this week in security — february 6 edition
THIS WEEK, TL;DR
iPhone flaw exploited by second Israeli spy firm
Reuters ($): Move over NSO, there's another major spyware player in town — literally. According to Reuters, a company called QuaDream is a smaller, lower-profile Israeli firm that was simultaneously exploiting the same vulnerability in iPhones last year as NSO. The exploit, which Citizen Lab discovered and called ForcedEntry, bypassed the new protections that Apple put in iPhones to make NSO-style zero-click attacks more difficult. At the time Google researchers called the exploit "one of the most technically sophisticated exploits" ever. But turns out the very secretive Israeli startup QuaDream, known to sell to foreign governments like Saudi, Mexico and Singapore, had built a similar exploit on their own. That must be bruising to NSO's ego, but it's a reminder that NSO isn't by far the only spyware maker in play, per @RonDeibert.
More: @billmarczak tweets | @iblametom
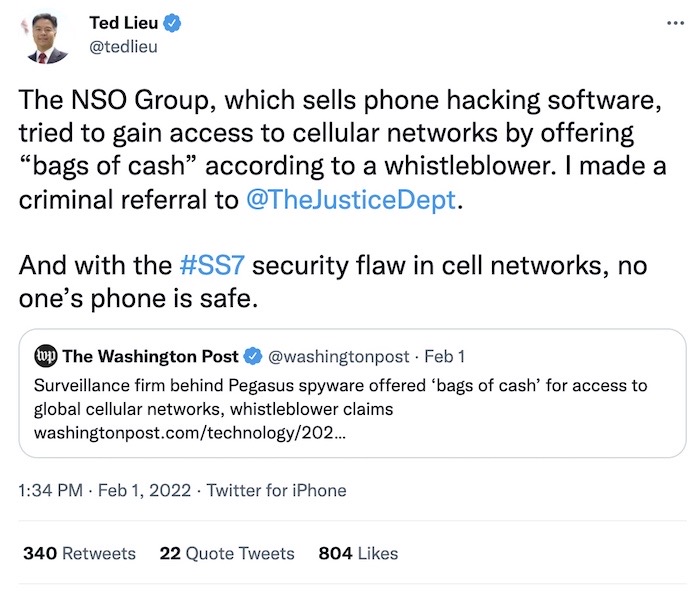
NSO offered US mobile security firm ‘bags of cash’, whistleblower claims
The Guardian: Incredible reporting from The Guardian (and others) which revealed that NSO allegedly offered "bags of cash" for access to the U.S. phone network. NSO says it can't hack into U.S. phone numbers — though that hasn't stopped NSO hacking the phones of Americans with foreign country codes. But whistleblower Gary Miller said NSO asked a U.S. company that helps to protect the decades-old and very-flawed SS7 network — which without fixes can be abused to track people's locations — under the assumption it would help NSO "enhance" its hacking and snooping capabilities. "This should terrify every American," said Rep. @tedlieu on the claims.
More: Washington Post ($) | @jsrailton | @fbdnstories
North Korea hacked him. So he took down its internet
Wired ($): Ever have one of those days where you just hate everything? Some people let it go, and some people get even. Meet a hacker who goes by P4x, who was targeted by North Korean hackers in early 2021 with a backdoor. It failed, but left P4x angry. With a feeling that there's "nobody on our side," P4x took an unusual step and hacked back by targeting the regime's central routers — which took down North Korea's tiny internet for several weeks in the process. Come for the storytelling, stay for the ending. Clearly, Hell hath no fury like a scorned hacker.
More: @a_greenberg tweets | @BlakeSobczak
Biden administration forms cybersecurity review board to probe failures
Wall Street Journal ($): The U.S. has set up a Cybersecurity Review Board (CSRB), which is modeled on the NTSB, the agency that investigates air and train crashes. Instead, the CSRB will probe the lessons learned from past cyber incidents and attacks, and how to prevent them in future. The idea for the body was created in the wake of the SolarWinds espionage campaign, but a year later was finally set up just in time to tackle the fallout from the Log4j bug. The board will see participation from members both in government and in the private sector, including @argvee, @k8emo, @dalperovitch and more. The expertise from both sectors will help with the board "study high-profile cybersecurity episodes and share comprehensive findings with the public."
More: Nextgov | @ericgeller | @CISAJen tweets
Ransomware roundup: KP Snacks; European oil facilities; Kronos fallout
The Register, BBC News, Threatpost: This week saw British salty snack maker KP hit by ransomware, and the company said it doesn't know how long it'll take to get back up and running, leaving pubs and stores potentially without supply. Meanwhile in continental Europe, several oil facilities were hit by ransomware, though there's no evidence yet that it's coordinated. Three companies were impacted across Germany, Belgium, and the Netherlands. And, Threatpost reports that the fallout from the ransomware attack on workforce management giant Kronos continues to grow, weeks on from the pre-Christmas attack, and the company is facing class action suits as the company continues to claw its way back online.
More: BBC News | Threatpost
~ ~
~ ~
THE STUFF YOU MIGHT'VE MISSED
Facebook investor Peter Thiel secretly funded a startup that hacked WhatsApp
Forbes ($): Filed under extremely ironic: Billionaire investor Peter Thiel, an early investor in Facebook and co-founder of controversial analytics startup Palantir, invested at least $10 million in a "cyberwarfare" startup called Boldend, which built an exploit for no other than Facebook-owned WhatsApp. Boldend got the investment via Thiel's investment vehicle, Founders Fund. @iblametom notes that Thiel also invested in Clearview AI, which infamously scraped 3 billion public photos from social media giants — like Facebook.
ID.me is raising concerns among rights groups for its data collection
Insider: @caro1inehaskins has a deep-dive on ID.me, the identity provider soon to be used by the IRS, which will require taxpayers to enroll their identity with the provider before they can access their IRS records online. But as noted, there are many concerns — not least with the amount of data that ID.me collects, including biometric data. One of the many problems is that there's no public policy that says ID.me won't voluntarily hand data to law enforcement. And without a transparency report, we have no idea what's been handed over already.
U.S. foes evade sanctions by deploying digital warfare tech to hide vessels at sea
Associated Press: Fascinating story on how technology, normally only available to world militaries, is being used to hide the locations of rogue ships trying to circumvent U.S. sanctions. One company says there were more than 200 vessels involved in over 350 incidents in which GPS locations were electronically manipulated. Definitely worth the read.
Microsoft says multifactor adoption remains low
Dark Reading: According to Microsoft's telemetry, some three-quarters (78%) of organizations that use Microsoft's Active Directory don't employ multifactor authentication for their user accounts. That's a major problem, since password spraying remains a major attack route.
~ ~
OTHER NEWSY NUGGETS
How $323M was stolen from a blockchain bridge called Wormhole
Ars Technica: A good explainer here on how $323 million in cryptocurrency (sorry, I still can't bring myself to say "crypto" full-time, I'm working on it) was stolen from Wormhole, a blockchain bridge, which are used by decentralized finance services that rely on two or more chains, each with different rules and processes. More technical details can be found in this tweet thread, too.
WSJ and other News Corp. properties hacked, believed linked by China
Wall Street Journal ($): This is one of the biggest fears that reporters can have — that their files, notes, stories and sources could be compromised. WSJ reported this week on its own breach, which saw hackers "likely involved in espionage activities to collect intelligence to benefit China’s interests" compromise reporters' emails and Google Docs, including drafts of articles. WSJ's backend cloud is run by Google, though there's no indication Google was breached. It comes in the same week that Coinbase's content management system for writing and publishing stories was also reported compromised, which the site confirmed allowed "someone accessing an API to trade on nonpublic information ahead of the publication of at least one article." Props to both news outlets for their candor and transparency. It almost makes you wonder how many other news orgs have been hacked over the years and said nothing...
Inside Trickbot, Russia's notorious ransomware gang
Wired ($): Incredible reporting from Wired this week after it viewed internal messages from the Trickbot ransomware group, one of Russia's most notorious and ruthless, blamed for hitting hospitals and medical centers all over the U.S. It's a fascinating new insight into the crime group, — which last year was temporarily halted after U.S. Cyber Command launched an operation to disrupt some of its activities — and includes details about how the operation is structured and works. @mattburgess1 has more in a thread.
~ ~
THE HAPPY CORNER
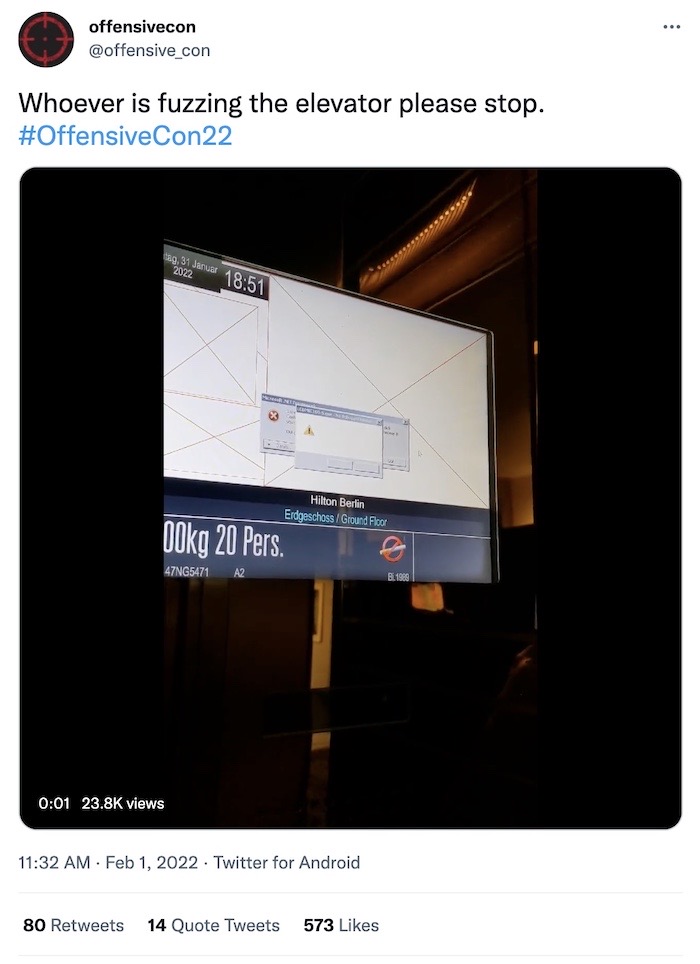
Right, let's see what we have in the happy corner. @offensive_con was in full swing this week, but, please folks, stop trying to hack the elevators.
Meanwhile, @shehackspurple has a really empowering story about workplace stress, yelling, and the art of de-escalation. A reminder to all that at the end of the day, we're all people trying to co-exist and why bad news doesn't have to involve lost tempers and raised voices.
If you want to submit good news from the week, reach out! this@weekinsecurity.com.
~ ~
CYBER CATS & FRIENDS
Meet Chuck, who features this week. Chuck is a snail that literally doesn't have the brain power for the cybers, but according to their human, deft at risk management through constructing lettuce caves and dragging provisions under their cuttlefish bone, which helps keep their shell healthy. (You learn something new every day, folks.) Big thanks to @joebeone for the submission!

Please keep sending in your cyber cats (or their friends). You can drop me an email here with their name and photo, and I'll make sure they're featured in an upcoming newsletter.
~ ~
SUGGESTION BOX
That's all for this week, cheers for reading. As usual the suggestion box is open, or drop any feedback to this@weekinsecurity.com. Take care and be well.