this week in security — february 13 edition
THIS WEEK, TL;DR
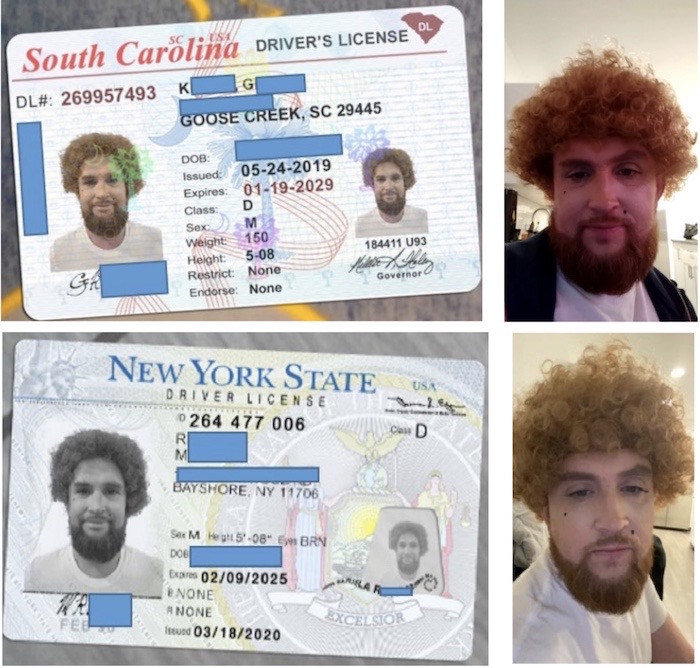
IRS abandons facial recognition plan after firestorm of criticism
Washington Post ($): And just like that, plans by the IRS to use third-party identity verification ID.me have been pulled after a "firestorm of criticism." (AP has a non-paywalled story.) The planned roll-out of ID.me on the IRS' website was meant to take effect later this year, but critics say the service would amass a huge database of identity documents that could be targeted. Senate Finance chair Ron Wyden said bluntly that "no one should be forced to submit to facial recognition to access critical government services," which seems entirely fair. After all, the tax-collection service is a taxpayer-funded service. Meanwhile, the Post notes just how problematic the ID.me service can be, after scammers found a way to trick the company into accepting fake face scans (see below, and yes, it's a wig). ID.me also collects location data and uses Palantir's software to process it.
More: Internal Revenue Service | Washington Post ($) | ZDNet
Microsoft's small step to disable macros is a huge win for security
Wired ($): Macros are, and have been, a major thorn in the side of network defenders for a decade-plus. While these little bits of programmable code are helpful for automating tasks, they're also great for planting malware, and these days are said to account for about 25% of all ransomware entry routes. Now, Microsoft said it will block internet macros by default in Office, making the macro attack route far more difficult. Microsoft is taking what @lilyhnewman calls a "diplomatic approach" by blocking macros in documents that have been downloaded from the internet, while allowing macros in spreadsheets and documents that have only been shared on an internal network and have never moved across the internet.
More: Microsoft | The Verge
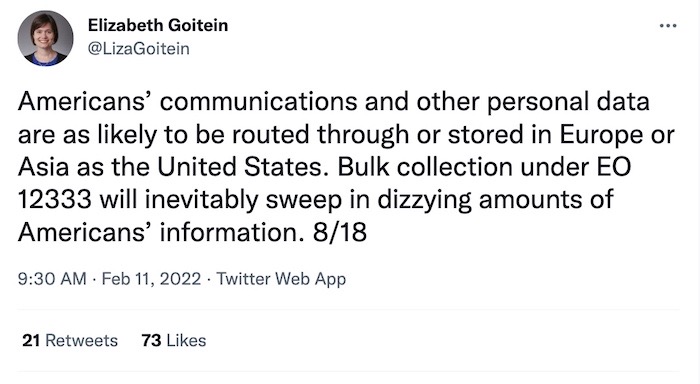
Lawmakers allege 'secret' CIA spying on unwitting Americans
BBC News: The U.S. government is still spying on Americans, according to two senators who went public this week. Sens. Wyden and Heinrich, who sit on the Senate Intelligence Committee, said the CIA is secretly collecting data on Americans, years after the NSA was caught out doing much of the same thing. We don't know what the CIA is collecting or why. But, what's important here is the authority that's used, an executive order (EO) called 12333, which is the government's catch-all authority for secret collection of data. It's complicated, but read this thread from national security expert @lizagoitein for more. The CIA's data collection apparently skirted accountability for years using this authority. It was only last month that the senators found out for themselves; apparently the program was "withheld even from" the senators on the Intelligence Committee, which oversees these programs! This will be a story to watch...
More: Sen. Ron Wyden | Wall Street Journal ($)
Decryptor released for Maze, Egregor, and Sekhmet ransomware strains
ZDNet: Some good news this week after the master decryption keys for three ransomware strains, Maze, Egregor, and Sekhmet, were published, allowing the creation of decryption tools. The keys were posted on a forum used by Bleeping Computer. It seems like the linked gangs, which are no longer active, are rattled by recent events — including U.S. threats to find ransomware actors and Russia's unexpected arrests against REvil. Maze, if you recall, was one of the first gangs to publish stolen files, rather than just encrypt them.
More: Bleeping Computer | Emsisoft
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
U.K. Foreign Office calls in ‘urgent support’ after cyber incident
TechCrunch: The U.K. Foreign Office, tasked with handling Britain's foreign and international affairs, called in BAE Applied Intelligence as cyber-reinforcements after a reported "serious cyber security incident." The government department wouldn't say what happened, and the incident was only revealed by the public contract requesting assistance. Per the BBC's @gordoncorera, there was a breach of the Foreign Office's systems but that it was detected, and that classified systems are said to be unaffected. Another story to keep an eye on, clearly...
France says Google Analytics breaches GDPR when it sends data to U.S.
The Register: France's data protection authority, the CNIL, says Google Analytics is in breach of Europe's GDPR regulations because it transfers European citizens' data to the United States — and therefore in reach of the U.S. intelligence services. The CNIL said these transfers are "illegal," and ordered an unspecified French website manager, which was at the center of the case, to stop using the service. The decision only applies to France, though the decision comes a month after Austria came to a similar ruling.
~ ~
OTHER NEWSY NUGGETS
Inside the numbers of 2021's cyber mergers, acquisitions and investments
Cyberscoop: For a quiet year of pandemic recovery, security investment and M&A saw record-breaking growth. New data from Momentum Cyber shows M&A activity was up almost three-fold in 2021 compared to the year earlier, some $77.5 billion. Some eye-watering numbers in here for the startup watchers.
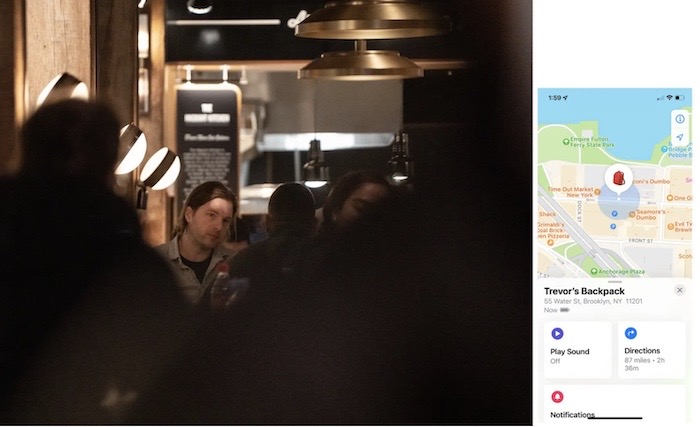
Apple makes changes to AirTags amid stalking concerns
The New York Times ($): Apple is making changes to AirTags, after numerous reports that these button-sized trackers were being used for stalking and following people without their consent. Case in point, though consent was granted, @kashhill planted several location trackers on her husband to see how easy it would be and what, if any, safeguards exist to protect would-be victims. It's a great story that exposes just how ripe for abuse these tracking services can be.
EARN-IT aims to protect children online, but reignites privacy and speech concerns
Washington Post ($): Senators have advanced the highly controversial EARN-IT bill through committee this week, putting the bill up for a potential vote on the Senate floor. The bipartisan bill aims to hold tech companies accountable for posts that exploit children by stripping the companies of legal protections. But critics say the bill could have unintended side effects, such as discouraging companies from deploying encryption that protects people's private conversations, says @Riana_Crypto. It could also have a chilling effect on free speech, some warn.
Why have 14 of 15 U.S. cabinet departments bought phone unlocking technology?
The Intercept: Nearly all U.S. cabinet departments have bought Cellebrite's phone hacking tools, according to new findings from The Intercept, including the U.S. Fish and Wildlife Service and the Centers for Disease Control and Prevention (CDC). Critics are concerned that the agencies aren't properly drawing up guidelines on what to do with the data once it's collected.
~ ~
THE HAPPY CORNER
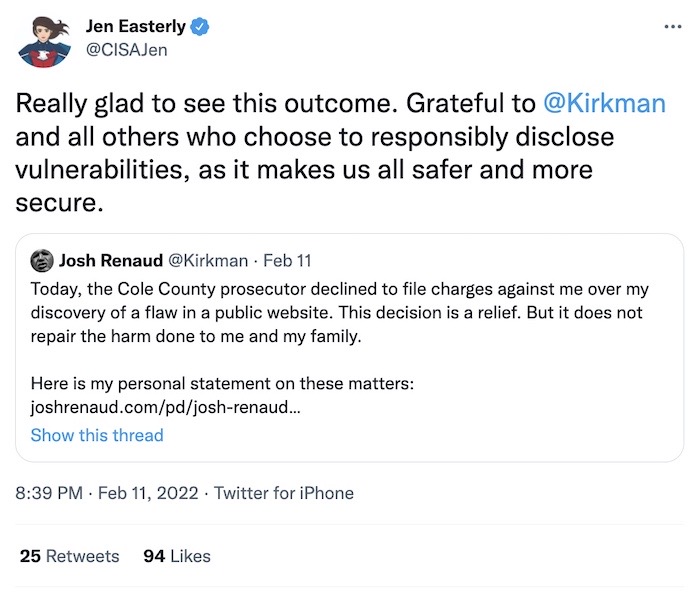
This week saw the end of a long-running saga we have covered in this newsletter. The prosecutor for Missouri's Cole County has declined to file charges against a St. Louis Post-Dispatch developer and journalist Josh Renaud, who found a ton of state educators' private information exposed on a state government website and ethically reported it to the state. Gov. Mike Parson threatened to prosecute Renaud for doing journalism, apparently, and used it to score political points. Glad this ordeal is over, but furious it ever happened to begin with.
And, lastly: In a day and age where politicians are threatening to withhold funds from a public library if LGBTQ+ books are removed, you can trust your friendly neighborhood furries to save the day and raise over $100,000 for the library. Look, I try not to get overly political in this newsletter but maybe the folks who are trying to ban the books would be better off actually reading them. This whole tweet thread is absolutely worth your time.
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is a two-for-one kitten special (my favorite kind). Meet the four-month-old kittens, Calliope and Piper, who according to their human are excited to interrupt future livestream recordings. You just wait until they discover your keyboard, then it's really game over! A big thanks to Jon M. for the submission!

Keep sending in your cyber cats (or their friends)! You can drop me an email here with their name and photo, and I'll make sure they're featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for now. As always, the suggestion box is open, or feel free to drop any feedback to this@weekinsecurity.com. Hope you have a great week and see you next Sunday.