for signs of spyware, like the Harris presidential campaign found out recently when Apple refused to get hands-on with the phones. Instead, the tech giant will direct folks to the digital lab at Access Now. Security experts working in the digital defense space say this is actually a good approach. Great story from my TC colleague @lorenzofb.
Cyber agency CISA says gov't officials should use E2EE
CISA: After decades of advocating for (and sometimes winning) backdoors, those very same senior officials and lawmakers are now being told to use end-to-end encrypted apps, like Signal, to avoid having their communications accessed by Chinese hackers who are currently in the networks of numerous phone and internet companies. I know, the irony is not lost. But still good advice for everyone, anyway.
BeyondTrust says hackers accessed remote-support SaaS instances
BeyondTrust: This week, identity giant BeyondTrust, used by tons of companies to handle their employee logins, confirmed an incident in which hackers got their hands on an API key for its Remote Support SaaS instances, allowing password resets for affected accounts. Bleeping Computer explains in its reporting that BeyondTrust's report (which isn't very clear!) implies two potential zero-day bugs were exploited to gain access. It isn't yet known if downstream customer data was accessed.
~ ~
OTHER NEWSY NUGGETS
Change Healthcare's hack somehow gets worse: New details from the massive February ransomware attack at Change Healthcare, which caused widespread disruption and outages across U.S. healthcare for months and led to the theft of 100 million-plus individuals' medical data, reveal more about the attack. That's because the state of Nebraska is suing Change for its "alleged" (heavy quotes) mishandling of the world-class fustercluck. Plus, its parent company UnitedHealth told TC's @carlypage that it's still notifying affected individuals, so the 100-million number is likely to rise even further. Welp. (via TechCrunch)
Clap Clop back: The Clop ransomware gang took credit for another round of mass hacks, this time targeting file transfer tools developed by Cleo Software. That makes sense, since this isn't Clop's first rodeo targeting corporate file-transfer tools. Clop previously exploited bugs in Accellion, MOVEit, and GoAnywhere. These file transfer tools are targeted because the customers use them to send large, sensitive files over the internet but don't (or forget to) delete them afterwards. (via Bleeping Computer)
He makes it, he breaks it: CISA was created in 2018 by the Trump administration, and now looks set to be the focus of attention when Trump takes office again. @ericgeller (+ thread) speaks with sources and agency insiders who fear the worst about what's to come, and what that ultimately means for defending the nation against malicious threats. (via Wired ($))
Third LockBit member in the can: The U.S. has charged a Russian-Israeli national with being a key developer of the LockBit ransomware. Rostislav Panev is currently in Israeli custody awaiting extradition to the United States. That's now three members of the LockBit crew in custody out of seven charged to date; that's progress. (via Cyberscoop)
Russia, China, Iran, Israel, aka the SS7 crew: Sen. Ron Wyden casually dropped new info [PDF] on which countries the U.S. believes are exploiting flaws in SS7, the global protocol used to route phone calls and texts around the world but also widely abused for surveillance purposes. In the note, DHS reportedly said that Russia, China, Israel and Iran are the "primary countries" reportedly "using telecom assets of other nations to exploit U.S. subscribers." (via 404 Media ($))
~ ~
~ ~
THE HAPPY CORNER
Take a moment for you, we're in the happy corner.
If we ever needed an update to the "task failed successfully" meme, here's @meetar with a solid substitute.
Enjoy this alternative to The Twelve Days of Christmas with much better, modern, geeky lyrics.
If you need a last minute present for a relative who you know loves to grill, you can exchange your Social Security number for some actual CIA barbecue sauce.
And, since we're about to heat peak festive season, enjoy this week's final moment of peace, courtesy of RGB_Lights' annual holiday light show — though, as a friendly fyi, there are ⚠️ a lot of flashing lights! ⚠️
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week is a multi-cyber cat special that I title simply: "Reservoir Cats."
Thank you so much to Rosa U. for sending in!

Send in your cyber cats! (or a non-feline friend). You can email them in at any time with a photo, including their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
I want to close out this week's newsletter with a personal note from me, sending my best and wishing you a very merry and happy Christmas, Hanukkah, Festivus and more to all those who celebrate, and peace to everyone. I hope you have a chill and relaxing festive season, however and wherever you spend your time.
And really, thanks so much for reading; getting the coffee pot on and writing this newsletter every week to thousands of you is one of my favorite things. I love hearing from you, too, so if you ever want to get in touch, please do. I'll catch you next week to close out the year, and onwards to 2025!
With love from me, to you and yours,
@zackwhittaker