this week in security — february 20 edition
THIS WEEK, TL;DR
The elite hackers of the FSB
BR Recherche, WDR: Turla is one of the most skilled and long-running hacker groups operating today. With links to the Russian FSB, German reporters tracked down two people who they believed are core members of Turla. BR and WDR decided not to publish the full names of the developers, but this is by far the deepest dive on the hackers to date, and in an awesome and engaging storyboard-style format. Beautifully done in both English and auf Deutsch. Good tweet thread by @hatr, who co-authored the story.
More: @hatr | Background: Kaspersky | Cisco Talos

Hacking group is on a tear, hitting US critical infrastructure and SF 49ers
Ars Technica: Ransomware group BlackByte is back — after a rocky start. The group first emerged last year but quickly went dark after researchers found a bug that allowed some victims to decrypt their files without paying the ransom. Back with a vengeance, BlackByte claimed the San Francisco 49ers this week, a day before the Super Bowl, and caught the attention of the federal authorities, who say multiple critical infrastructure sectors — including government facilities, food and agriculture, and financial — have also been targeted by the group. It comes in the same week that the DOJ said it would beef up its efforts to combat the illicit use of cryptocurrencies, such as when used by ransomware actors. Some three-quarters of all money made through ransomware attacks went to Russia-linked hackers, per Chainalysis.
More: CNN | BBC News | IC3 Advisory [PDF] | Justice Department
FBI, DHS warn U.S. officials of possible Russian cyberattacks linked to Ukraine invasion
Yahoo News: As we wait for what seems like an inevitable further Russian incursion into Ukraine's territory, U.S. authorities are warning that cyberattacks against U.S. critical infrastructure could land in conjunction with a possible invasion. Remember, this story was published on Monday. Since then, a flood of activity kicked off — some attributed to Russia, like a DDoS targeting Ukraine's banks and defense ministry, a feat that normally took years — and warnings from the FBI, CISA, and NSA. In a statement [PDF], the trio of government agencies said Russian state hackers are lurking in defense contractor networks (which of course is exactly what intelligence agencies should be doing).
More: Ars Technica | TechCrunch | CISA | @olivia_gazis | @a_greenberg
Mexican businessman pleads guilty in U.S. to brokering hacking tools
SecurityWeek: Mexican businessman Carlos Guerrero has pleaded guilty in a U.S. federal court for selling hacking tools and spyware from now-defunct Italian company Hacking Team and other unnamed Isareli companies, according to a DOJ indictment. Guerrero is said to have sold the equipment to target individuals for political purposes, not legitimate law enforcement purposes, including selling exploits that have the "ability to hack WhatsApp messages." (There's one spyware maker that's known for this — NSO Group, which when asked denied any connection to Guerrero.) He also arranged for a Mexican mayor to hack into a political rival's online accounts. Guerrero faces up to five years in prison. This all happened some 5-7 years ago... but it's noteworthy that prosecutors are going after spyware brokers even after all this time.
More: TechCrunch | Motherboard | @lorenzoFB
Five DIY home security systems are vulnerable to hacking
Consumer Reports: In testing, Consumer Reports found only half of the DIY home security systems could withstand close-range radio frequency jamming attacks, which are supposed to block window and door sensors from working and triggering an alarm. The companies' responses... weren't great, but it's clear that your home security system is only as strong as its weakest component. Fantastic work here.
More: @ConsumerReports
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Documents show ID.me's marketing to states about facial recognition tech
Cyberscoop: Great reporting here from @TonyaJoRiley, who's been all over ID.me, the identity verification company, and its recent deployment (and subsequent pulling) of its service to the IRS. New documents shared by Cyberscoop show that ID.me deployed a powerful form of facial recognition — known as 1:many, in which photos are compared to a database of photos that checks for a duplicate (and therefore a potentially fraudulent account). But critics are concerned about accuracy. The documents also include "talking points" for states to combat media reports that it used 1:many facial recognition. Also, this Slate op-ed is a good explainer on the privacy implications, even after the IRS abandoned its plans to roll out ID.me.
Never, ever, ever use pixelation for redacting text
Bishop Fox: Interesting research here about pixelation, and how it cannot — and should not — be used as a method of redaction. They also released the Unredacter code on GitHub, so check it out. Take the time to read this.
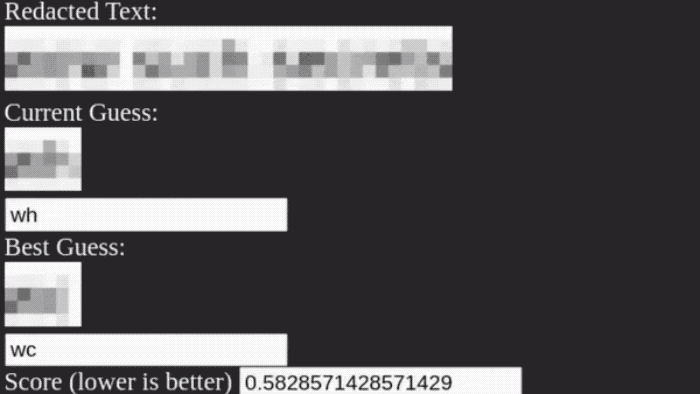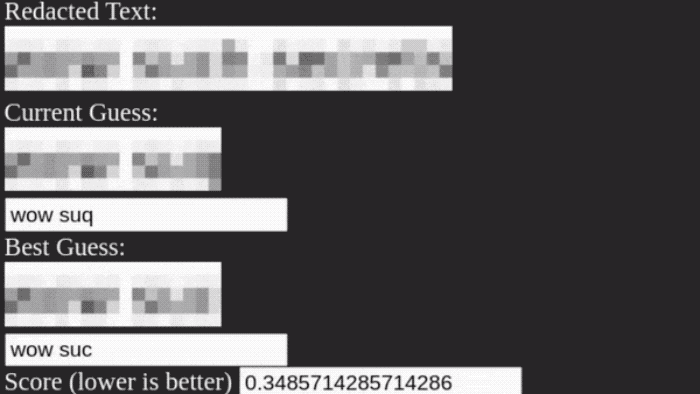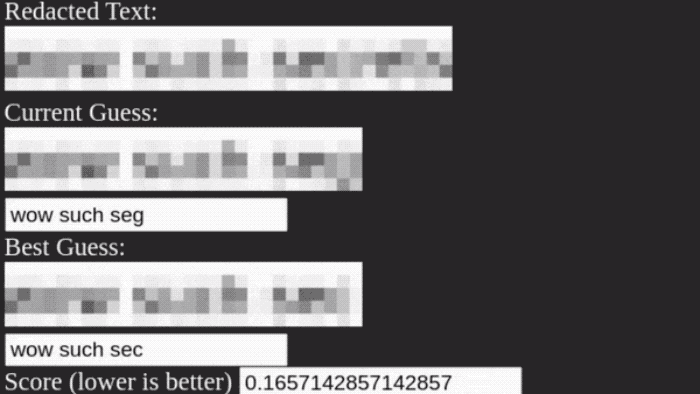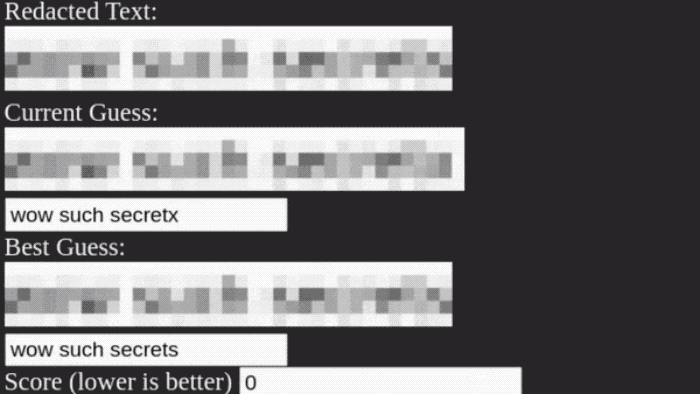
Broward schools took extraordinary steps to hide key details of data breach
South Florida Sun Sentinel ($): When Broward School District learned that hackers accessed the personal data of thousands of people, including students, its response was to "hide and delay." This report is a long-running look at the district's haphazard handling of a ransomware attack in November 2020. Every word is worth the read, though admittedly I got to the first set of bullets and was already clenching my jaw with anger. As a security reporter who's been on the painful end of disclosures before, I can sense this reporter's frustrations. Props to the Sun Sentinel for not letting Broward off the hook.
~ ~
OTHER NEWSY NUGGETS
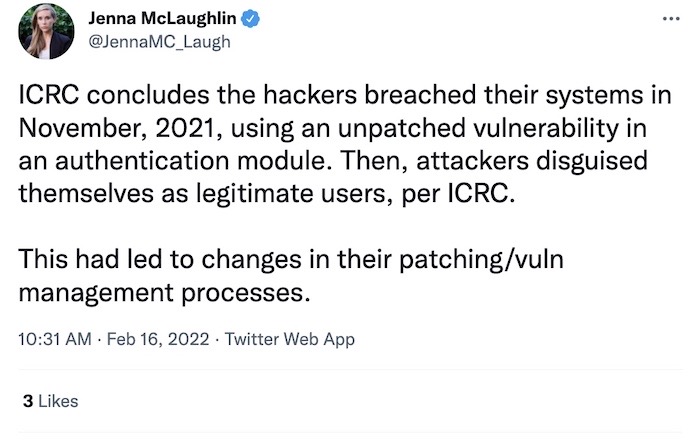
Red Cross says nation-state attacker behind data breach
ICRC: The International Committee of the Red Cross says a "state-sponsored" actor was behind a data breach of its systems, which compromised the data of more than 515,000 "highly vulnerable" people. It wasn't said which state the ICRC believes the hackers are backed by, but that they exploited a known but unpatched vulnerability in its systems, which it found code that suggests it was specifically targeted. Good thread by NPR's @JennaMC_Laugh.
SEC proposes cyber rules for investment funds and advisers
WSJ Pro Cybersecurity ($): Financial regulators proposed long-awaited cybersecurity rules for investment funds and advisers last week that would require thousands of companies to report cyberattacks within 48 hours, reports the WSJ. That means funds and investment advisers will need to have written policies and procedures for dealing with cybersecurity incidents. More from the SEC here.
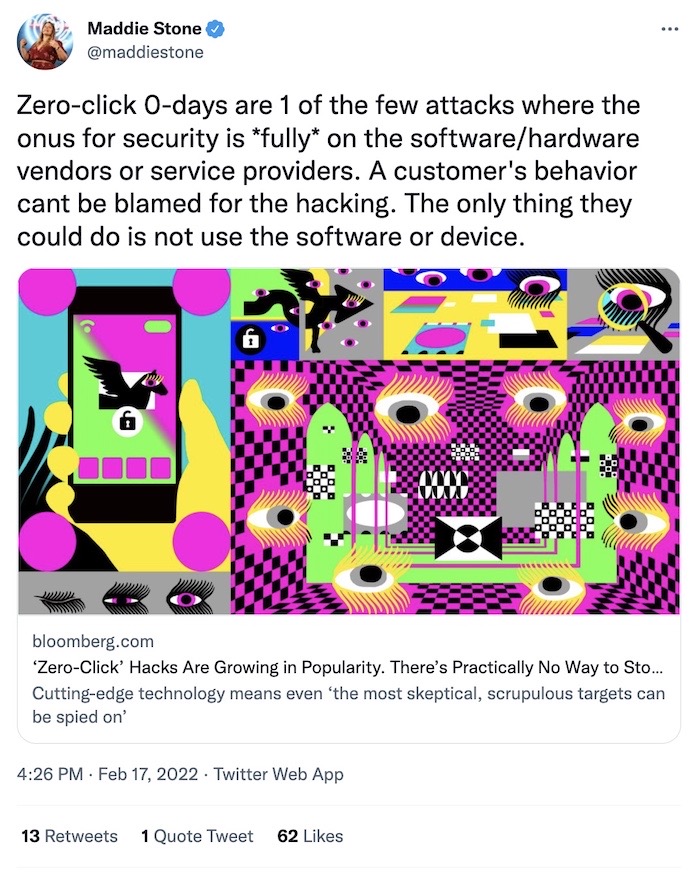
'Zero-click' hacks are growing in popularity. There's no easy way to stop them
Bloomberg ($): Zero-click attacks are the silent, interactionless attacks that have been used by companies like NSO but others, including QuaDream, Candiru, Cognyte, and Paragon, to infect targets' phones with spyware. But these attacks are nearly impossible to stop without direct intervention and security fixes from the tech companies. It's a really good read for a beginner to get apprised on the matter, which also looks at the victims of zero-click attacks, like Rania Dridi, a London-based reporter for Arab media, whose phone was compromised by a zero-click zero-day for months starting in October 2019 that had yet to be patched by Apple. Dridi was one of dozens of reporters whose phones were targeted. You should also read this Reuters ($) story of Saudi women’s rights activist Loujain al-Hathloul, whose recently-hacked iPhone helped Citizen Lab identify a bug that let Apple notify thousands of victims of zero-click attacks.
~ ~
THE HAPPY CORNER
Welcome to the newsletter, for those who read from the bottom-up. (So I've been told!) This week @runasand started a new project fearing spies who used journalism as a cover and journalists who were also spies. First post dropped on Instagram, follow along for the ride.
Suggestion from @LisaForteUK: Cat chonk chart for cyberattacks (now say it quickly, five times). Who's in? By all accounts, SolarWinds would've been an "oh lawd he comin."

I missed this last week, but @payloadartist made BugBountyHunting.com as a bug bounty search engine to look for write-ups, payloads, bug bounty tips and more. Great resource here.
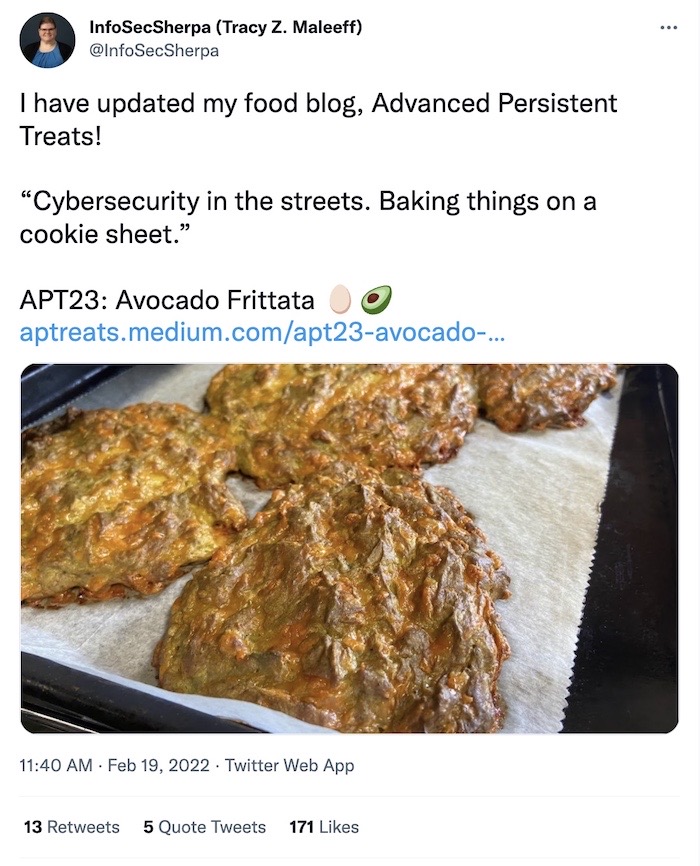
And finally, @InfoSecSherpa has a new recipe out — APT23: Avocado Frittata. Looks absolutely delicious. Check out APTreats for more recipes. (h/t: @k8em0)
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cyber cat is Pancake. Even though he hates Windows Update, he makes sure all his stuff is fully patched because you know why. Setting a great example there, Pancake. Big thanks to his human @paulrobichaux for the submission!

Keep sending in your cyber cats (or their friends)! You can drop me an email here with their name and photo, and I'll make sure they're featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And I'm out... to spend a bit of time in the sunshine after what feels like a month of snow, sleet, wind and gloomy weather. Thanks for reading this week. As always, feel free to send any feedback to the suggestion box is open, or drop me an email.
See you next week, have a good one.