this week in security — february 16 2025 edition
THIS WEEK, TL;DR
Bruce Schneier: 'DOGE is hacking America'; as CISA hit by layoffs
Foreign Policy: We start this week with the federal government (again). (Sigh; I know, but don't get cross at me, I'm not the one doing the things.) To wit: legendary security pro Bruce Schneier described the ongoing DOGE takeover of government as the "most consequential security breach" in its history as court battles go on to rein in DOGE's access to, well, practically everything the government has — including classified data, some of which DOGE posted online. The EFF has arrived and is here to help, chiefly by suing to block the ransacking of (our!) data. As things pertain to cyber, the folks at CISA got hit hard by layoffs, with some 130 staffers laid off and its election security staffers placed on leave — but sure, the security of DOGE's own website is jusssst great... (it's not). There are more and ongoing layoffs across government, including infosec folks at the U.S. Digital Service, leaving few — if anyone — able to defend these systems from attacks.
More: Bloomberg ($) | SecurityWeek | Foreign Policy | Zero Day | Cyberscoop | Popular Information | NPR | @w7voa | @metacurity
Microsoft fixes two zero-days in February's Patch Tuesday
Krebs on Security: Roll up, roll up, it's patch-yo'-systems o'clock — and this month's round of security fixes includes patches for two low-complexity zero-days, which are being exploited in the wild. One of the bugs (CVE-2024-38193) is under attack by North Korean hackers to maintain persistence to a compromised system, meanwhile Rapid7 added that another bug, CVE-2025-21418, should be prioritized as this bug has "no requirement for user interaction" to be exploited. Separately, Apple fixed a zero-day bug in iPhones and iPads that may have been exploited (heavy wink) in what it calls an "extremely sophisticated attack" to disable USB Restricted Mode on a locked device.
More: Sophos | Cyberscoop | TechCrunch
DOJ arrest two Russians accused of running Phobos/8Base ransomware gangs
Justice Department: The U.S. feds have nabbed two Russian nationals, Roman Berezhnoy, 33, and Egor Nikolaevich Glebov, 39, accused of running the Phobos ransomware crew (which also went by 8Base), effectively shutting the operation down. Europol also participated in the operation. After the arrests and server seizures, the feds alerted some 400 companies that they were compromised. In the end, the gang targeted over a thousand victims during its time, and netted some $16 million in ransoms. Security researchers noticed the site was seized a whole day before the feds announced its action. Relatedly, U.S. and U.K. governments have sanctioned the Russian "bulletproof" (aka, hosts anything) hosting service zServers, which the feds claim supported LockBit attacks. The Dutch dismantled much of zServers' infrastructure.
More: State Department | The Register | TechCrunch

~ ~
THE STUFF YOU MIGHT'VE MISSED
Russian spies caught using 'device code' phishing attacks
Volexity: Multiple groups of Russian hackers are using a 'device code' phishing attack, which takes advantage of a device flow weakness that Volexity warns that users "may not recognize it as phishing." The compromise targets Microsoft 365 accounts, and the hackers have been seen sending legit-looking emails as if they came from government departments and others. More from Ars Technica.
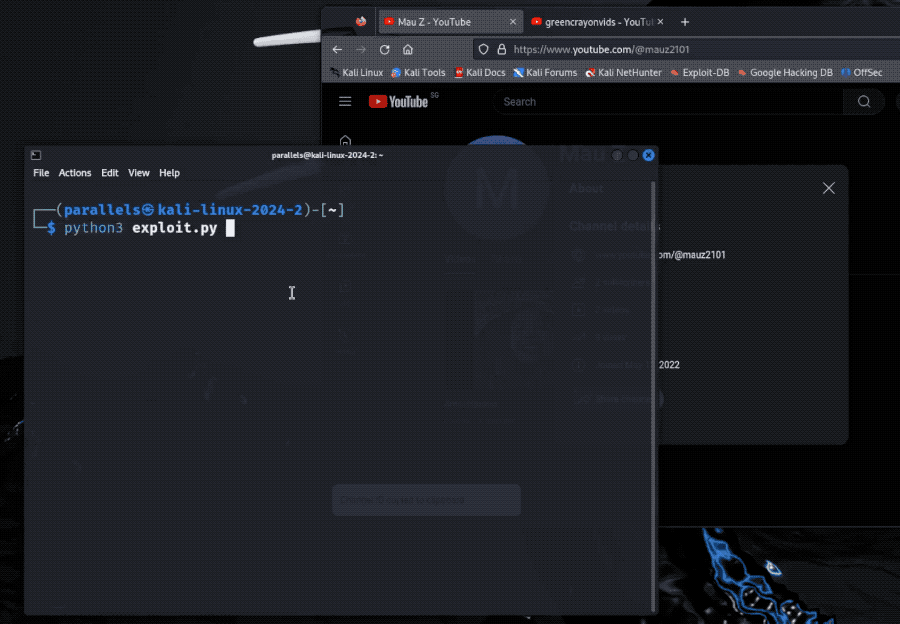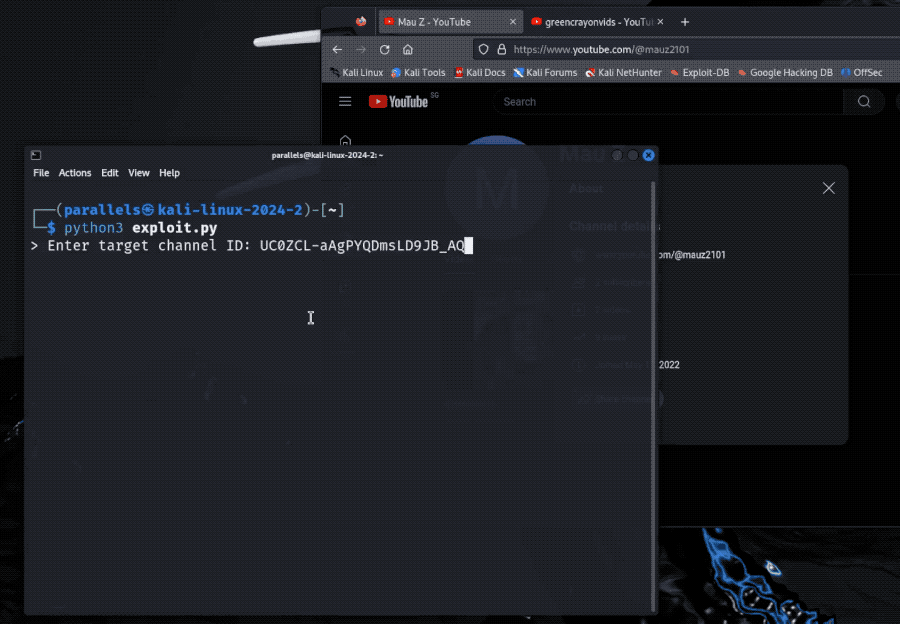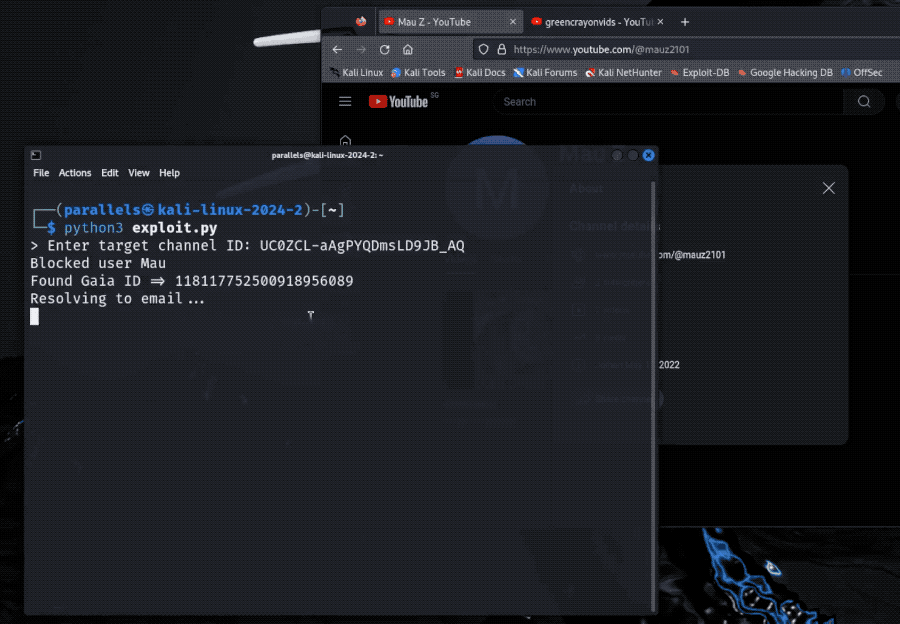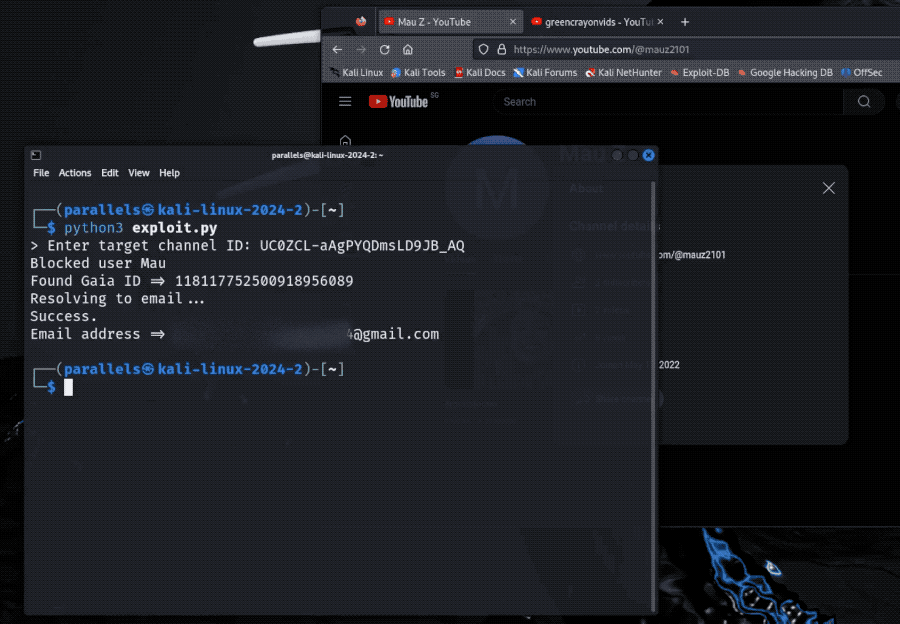
Bug leaked email address of any YouTube user
Brutecat: Interesting finding by @brutecat, who found it was possible to obtain the email address of any YouTube user. The bug was exploitable thanks to a forgotten Google product that allowed the conversion of a YouTube user's obfuscated unique ID (called Gaia, which Google uses across products) into an email address. Ta da! The bug netted the researcher $10,000 in a bug bounty payout and got the bug fixed. Never forget your legacy endpoints!
Security experts denounce U.K. iCloud backdoor demand
Global Encryption Coalition: The U.K. unilaterally decided last month [correction: last edition I mistakenly wrote last year, apologies!] that British officials can demand Apple open up its iCloud cloud service to allow access to data on any Apple user anywhere in the world. A lot of very smart people — specifically 193 (at the time of this newsletter) — think this is a very bad idea, and wrote an open letter to the U.K. government to that effect. The letter is pretty much a who's who of incredible security people — Callas, Grossman, Landau, Mill, Pfefferkorn, and White, to name a few as signatories. Let's hope someone over there in the U.K. listens. (via @josephhall)
~ ~
OTHER NEWSY NUGGETS
Media outlet outages after Lee cyberattack: Dozens of newspapers and media outlets that rely on publisher Lee Enterprises reported outages and disruption after Lee was hit by a cyberattack last week. (Disclosure: I wrote this story!) One of its datacenters was hit, per an email I obtained from Lee notifying customers of the incident. Lee said it was working to "fully restore our systems," while newspapers are still locked out of some of their most important technologies and systems. (via TechCrunch, St. Louis Post-Dispatch ($))
Sandworm's initial access broker revealed: Meet BadPilot, said to be a subgroup within the notorious Russian intelligence unit dubbed Sandworm. Microsoft dropped new details of the subgroup, thought to be an initial access broker that breaks into networks and then hands off that access to Sandworm proper for conducting data theft or causing destructive cyberattacks. Microsoft says BadPilot takes a "spray and pay" approach to hacks — seemingly picking indiscriminately, then coming back to see what they like, per @sherrod — but has been focusing on Five Eyes countries (UK, Canada, the U.S., etc.) of late. (via Wired ($))
Gotta catch 'em all, spyware makers: Italian spyware maker SIO was caught making and distributing Android spyware for years, per @lorenzofb, who obtained samples that were masquerading as WhatsApp and other popular apps. The spyware is called Spyrtacus, and was traced back to the Italian company (which also sells its services to the Italian government), thanks to the awesome researchers at Lookout who analyzed the samples. (via TechCrunch)
Bye, bye, Variston, you won't be missed: Now there's one less spyware maker in the world, thanks to the shuttering of Barcelona-based Variston, which was outed by Google in 2022 as a secret spyware developer, and later lost a ton of staff following Google's report. Now it has fully "liquidated," per business records. Don't forget to switch the lights off... (via Intelligence Online ($), TechCrunch))
~ ~
~ ~
THE HAPPY CORNER
The happy corner isn't just a quiet oasis on the burning hellscape of the internet, it's very much a state of mind. Ahhhhhh, and breathe.
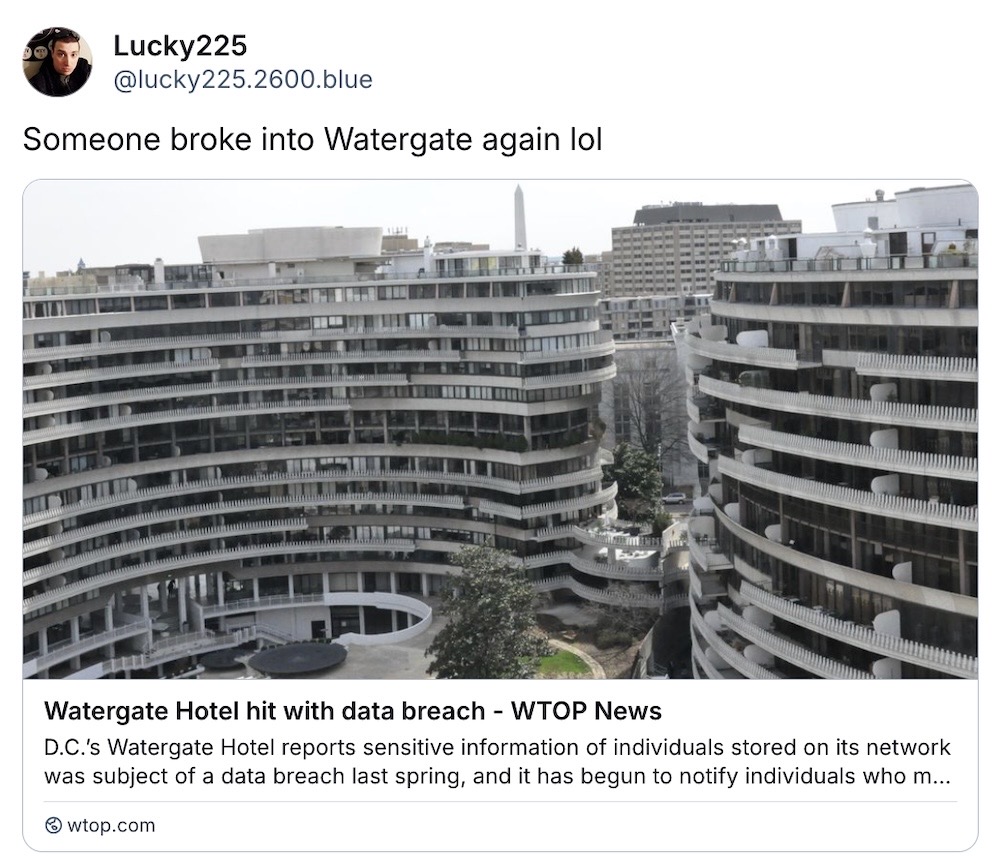
The Watergate Hotel had a data breach... (yes, that Watergate Hotel). And the jokes pretty much just write themselves at this point.
And, since it's a happy corner on the lighter side this week (have you seen what's happening outside?!) — please enjoy this bonus cybercat from the Rare Personal Collection™. I call this particular piece, Theo aka Long Cat.

If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber-cat is Tabasco, who can be seen here checking his human's code... don't let me disturb you, Tabasco, you're doing important work. (He's the lead developer, you know.) Thank you so much to Adwayan for sending in!

Keep sending in your cyber cats! (or a non-feline friend). Drop me an email at any time with their name and a photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's it for this week's.... well, whatever that was. Thank you for taking the time to read, and I hope that you enjoy the rest of your weekend. If you want to reach out with anything for the newsletter — a cyber cat (or friend), or some good news that you've come across, please do get in touch.
As for me, I'm off to make another pot of coffee, grab some breakfast, and then go outside and touch grass snow. (Yes, still.)
Dreaming of a warm beach somewhere...
@zackwhittaker