this week in security — february 18 edition
THIS WEEK, TL;DR
Poland's new PM says prior government 'illegally' used Pegasus spyware
Associated Press: Poland's new prime minister dropped a bombshell this week revealing that the government under his predecessor, the former PM of the right-wing Law and Justice party, deployed and "widely" used the Pegasus spyware for real-time surveillance of its opponents. Many of those opponents included the country's then opposition party, which is now in power under PM Donald Tusk. Dropping the news in front of Poland's president, Tusk said the list of Polish victims is "unfortunately very long," and believed to be around 100 people or so. The use of spyware, in this case developed by NSO Group, was previously found to be "illegal" by the Polish Senate as it investigates the prior government's use of the spyware. Several EU countries have used Pegasus, including Hungary, Germany and Spain.
More: Polskie Radio 24 | Meduza | @rondeibert | @jsrailton
Spyware startup Variston is losing staff, some say it's closing
TechCrunch: From one spyware to another, this time it's Barcelona-based spyware maker Variston. Over the past year or so since Google exposed Variston as a spyware and exploit maker (due to a deliberate leak, no less), the company has lost staff and some say it's shutting down. Variston's hacking tools have been used to target iPhones, Android devices and Windows PCs. According to former employees speaking with @lorenzofb, the attrition in staff was largely blamed on Protect, a UAE-based company that was Variston's sole customer, which demanded that staff onshore to Abu Dhabi or "get fired."
More: Google TAG | Intelligence Online ($) | Metacurity | @lorenzofb
Atlassian breach blamed for GAO federal agency breach
Cyberscoop: The Government Accountability Office, the federal government's nonpartisan watchdog, said some 6,600 current and former agency employees had data compromised due to a vulnerability in a contractor-hosted Atlassian system. The GAO said CGI Federal was breached via the Atlassian bug, which Atlassian fixed back in October, but in this case it's unclear if this government contractor's system had patches applied at the time it was exploited.
More: CISA | Reuters ($) | Nextgov/FCW
US military notifies 20,000 of data breach after cloud email leak
TechCrunch: That wasn't even the biggest government data breach disclosed this week... last year if you recall, a U.S. military email server was left exposed and sensitive (but unclassified) emails were spilling to the open web (from Microsoft's dedicated government cloud), because the server had no password, likely due to a misconfiguration or human error (whoops). Anyone with the IP address could dive in and access the data within. Luckily, a security researcher found it at the time and contacted me. Microsoft blamed the DOD, and the DOD blamed Microsoft (which hasn't commented since). A year on, and the Pentagon is notifying 20,600 people that their information was exposed as a result of this issue. (Disclosure: I wrote this story!)
More: DefenseScoop | @zackwhittaker | @brideoflinux
~ ~
THE STUFF YOU MIGHT'VE MISSED
Cryptic tweet doxes Russian space-based nuclear weapon
New York Times ($): Let's talk about that story for a second. The week started with a leak about a national security secret, and ended the same day(!) with news of a Russian nuclear anti-satellite space weapon. The intelligence was made public following a cryptic disclosure from the House Intelligence Committee chair, who is one of the "Gang of Eight" in Congress notified about sensitive national security threats (and probably isn't keeping that job for much longer). The anti-satellite weapon isn't said to be operational (yet), but that the U.S. has no way to counter such a weapon (also yet). More from the Associated Press.
Russia's Fancy Bear relies on ChatGPT for scripting
Microsoft: Moving on... from Russia-based space threats to Russia-based cyber threats. Microsoft's new research this week shows Russia-backed hackers, specifically Fancy Bear — the smash-and-grab hackers who raided the Democratic National Committee's systems back prior to the 2016 election — are using AI to help hone their attacks. A reminder that they aren't using LLMs or AI to generate zero-days that can puncture any security defenses, rather Fancy Bear is relying on ChatGPT to write scripts and composing phishing emails akin to, well, script kiddies. Threat intel boss @likethecoins has more context for network defenders in the tweets.
Details of Mastodon account hijack bug released
Arcanican: Remember a couple of weeks ago when Mastodon fixed a critical account takeover bug? Details are now out, and it's a doozy. A detailed write-up of the bug showed it was possible for anyone to impersonate and hijack any Mastodon account. Admins, if you haven't updated your Mastodon instance, now would be a good time — though most of the big ones have already.
Hackers uncover new TheTruthSpy stalkerware victims
TechCrunch: The notorious stalkerware operation TheTruthSpy continues to facilitate the secret surveillance of thousands of unknowing victims around the world. We know this because the stalkerware operation, which has previously leaked data and also been hacked several times before, was hacked again. Two groups of hacktivists independently found the bug that allows the mass-exfiltration of victims' stolen data from TheTruthSpy's servers. The exfiltrated victims' data was provided to me by @maia (great read, also features an excellent IDOR joke). That data is now lookup-able by anyone who thinks they might have had their phone compromised by TheTruthSpy's stalkerware apps. The spyware lookup tool now has about 400,000 entries (or thereabouts every victim since 2016). As long as TheTruthSpy remains online, it presents a major threat to its victims, not least because it can't keep their stolen data safe.
~ ~
OTHER NEWSY NUGGETS
FCC gives telcos seven days to disclose hacks: The Federal Communications Commission has updated its breach reporting requirements to mandate telecom companies notify the agency of a breach within seven days and "no case more than 30 days" of its discovery. Prior to this, telcos only had to disclose in the event of a breach of CPNI, which is data that's typically on your phone bill. The new rules now include non-CPNI customer data, which largely relates to customers' personal information. Better late than never, but probably not much comfort for the collective millions affected by T-Mobile's nine data breaches since 2018. (via The Register)
DOJ's latest hack-back knocks GRU botnet offline: The Justice Dept. says it's taken down a botnet made up of hundreds of small office and home office (aka SOHO) routers used by the Russia hacking group Fancy Bear to exfiltrate stolen data. The DOJ's court-authorized operation tapped into the routers and replaced the botnet's malware, known as Moobot, and blocked router firewall rules to block remote access (effectively closing the backdoor). That's two for two after the DOJ's recent takedown of a Chinese-made botnet... (via Justice Dept., SecurityWeek)
Ransomware hits Romanian hospitals: More than a hundred Romanian healthcare facilities were hit by a ransomware attack, with many going offline, including a children's hospital. The extortion group behind the attacks demanded some $50,000 in bitcoin to decrypt the files. Much of the affected data had been backed up recently, allowing some facilities to bounce back fairly quickly, per @joetidy. (via BBC News, Romania Health Ministry)
U.S. cyberattacks Iranian ship: Here's a curious one. The U.S. government carried out a cyberattack (so far as yet unspecified, though Lawfare reads between the lines) targeting an Iranian military vessel in the Red Sea, where Iranian-backed Houthi forces that control much of Yemen have been attacking ships with drones and missiles. Per the New York Times ($), the "cyberattack was intended to disrupt the Iranian ship’s ability to share that information with the Houthis." Little else is known about the cyberattack, but it sounds like it could feasibly be anything from a denial-of-service (think radio or signals jamming) or a destructive cyberattack targeting the ship's systems (such as deploying malware on a navigation system). We may find out more about this soon... (via New York Times ($))
Data broker tracked visits to 600 Planned Parenthood clinics: Filed under, "I still can't believe it's not illegal," a data broker called Near Intelligence gathered and sold the location data of people visiting hundreds of Planned Parenthood clinics to one of the largest anti-abortion ad campaigns in the United States. The new reporting by Politico's @alng shows how freely available this highly sensitive data is, even though it clearly absolutely shouldn't be. More from Sen. Ron Wyden's office, who warned that the data could be used to put women in jail in U.S. states where abortion access is illegal. (via Politico, @WolfieChristl)
~ ~

~ ~
THE HAPPY CORNER
And that's the news. This, here, is the happy corner.
TIL how ssh, the secure shell protocol, got its now-famous port 22. You might not think much about it, but here's the weirdly heartwarming story of how ssh on port 22 came to be.
404 Media, the new journalist-owned tech site that has been crushing it on the cyber beat (and at large), is profitable after six months of its founding. Great to see, and should have media giants terrified as this trend of journalist-owned media startups continues. I'm proud to be a paid subscriber of 404 Media, and you should sign up for their incredible reporting.
Here's an interesting low-tech take on a rising cyber-scam (and where passwords actually still might help). Extortion tactics that try to trick would-be victims into handing over money — such as impersonating a family member, or worse, claiming to have them hostage — can be defeated by way of a "family password," per Bloomberg ($). That's a password or phrase that only you and your family know, so that in the event someone tries to spoof a family member and scam you out of your life savings, you can ask them what the family password is. Smart, right? Here's some sage @RachelTobac advice on picking a good family password.

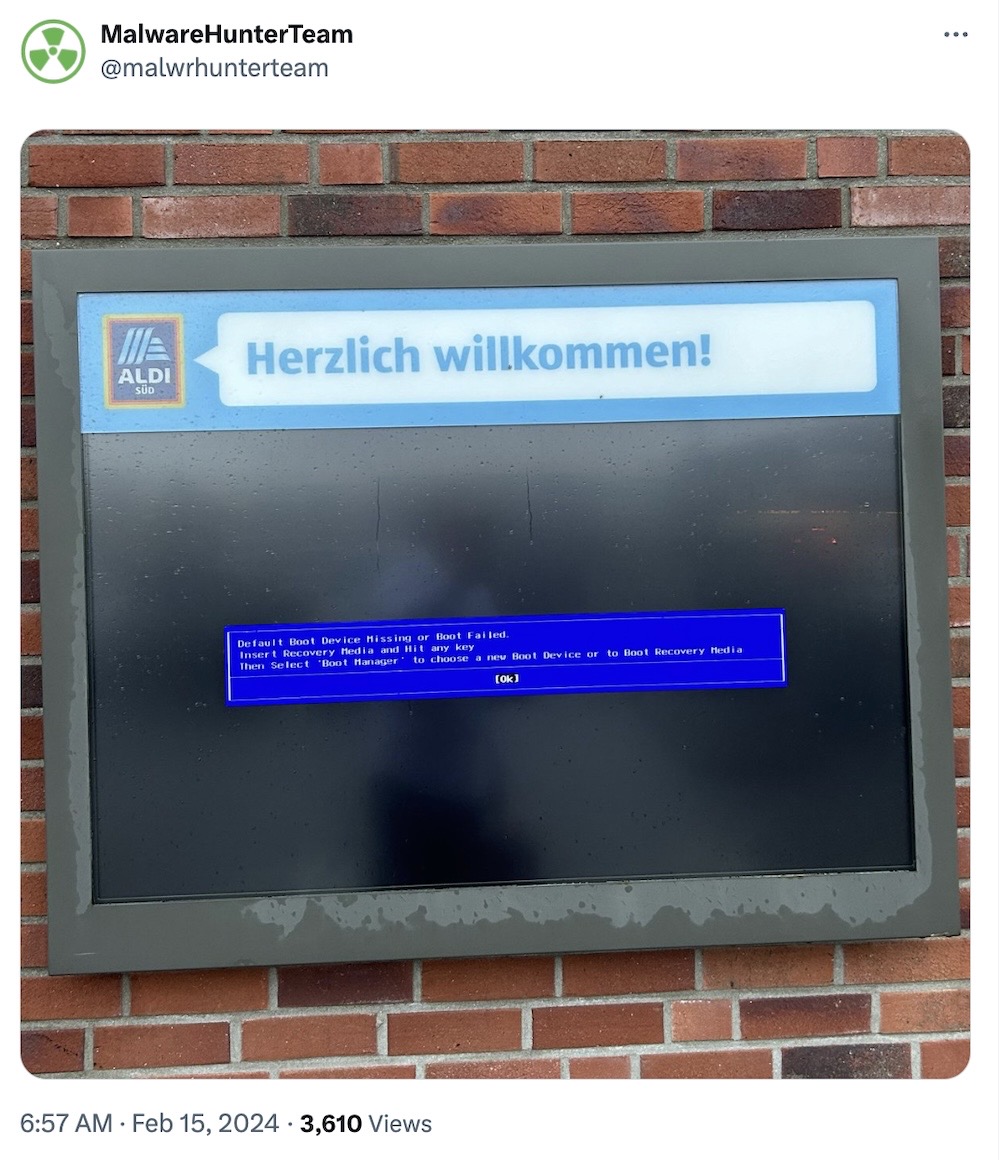
And a warm welcome to Aldi from this German boot error message.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat digital dog(?) is Max, who can be seen here standing guard against all cyber threats — although known vulnerabilities include toys, walks, and treats. Many thanks to Amanda W. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for this week. Thanks for joining me again! As always, you can contact me by email any time with any feedback you have. Also, please send in your cyber cats! It's really the highlight of my week.
All my best,
@zackwhittaker