this week in security — february 12 edition
THIS WEEK, TL;DR
Ransomware attack targets VMware ESXi servers worldwide
Bleeping Computer: Attackers are actively exploiting a remotely exploitable bug in VMware ESXi servers, which was patched some two years ago, but is wreaking havoc this week after attackers found a way to mass-deploy ransomware. ESXi servers are hypervisors, which pack in multiple virtualized computers onto a physical server; great for datacenters and saving space. The bug can be exploited without authentication, meaning no passwords or secrets are needed to hijack an unpatched ESXi server from over the internet. The number of affected servers is fluctuating from hundreds to thousands. While not a zero-day bug, this particular flaw shows that even the bigger cloud hosting companies aren't patching their gear when they should have been. The good news is that the ransomware itself is (or was) crap, so CISA has a fix that might work to recover data in some cases, though not all. The attackers have since fixed their flawed file-encrypting algorithm. Rapid7 has some good remediation advice.
More: VMware | CISA | CISA on GitHub | The Register | @vmiss33 | @ransomwhere tweets | @GossiTheDog toots
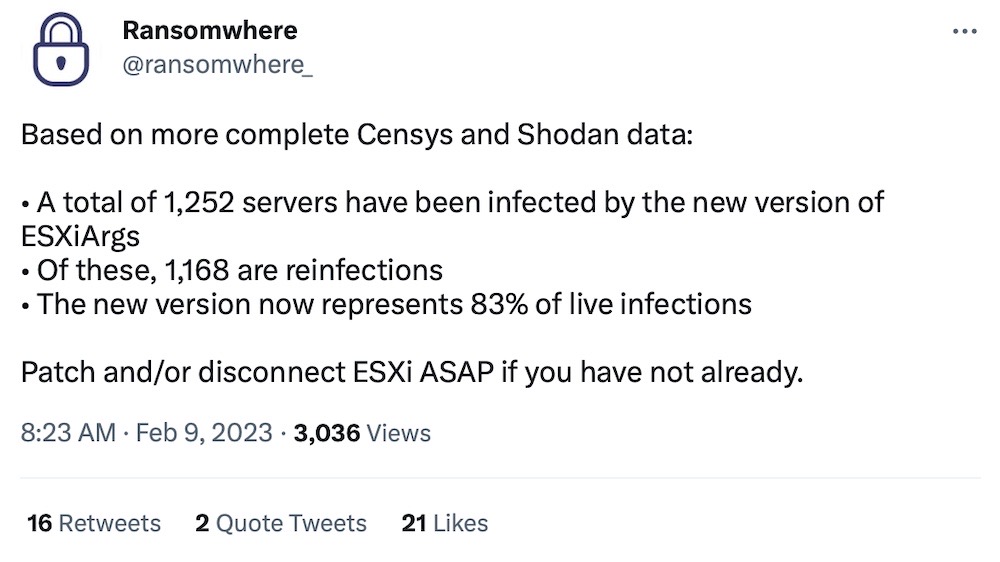
Several Russians sanctioned over links to Trickbot, Ryuk ransomware
CNN: U.K. and U.S. authorities have sanctioned seven Russian individuals who they accuse of having central roles in Trickbot, Conti and Ryuk groups, which the U.K. and U.S. are saying are part of the same criminal organization, and are linked to Russian intelligence. The criminals have extorted $180 million in ransomware demands in 2021 alone, causing disruption to government, hospitals, and businesses. By sanctioning the individuals behind the operations, it'll make it far more difficult for them to evade sanctions by just rebranding — plus, they will be wanted as soon as they step foot out of Russia. No more secret vacations! In other fun related ransomware news, the U.S. and South Korea took action against North Korean ransomware, which has long used ransomware proceeds and cryptocurrency to fund its nuclear weapons program.
More: BBC News | NSA | @silascutler | @jipe | @joetidy tweets
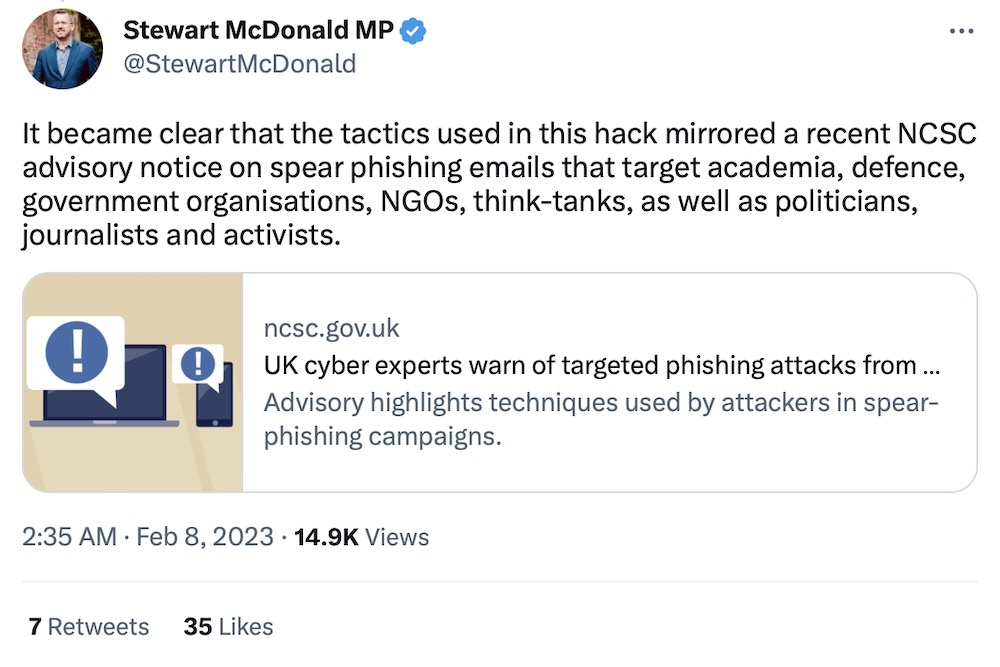
Russia-linked Cold River hacks U.K. lawmaker's emails
BBC News: The Russia-backed hacking group known as Cold River (or Seaborgium, if you follow Microsoft's naming scheme) is back with a new hack-and-leak operation, this time targeting a U.K. lawmaker known for his close interest in Ukraine. The BBC has the full scoop, and it's worth the read. Cold River has targeted nuclear scientists, a former U.K. spy chief, and lawmakers as part of a wide effort to obtain information from individuals with perceived access — including journalists. The U.K. recently warned about Cold River.
More: U.K. National Cyber Security Centre | TechCrunch
FBI's most controversial surveillance powers are under threat
Wired ($): Wired takes a look down Section 702 memory lane at some of the recent times the FBI spied on Americans without a warrant, in some cases inadvertently, but other times very much deliberately. Section 702 (named for its place in the law books) are the legal powers that allow the NSA and the FBI to intercept electronic communications of non-Americans overseas. But, to spy on one foreigner's messages might incidentally also collect the communications of an American — such as if the two are chatting online. These powers were put under the spotlight back when Edward Snowden gave thousands of classified docs to journalists... ten years ago (yikes, time flies!) but little has legislatively changed since. Now, those Section 702 powers are up for renewal this year, and now with Republicans leading the House, we're set for a showdown that could see the FBI's crown jewels reined in. Also read @jkosseff, who has a sensible and reasoned take in Lawfare on what needs to change. (Ahem, we're looking at you, FBI.)
More: Wall Street Journal ($) | @jkosseff tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Reversing U.K. mobile rail tickets
eta: For a moment, read this and get super nerdy with this excellent post on decoding U.K. railway tickets. She has a really interesting read on how to reveal the information from a train ticket — and with a real-world demo site to play with. Interestingly, all U.K. train tickets are signed with public keys so there's no practical danger of forging tickets en masse. (I'm a British native, so this is very much my jam.)
China's top Android phones collect way more info
The Register: To absolutely nobody's surprise whatsoever, Android devices bought in China are crammed with preinstalled apps that transmit privacy-sensitive data without the user's consent or notice, even when the phones travel to countries or regions with stricter privacy laws. The data includes location identifiers, phone numbers, social connections and app telemetry. You can read the research here.
An apparent leak of Booking.com reservation data is used to scam customers
Ars Technica: For years, Booking.com customers have been plagued by scams that clearly show criminals have somehow obtained travel plans and other personal information that customers provided to the travel site. You could be forgiven for being skeptical, but @dangoodin does a splendid job following five years of threads directly back to Booking.com's front door. Booking.com isn't taking any responsibility for the apparent insider in its network, leading to one simple but necessary conclusion: "Until Booking.com comes clean, people would do well to book travel using a different site."
EFF infiltrates 'Dark Caracal' APT group
Electronic Frontier Foundation: Incredible work by EFF's @cooperq, who found that a government-backed threat group known as Dark Caracal, highly active in Latin America, did not register a domain used by one of its back-end command and control servers — so the EFF registered it. By sinkholing the domain, the EFF could get a real-time view into the hackers' actions, and was shown to have between 600-800 infected machines at any one time. It's not clear if the group is even aware that its domain was effectively snatched from under its nose. Whoops! More at TechCrunch by @lorenzofb.
~ ~
OTHER NEWSY NUGGETS
No encrypted phone for you, guv'nor: The U.K. Home Office wants to make [PDF] the sale and possession of "bespoke" encrypted phones for the purposes of committing a crime a criminal offense in itself. The idea is that the proposed law would target organized criminals that use encrypted phones to hide their illegal activities, like Anom, Sky and Encrochat. Just one problem: the proposal is incredibly vague and nobody's sure what "bespoke" even means or what a ban would look like — and even then, critics argue there are legitimate uses for encrypted phones. Wild stuff. (via Motherboard)
Australia rips out Chinese cameras: More than 900 products made by Hikvision and Dahua — two Chinese surveillance companies under sanctions for supplying their surveillance technology to detention camps holding millions of Uyghurs — will be removed from Australian government buildings over security concerns. That's because of fears that Hikvision, a known maker of torture/restraining devices, also poses an espionage fear over its links to the Chinese government. That's a pretty big job, since there are some 250 government buildings with Hikvision and Dahua cameras. (via The Guardian)
Netflix crackdown extends: Canada, New Zealand, Portugal and Spain are next in line to face new password sharing limits on Netflix accounts. Customers will have to pay an extra fee if they want friends and family who don't live with the account holder to access their subscription. More in a Netflix blog post. (via BBC News)
Taiwan fines iRent for data spill: The Taiwanese government didn't waste a second investigating car renting and ride-sharing giant iRent after it left thousands of customers' data exposed for months, and ignored my requests (disclosure alert!) for a week to take the data down. The government intervened, and the data was eventually secured. Now, in its aftermath, Taiwanese authorities issued two separate fines to iRent — and the country's vice premier vowed to change the country's laws to vastly increase fines for companies that violate its data protection and privacy laws. (via @PogoWasRight)
Reddit phished, customer data 'safe': Reddit said it was hit by a brief intrusion, allowing hackers access to production systems, contact information of current and former employees, and some advertiser information. No customer data was accessed, the company said. Reddit's CTO Christopher Slowe blamed an employee, calling humans the "weakest part of the security chain." That misplaced blame drew sharp rebuke from @konklone, who rightfully pointed out that it was absolutely the company's fault for not using phishing-resistant MFA, since they can't be remotely phished. Case in point: Cloudflare, which fended off intruders because it uses security keys. (via TechCrunch)
Weee! But booo: Online grocery delivery startup Weee! was hacked, the company said in a scant data breach notice this week. A year's worth of data was stolen, the company said, for anyone who placed an order between July 12, 2021 and July 12, 2022. A seller on a known cybercrime forum is offering the data, allegedly containing 11.3 million orders and 1.1 million unique email addresses. You can check if you're affected via Have I Been Pwned. (via The Record)
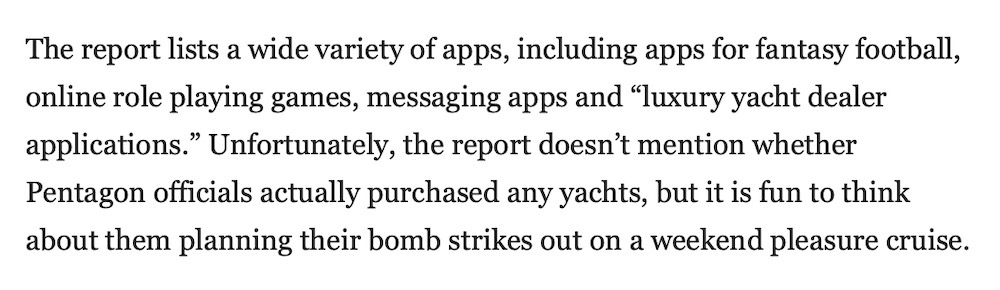
Pentagon employees 'too horny' to follow security protocols: A Pentagon watchdog report released this week found that Dept. of Defense employees are using banned and unauthorized apps to hook-up, watch TikToks, and buy cryptocurrency on government phones and devices. Some of the apps have "known cybersecurity risks, operational security risks," and could expose device access to contacts, location data, and photo libraries, which may contain sensitive government or military information. Plus, I can't not mention this golden line of copy: (via Gizmodo)
~ ~
THE HAPPY CORNER
Happy Sunday to all those who celebrate. It's the happy corner.
Ransomware is hard! And the Clop ransomware group is finding out the hard way after researchers found that its latest Linux-targeting variant is flawed, reports SentinelOne. As such, there's a free decryption tool available for anyone hit.
Google is dishing out 100,000 phishing-resistant security keys to help at-risk individuals stay protected ahead of the 2024 U.S. elections and other democratic events.
And your final moment of wisdom for the week.
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber-cat duo, known only as the Cyber Red Team, according to their human. They look like they've seen some things... incident response is no joke. Many thanks to David C. for sending in!

Send in your cyber cats! (You can send in your non-feline friends too.) Email me a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And we're out — thanks for reading! As always, you can email me or drop your feedback in the suggestion box. Oh, and if you haven't perused this newsletter's Patreon recently, have a gander. I still send out mugs and stickers!
Take it easy, and see you next time.
—@zackwhittaker