this week in security — february 14 edition
THIS WEEK, TL;DR
Hackers try to poison Florida town's water supply after computer breach
Reuters: What a wild story this was: a hacker broke into a system that treats the drinking water supply for a small town near Tampa and cranked up the lye (sodium hydroxide), almost poisoning some 15,000 people. The local sheriff announced the breach at a press conference. Turns out the town was running TeamViewer on a system that controlled the lye. Wired ($) has a good tick-tock of the attack. The fact that a hack was able to get into such a sensitive system is alarming, but Cyberscoop said the blame lies at the lack of funding and cyber resources at the local level, sparking concern by other state governments like Massachusetts, which sent alerts to state water facilities warning them to take basic security precautions. No word on who the culprit may've been: some are pointing to an insider (or former, disgruntled insider), but this breach has all the hallmarks of both a kid on Shodan and a nation state, so really it's anybody's guess.
More: Wired ($) | Motherboard | Cyberscoop | Mass.gov | @snlyngaas
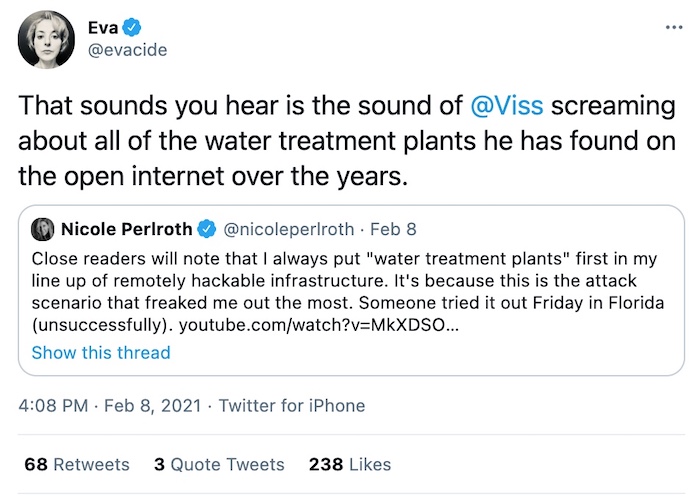
Google boots location data broker that sold Muslim prayer app user data
Motherboard: Another company banned from Google's app store thanks to @josephfcox's reporting. Predicio is a data broker that was selling location data from Muslim prayer apps, and is part of a supply chain linked to U.S. immigration authorities. Motherboard has been digging into particular data brokers with links to the government and the military, including X-Mode. This ban isn't just on the apps but the company itself, potentially having a devastating effect on its bottom line. Google is increasingly pushing back on these particular companies with governmental relationships. In the end, it's a major win for Android users' privacy.
More: @josephfcox
How a supply chain attack let one researcher hack into Apple, Microsoft and more
Alex Birsan: Speaking of complex supply chains, here's an attack that saw @alxbrsnz breaking into dozens of companies by hijacking dependency names. The post is well worth the read and explains step by step how this supply chain attack works. But in short: "Squatting valid internal package names was a nearly sure-fire method to get into the networks of some of the biggest tech companies out there, gaining remote code execution, and possibly allowing attackers to add backdoors during builds." Really incredible work here and well worth the bounty payouts.
More: ZDNet | @doctorow tweets
The long hack: How China exploited a U.S. tech supplier
Bloomberg: *heavy sigh.* This again. I defer to this @pwnallthethings thread, who provides close to line-by-line annotations of Bloomberg's second attempt on this story.
More: @ericgeller | @lukOlejnik
Virginia is about to get a major California-style data privacy law
Ars Technica: Love it or loathe it — and plenty do — Virginia is on deck to see major changes to its state privacy laws, giving residents similar access to their data that California residents currently enjoy under CCPA (and Europeans under GDPR). The EFF criticized the bill as one with "almost no teeth," and pointed out several major flaws. Ars also does its usual teardown of the law; certainly worth reading if you're a Virginia resident, but also noteworthy that several other states are pushing for similar laws.
More: Washington Post ($) | EFF
Cyberpunk 2077 Maker was hit with a ransomware attack — and won't pay up
Wired ($): Hackers hit Cyberpunk 2077 game maker CD Projekt Red with a ransomware attack, and are threatening to publish the stolen source code if the demand isn't paid. That ransom payout is not likely to happen, since the company confirmed it's not coughing up. It's believed the ransomware was called HelloKitty, which was recently deployed at a Brazilian power company.
More: Motherboard | Ars Technica
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Browser 'favicons' can be used as undeletable 'supercookies' to track you
Motherboard: Browser favicons are helpful to know which website is amid an ocean of tabs, but one researcher now says these tiny browser icons can be abused to track you across incognito windows, VPNs, and more. Researcher Jonas Strehle created a proof-of-concept on GitHub that can trick a browser into turning over information about the browser when it needs a new favicon. "When the website is reloaded, the web server can reconstruct the identification number with the network requests sent by the client for the missing favicons and thus identify the browser." Fascinating stuff.
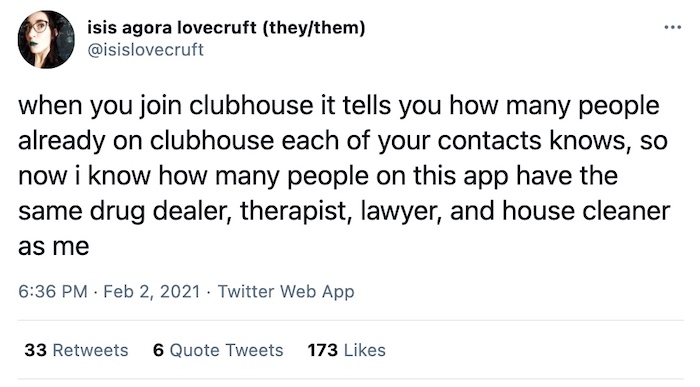
Clubhouse is suggesting users invite their drug dealers and therapists
OneZero: In case you don't know, Clubhouse is an audio-only social network that relies on your phone number to log in and your contacts to share invites. I think Clubhouse is cool, but demanding access to your contacts is a terrible idea — unless the goal is to rapidly grow a social network from nothing to something in a short space of time(!). @WillOremus walks through the privacy issues associated with uploading your contacts list, which inevitably includes examples such as doxing your therapist and your drug dealer as good reasons why you shouldn't. @wbm312 has already put in a request under CCPA for her data from the company. That could be fun to keep an eye on.
Anne Neuberger will oversee the SolarWinds recovery effort
@TonyaJoRiley: A press release from the Senate Intelligence Committee this week welcomed the news that Anne Neuberger, former NSA cybersecurity director, member of the Russia Small Group, and now de facto NSC cybersecurity chief, to lead the administration's response to the SolarWinds breach, attributed so far to the Russians. It comes after the lawmakers pressed the administration on who exactly will be running point on the recovery, since last week it was apparent that there were far too many cyber-cooks in the cyber...kitchen? I'm bad at metaphors, but you get the idea.
This famous router is loved by hackers
Tedium: A blast from the past from @ShortFormErnie on the Linksys WRT54G, a popular router used by hackers all over the world, and was for a time the router of choice in my first house out of university (though admittedly not for the same reason). A bit late on featuring this but it's a great read on why the Linux-based operating system that powered the router was so important, and how the company was effectively forced to release open-source code for the router under the Linux license, sparking the creation of OpenWRT and Tomato firmwares and others.

Hacked therapy centre Vastaamo goes into liquidation
Yle: You may remember a few weeks back that a Finnish therapy center, Vastaamo, was hit with ransomware and the hackers threatened to release (and subsequently did) hundreds of private medical files of individuals who sought therapy. (Wired ($) has a great explainer; BBC News does too). According to @mikko, the organization has declared bankruptcy as a "direct result" of getting hacked, joining only a few companies that have shuttered as a result of a breach.
Proofpoint sues Facebook to get permission to use lookalike domains for phishing tests
ZDNet: Email security firm Proofpoint has sued Facebook in order to use a lookalike domain for phishing tests. It's not a huge surprise, since Facebook aggressively goes after domain typosquatters who deliberately try to ensnare Facebook users. What makes Proofpoint any different? It'll be an interesting case to watch. Credit to @seamushughes who discovered the court filing first.
~ ~
OTHER NEWSY NUGGETS
How Let's Encrypt prepared to issue 200 million certificates in 24 hours
Here's a great writeup from Let's Encrypt, the free TLS certificate provider, on how it issued over 200 million certificates in a single day, because of a bug it traced back to February 2020 that caused the non-profit to revoke and replace some 2.6% of all active certificates. Incredible effort here.
Estonia's diplomacy training aims to shape state behavior in cyberspace
A virtual confab organized by Estonia's foreign ministry convened this week to try to understand acceptable conventions in cyberspace, and what happens when those rules are broken. (Think Geneva Convention but for cyber.) @shanvav also has a good thread on the event. Really what it comes down to is, "Computers don’t attack each other, it's people," so how do we prevent reaching a point where cyber-warfare is an option?
Microsoft Patch Tuesday gaffe leads netizens to 'Microosft' typo-squatting domain
Easter egg or inadvertent typo? Probably the latter, but a perfect story for El Reg to pick up. Microsoft's monthly Patch Tuesday report contained a typo that sent inquisitive researchers hunting for details about its API changes to a typo-squatted domain that at the time of writing looks like a fake search page. As for the good stuff, Microsoft fixed 56 CVE-assigned flaws — 11 of which were rated critical.
Despite scanning millions of faces, feds caught zero imposters at airports last year
Imagine having some of the most state-of-the-art surveillance technology and not finding a single criminal? That's what happened with CBP, whose airport face scanning tech didn't detect a single imposter trying to sneak into the U.S. — out of some 23 million people. Good to know that taxpayer's money was well spent. (Note to self: We need a sarcasm emoji.)
What do you actually agree to when you accept all cookies
An interesting read for anyone, but especially Europeans who, thanks to GDPR, are given the "choice" (often a joke) of how websites track you. Turns out when you "accept all cookies," you're opening yourself up to an enormous amount of tracking, more than you may think. This is a deeply technical breakdown of just what happens and who — of the many hundreds(!) of data brokers — that collect your data once you hit that fateful button. All the more reason to use Privacy Badger and a good ad-blocker.
Pro-India hacking group expands mobile malware arsenal
New research from Lookout explores how a pro-India hacking group has been using two kinds of Android malware to spy on hundreds of cell phone users' for years. The spyware has the typical features: accessing the camera and taking screenshots of the display. Some 18GB of data was "incidentally exposed," allowing the researchers to investigate.
iOS 14.5 redirects "safe browsing" traffic to Apple, and no longer to Google
The upcoming version of iOS 14.5 is directing users' "safe browsing" traffic to Apple's servers and no longer to Google's, as the company continues to distance and untangle itself from its web of messy relationships with data hungry giants. Apple has a "safe browsing" feature to help steer users away from phishing and fraudulent sites, but previously used Google to check against a list of hashes. Google never saw the website URL you were visiting, but did collect your IP address. Now Apple is changing that so it's routing this data through its servers, as confirmed by @othermaciej, who heads WebKit at Apple.
~ ~
THE HAPPY CORNER
Right, onto the good stuff.
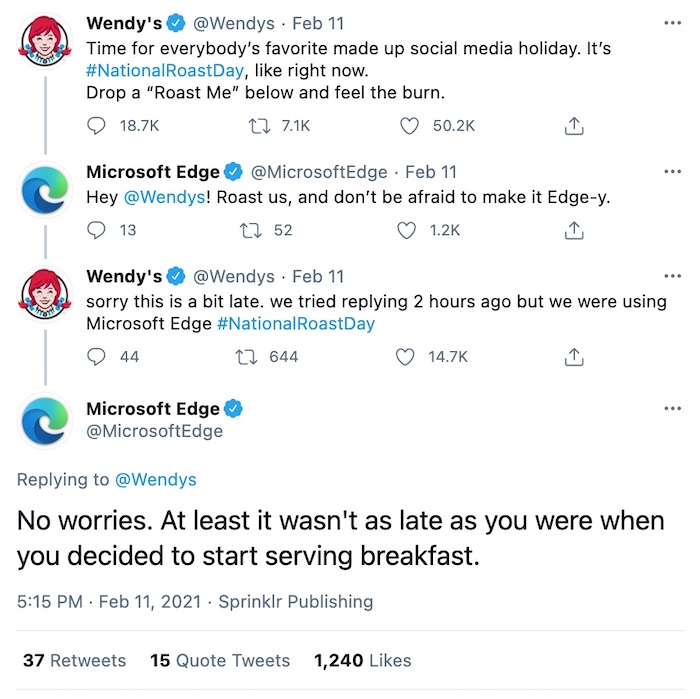
Microsoft Edge got roasted this week by Wendys, in recognition of National Roast Day.
#ShareTheMicInCyber is almost here again. On March 19, a ton of folks in cybersecurity will celebrate and recognize Black women working in security and privacy as part of Women's History Month, which runs all through March. It's an incredibly good cause dedicated to making cyber and privacy more inclusive for everyone, which especially relies on diverse voices and experiences to help address some of the most important issues in cybersecurity. The website has more info on how to get involved.
Also this week: if you were living under a rock this week and missed the accidental lawyer cat, you probably won't get this @1Password joke.
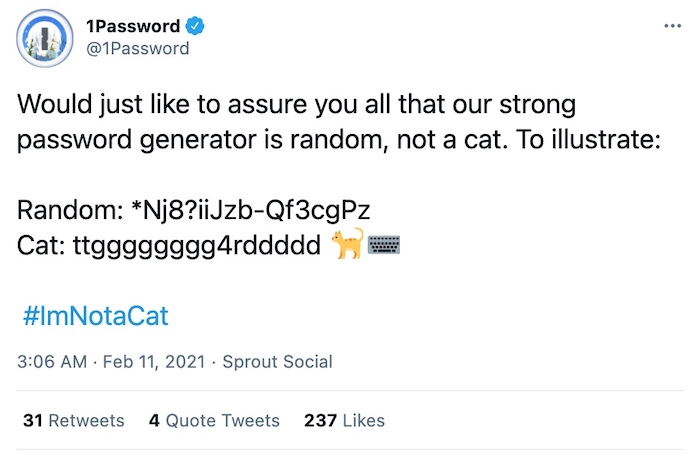
Here's a Cyberscoop for you: A big congrats to @snlyngaas, who this week became a dad. Best wishes and love to the whole family.
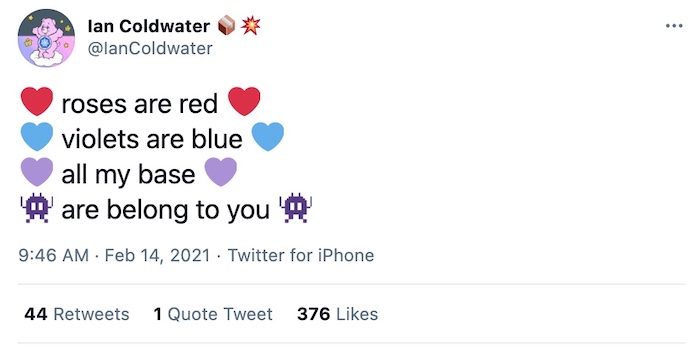
And, finally, since it's Valentine's Day today, here's @iancoldwater .
If you want to nominate some good news from the week, feel free to reach out.
~ ~
CYBER CATS & FRIENDS
Meet Sweetpea, this week's cybercat. Why does she gaze with judgment, you might ask? She knows you haven't applied the latest patches yet. A big thanks to Matt E. for the submission!

Keep sending in your cyber cats (and your non-feline friends). You can send them in here.
~ ~
SUGGESTION BOX
And we're out. Thanks much for reading, as always. If you have any feedback, you can email this@weekinsecurity.com or hit the suggestion box.
By the way... if some of you find this newsletter buried in your "promotions" tab in Gmail, just click and drag this email to your inbox and it will allegedly show up in your inbox going forwards.
Be well, stay safe, and have a great week.