this week in security — december 3 edition
THIS WEEK, TL;DR
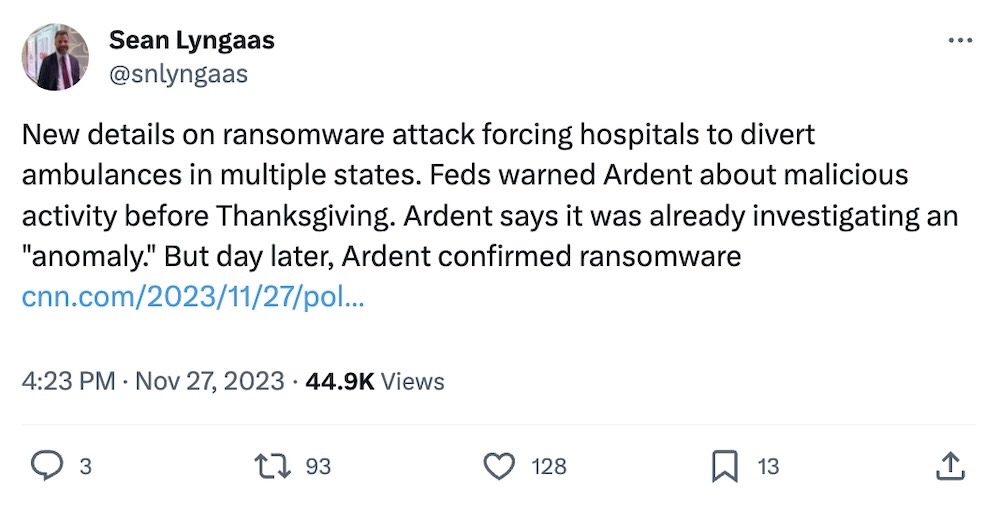
Cyberattacks hit hospitals across the U.S., amid CitrixBleed warnings
CNN: The U.S. Department of Health and Human Services sounded the alarm this week about ongoing CitrixBleed exploitation by ransomware gangs. CitrixBleed is extremely easy to exploit, yet so many organizations haven't patched, and by all accounts, it's hitting hospitals particularly hard. A number of Ardent hospitals across Texas (and other states) and Capital Health in New Jersey were hit by ransomware attacks, resulting in diverting ambulances away from emergency rooms. In Ardent's case, it was warned about malicious activity "before Thanksgiving," but a day later, ransomware hit. Not to mention, U.K. hospitals are reportedly also affected, and a U.S.-based MSP (think of it as outsourced IT) that works with hospitals also got hacked by way of CitrixBleed. Just think how much these private healthcare providers charge and profit from people's ill-health, yet can't be bothered to invest in their own cybersecurity. Truly wild state of affairs.
More: Bleeping Computer | Telegraph ($) | Capital Health | AHA
Ransomware hackers 'wreaking havoc' arrested in Ukraine
BBC News: If there's one drop of good news this week, it's that a ransomware gang in Ukraine that wreaked "havoc" for years has been dismantled following arrests in Kyiv and other cities. The gang, including its 32-year-old suspected ringleader, is accused of extorting "several hundred millions of euros" from victims in more than 70 countries. The gang is linked to the deployment of LockerGoga, MegaCortex, Hive and Dharma ransomware variants. Europol said the gang had different roles: some were involved in breaking into networks, others were laundering crypto. As we've seen with similar law enforcement efforts in the past, this may result in more ransomware-related arrests down the line.
More: Europol | @BushidoToken
ownCloud vulnerability with max. severity score comes under 'mass' exploitation
Ars Technica: The popular open source file-sharing platform ownCloud has confirmed a critical vulnerability with a maximum-rated 10.0 for its simplicity of exploitation. The remote unauthenticated bug (ie: no credentials needed to exploit) can be used to steal sensitive data, such as the ownCloud admin password, license key, and mail server credentials. The bug is said to be under mass exploitation, per Greynoise's honeypots, which "indicates that they are pretty much spraying it across the internet to see what hits." More from Greynoise on how to scan for exploitation.
More: SANS ISC | The Register | @GossiTheDog
Security flaws exposed sealed documents across five U.S. states
Jason Parker: A security researcher found at least nine vulnerabilities in court records systems used in five U.S. states, including Ohio, Georgia, Florida and others. The bugs vary by complexity, but all can be exploited using only a browser's in-built developer tools (suffice to say, that means anyone can exploit them). One of the bugs was as simple as incrementing a sequential document number in the browser's address bar. Three vendors patched (though only two confirmed), and one Florida judiciary said it patched, too, and checked its logs for exploitation and found nothing. That said, Lee County in Florida threatened legal action, which just means Lee County doesn't want to accept responsibility for its own screw-up. CISA put out an advisory, and I wrote a story. (disclosure alert!). Parker said additional platforms with known vulnerabilities will be included in future disclosures, so keep a close eye.
More: CISA | TechCrunch | Sarasota County | @kirkman | @north
~ ~
THE STUFF YOU MIGHT'VE MISSED
CISA warns ICS device at risk following water utility hack
CISA: A joint notification by CISA, FBI, NSA and the Environmental Protection Agency (hello, EPA, welcome to the cyber crew) has a new advisory warning about a vulnerability in Unitronics programmable logic controllers, or PLCs, which control industrial systems like water supplies. The advisory comes after the Israeli government warned that the Israeli-made Unitronics PLCs are publicly exposed to the internet by way of default passwords. Iran-backed hackers are already exploiting the bugs, per CBS News, including the Municipal Water Authority of Aliquippa in Pennsylvania, which said hackers took control of one of its water booster systems. Associated Press has more. While you're here, you might want to read @hacks4pancakes' LinkedIn post exploring practical lessons learned from incident response in the OT space.

KidSecurity parental control app exposed backend database
Bob Diachenko / X ($): Parental control app KidSecurity, which is used to track children's devices, exposed its backend logging database for at least a month, according to data breach finder @MayhemDayOne. "Logstash updated daily, with gigabytes of data, usual story," said Diachenko. Friendly reminder that many of these data/tracking apps are insecure, and can expose the private data of children.
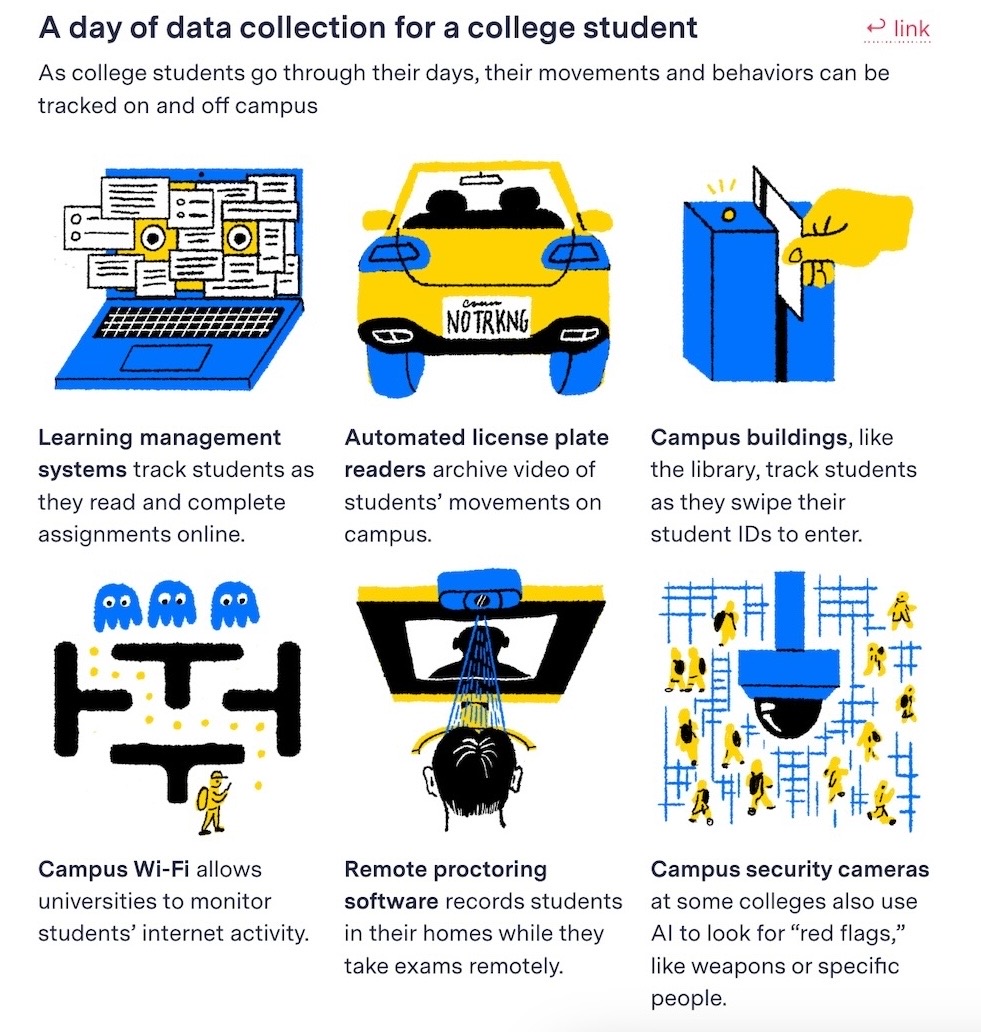
He wanted privacy. His college gave him none
The Markup: Solid reporting from The Markup, which found one of California's largest community colleges, Mt. San Antonio College, which serves more than 26,000 students in Los Angeles, is a surveillance hotbed. Colleges and universities are allowed to surveil their students (in some cases with flawed and untested tech). That includes monitoring their activity on the "learning management system, online proctoring services, and automated parking enforcement technology, three of the most invasive data collection mechanisms on campus." The student in question is part of "a growing group of college students arguing it shouldn’t be this way." Exactly!
Booking.com hackers increase attacks on customers
BBC News: Hackers are increasing their attacks on Booking.com customers by posting adverts on dark web forums asking for help finding victims, according to the BBC. Booking.com says it wasn't hacked, but criminals have figured out how to break into the admin portals of individual hotels, allowing them to see guest records, and using that access to trick victims into paying them money instead of the hotel.
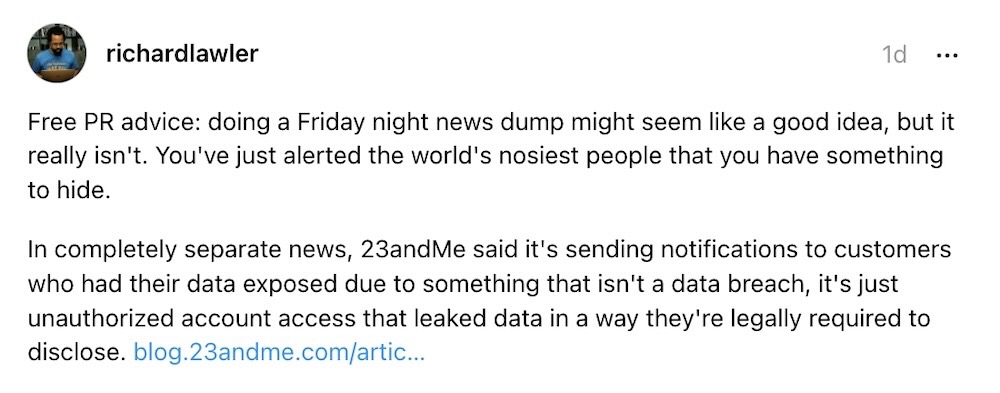
23andMe says hackers accessed ‘significant number’ of files about users’ ancestry
TechCrunch: Genetic testing giant 23andMe says an earlier credential stuffing attack affected 0.1% of its customers, around 14,000 people, but this allowed the hackers access to a "significant number of files" containing profile information about other users’ ancestry. (Disclosure alert: I wrote this story alongside @lorenzofb.) That's because of a feature that those users opted-in to called DNA Relatives, which matches users with their relatives. A spokesperson later said that about 7 million users had data stolen. For reference, that's about half of its 14 million total users.)
Google researchers report zero-days in Chrome and most Apple devices
Ars Technica: Researchers at Google's Threat Analysis Group, which investigates government-backed hacks and cyberattacks (think spyware), said it has evidence that bugs found in Google Chrome and nearly all Apple devices are being actively exploited. Google patched the Chrome bug in four days, and Apple in about a week, per @maddiestone. Update your Chrome browser (close, and reopen) and patch your iPhones, iPads, and Macs today.
~ ~
OTHER NEWSY NUGGETS
Knock knock, who's there? Lol, jk, we've been here for years: A prolific espionage group with links to China spent at least two years looting the corporate systems of chipmaker NXP, which manufactures chips found in phones, smartcards, and electric vehicles. NXP said there was no "material adverse effect" on its business. News of the breach was reported this week, some six years after the breach was discovered towards the end of 2017. (via NRC ($), Ars Technica)
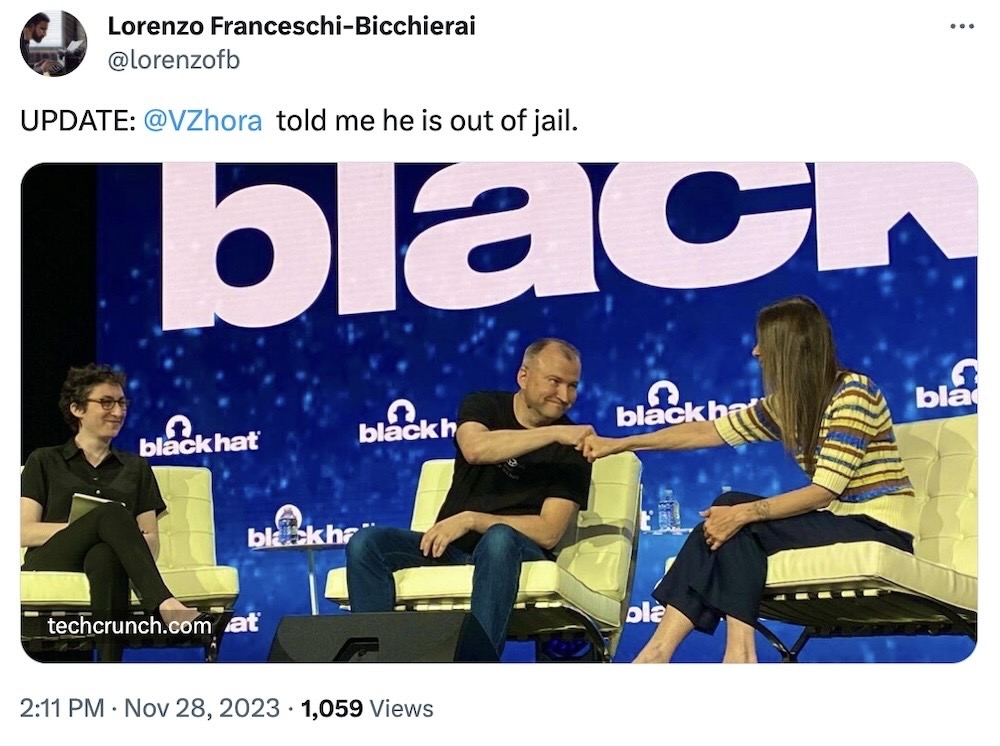
Ukrainian cyber official bailed: Ukrainian authorities briefly detained former senior cyber official @VZhora, who officials accused of embezzling state funds. In a brief press release, Ukraine's anti-corruption court said it detained the former deputy — though not directly naming Zhora — and set the bail at about $270,000. Zhora later told @lorenzofb that he was "out." (via TechCrunch, @lorenzofb)
No new NSA boss until DOD 'fesses up: There will be no new director of the National Security Agency until the Department of Defense answers whether or not it purchases commercially available location and browsing data (without using a warrant) of Americans. Sen. Ron Wyden is blocking the nomination of the new NSA director until he gets answers. The implication is that DOD does buy location and browsing data from data brokers, since at least one other DOD agency, the DIA, confirmed that it does. (via Ron Wyden, @charlie_savage)
Okta breach impacted a lot more than 1% of customers: A belated update to Okta's data breach notification of its customer support system confirms that every customer support user had information taken in the breach, not 1% as the company had previously reported. Most of the information included names and email addresses, but other records had more data. Interestingly, Okta disclosed that about 6% of its customers don't use MFA on their Okta administrator accounts, which seems bizarre that MFA isn't mandatory. (via Wired ($), Bloomberg ($))
British Library hacked, outage expected to last 'months': The national library of the U.K. said that user data was stolen by hackers, as its ongoing outage — thought to be a ransomware attack — continues on into its fourth week. The British Library previously said user data wasn't affected. It's not known how many users are affected by the breach, which includes some personal information. Now it says the disruption to its services is expected to "persist for several months." (via TechCrunch)
~ ~
THE HAPPY CORNER
Welcome to the happy corner. There's just enough time for a light sprinkling of good news.
A few months ago, I noted that @uuallan was working on a comic-book reboot of Yours Truly, Johnny Dollar, featuring Dollar as a modern-day cyber insurance investigator fighting back against ransomware. Well guess what arrived in the post this week! I cannot wait to get stuck in. (As an aside, the print and paper quality is exquisite.) Congrats to Allan and team. You can check out their website, and Kickstarter to support the second issue.

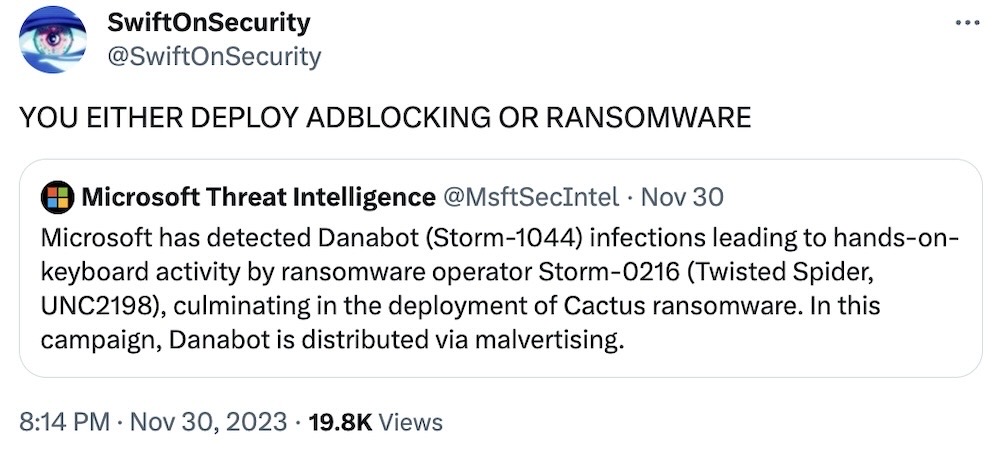
Speaking of ransomware, listen to your neighborhood IT admin. Ad-blockers are your friend, and don't let anyone tell you otherwise. uBlock Origin is pretty great.
Finally, this week, bonus cyber cat.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
~ ~
CYBER CATS & FRIENDS
Meet this week's two-for-cat cyber-kitten special, Milo and Mabel, who are cyber cats in training. Give it time and they'll be excellent threat hunters. Many thanks to gh0sti for sending in!

Send in your cyber cats! Drop me an email with your cyber cat (or non-feline friend) with their name and photo and they'll feature in an upcoming newsletter.
~ ~
SUGGESTION BOX
Another busy one — thanks for sticking around for this bumper edition. I'll be back next Sunday with the usual round-up from the week. As always, I'm reachable by email — let me know if you have any feedback!
Enjoy your week. See you next,
@zackwhittaker