this week in security — february 9 edition
THIS WEEK, TL;DR
Iowa's caucus reporting app could've been easily hacked
ProPublica: Iowa was at the top of the news this week — not for the caucus per se, but because the horrendous app that was designed to make the reporting process faster spectacularly crapped out. Though security wasn't to blame, the conversation quickly turned to "what if" when ProPublica got hold of the app and found it wasn't using basic security mechanisms (including a lack of HTTPS and other things). Motherboard also got a copy of the app and ripped it apart (because of course they did, classic Motherboard) and found that the app was an absolute disaster. Homeland Security reportedly offered to test the app but was basically rejected. @fs0c131y also looked at the app's back-end infrastructure with hilarious (or depressing?) results. Anyway, this is exactly why elections on the internet are dumb, says @gregotto.
More: Motherboard | Politico | @fs0c131y
Feds use phone app location data for immigration enforcement
Wall Street Journal ($): Not surprising and yet still shocking. The feds, specifically ICE, are buying access to the location data collected by apps and sold by data brokers and advertisers for use at the southern border to track migrants, among other things. ICE spent millions on the data instead of obtaining warrants — a loophole that's legal, but hasn't yet been tested in court. In some identified cases, police records didn't say how they got the location data used for arrests, so clearly it's something they wanted to hide. @WolfieChristl has a good tweet thread on this.
More: @mhackman | @rebeccaballhaus
Mysterious new ransomware targets industrial control systems
Wired ($): Ekans (or Snake backwards) is a new malware — specifically ransomware — that targets industrial control systems (ICS) devices, the sorts of kit you find in energy grids and water works. Given ICS devices are high value targets and can cause considerable disruption if attacked, there's an ongoing scramble to better understand the malware. Dragos said it's likely launched by cybercriminals, not a nation-state. Not that much reassuring, as @a_greenberg put it. It's not the first of its kind; Megacortex was the first, making its debut early last year.
More: Dragos | Ars Technica
Ancestry.com refused a search warrant for access to its DNA database
BuzzFeed News: Ancestry.com, one of the largest DNA profiling sites, was served an out-of-state warrant that it refused to comply with on "jurisdictional" grounds — which is within its right. Ancestry.com is based in Utah and the warrant came from Pennsylvania. The fact is that police are only a technicality away from having to hand over gobs of user data.
More: Ancestry.com | TechCrunch
Cybersecurity giant Darktrace haunted by its past
Forbes: This was an incredible story — must've taken @iblametom an absolute age to nail down. Brewster went down the Darktrace rabbit hole, a cybersecurity giant valued at $2 billion. The story follows Sushovan Hussain, a convicted fraudster who's been involved in Darktrace but was jailed for fraud following his role in the collapse of Autonomy. But the report goes deeper and reveals sexual harassment, inappropriate conduct, and aggressive tactics. Incredible reporting.
More: @iblametom
Cisco flaws put millions of workplace devices at risk
Wired ($): Bugs in Cisco Discovery Protocol, which lets Cisco devices see each other on the same network, could be used to break out of a segmented network. If properly exploited, a skilled hacker with a foothold on a network could traverse the network with relative ease. Armis found the bugs and disclosed them to Cisco, which released patches for the bugs this week. Cisco said there's no (current) evidence of active exploitation.
More: Armis
Twitter says state-backed actors may have accessed users' phone numbers
Reuters: Twitter said a bug that allowed a security researcher in December to match randomly generated phone numbers to Twitter accounts may have also been used by nation-backed hackers. Cool, cool. I broke the story first back in December. Twitter wasn't thrilled, and suspended the researcher's accounts. But now it seems that discovery helped find more nation-backed activity on the platform. Twitter, unpredictably, didn't say much on how it reached that conclusion. (You're welcome, I guess? Who knows.)
More: TechCrunch | @zackwhittaker
~ ~
THE STUFF YOU MIGHT'VE MISSED
Dear Ashley Madison user, I know everything about you. Pay up or else
Ars Technica: An extortion scheme targeting Ashley Madison users is still going on some four years after the breach laid bare millions of user accounts. Researchers say "several hundred" emails have been sent of late, threatening former users to turn over bitcoin in exchange for their silence. It's not the first extortion attempt — shortly after the breach, two members reportedly died by suicide after their data was included in the stolen data.
Lawyers argue Vault 7 suspect Joshua Schulte is a whistleblower
Cyberscoop: Three years after WikiLeaks started publishing classified CIA-built hacking tools, the lead suspect's legal team will say he did so to reveal how the government breaks into common consumer tech products. By designating him a "whistleblower," it's hoped he'll get a reduced sentence. Joshua Schulte, a former CIA software engineer, is accused of stealing the files and giving them to WikiLeaks. The massive collection of published files was called Vault 7.
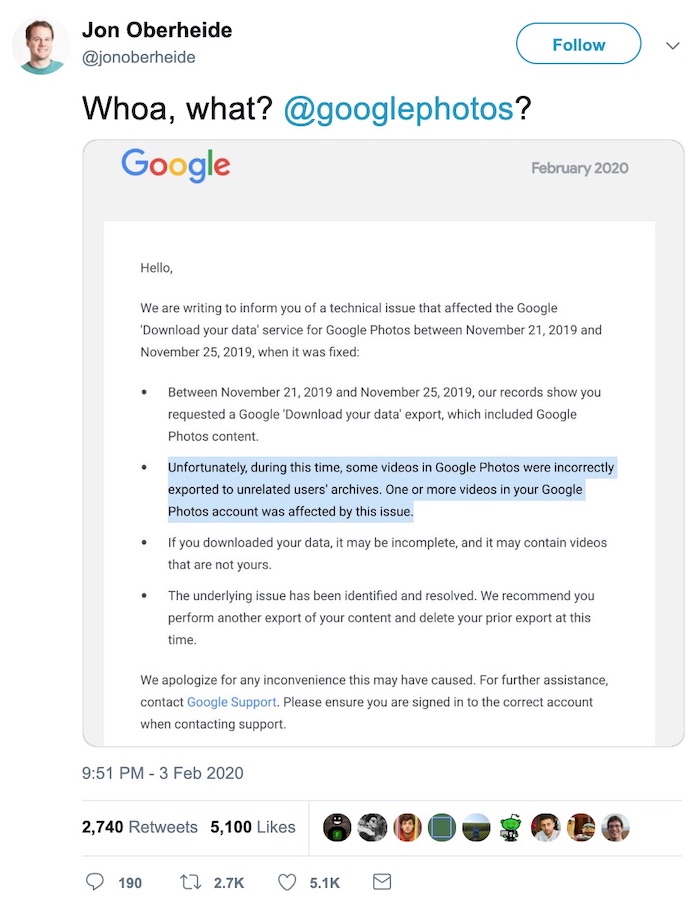
Nightmare Google Photos bug sent private videos to the wrong people
Ars Technica: Here's a nightmare situation: Google's data export service, which keeps the company compliant with GDPR and California's CCPA, accidentally delivered users' private photos to the wrong people. It's not known how many people were affected during the four-day security lapse in November 2019, only"less than 0.01%" of Photos users. Given it went past the billion mark last year, that could still be 100,000 people affected. Ouch.
Dangerous 'corp.com' domain goes up for sale
Krebs on Security For all those years you were told to use "corp.com" across your internal network, now that might come back to bite you in the ass. If corp.com is sold, it could create a "namespace collision," where domain names only to be used internally end up with an internet-resolvable domain name. That could be a real security concern down the line. Allowing corp.com to resolve could allow the siphoning off of email from internal networks that use corp.com as an internal-only domain name. A fascinating and eye-opening problem.
Safe harbor, or thrown to the sharks by Voatz?
Cointelegraph: @yaelwrites returns with new details on Voatz, a blockchain-enabled voting app that's been used in a handful of states and localities. CNN wrote last year about a security researcher who was referred to the FBI over he found an out-of-scope vulnerability in Voatz's system. But @yaelwrites goes further in examining the case, and found it was more to fire "warning shots" to prevent others from researching its closed-off voting system. I dream of a day where security research isn't matched with a legal threat.
One small fix would curb stingray surveillance
Wired ($): Clearly it's been a baller week for Wired. @lilyhnewman looks at stingray surveillance — where police using specialist technology can use cellular downgrade attacks to track your location and in some cases listen to your calls and read your messages. Turns out there's a simple fix to prevent this police snooping attack by adding a few extra bytes to the connection between the cell tower and the device. But surprise — the cell carriers don't like it because those extra bytes add up and cost them money. Classic. You can also read @rival_elf's tweet thread here.
~ ~
~ ~
OTHER NEWSY NUGGETS
Critical remote execution flaw found in WhatsApp
These findings were pretty breathtaking. The RCE found is particularly interesting, allowing remote access to a computer's files by sending a crafted message to a user on WhatsApp Desktop. Ars Technica has a tl;dr read. Facebook, which owns WhatsApp, has fixed the bugs.
Microsoft Teams went down due to an expired certificate
"Whoops" is an understatement. @GossiTheDog first spotted the cause, and was later confirmed by Microsoft. The outage only lasted a few hours but it was nevertheless an embarrassing (and very public) fustercluck.
CISA has helped to improve federal cybersecurity, but improvements needed
CISA, the Homeland Security cybersecurity division, has "been effective in strengthening federal cybersecurity" by issuing security advisories and directives, according to GAO, the government watchdog. But it also found agencies didn't always comply with the directives. That said, CISA didn't always check to see if the agencies were complying either. Another report this week found that CISA still hasn't released its election security plan, which is causing the watchdog considerable concern.
Iran-linked hackers posed as journalists in email scam
Several emails sent using the names of real-life CNN and Wall Street Journal reporters tried to ensnare a number of would-be victims in an effort to hack into their email accounts. The attempt was traced back to Charming Kitten, an Iranian-backed hacker group. Iran called the claims a "disinformation" effort against the country. Uh-huh.
~ ~
THE HAPPY CORNER
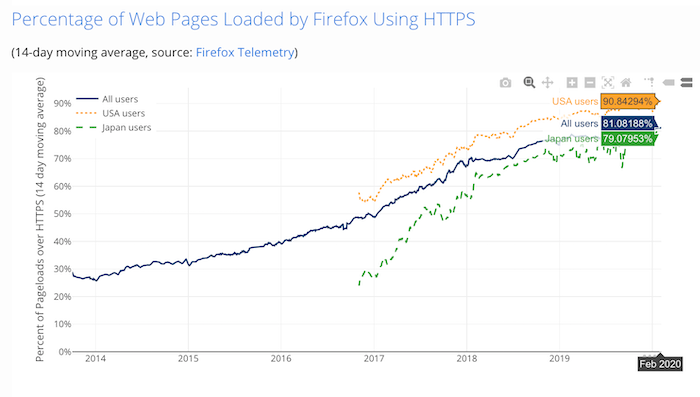
This week, we saw HTTPS rise to over 90% of all Firefox requested webpages in the U.S.. That's a huge milestone from just five years ago when it was half that. We can basically thank @letsencrypt for that. You can see the stats here.
And, also @laparisa, found a road crossing button that was offering some good security advice. Assuming, that is, it knows something we don't...
If you want to nominate some good news from the week, feel free to reach out.
~ ~
THIS WEEK'S CYBER CAT
This week's cybercat is Smokey, who loves his human but only lets him have the far left corner of the mouse pad. Classic! A big thanks to her human @ITGuySoCal for the submission!

Please keep sending in your cybercats! You can send them here.
~ ~
SUGGESTION BOX
And we're done for this week. What a busy one. Thanks for reading and subscribing. If you can, feel free to drop a dollar in the newsletter's Patreon. And as always, if you have feedback please drop me a note in the suggestion box. Have a great week — see you next Sunday.