this week in security — february 25 edition
THIS WEEK, TL;DR
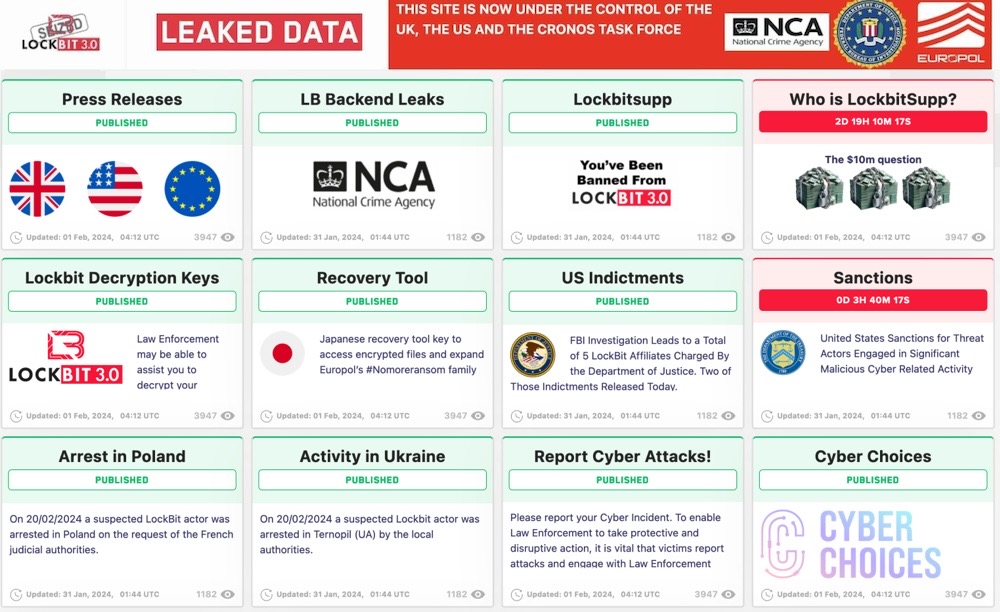
U.S. and U.K.-led operation disrupts LockBit ransomware, for now
Justice Department: Well, that was a week. Let's get started with LockBit, the notorious Russia-based ransomware operation that the U.S. and U.K.-led operation claimed to take down this week. U.K.'s National Crime Agency took over LockBit's dark web leak site and infrastructure (apparently by way of an old PHP vulnerability, whoops) and replaced the victims' data with LockBit's own internal files. Hack-and-leak, then name-and-shame. Several LockBit affiliates outside of Russia were arrested and sanctioned, effectively making it far more difficult for U.S. businesses to pay LockBit's ransom (but also ransoms for other ransomware gangs the affiliates are working with; and bonus @fs0c131y OSINT thread digging into the life of one sanctioned LockBit member). But as the end of the week rolled around, hopes faded that the LockBit takedown would last after LockBit's admins (or admin, singular) published a rambling statement giving off very "this is fine" energy, even with a hint of vengeance. LockBit's sites are back online, apparently sourced from backups that the feds missed. And after researchers linked LockBit to this week's "mass exploitation" of a new set of zero-days in the popular remote access tool ConnectWise, it seems as though LockBit is more determined to hack and extort than ever.
More: U.S. Treasury | TechCrunch | BankInfoSecurity | @joetidy | @vxunderground
Spyware leak offers rare window into China's state surveillance
Associated Press: From one blown cyber operation to another... This week saw a huge leak of hacking documents related to a Chinese government contractor called i-Soon, which was found to be spying on other governments — including India, Thailand and the U.K. — and targeting citizens and dissidents at home. The documents show how i-Soon hacks into other government agencies and the exploits — and hardware tools — they use. The hacks involve targeting Windows, Macs, iPhones and Android devices. After the leak, the Chinese hacking contractor reportedly told its staff to "continue working as normal." (Nothing to see here!) "We rarely get such unfettered access to the inner workings of any intelligence operation," said Mandiant's @johnhultquist, with the sheer delight of a kid in a candy shop.
More: SentinelOne | Washington Post ($) | BushidoToken | Krebs on Security | TechCrunch | @davekang tweets
U.S. health tech giant Change Healthcare hit by cyberattack
TechCrunch: One of the largest healthcare tech companies in the U.S., Change Healthcare, continues to experience outages following a cyberattack, which it has attributed to an unspecified nation-state actor. As one of the biggest prescription processors, the ongoing outage means thousands of pharmacies across the U.S. (and "all military pharmacies worldwide") can't dispense medications through a patient's insurance. (If you've never heard of Change, it merged with Optum in 2022 in a $7.8B deal, which allowed Optum to "gain access to data from millions of healthcare transactions covering a broad swath of the U.S. population." Change is now owned by U.S. insurance giant UnitedHealth — so it's absolutely huge.) Change Healthcare claims to handle around one-in-three Americans' patient records. Keep a close eye on this story as it develops. (Disclosure: I wrote this story.)
More: WSJ Pro ($) | AHA | Becker's Health IT | @zackwhittaker

~ ~
THE STUFF YOU MIGHT'VE MISSED
Microsoft to roll out logging after China hack
Cyberscoop: Microsoft came under heavy fire last year for a Chinese espionage campaign that hacked into the Microsoft-hosted email inboxes of several U.S. government officials. The breach wasn't the issue per se (although, not great), it was that the breach was only discovered because U.S. State Dept. officials had a higher-paid tier Microsoft account which allowed access to detailed logs. Of course, having to pay for access to logs that can tell you if you were breached is silly and Microsoft eventually (and reluctantly) reversed course. Microsoft "doesn't deserve any praise for caving to pressure," said Sen. Ron Wyden in a statement. "Like an arsonist selling firefighting services, Microsoft has profited from the vulnerabilities in its own products and built a security business generating tens of billions of dollars a year." Savage.
Biden cyber official sees 'promise and peril' in AI
Wired ($): White House's cyber advisor Anne Neuberger chats with @vermontgmg about AI, emerging cyber threats, and the Biden administration's plan for autonomous vehicle standards, 6G telecoms and critical infrastructure. Much of this is middle-of-the-road stuff as the government contends with a range of very fast, emerging threats, including AI-generated deepfakes, but a good read nonetheless on the broad approach the U.S. government is currently taking to today's threat landscape.
What happens to your sensitive data when a data broker goes bankrupt?
The Markup: We've all seen mergers, acquisitions and bankruptcies over the years that have seen our data shared, sold, or changed hands to more and more corporations. But when a data broker, like Near Intelligence – which boasted to have location data on 1.6 billion people — went bankrupt, it left open the question of what would happen to all of that sensitive location data? A new bankruptcy filing this week put restrictions on Near's "use, sale, licensing or transfer" of location data collected from sensitive U.S. locations (think healthcare facilities). More from @alng.
Avast ordered to stop selling browsing data from its browsing privacy apps
Ars Technica: Filed under "I can't believe it's not illegal" — except, well, it is: the FTC slapped antivirus and (ostensible) security giant Avast with a $16.5 million fee to settle charges that the company sold the sensitive browsing data of its customers to more than 100 other companies (and advertisers, think Google, Microsoft, and — ick — McKinsey) through its since-shuttered Jumpshot subsidiary. Avast is now banned from selling this data in future. The FTC was particularly scathing in its statement, given Avast claimed its own products would stop the very tracking it was doing at the time. Shame the FTC didn't cite its sources; this all came from a Vice–PCMag investigation in 2020, which prompted Avast to shutter Jumpshot altogether.
~ ~
OTHER NEWSY NUGGETS
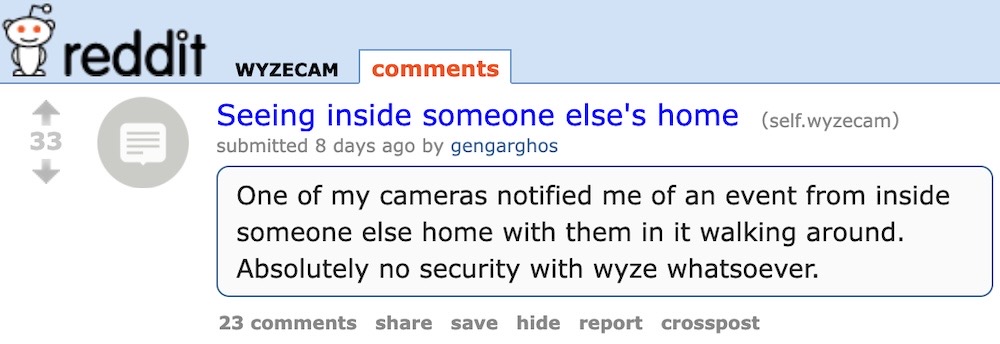
Wyze bug granted strangers access to stream data: Surveillance camera maker Wyze confirmed yet another bug allowed users access to image thumbnails from inside other people's houses. “We have now identified a security issue where some users were able to see thumbnails of cameras that were not their own in the Events tab,” Wyze cofounder David Crosby said, adding that at least 13,000 users were granted improper access to other people's thumbnails. This isn't even the first time it's happened. Remember, folks: if it's not end-to-end encrypted, someone else other than you can absolutely get access. (via The Verge, Ars Technica)
Vietnam plans huge DNA identity database: The Vietnamese government will later this year begin collecting biometric details — including iris scans, voice samples and "actual DNA" — per The Register — as part of the country's new national identity database. What could possibly go wrong; how much time do you have? Just last week revealed a security gap in Germany's e-ID scheme (more here) and India's Aadhaar program hasn't been able to keep its citizens' sensitive data secure or private. (via The Register, Vietnam Gov. News)
Code Tangerine means data breach: Australian telecom Tangerine said 232,000 people had personal information stolen in a data breach, including customer names, addresses, dates of birth, email addresses, and cell phone numbers the fruit-themed company said in a statement. While the telco touted its customer use of MFA, it turns out the breach was caused by the use of "login credentials of a single user engaged by Tangerine on a contract basis." Which is to say, it's still Tangerine's fault. (via Tangerine)
Mon portable, mon écoute électronique: The European Parliament asked its lawmaker members to have their phones checked for spyware after traces of hacking were found on two devices (though unclear how many individuals this pertains to). The lawmakers affected sit on the EU Parliament's defense and security committee, responsible for, well, security and defense policy across Europe. Another EU Parliament committee was already investigating the use of spyware on the continent, but faced considerable pushback and stonewalling from the member states who used spyware (including Spain). Shout-out to @SophieintVeld, one of Europe's most vocal lawmakers in the privacy space, who's calling on the EU Commission to investigate. (via Politico, @AntoanetaRoussi)
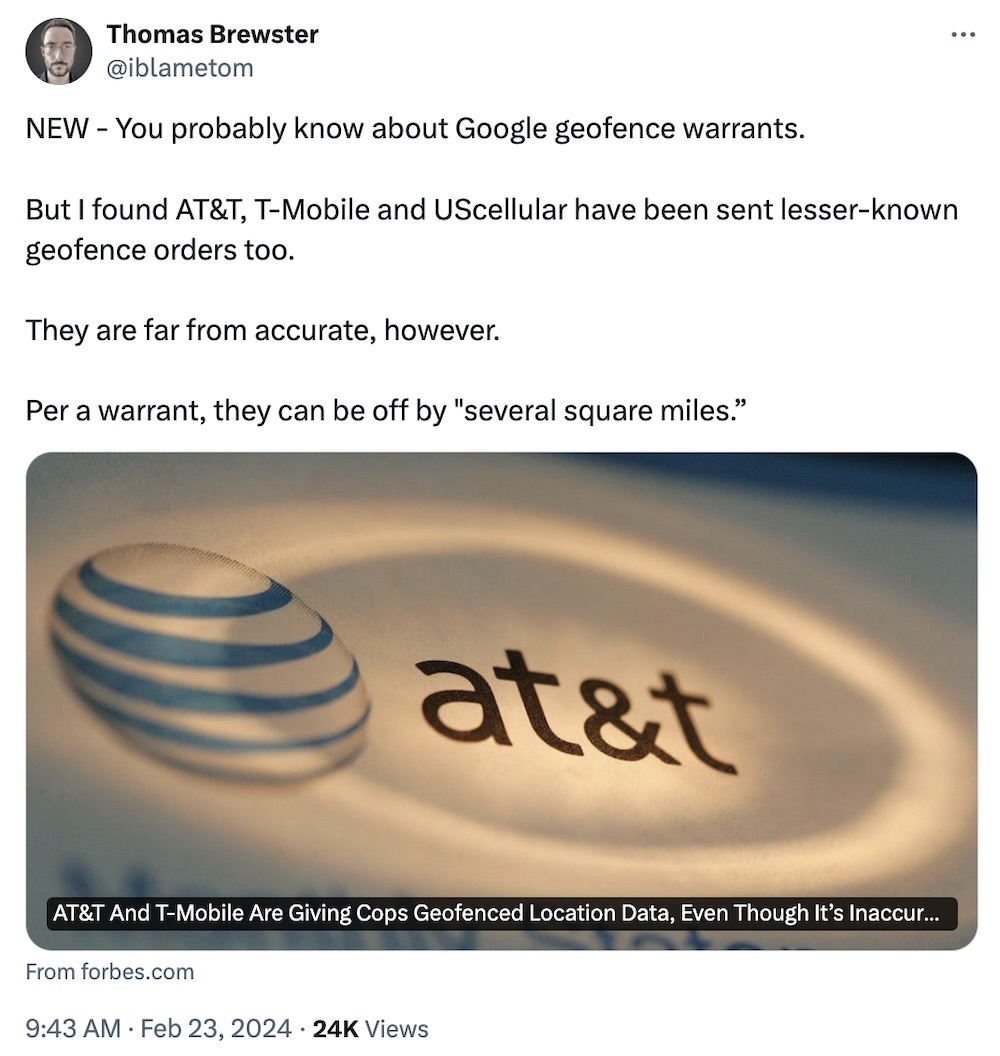
AT&T and T-Mobile give cops duff location data: Google effectively ended its geofence program in December after years of mounting criticism that cops can effectively reverse-engineer who was at the scene of a crime based on their cell phone location. Now, cops are turning to the telcos — which also store a lot of location data on its customers. Just one problem: that location data is derived from cell signals and isn't nearly as accurate as Google's, which gets precise GPS coordinates directly from a user's phone. Another square you can check off on your "what the fresh hell is this" bingo card, 2024 edition. (via Forbes ($))
~ ~
THE HAPPY CORNER
Breathe a sigh of relief. At last, it's the happy corner.
Next time your corporate internet seems like it's running on the slower end, maybe it's because someone in IT is playing Snake:

Signal announced it's rolling out usernames to the popular end-to-end encrypted messaging app. Finally a way to keep your phone number private using Signal. Excellent news! Heaps of praise from Lawfare. The update is in beta and will fully roll out to users in the coming weeks.
Moving on. So, how are yo..
And finally this week, @runasand looks at how the Norwegian government helps to stand up for high-risk communities, such as those targeted by other governments.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~

~ ~
CYBER CATS & FRIENDS
Meet this week's cyber-cat, Frosty, a mischievous kitty who can be seen here trying to rig a weight sensor to convince his human to double his daily treats immediately. Frosty can't hack when he's hungry! Many thanks to Samuel M. for sending in!

Please send in your cyber cats! Drop me a photo of your cyber cat (or non-feline friend!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
That's all for this week's newsletter. Join me next for the usual round-up from the week. As usual, if you want to get in touch, drop me an email any time with your feedback (and your cyber-cats!).
And if you're interested in supporting the newsletter or swag (shipped out regularly), check out the newsletter's Ko-fi page.
All the best, and see you next,
@zackwhittaker