this week in security — february 19 edition
THIS WEEK, TL;DR
Clop ransomware gang claims it breached 130 organizations using GoAnywhere zero-day
Bleeping Computer: Let's start this week in ransomware-land. The Clop ransomware gang claims it's behind a mass-hacking effort that's breached 130 organizations by exploiting a new zero-day vulnerability in a widely used enterprise file transfer tool, developed by Fortra. (If that sounds vaguely familiar, it's because it is — Clop abused a similar flaw in another file transfer system called Accellion a few years ago.) The bug allows unauthenticated remote access to an affected server, so attackers can mass-scan for targets. One of those said to be hit by the latest round of Clop ransomware attacks is healthcare and hospital giant CHS, which said 1 million patients had data stolen following a breach of its Fortra file transfer tool. Fortra was flamed for hiding its security advisory behind a login wall, but @briankrebs has the notice you need.
More: Ars Technica | TechCrunch | DataBreaches.net | Huntress | Rapid7
FBI 'contained' cyber incident on bureau's computer network
CNN: The FBI said this week it was investigating and "contained" a security incident involving — and I'm quoting CNN verbatim here — "an FBI computer system used in investigations of images of child sexual exploitation," per two sources, but no further details. If there was a compromise of one of those systems, there are so many questions to answer. (Was a computer containing CSAM — even if it was for investigative purposes — connected to the internet, and if so, why?) The FBI hasn't commented further. Maybe we never will. (Classic FBI!) But I can't help but feel like this is going to get worse before it gets better. Let's hope Congress looks into this, because the feds aren't exactly great at investigating themselves.
More: Reuters ($) | @snlyngaas tweets
Now for sale: Data on your mental health
Washington Post ($): New research this week found that telehealth and therapy apps collect a huge amount of sensitive health information about its users, and share that with data brokers for resale. The full research is worth the read, but the bottom line is clear — healthcare apps took advantage of you during the pandemic to make money. No apps were named (nobody wants to get sued!) so assume that this is all of them. Why? Because the U.S. still doesn't have a federal data security or privacy law. Bonkers, isn't it? But as such, this data sharing and selling will continue to be allowed to happen until regulators (or lawmakers) intervene. This comes not long after the FTC took action against GoodRx for sharing a ton of sensitive health information with third-parties and advertisers. Now let's see the FTC enforce its own orders!
More: Duke University | @ACLU
Ransomware roundup: 3 million patients and a California city
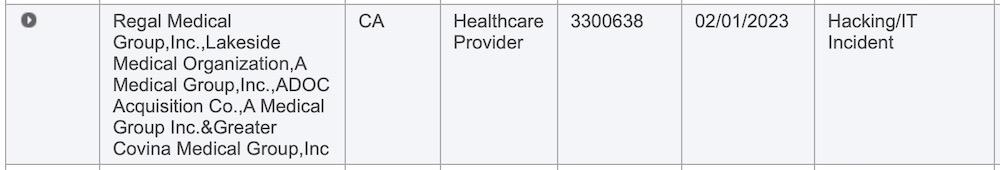
San Francisco Chronicle ($): First up, the city of Oakland declared a state of emergency this week following a ransomware attack that hobbled the city's tech systems. The incident is dragging into its second week, with residents unable to pay parking fees, fines, or pay taxes online. Oakland has about half-a-million residents. Meanwhile, California healthcare giant Regal Medical Group said it was hit by a ransomware attack back in December but only recently disclosed. In a filing with the U.S. Department of Health and Human Services, Regal said an eye-watering 3.3 million patients are affected (no wonder a class action has been filed), making it one of the biggest breaches of personal health information this year. And yes, it's only February.
More: SFist | City of Oakland | SecurityWeek
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
With Section 702 up for reform, a look at 'backdoor' searches
Just Security: The U.S. government's "crown jewel" surveillance powers, also known as Section 702 (for its place in the law books), allows its spies to snoop on communications of overseas nationals outside of the United States. Americans can't be directly targeted. But, their communications can be collected if they're chatting with, say, a foreign national who's under suspicion of something. Natsec legal superstar @LizaGoitein has your 101 guide on these so-called "backdoor searches," what they are, how they work, and why Congress should close that backdoor.
California bill would ban 'unconstitutional' warrants
Mia Bonta: A California assemblymember has introduced a bill, backed by the ACLU and EFF and more, which would ban the use of certain kinds of warrants that are considered "unconstitutional." Specifically we're talking about geofence, keyword and reverse warrants, which allow police to ask companies like Google to determine if a person was near a certain place at a certain point in time, or searched a particular query at a specific time. Police use these warrants as a way to find suspects faster, but critics argue the constitutionality of this is in serious doubt because it violates the privacy and rights of anyone else who was there, or searched a keyword, at the same time. Bonta introduced the bill specifically to protect those seeking abortions and gender-affirming care, but would also apply broadly to everyone in the state. Cyberscoop has more.
Albanian gangs set up their own CCTV networks to spy on cops
Vice: Police in Albania say they found a shadow network of about 500 illegal surveillance cameras, installed by gangsters and organized criminals around major cities — including Tirana, the country's capital — so that the gangs could use the cameras to keep a close watch on the movement of police. Except, as you can imagine, the cameras weren't enough to stop the criminals from getting caught. Brazen, yes. Impressive, almost. Incredibly stupid? Definitely. More details via Euronews Albania.

U.S. border officials can now check e-passport data
Wired ($): For the past decade and a half, U.S. border authorities haven't been checking the digital signatures in travelers' passports. Yeah — wild, right? Finally, though, the U.S. border agency has implemented the software to cryptographically verify passports — and it's already caught about a dozen individuals using dodgy or forged passports. So the system works! Now, imagine how many criminals the authorities could have caught in the past 16 years they weren't properly checking passports?
Amazon lawyer warns against sharing corporate data with ChatGPT
Insider ($): ChatGPT, everyone's new internet favorite plaything (until it becomes sentient, that is), is ingesting corporate secrets and spitting them out as responses. Amazon warned its employees in a Slack message (which itself was leaked) not to share confidential information with the chatbot out of fear it'll end up sharing company secrets with anyone who asks the right questions.
~ ~
OTHER NEWSY NUGGETS
National cyber director Chris Inglis departs: Chris Inglis, the U.S.' first national cyber director, is leaving the office after a year and a half. The position, now in the hands of acting director Kemba Walden, oversees the position, which is effectively chief cyber advisor to the president. The Washington Post ($) looks back at Inglis' career and what's next for the office. News of his departure comes as the Biden administration is poised to publish its first national cybersecurity strategy in the next week or so (depending on who you ask). (via @ncdinglis)
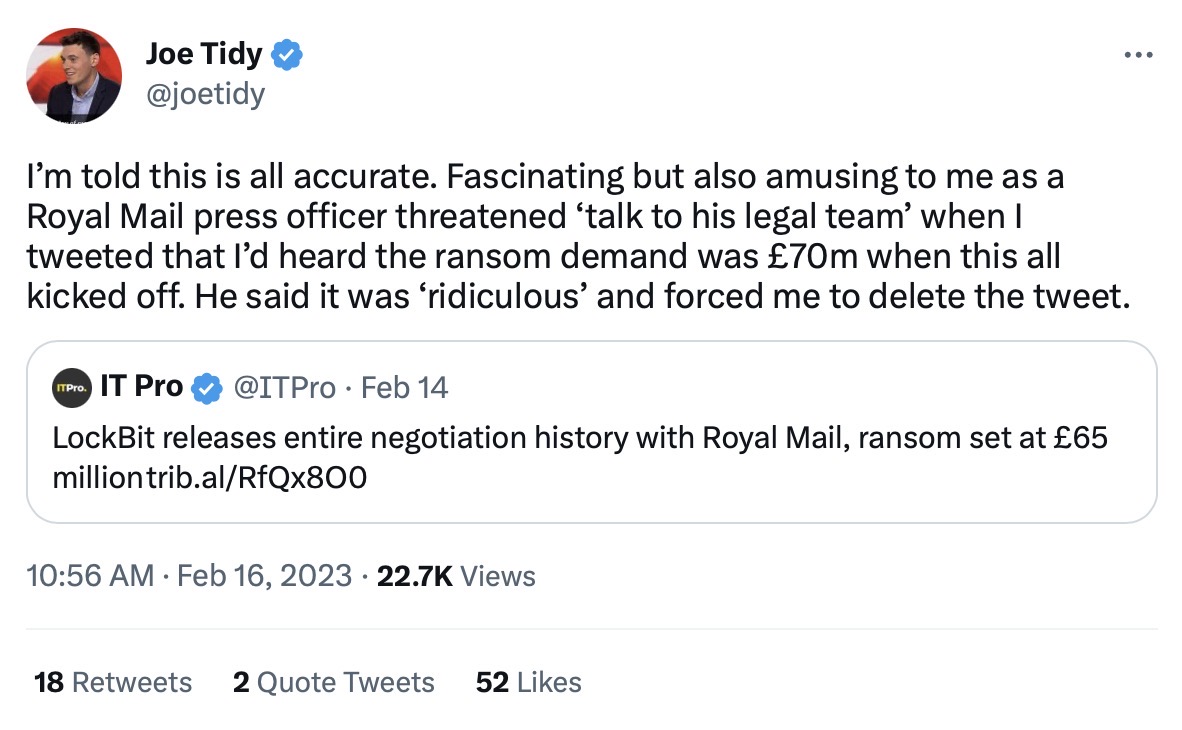
Royal Mail flaps as LockBit drops chat logs: The U.K. postal service rejected an "absurd" ransom demand for $80 million from the Russia-linked LockBit ransomware group, which published the chat log negotiations this week after Royal Mail refused to pay. Royal Mail continues to face shipping disruptions, but instead of being transparent about the situation, one of its press officers took this week to threatening a journalist who reported on the ransom demand. The fact that Royal Mail is negotiating with a ransomware group just shows its executives have absolutely no clue what they're doing. While Royal Mail flaps and threatens, LockBit seems to be doing Royal Mail's communications for them. (via The Guardian)
GoDaddy hacked in multi-year breach: Hosting giant GoDaddy confirmed that its hosting infrastructure was breached by malware over a multi-year effort to orchestrate spam injections across the internet. According to GoDaddy's 8-K filing with the SEC (and more in a statement), the hackers stole source code and used malware to compromise the company's WordPress hosting accounts. GoDaddy said it also found evidence linking the threat actors to a broader campaign targeting other hosting giants in recent years. If you're wondering how this all came to be, you need to read this 2021(!) blog post by @thezedwards, who warned GoDaddy about this long ago. (via Victory Medium)
Twitter drops SMS 2FA for non-paying accounts: Beleaguered social media giant Twitter said it will deactivate SMS two-factor authentication for any account that doesn't pay for its premium offering, Twitter Blue. (Another way of looking at this is, Twitter is making its least secure 2FA offering only available to paying users.) The good news is that you can still use app-based 2FA without paying Elon Musk a dime. Here's how to set it up. (via @ZoeSchiffer)
~ ~
THE HAPPY CORNER
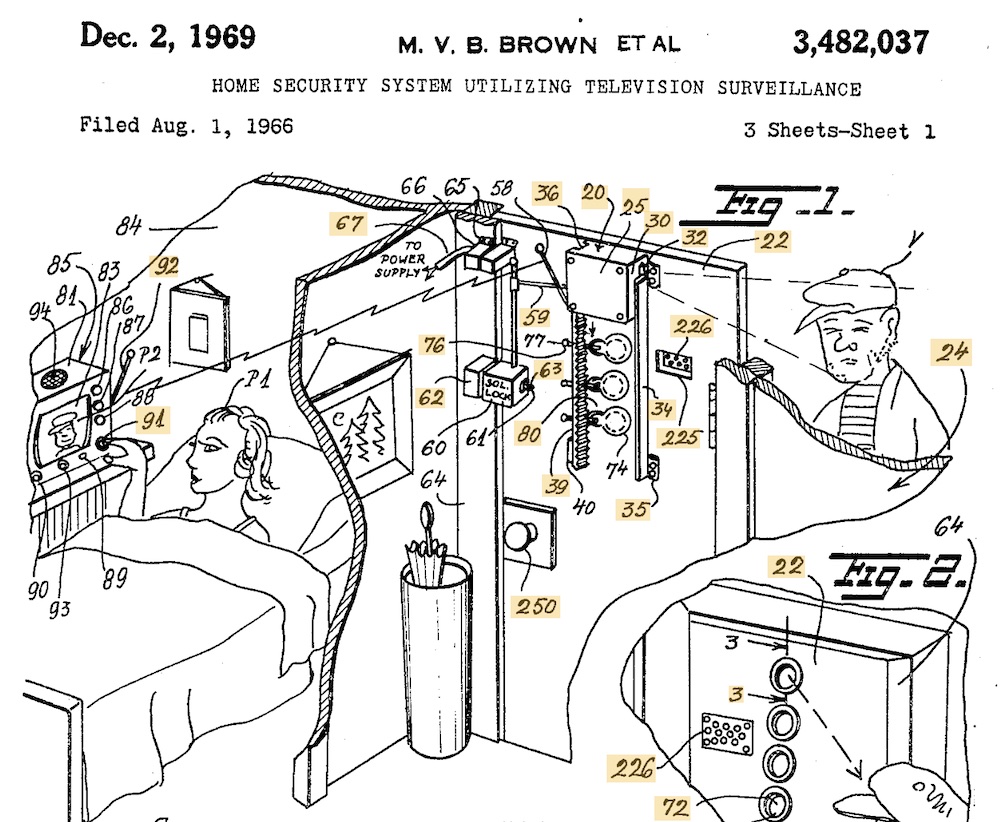
Happy Sunday. Welcome to the happy corner. February is Black History Month, and this week comedian @MateenStewart dropped this video about Marie van Brittan Brown, who you might know as the inventor of the home security system. Brown's original patent, filed in 1966, includes cameras, television monitors, microphones and a panic button. MIT has more on Brown's invention.
This week, if you're in the Washington DC area, @kimzetter is giving a talk about Stuxnet, a topic few know better than Zetter, who literally wrote the book about the digital weapon. It's at Johns Hopkins SAIS on February 22. (Side note: Countdown to Zero Day remains one of my all-time favorite non-fiction books, and if you haven't read already, you're missing out.)
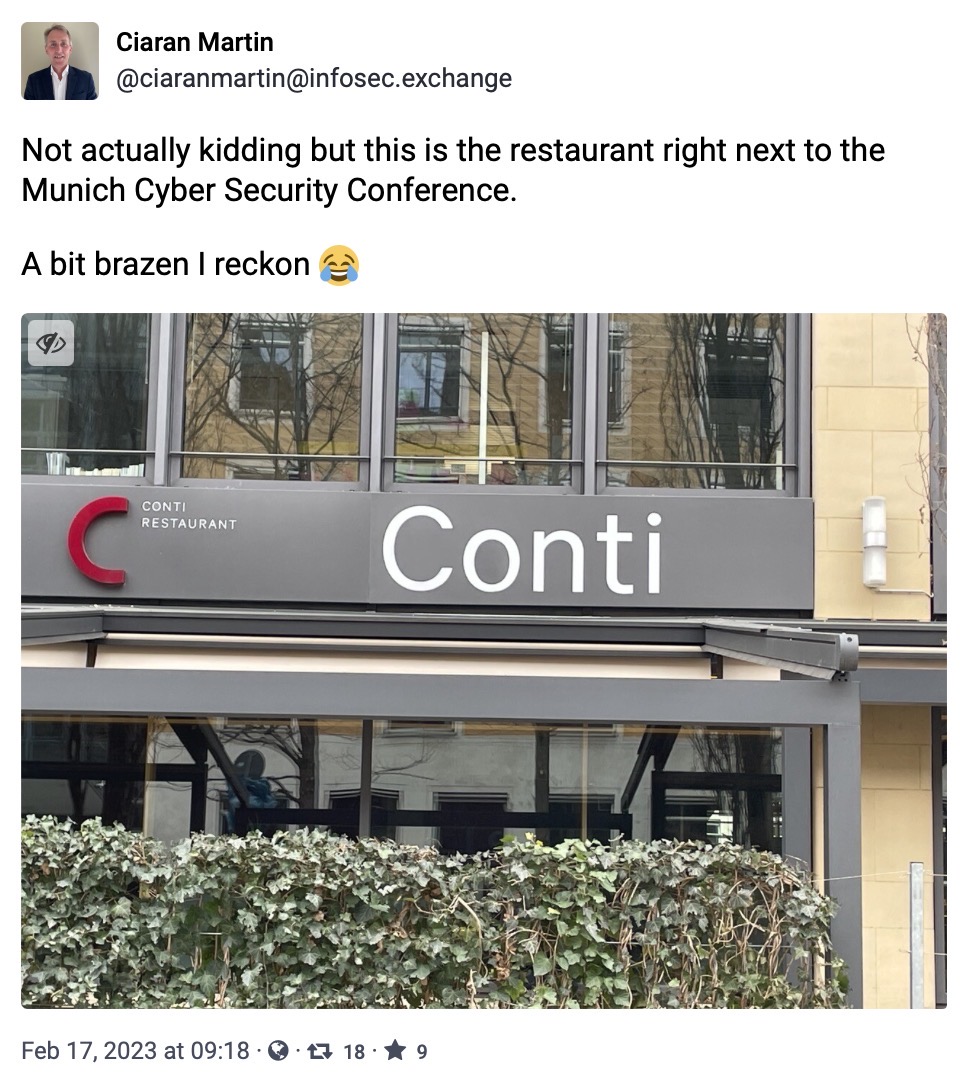
And finally, spotted by @ciaranmartin, next door to the Munich Security Conference. A little on the nose!
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Toni, who loves being around while her human does school work. Toni's human is a high school senior currently enrolled in a cybersecurity class, and got the idea to send in a snap of Toni thanks to having a teacher who has excellent taste in security newsletters (shoutout to Mr. Pudaloff!). Thanks to James P. for sending in!

Send in your cyber cats! (You can send in your non-feline friends too.) Email me a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for this week — back next Sunday, same time(-ish, always accounting for breakfast). Feel free to email any feedback or drop a note in the suggestion box.
Have a wonderful week, and be well.
—@zackwhittaker