this week in security — february 26 edition
THIS WEEK, TL;DR
Sensitive U.S. military emails spill online
TechCrunch: So, uhh, whoops? The U.S. Dept. of Defense secured a cloud mailbox server this week that was spilling terabytes of internal military emails, mostly belonging to USSOCOM, the military wing tasked with U.S. special military operations. The data was highly sensitive — including SF-86 questionnaires for vetting folks seeking security clearances — but unclassified. Still, not the sort of information you want entirely exposed to the internet without a password, but that's what happened. A security researcher found the data and provided it to me to get it secured. It took me an extra day and a half to get this data secured because, of course, nobody responded because of the long weekend, even though the data had been spilling for weeks already. Both the DOD and Microsoft, which runs DOD's Azure cloud, are investigating how this happened, and so far seem to be pointing the blame at each other.. On the bright side, at least we finally have an answer for what military grade security really means. (Disclosure alert: I wrote this story.)
More: Bloomberg ($) | CNN | Wired ($) | Fox News | @zackwhittaker | @k8em0
Signal would walk from U.K. if bill undermines encryption
BBC News: Encrypted messaging app Signal would "walk" from the U.K. if the government passes a bill that undermines the security of encryption under the guise of allowing authorities to scan encrypted messages for child abuse content. Dubbed the Online Safety Bill (because if it's a law undermining encryption, it must have an oxymoronically ironic name), the U.K. Home Office said the bill was to protect children. But, as is always the case with these ill-thought-out laws, the politicians don't realize that it would decimate U.K. cybersecurity. That's why Signal said it wouldn't bow to pressure to weaken its security for the sake of a former powerhouse in frosty waters. As Signal president Meredith Whittaker said, it was "magical thinking" to believe we can have privacy "but only for the good guys." (Writing this, I laughed to myself, "I wouldn't call the people running the U.K. right now 'good guys'." But actually, maybe that's the point.) It's a near-identical position also set out by WhatsApp last year that said it wouldn't weaken its security for one, or any country. Sorry, my fellow Brits, but you need better lawmakers.
More: Riana Pfefferkorn | The Guardian | Ars Technica | @mer__edith
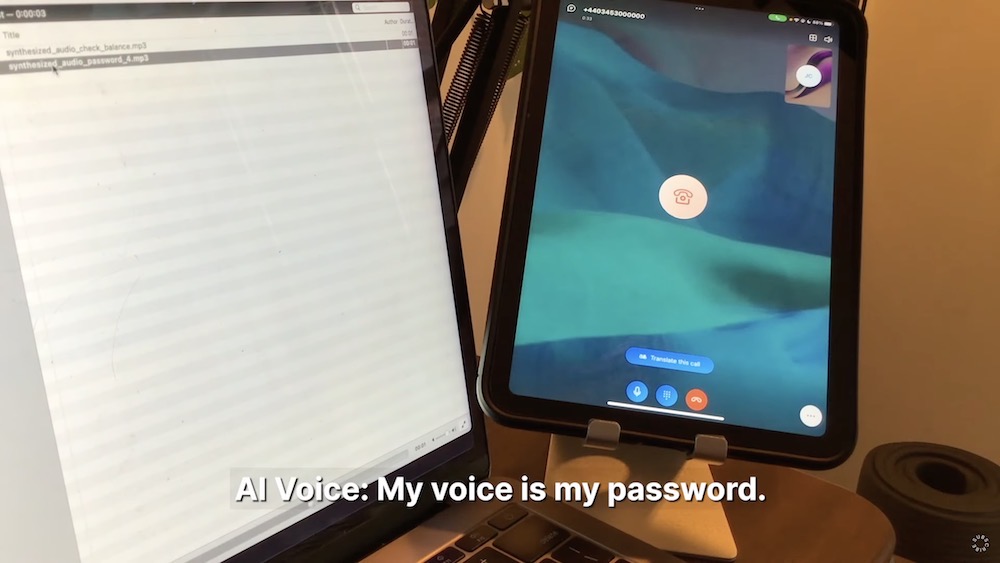
How I broke into a bank account with an AI-generated voice
Motherboard: Banks these days will try anything to make "passwordless" logins seem appealing, even if it means neglecting to use actual multi-factor authentication (because most still don't). No surprise that some banks, like Chase, TD Bank, Wells Fargo, and Lloyds Bank, claim to be able to recognize a person's voice and use it to progress through phone customer service. But, as @josephfcox proved this week, an AI-generated voice can also trick these systems into thinking they are real people. That's obviously a major flaw and shatters the idea that voice biometrics are foolproof.
Archive: Forbes ($) | More: Biometric Update | Futurism | @josephfcox tweets
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Supreme Court declines to hear NSA surveillance case
Cyberscoop: Remember a decade ago(!) when the Snowden leaks first dropped? Lawyers all this time have been fighting to get the legality of some of the Snowden revelations — specifically the NSA's collection of web traffic from internet backbones — challenged by the courts. But after almost-exactly ten years since the first tranche of classified documents dropped describing the NSA's secret surveillance capabilities, the case finally made it to the Supreme Court, which this week declined to hear the case. The NSA used its state secrets privilege card — effectively its "get out of jail free" card, so to speak – at the U.S. Court of Appeals for the Fourth Circuit. Since the Supreme Court declined to hear the case, that lower court decision remains in place, ending the case. More background from the Wall Street Journal ($).
Twitter's transparency efforts crumble under Elon Musk
Rolling Stone: Speaking of disclosing government surveillance, guess who's no longer revealing how many subpoenas, wiretaps, search warrants, or secret orders it received? Twitter, under Elon Musk's ownership. Rolling Stone reports that Twitter hasn't posted its transparency report figures — as it has done for years, just as other tech companies continue to do — since Musk bought the company. Twitter reveals these figures twice a year. One reason for this might be that there's basically nobody left to publish the figures. Forbes ($) reports that Musk quietly fired its democracy and national security policy team who protect human rights on the site. Like it or not, Twitter has done probably more than most tech companies in terms of efforts to support and defend online speech, especially fighting legal demands that attempt to curb free expression. Actually, TechDirt (as usual) has the definitive piece on exactly how and why Twitter did so. It's a shame to see this collapse under new management.
A new class of Apple bug is causing headaches
Trellix: An entire class of vulnerabilities found in an Apple feature designed to block remote zero-click spyware attacks could allow malicious apps to gain escalated privileges on an affected iPhone, iPad or Mac, and access sensitive data, such as messages, location data, call history and photos — precisely the sort of thing spyware would try to obtain. The bugs hone in on a new area of focus, specifically NSPredicate, and Wired ($) has a solid write-up explaining the ins and outs. Apple released patches, but clearly there's more for researchers to explore. It's not to say that all Apple devices are immediately or easily pwn-able, but independent researchers noted that this is why Apple devices rely on layered security defenses.
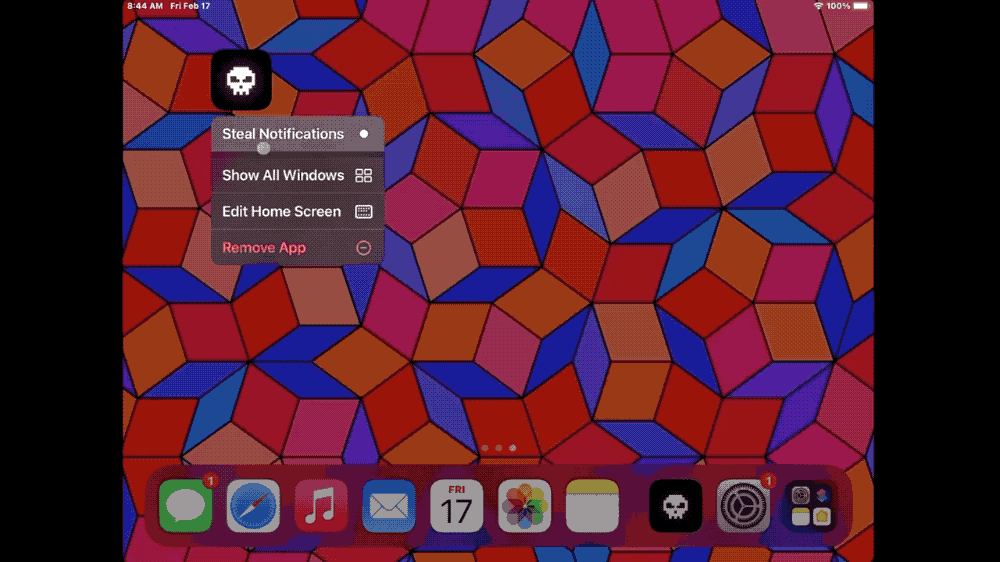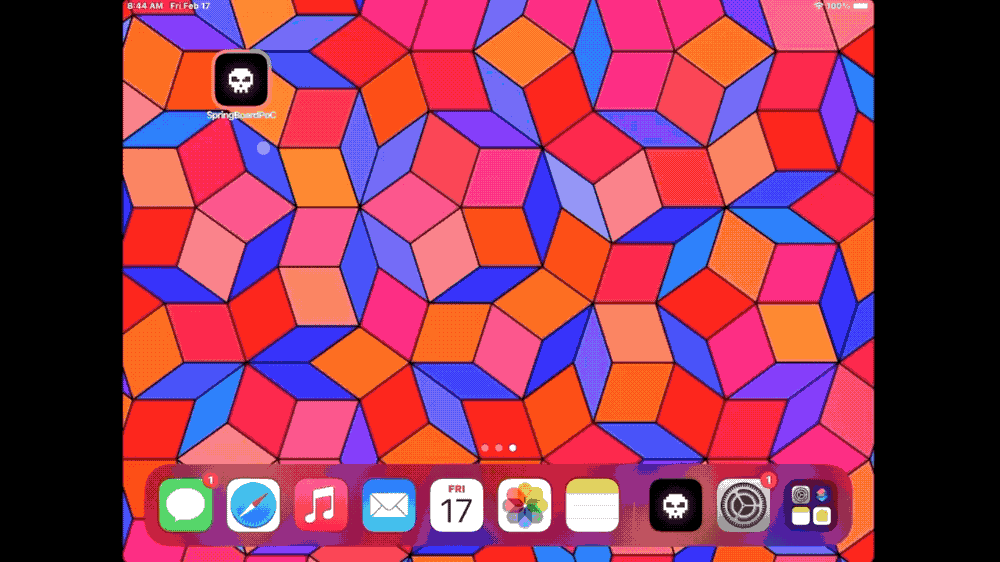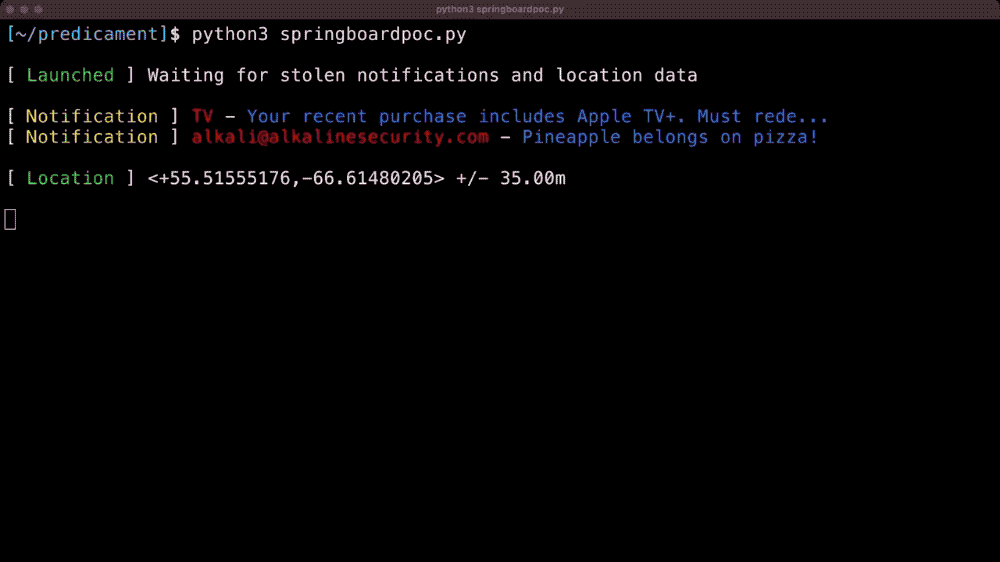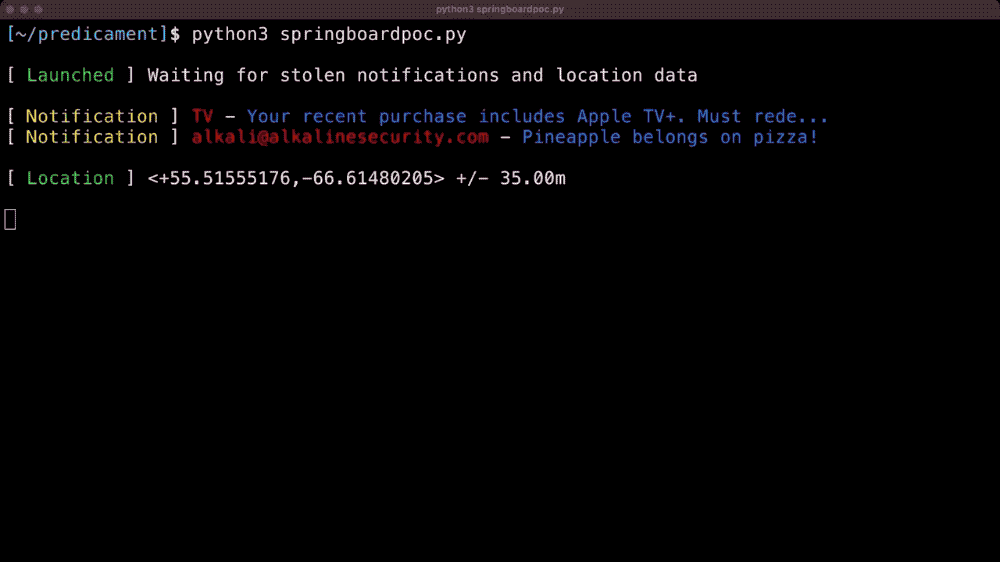
Let's build a Chrome extension that steals everything
Matt Frisbie: Manifest v3, the new way that Chrome will eventually handle browser extensions, faces ongoing criticism for restricting browser extensions and their capabilities, which can be harmful to privacy (more from the EFF for context). So, Manifest v3 is better, right? Right? Well, probably not, since Matt Frisbie built a Manifest v3 browser extension that's capable of... stealing pretty much everything from your browser as possible. This is a fantastic post — or rather, proof-of concept.
Trove of L.A. students' mental health records posted to dark web after cyberattack
The 74: The Los Angeles Unified School District, or LAUSD, the second-largest school district in the United States, was hit by a Vice Society ransomware attack last year, and it's still causing havoc. The 74, which does excellent reporting in the education space (as it often overlaps with cyber), covers the latest twist — that the hackers are now posting the mental health records of students to the dark web. This comes despite the school district's superintendent Alberto Carvalho downplayed the attack and its effects on students. Worse, students or parents had no idea — because while health records are covered under HIPAA and have to be disclosed in the event of a breach, psychological assessments are not, bafflingly. Again, for the millionth time, and for the folks at the back — the U.S. still doesn't have any federal data protection laws.
Valve set a trap to catch and ban thousands of Dota 2 cheaters
Polygon: Gaming giant Valve recently posted a fix to the wildly popular game Dota 2 to patch a vulnerability that was being actively exploited by third-party cheating apps. In doing so, Valve created a honeypot that allowed it to detect which players were exploiting the flaw that gave them an advantage over other gamers. As such, 40,000 players were banned as a result. Absolutely savage, but also fair play (excuse the pun)
Medibank says hackers broke in using stolen password, other flaws
Medibank: Australian private healthcare giant Medibank, which was hacked last year with close to 10 million Australians' personal details stolen, provided more details of the attack in its latest earnings report. Medibank said criminals initially accessed its systems using a stolen internal username and password combo used by a third-party IT service provider, but a firewall misconfiguration and other security problems allowed the hackers in. You can read more here, or see @Jeremy_Kirk for the highlights.

~ ~
OTHER NEWSY NUGGETS
Cyberattack stalls salad shipments: Produce giant Dole was forced to shut down its production plants in North America after a cyberattack — confirmed to be ransomware — resulted in stalled shipments of salad and other goods to grocery stores. Some grocery stores said they couldn't stock Dole salad kits on their shelves for days. Salad, love it or hate it, but I think we can all agree that food shortages caused by the knock-on effects of ransomware is not a trend we want to see. (via CNN)
Criminal hackers are facing layoffs, too: It looks like efforts by U.S. prosecutors might just be working if the latest statistics are anything to go by. According to reporting by @dustinvolz, CrowdStrike and Mandiant say ransomware actors are demanding less in ransoms and that ransom payments have fallen significantly. As such, some criminals are being laid off by their hacking crews. (via Wall Street Journal ($))
Dish down: For some reason, Dish Network's internal systems are down and nobody seems to know why. Dish is blaming an "internal systems outage" and is telling staff to wait to hear from leadership (which has so far said nothing) but some employees haven't been able to work for the past few days. It's not just phones and VPNs. "All of our systems are down," an internal email said. Are you thinking what I'm thinking? Well, one person said it's not that, but in absence of anything concrete, we probably shouldn't rule out something nefarious. Though, the best case scenario — that someone really, really screwed up — isn't much better, either. (via The Verge)
Call for EU-wide ban on spyware grows: A European digital rights group is calling on the EU Parliament's committee investigating the abuses of Pegasus and other spyware used by nation states to call for a ban on the use of spyware across the EU. The committee, however, doesn't have much power to ban or legislate on the matter. That said, the EU has the most progress we've seen in terms of investigating the use of government spyware so far. It's not clear on how the wider EU bureaucracy will respond to the committee's work to protect Europeans at large, but some national governments — like Greece — amidst the throes of its own Predator spyware wiretapping scandal — have already moved to ban spyware. Speaking of Predator, @runasand's startup Granitt is keeping track of known victims of the Predator spyware, based on publicly available information. (via The Record)
Google's app privacy labels are full of junk: Mozilla says that the data privacy labels that Google attaches to apps in its Android Play Store are mostly false or misleading. Case in point. "When you land on Twitter’s app page or TikTok’s app page and click on Data Safety, the first thing you see is these companies declaring that they don’t share data with third parties. That’s ridiculous — you immediately know something is off." (via Wired ($))
~ ~
THE HAPPY CORNER
Welcome to the happy corner. (We're a shoes-off happy corner, thank you.) First up this week, this joke is both brilliant and truly terrible, and yet I still chuckled.
I know we've all moved on from high-altitude balloons to suspicious sea buoys, but spare a thought for the poor blimps who just want to be noticed.
And finally. Friday marked 1 year since Russia launched its full-scale illegal invasion of Ukraine, and vigilante hackers marked the occasion in protest by mass-breaching dozens of Russian sites with a video depicting the Kremlin on fire. Slava Ukraini! 🇺🇦
If you have good news you want to share, get in touch at: this@weekinsecurity.com
~ ~
CYBER CATS & FRIENDS
Meet this week's cyber cat, Oogies, who as you can see is offering the strongest possible multi-factor authentication — a hardware security key cat. Absolutely unphishable. Unless they're treats, obviously. Many thanks to Christophe T-D. for sending in!

Don't forget to send in your cyber cats (fluffy non-feline friends are also welcome!). Email me a photo and their name, and they'll be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
And that's the lot for now. Hope you enjoyed this week's newsletter — if you did, please share on your social networks. And as usual, feel free to email any feedback or drop a note in the suggestion box. I'll be back next Sunday with the usual round up of security news.
Until then, have a wonderful week.
—@zackwhittaker