this week in security — february 27 edition
THIS WEEK, TL;DR
Hacktivists plot attacks on Russia with Ukraine government's urging
Bloomberg ($): War broke out in Europe after Russian forces invaded Ukraine this week, launching an unprovoked, long-anticipated attack on a democratic sovereign nation. The situation is unfolding hour by hour, but Ukraine stands strong to defend itself, both in major cities and online. Those with IT and cyber backgrounds are being enlisted to the Ukrainian IT army, per the vice prime minister, who's asking the hacker community to defend the country from Russia. The invasion was first spotted thanks to Google Maps as forces began to cross the border. Internet connections are spotty in places but Ukraine has largely been spared massive cyberattacks — so far — despite Belarusian hackers (aka UNC1151) and the Russian state-backed Sandworm rearing its ugly head again. @SecEvangelism, who was responsible for getting the Saudi Aramco network up-and-running after the Shamoon cyberattacks in 2012, flew to Kyiv to lend her assistance in case of a massive Russian cyberattack. Luckily, the networks remain largely up. She evacuated the capital before the aerial bombardment began and escaped to neighboring Romania, taking a convoy of people fleeing the country with her.
More: Reuters ($) | Wired ($) | NCSC | @joel_schectman | @fedorovmykhailo
Ukraine crisis: 'Wiper' discovered in latest cyber-attacks
BBC News: As the build up to an invasion grew this past week, European and international cybersecurity experts flooded to lend their help. Just before the invasion, as expected, the country was hit with a slew of cyberattacks — including flooding internet traffic at government websites linked to the Mirai botnet, but also wipers designed to destroy data on infected machines — though much of the capital's wider infrastructure and connectivity remains up. @kimzetter has a great piece on the "extremely targeted" attack involving the so-called HermeticWiper malware. Although cyberattacks were expected, we have yet to see Russia using the full force of its cyber capabilities. Ukraine is holding its ground, while Russian government sites are up and down.
More: BBC News | Zero Day | @dougmadory | @kimzetter
Behind the stalkerware network spilling the private phone data of hundreds of thousands
TechCrunch: This week I published a months-long investigation into a fleet of Android spyware apps that are exposing the call records, messages, photos, browsing history and precise location data of about 400,000 phones, including Americans. A Vietnamese startup is behind the operation, but refuses to fix the security vulnerability, which can be easily exploited. With no expectation of a fix or a way to contact those affected, there's a separate guide to help victims whose phones have been compromised to remove the spyware. The vulnerability is tracked as CVE-2022-0732. (Disclosure: I wrote this story.)
More: TechCrunch | EFF | @uscert_gov | @zackwhittaker
Risky permissions and security concerns in all five printer manufacturers
Consumer Reports: Great research from @yaelwrites, who found concerning permissions and security issues in all five printer brands of the 90-or-so printers that they recently tested. Printers might seem like benign office equipment, but are frequently targeted for their access to the wider network, plus they often store gobs of data on what's already been printed, like company secrets.
More: @yaelwrites
Police probe shows Missouri data was exposed for a decade before Post-Dispatch found it
St. Louis Post-Dispatch: A Missouri state website exposed hundreds of thousands of educators' Social Security numbers for a decade, a police report has found, debunking the state governor's baseless claims that the journalist, who discovered the exposed data, was a criminal "hacker" who should have faced charges. Bzzzt, wrong! A county prosecutor declined to press charges in the end, saying the reporter did nothing wrong. The bug was found to have been reported entirely ethically and in line with standard disclosure practices. But the governor used the case to score political points. The St. Louis Post-Dispatch does a good job on the post-mortem.
More: Ars Technica | Krebs on Security
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Veterans say ID.me locked them out of disability payments
Insider: ID.me has a lucrative contract with the Dept. of Veterans Affairs, but a public records request shows that more than 700 complaints were made about the identity verification service in a four-month span ending in January. Check out @caro1inehaskins' tweets on her report. There are some really harrowing stories here. ID.me recently got into hot water — and ultimately rejected from use at the IRS — for using a powerful 1:many facial recognition technology, which critics say is bad for security and privacy as it involves amassing huge stores of biometric data.
Inside the lab where Intel tries to hack its own chips
Wired ($): This week Wired took a look at Intel's security threat analysis and reverse engineering team, set up five years ago and tasked with hardware-hacking Intel's chips. The 20-or-so researchers work in labs in Israel and the U.S., and work to figure out ways to compromise the finished product. "The goal is to probe the chip for weaknesses under the same conditions an attacker would — albeit with prototypes or even virtualized renderings — using tools like electron microscopes to peer inside the processor's inner workings," writes @lilyhnewman. The team was launched around 2016 following a bruising time at Intel that saw security researchers find and disclose several chip vulnerabilities.
Visual voicemail credentials are not encrypted
Chris Talbot: Visual Voicemail transcribes your voicemails without having to call a number. But the credentials for Visual Voicemail are only Base64 encoded, not encrypted (which is to say, slightly scrambled but easily decoded). Because of this, if a phone number is hijacked, even temporarily (such as a SIM swap attack), an attacker can then gain access to their Visual Voicemail without needing their SIM card. The issue was tested on T-Mobile and AT&T. The networks said it was "not a concrete and exploitable risk," but was submitted as CVE-2022-23835.
Meet the secretive company helping the feds wiretap Facebook and Google users
Forbes ($): PenLink might be the most pervasive wiretapper you've never heard of, according to Forbes. The Nebraska-based company doesn't talk much about what it does, but @_jack_poulson recorded a talk at the National Sheriffs’ Association’s winter conference in Washington of a PenLink employee explaining what the company does — and how it helps tech companies like Apple, Facebook and Google provide data to police in response to a legal order. Several of these companies exist, often called trusted third-parties, though Neustar, one of the biggest wiretappers-for-hire years ago, no longer works in the space.
~ ~
OTHER NEWSY NUGGETS
Academics publish method for recovering data encrypted by the Hive ransomware
The Record: A team of South Korean researchers have a new paper detailing a way to recover files encrypted by the Hive ransomware without needing to pay. The researchers say vulnerabilities in the encryption algorithm (a classic mistake) allows them to "sufficiently" guess what should've been a random keystream. With that, a large portion of the master key was derived, which can be used to decrypt up to 98% of the victim's encrypted data.
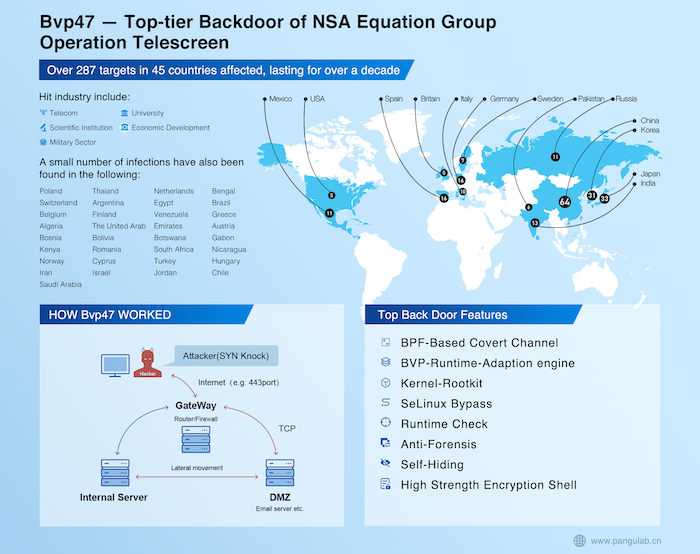
Chinese company doxes apparent NSA hacking operation
Motherboard: Chinese cybersecurity company Pangu Lab has accused the NSA of authoring a hacking tool that's been used over the past ten years. In a report out Wednesday, the lab said researchers first looked at a particular malware in 2013, but couldn't figure it out. Then, when data leaked on the Equation Group (widely believed to be NSA) by the Shadow Brokers, the lab connected the dots and realized the malware was created by Fort Meade. Some are wondering if this is part of a new strategy of naming-and-shaming — something the U.S. does a lot, but less so from China.
Who is policing the location data industry?
The Markup: Our security and privacy these days is wrapped up in the massive amounts of data collected on us, often through apps. A big part of that is location data, collected and sold by data brokers, which are known to sell this data to the U.S. military. Google and Apple tried to crack down on these location-collecting apps by banning the more egregious location-gathering SDKs, like X-Mode, but to little effect. The Markup found that data brokers are still collecting data, but directly from the source — the app developers. It's complicated, but as usual The Markup explains with precision detail.
~ ~
THE HAPPY CORNER
To submit good news for the happy corner, reach out: this@weekinsecurity.com. More next week.
~ ~
CYBER CATS & FRIENDS
This week's cyber cats are Tom (left) and Yoyo (right), who just like their human have moved from Seoul, to Hanoi, to London. International jet setting side, these cats look like they're about to drop the hottest album of the year. Thanks to @pearswick for the submission!

Don't forget to keep sending in your cyber cats (and their friends!). Drop me an email here with their name and photo, and they will be featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for this week, thanks so much for reading. On a personal note, my thoughts are with everyone in Ukraine. I will continue to keep you apprised of pertinent cybersecurity developments from the region each week, as well as the rest of the week's news. Feel free to send any feedback via the suggestion box, or drop me an email.
Stay safe, friends.