this week in security — december 4 edition
THIS WEEK, TL;DR
Spyware maker Variston exploited Windows, browser zero-days
Google: Google's threat hunters obtained a set of exploitation frameworks designed to target Chrome, Firefox and Windows Defender in order to plant spyware, which they say belongs to Barcelona-based commercial surveillance vendor Variston. The code obtained by Google contained clues (likely inadvertently) including a script that was designed to remove references to Variston and its developers from the final binary, suggesting it was behind the exploits (see below). When reached, Variston's director Ralf Wegner said he hadn't seen Google's findings but didn't deny the claims either. The bugs are now fixed. Remember, there's a whole world of spyware outside just NSO... speaking of, the U.S. State Department said this week it's committed to the "proliferation of foreign commercial spyware," but says nothing about the ones at home.
More: TechCrunch | New Yorker ($) | Wired ($) | Cyberscoop | @jsrailton
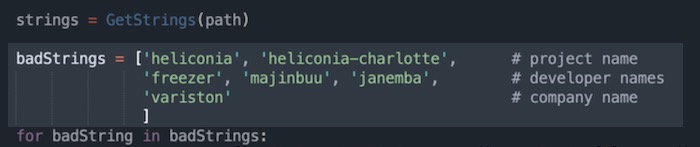
LastPass hacked for the second time this year
LastPass: Password manager LastPass said it was breached for a second time this year — months after its developer environment was compromised. LastPass said this time the "unauthorized party" (we can probably assume it's a cybercriminal at this point) broke in using information they had stolen from its first breach in August. Clearly something went wrong in remediation, or exposed keys or credentials weren't revoked, because this time the attacker was able to break into its cloud storage and obtain "certain elements of our customers' information" from its servers, but has so far refused to say what (or even if it knows) what customer data has been stolen. LastPass' parent company GoTo also uses that shared storage and confirmed in a blog post that it was investigating. But if you didn't see that blog post, that was by design, since GoTo hid the breach notice from Google's search index. (GoTo eventually dropped the code from the blog, so now it's showing up.)
More: TechCrunch | The Register
Android phone makers' encryption keys used in malware
Wired ($): It's never good when private keys are leaked or stolen, but even worse when they're reused for malware. But that's what happened with Android device makers Samsung and LG. @maldr0id found that "platform certificates" used to verify legitimate third-party Android system apps developed by device manufacturers like Samsung and LG had been stolen and used to sign malware, essentially allowing malware to run as if it was a highly privileged Android system app. Not good! Google said the Android device makers had rolled out mitigations and rotated their keys, ending the threat. There have been "no known security incidents," Samsung said, with an emphasis on "known." That's more than what LG said, which was sweet nothing.
More: Chainguard | Chromium Bugs | @mandr0id
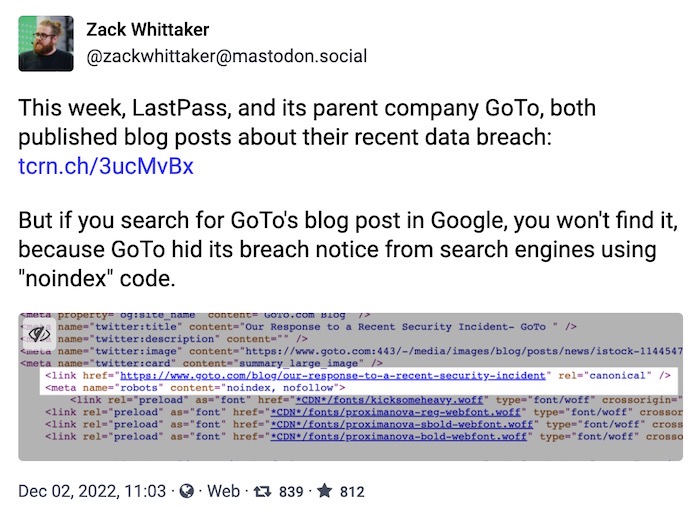
Researcher says Eufy cameras aren't as local-only as it claims
The Verge: Anker's Eufy smart home cameras promise that they'll store your data locally. Your video footage "never leaves the safety of your home," and is only transmitted to your phone via end-to-end encryption, with no way for Eufy to access the data. Except, @Paul_Reviews and The Verge found that it was possible to access a Eufy stream from the other side of the country using VLC Player on someone else's network, with no encryption. Both presented compelling evidence of their claims, even if Anker largely denied (and ignored) key claims. Something weird is definitely going on, but it sounds like Eufy's lawyers are already engaged, so make of that what you will.
More: Ars Technica | @Paul_Reviews
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Hacking back against Instagram phishers
@Hipotermia: Follow @hipotermia down a path of how a friend was targeted with an Instagram phishing page, and stay for how they dug around, compromised the site and deleted the attacker's data. That's one way to get even. The full thread is worth the read.
Don't use Hive, say researchers who found critical flaws
Zerforschung: Following the exodus from Twitter, many have migrated to Mastodon (find me here) and the far, far newer Hive, another popular social platform. But researchers this week say they found "a number of critical vulnerabilities" that allowed them to modify, edit and delete "all data" on Hive, including private email addresses and phone numbers. Here's a demo of the bug in action. In response, Hive pulled its servers offline for now.
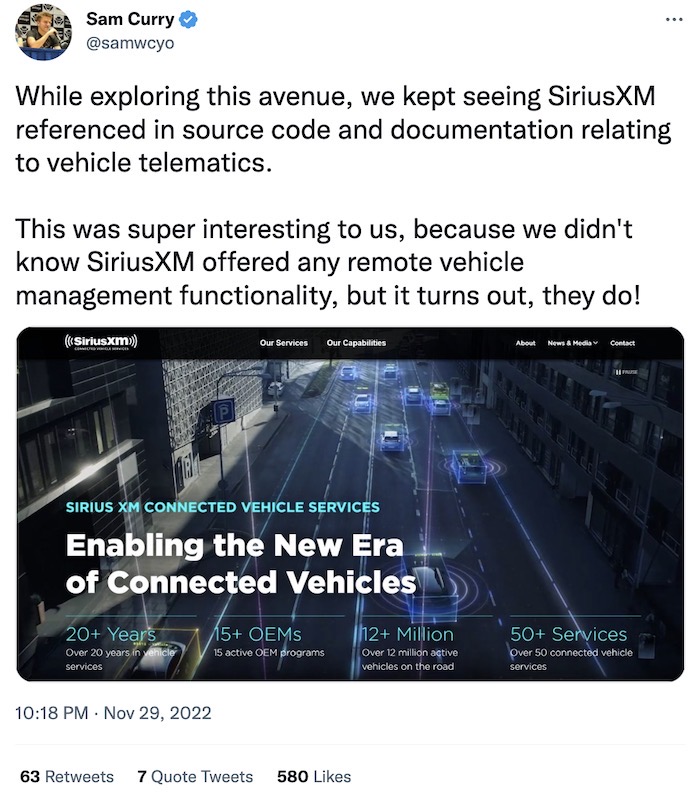
Researchers find bugs allowing access, remote control of cars
The Record: Not a great week for car makers. @samwcyo and team discovered two sets of flaws — one affecting Hyundai and Genesis cars and another affecting Honda, Nissan, Infiniti and Acura vehicles. The bugs allow remote access and control over thousands of cars made after 2012. The Record consolidates the bugs one place (and more from SecurityWeek, too). The second batch of flaws were particularly interesting as they all involve upstream telematics and broadcasting company Sirius XM, which could allow an attacker to remotely fully manage a vehicle by exploiting the app. That's because SiriusXM is baked into many modern vehicles. ("So many brands under one roof!" remarked @samwcyo.) Forbes ($) brings this all together by looking at how police can use this broad level of remote access to vehicles' data to obtain warrants for car data, like location data.
ConnectWise fixes bug abused by phishers
Cybir: You might not have heard of ConnectWise, but it's big in the IT industry. ConnectWise offers a self-hosted, digitally signed remote desktop app that is used by MSPs to allow instant remote access to another network with a single email click. That's by design, but phishers caught wind of this attack mechanism to bounce the connection through an attacker's ConnectWise control server. In short, it makes breaking into usually-walled networks far easier. ConnectWise fixed the bug. The full technical write-up is worth the read, while @briankrebs has a good explainer for normies like me.
~ ~
OTHER NEWSY NUGGETS
How Russia is spying on Telegram in Ukraine: @PwnAllTheThings has a solid half-explainer, half-analysis of a Washington Post ($) report that broke last month. The short version is that Russia is able to surveil individuals using Telegram, the messaging app known to have janky encryption. How? Metadata! The full post is really worth the read. If there's ever been a reason to use Signal... (via @PwnAllTheThings)
U.K. water supplier hacked: Not a great week for the 1.7 million customers of South Staffs Water and Cambridge Water in the U.K., whose parent company has confirmed a breach of customer bank details — though it's not saying how many customers are actually affected (assume the worst). The water supplier is just coming clean now, months after the alleged ransomware hit its network in August, which we know because the ransomware group in question, Cl0p, claimed at the time that it had hacked the wrong victim. (via BBC)
ICE in hot water: U.S. immigration enforcement accidentally released the identities — including names, nationalities and detention locations — of more than 6,200 immigrants who have fled torture and persecution and are seeking asylum to the United States. ICE said that the exposure was caused by a "routine" website update and lasted five hours. A Homeland Security official told the Los Angeles Times that the disclosure was potentially dangerous for those affected. Immigrant advocacy group Human Rights First first notified ICE of the data breach. (via Los Angeles Times ($))
CommonSpirit finally notifies of ransomware attack: The second-largest non-profit hospital chain in the U.S. says a ransomware attack allowed cybercriminals to make off with personal information of its patients. In a disclosure (finally...), CommonSpirit declined to say how many patients were affected, but said the attackers were in its network for more than two weeks in September and October. So, about as transparent as mud on a foggy night. (via DataBreaches.net)
~ ~
THE HAPPY CORNER
OK, now that the serious stuff is out of the way, here's the happy corner.
Shout out to the hacker who played the long game here by getting "Hey, Google" broadcasted to thousands of households. Runner up to anyone who gets "Alexa" or "Siri" in their handle, since this requires some real dedication. (via @hacks4pancakes)
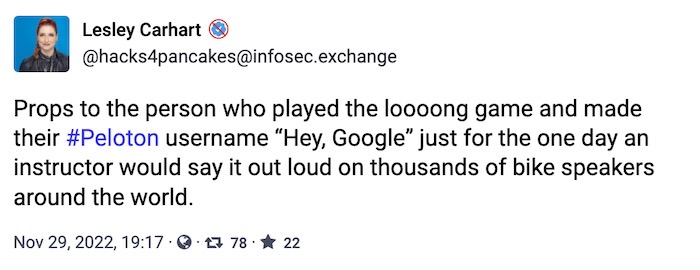
Meanwhile... no, I don't think they do.
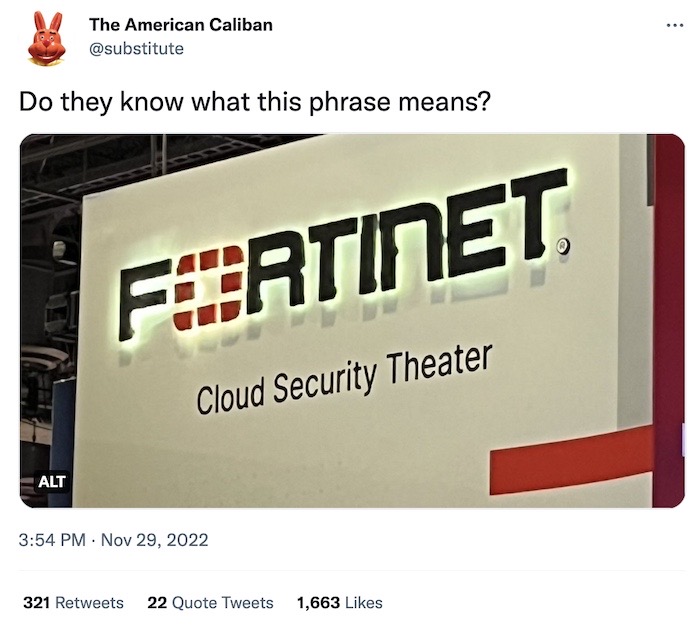
Next up this week. Can an artificial intelligence chat bot be programmed to write sarcastic data breach notices? Turns out yes, yes it can.
And finally. Huge congratulations to @kimzetter who is the new visiting scholar at The Alperovitch Institute at Johns Hopkins School of Advanced International Studies, and will join @ridt to co-teach a course on intelligence and cyber operations starting next month.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Charlie, who as you can see is in the loaf position, sitting on his human's arms while they work. Not sure if this is the first ever cat-on-a-man-in-the-middle attack? Many thanks to Dann T. for sending in!

Please send in your cyber cats (or their friends). Email me a photo and their name, and they'll be featured in an upcoming newsletter. Submitted before? Send an update!
~ ~
SUGGESTION BOX
Thanks so much for reading this week's newsletter! I will be back in a couple of weeks as I will be away next week. My partner and I are taking a short vacation to celebrate the launch of her book So When Are You Having Kids? which is out this week. It was the book we needed when we started out on our journey to have a family, and so she wrote it — a modern family planning book for anyone who isn't yet sure if, when, or how they want kids. It's an incredible, deeply researched feat of work, and I couldn't be more proud of her.
In the meantime, feel free to drop any feedback in the suggestion box or email me. And don't forget to send in your holiday season-themed cyber cats (or their friends!).
Take care, and see you soon,
—@zackwhittaker