this week in security — february 4 edition
THIS WEEK, TL;DR
U.S. disrupts Chinese botnet targeting critical infrastructure
Justice Department: Months ago came the news that Chinese spies (aka Volt Typhoon) had burrowed into critical infrastructure across the U.S. and Guam to plant malware, ready to activate to cause disruption in the event of a Chinese invasion of Taiwan, for example. This week came the news that the U.S. had disrupted that botnet made up of hacked devices, mostly end-of-life small office and home office (SOHO) routers. The malware, dubbed KV Botnet, was wiped from routers during a U.S. court-authorized operation. During a House hearing at the same time the botnet disruption news dropped, the heads of the FBI, CISA and the outgoing (well, now gone) NSA director gave some of the strongest words yet on the threat posed by the China-backed hacking, including accusing China of trying to "wreak havoc and cause real-world harm." CISA director Jen Easterly said the Chinese activity discovered so far was "likely just the tip of the iceberg."
More: Wall Street Journal ($) | Reuters ($) | @dustinvolz | @ryanaraine
Ivanti releases patches for zero-days under attack, but finds another
TechCrunch: Not great news if you're an Ivanti VPN customer (and there are plenty of them): the company says it's found another zero-day under active exploitation, on top of the previous two that were recently found. German cyber authorities say they have knowledge of "multiple" systems compromised by the new zero-day. The s(h)ituation is so bad that CISA has given federal agencies just 48 hours (yesterday!) to disconnect vulnerable Ivanti VPN appliances. On the bright side, at least there are now patches for all of the vulnerabilities, so patch already if you haven't already!
More: Ivanti | Bleeping Computer | SecurityWeek

Remote access firm AnyDesk says production systems hacked
Bleeping Computer ($): From one trash fire to another — especially for the orchestrated timing. In a late Friday afternoon disclosure, remote access software maker AnyDesk said its production systems were hacked and brought in CrowdStrike to run incident response. AnyDesk reset customer passwords and revoked its internal certificates. But the impact of the intrusion remains unclear (and likely ongoing). AnyDesk has more than 170k customers, including 7-Eleven, Comcast and the United Nations, per Bleeping Computer. The software is also popular for bad actors for persistent access to networks. It's unclear if data was stolen during the intrusion, but its code-signing certificates were reportedly taken, potentially allowing the threat actors to package malware in legitimate-looking apps. Expect more news to drop soon on this developing incident...
More: AnyDesk | BankInfoSecurity | BornCity | @MalwareJake | @_JohnHammond
~ ~
THE STUFF YOU MIGHT'VE MISSED
There's so much data, even spies are struggling to find secrets
Bloomberg ($): The intelligence agencies' problems are only getting worse with more and more data, so much so that spies are struggling to find secrets amid a vast ocean of unimportant, well, noise. The U.S. government is increasingly embracing OSINT, or open-source intelligence (including commercially available data — think data sourced from your smartphones), and relying on internal tools similar to ChatGPT that use AI to sift through the data.
Mastodon fixes remote account hijack bug
Mastodon, GitHub: The makers of Mastodon, the open source decentralized social platform, rolled out a bug fix this week that patches a "critical"-rated vulnerability that allows the remote user impersonation and takeover of a person's account. More details are expected out by Feb. 15. Patch your instances if you haven't already! More from @fj in a Mastodon post; how fitting.
Apple fixes zero-day WebKit bug in VisionPro
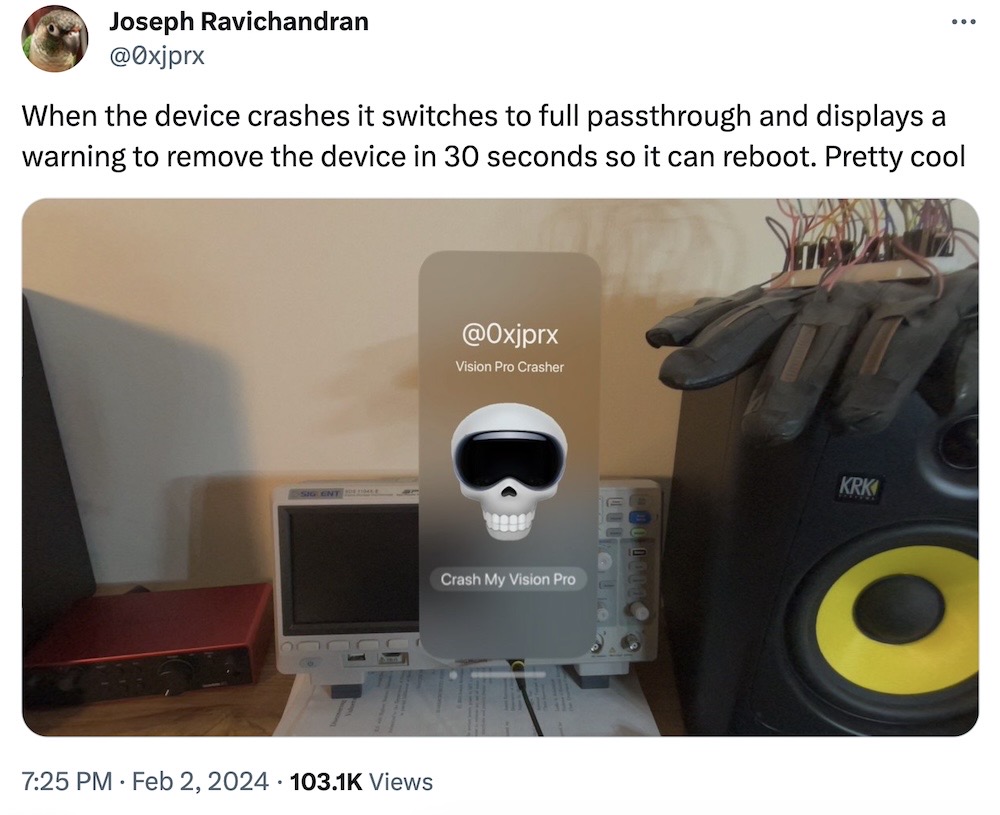
TechCrunch: Apple has ported a patch for an actively exploited zero-day flaw in WebKit, which was initially fixed in iPhones, iPads, Macs and Apple TV, to... Apple's brand new mixed reality headset Vision Pro. WebKit is used across Apple's devices, so it's not uncommon to see WebKit bugs affect multiple devices, even if exploitability isn't clear. Unsurprisingly, Apple declined to say if the vulnerability was actively exploited on the headset itself. (Disclosure: I wrote this!) However, in seemingly unrelated news, it looks like the Vision Pro saw its first ever kernel-level exploit (on launch day, no less). Congrats @0xjprx!
Florida teenager key suspect in 0ktapus hacking group
KrebsOnSecurity: A 19-year-old Florida man has been charged with wire fraud and identity theft for allegedly SIM-swapping victims to steal cryptocurrency. The teenager is also believed to be a key member of the criminal hacking group, dubbed "0ktapus" (also known as Scattered Spider), for its ability to break into tech companies' by spoofing Okta's login pages, including Twilio and others. @briankrebs dives into the hacker's history and how he was caught.
After NY settlement, stalkerware makers appear shuttered
TechCrunch: Last year, a consortium of tech companies registered in New York and Florida settled with the New York attorney general's office for illegally promoting spyware, specifically PhoneSpector and Highster, which the companies developed. Since then, the "stalkerware" maker appears to have shut down — taking the phone surveillance operations offline with it. The state's action fell short of a ban, unlike the FTC's recent moves against spyware makers, but appears that regulatory action is having an effect. (Disclosure: I wrote this, too!) Speaking of stalkerware, though... Swiss media NZZ did a deep dive into Spyhide (auf Deutsch; via @maia), an Iranian-developed stalkerware operation uncovered last year, which subsequently shuttered after a failed rebrand.
~ ~

~ ~
OTHER NEWSY NUGGETS
Cloudflare reveals Thanksgiving hack-but-no-breach: In a blog post this week, Cloudflare said it was briefly compromised by (likely) state-backed attackers during Thanksgiving 2023. The hackers didn't get far and no Cloudflare customer data (or systems) were affected. But the line-by-line account of what happened is a pretty interesting (and transparent) read. Cloudflare said it failed to rotate a token from Okta's support system hack back in October. (via Cloudflare)
Grandoreiro malware operators arrested: Brazilian police say they have disrupted a criminal operation behind the Grandoreiro banking malware, which relies on Azure and AWS to host their infrastructure, per ESET researchers tracking the group. The malware botnet has been operational since at least 2017. (via The Record, ESET)
Apple says U.K. could 'secretly veto' security updates: While the U.K. brought in a new "secure by design" law to bake in better security controls to IoT devices by default, the U.K. is now looking to undermine user security at-large by proposing new rules allowing government ministers to veto new security features introduced by tech firms. Yes, the hypocrisy is astounding; and no, it doesn't make sense (unless you're a U.K. lawmaker, apparently). This isn't a new threat, per se, but it's ramping up after the last crypto battle wasn't actually solved but merely kicked down the road. Well, we're on the road again and Apple is getting feisty again (since it's largely the one pushing these security and privacy tools). But it's interesting and notable that Apple hasn't published anything on its own website about the issue though. (via BBC News)
Layoffs hit Proofpoint, Okta, and Netography: Layoffs have been brutal of late and my heart goes out to all those affected. This week, Proofpoint's all-male leadership laid off 280 positions across the company. I asked a company spokesperson if the company is presently profitable; the spokesperson declined to comment (welp). Okta laid off 7% staff (about 400 employees) almost-exactly a year to the day after it laid off hundreds back then. SecurityWeek said this week that Netography also laid off some of its staff. It makes you wonder why executives at these companies aren't publicly cutting their own salaries and bonuses instead of laying off the employees who, let's be honest, do the actual work. (via SecurityWeek, TechCrunch )
~ ~
THE HAPPY CORNER
At last, it's the happy corner. Let's check in with Elmo, since, well, he asked.
Some actual good news: A consortium of organizations are standing up to attempts to silence journalists by Appin, an Indian startup accused of hacking-for-hire. Several media outlets pulled their stories about Appin after the startup secured a New Delhi court ruling, including U.S. outlets that have no discernible link to India and had no actual reason to comply. But Techdirt isn't budging, nor is Muckrock, the organization that runs DocumentCloud used by journalists and media to host documents, and, of course, the internet rights group EFF. 🙌 Move over, Streisand effect. Maybe it's time we call this the "Appin effect." Read more on Wired ($) about this project.
Moving on. For those who are wondering which season of Crypto Wars we're in, ask these two world-leading cryptography buffs:
In this edition of "What Can We Run 'Doom' On?", it turns out you can run the classic first-person game Doom on a... *checks notes* a piece of gut bacteria. I know nobody asked for this, but now you know.
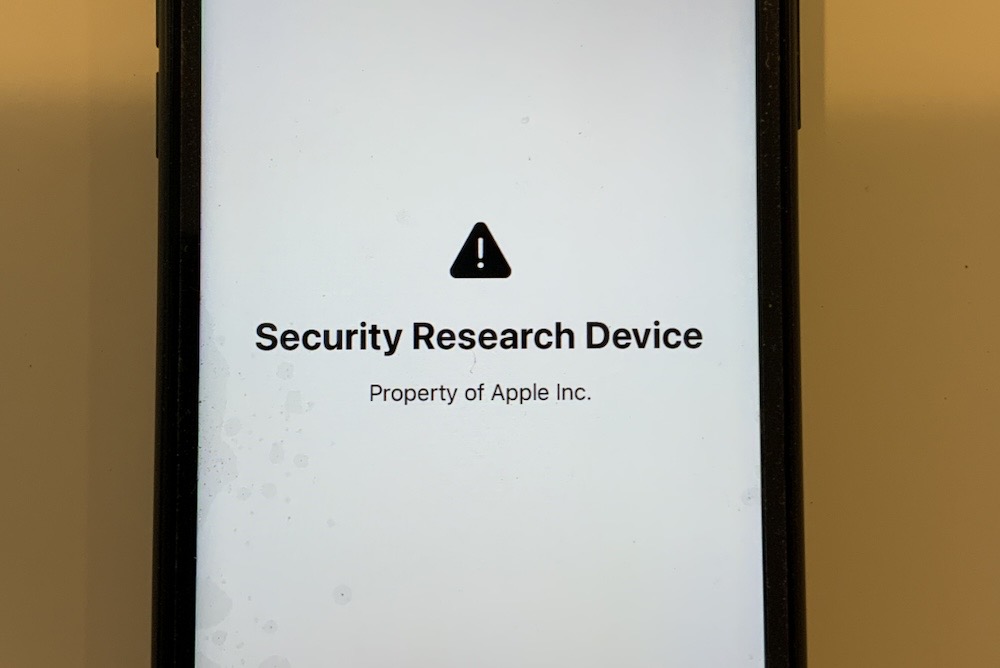
And lastly. If you're curious what Apple's security research devices look like, look no further. These are the special Apple-modified iPhones it gives out to security researchers. Granted, they don't look that much different from a regular iPhone, but really it's the innards that are the real goods. More photos here.
If you have good news you want to share, get in touch at: this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Eevee, this week's very relaxed cyber cat. You would be, too, if you also used unique passwords and MFA (better yet, passkeys!) on every online account. It's the basics that matter. Good advice, Eevee. Many thanks to Neil A. for sending in!

Send in your cyber cats! Email me a photo of your cyber cat (non-feline friends welcome!) with their name and they will be featured in an upcoming newsletter!
~ ~
SUGGESTION BOX
A busy one this week, and by the sounds of it, next week might be as well. Take care of yourself, and be kind to others.
As always, you can get in touch with me by email any time if you want to drop me any feedback. I'll be back next Sunday with the usual round-up (and post-mortem) of the past seven days. If you haven't checked out how to support this newsletter, check out my Ko-fi!
All my best,
@zackwhittaker