this week in security — february 24 2025 edition
THIS WEEK, TL;DR
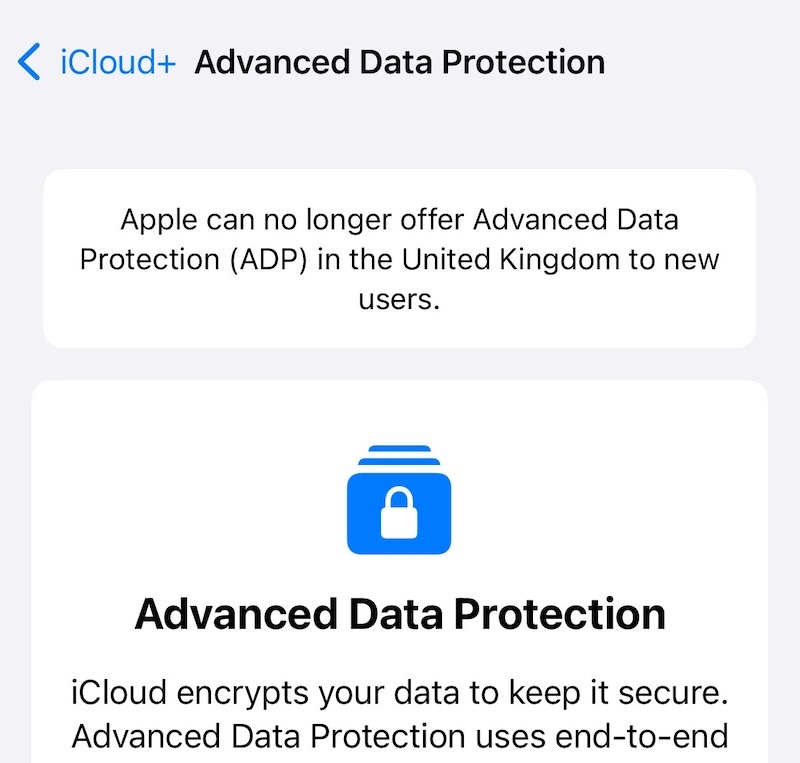
Apple pulls iCloud encryption feature after U.K. government 'backdoor' row
BBC News: Apple has pulled Advanced Data Protection, its opt-in security feature that adds a lot more E2EE to customer's data stored in Apple's iCloud, following a demand from the U.K. government to add a secret backdoor. Apple had the option to open up the backdoor, or get out. Apple chose to do neither and pulled the feature altogether, effectively weakening the security of every U.K. customer as a result, but also internationally (since now that the U.K. got its demand, now any authoritarian country can demand the same). ADP protects things like photos, notes, and other data in iCloud, which can now be accessed pursuant to a court order. Apple, a company worth more than $3 trillion, chose to take one that weakened the security of its U.K. users while allowing the company to continue profiting from its customers. Apple has long called privacy a "fundamental human right," but clearly up to a point of its own choosing.
More: Washington Post ($) | Bloomberg ($) | Associated Press | TechCrunch | EFF | @matthewdgreen | @davidtpegg
DOGE at CISA as federal cyber workers brace for firings
Wired ($): @KimZetter reports that DOGE, the team of government cost-cutters working for the world's richest man, Elon Musk, is now at CISA. The 19-year-old DOGE staffer Edward Coristine, aka "BigBalls" (per his since-private LinkedIn) is at the federal government's cyber agency, along with DOGE technologist Kyle Schutt, who're listed in the staff directory. (@marisakabas and @kevincollier also confirmed.) It's not clear what they're up to or after, but CISA has already seen its staff drastically cut, with fears that several hundred employees could also go at NIST, which sets the U.S. government's standards and benchmarks (including cyber and the National Vulnerability Database).
More: Wired ($) | NextGov/FCW | TechCrunch
Lee Enterprises hit by ransomware; newspapers face ongoing disruption
TechCrunch: Newspaper publishing giant Lee Enterprises is still hobbled after suspected ransomware (per the company's 8-K filing this week), which said the cyberattack on February 3 "encrypted critical applications, and exfiltrated certain files." (Disclosure: I wrote this story!) Lee publishes dozens of newspapers, many of which still can't access files or systems on Lee's network. Several news outlets across the U.S. continue to face disruption and can't print all of their papers on time. The Freedom of the Press Foundation has a running list of affected outlets.
More: SEC EDGAR | The Daily Progress | The Register
Google's ad-tech can target natsec 'decision makers' and the chronically ill
Wired ($): Fascinating reporting by Wired, citing data obtained from Ireland's oldest independent human rights body, looking into how Google's ad-tech platform can be used to target ads at specific banned audiences, including people with chronic illnesses, financial distress, and those who work in the field of national security as "decision makers." The data is from DV360, Google's ads platform for high-end paying customers, which currently hosts as many as thousands of restricted "audience segments" that can target practically anyone — and very helpful to foreign adversaries (or hell, even potentially those here in the United States).
More: @jshermcyber | @doctorow tweets
~ ~
THE STUFF YOU MIGHT'VE MISSED
VC giant Insight Partners says it was hacked
Calcalist: Venture capital firm Insight Partners, which has invested in Wiz, Wix, Optibus, and more, confirmed this week it had been hacked, following a report from Calcalist. Insight said very little in its statement, but added that it had notified "stakeholders connected to Insight" (read: founders and investors) "irrespective of having shared data compromised." Ah, so some data was compromised... gotcha.
Inside one of NSA's hacks, according to China
@inversecos: Really interesting research looking at an alleged hack of one of China's top universities that China blamed on the U.S. National Security Agency. While the allegations can't be verified (yet), the research looks from China's lens about the attacks and how the attribution to the NSA went down. (We don't hear often about U.S. or Western-led cyberattacks, so this was worth flagging.)
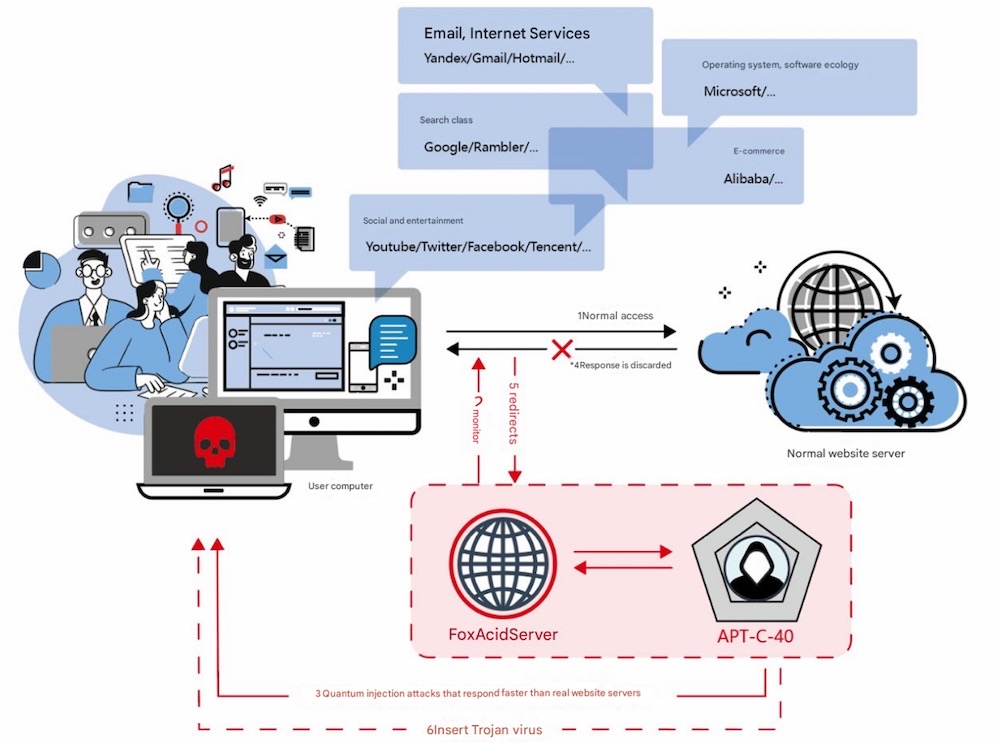
Google researchers warn of Russian attacks targeting Signal users
Google: Security researchers at Google's threat intel unit found evidence that several Russia-backed hacking groups are compromising Signal Messenger accounts using the built-in "linked devices" feature (for connecting the Signal mobile app to the desktop app). Targets are sent QR codes that, if scanned, will also deliver future messages to the threat actors, allowing for stealthy surveillance. Google said it's seen the notorious "Sandworm" hackers use this technique, often for targeting Ukrainian military units.
Network edge devices fueled hacking sprees in 2024
Cyberscoop: Turns out that 2024 was an absolute fustercluck for enterprise edge devices — the firewalls, VPNs and other access control systems that sit on the perimeter of your company's network. New research (Darktrace has its full report behind a sign-up form — ugh) found bugs in a range of Ivanti, Fortinet and Palo Alto devices, which put those companies' customers at risk from hackers breaking in. Some of the bugs were widely exploited during 2024, thanks to shoddy vendor coding and in the face of layoffs at some of these vendors. This comes in the same week as a new zero-day in Palo Alto Networks' firewall software (🫠) that is currently being exploited.
Microsoft patches Power Pages zero-day bug
MSRC: Microsoft has patched a zero-day bug under attack in its Power Pages website builder that allows malicious hackers to create new accounts with high-privileges on a customer's website. Microsoft said "affected customers have been notified." Let's just hope Microsoft hasn't emailed customers to an account that some never check, like it has in the past! (via @campuscodi)
Huge trove of Black Basta ransomware gang chat logs leak
TechCrunch: Notorious ransomware gang Black Basta (which has been largely quiet since the start of this year) had a year's worth of internal chat logs leaked online, thanks to security researchers at Prodaft. TechCrunch obtained the logs (which have since been made public) and pored over them; they include some interesting details about attacks, exploits, unreported targets, and some new victims. One of the hackers says they're only 17-years-old, while others discussed their concerns about getting vanned by the U.S. (and Russian!) governments. (Disclosure: I co-wrote this story!) @GossiTheDog has a good toot-thread on the highlights.
~ ~
OTHER NEWSY NUGGETS
Feds fine Warby Parker: The healthcare feds say eye-glass startup Warby Parker is on the hook for a $1.5 million fine after the company was found to have made security failings prior to a credential stuffing attack in 2018. The compromised data affected some 200,000 people, and hundreds of folks whose protected health information was also accessed. (via HHS [PDF], The Record)
Australia's Genea IVF reports breach: Some five days after its phone lines went kaput, Australian IVF giant Genea confirmed a cyberattack that "accessed Genea data." Whether that's customer or employee data, it isn't known just yet. But at least it was enough time to call in the crisis comms PR firm Porter Novelli to handle the company's scandal instead of responding to the Australian reporters who first reached out about the breach. (via Genea)
Record breaking crypto heist: Bybit, the world's second largest cryptocurrency exchange, was hacked. One of its cold (read: allegedly offline) wallets was compromised and some $1.4 billion worth of crypto stolen, tanking the price of Ethereum with it. Crypto investigator @ZachXBT linked the heist to North Korea, which wouldn't be a huge surprise given it's need for crypto to make nuclear weapons. If we start seeing bedazzled nukes, we know the North Korean regime was for sure behind the hack. (via TechCrunch)
$500k stolen from NioCorp in redirected payments: Someone broke into mineral discovery firm NioCorp's network and redirected $500,000 in vendor payments, likely to an account held by the hacker. The company disclosed the hack and theft in an 8-K filing with the SEC. (via SEC EDGAR)
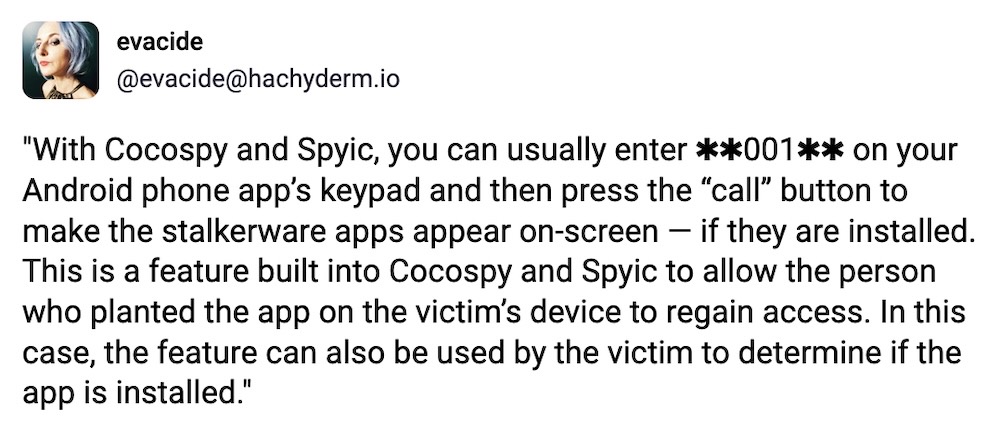
Cocospy, Spyic exposed as stalkerware operations: Enter the (at least) 22nd and 23rd stalkerware security incident since 2017, Cocospy and Spyic, two near-identical "stalkerware" mobile apps that can steal data from a victim's phone in real-time. A bug exposed millions of victims' data, as well as the email addresses of the bad people who signed up to spy in the first place. Those abusers' email addresses are now in Have I Been Pwned. I wrote about the breach, and also have some guidance on how to find and remove the spyware apps (if it's safe to do so). (Disclosure: I also wrote this story; busy week!) (via TechCrunch)
~ ~
~ ~
THE HAPPY CORNER
Welcome back to the happy corner. There's not much this week, aside from a couple of bonus cybercats.
In pretty funny (but also somewhat alarming) research, the folks at Truffle Security found a popular temperature controlled Eight Sleep bed exposed SSH access to any customer's bed by way of a backdoor update function. But, on the bright side, nothing an aquarium chiller couldn't fix. More from Bloomberg ($).
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
This week's cybercat-pup is Kenobi, whose human tells me that he protects the house from all the delivery drivers and suspicious people who have the audacity to pass by. That's some next-level perimeter threat detection, Kenobi. Who's the best pup? Thanks so much to Aly for sending in!

Keep sending in your cyber cats! (or a non-feline friend). Drop me an email at any time with their name and a photo, and they'll be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
And that's it for now — join me next week for the usual gamut of all the cyber news you need to know. Thanks for reading! As always, please get in touch if you have anything you want to share for the newsletter.
Catch you next,
@zackwhittaker